 |
市场调查报告书
商品编码
1913318
工业网路安全市场机会、成长要素、产业趋势分析及预测(2026年至2035年)Industrial Cybersecurity Market Opportunity, Growth Drivers, Industry Trend Analysis, and Forecast 2026 - 2035 |
||||||
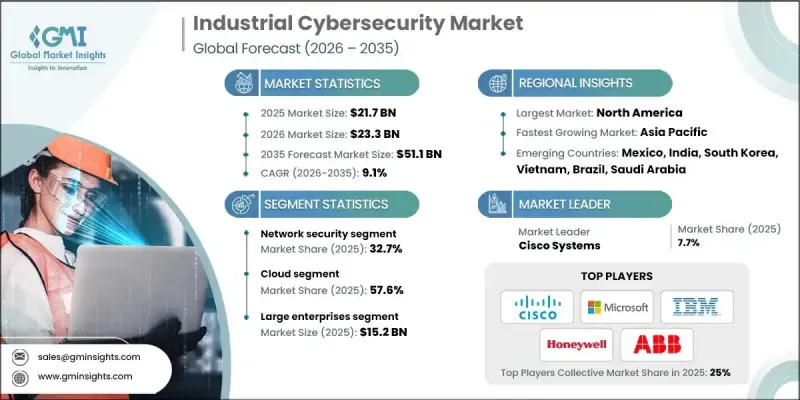
全球工业网路安全市场预计到 2025 年将达到 217 亿美元,到 2035 年将达到 511 亿美元,年复合成长率为 9.1%。
网路安全成长的驱动力在于针对营运系统的网路事件日益频繁、复杂化程度不断提高,且潜在影响也越来越大。随着工业营运的互联互通程度日益加深,保护关键基础设施已成为至关重要的策略要务。许多工业环境中仍存在显着的安全漏洞,导致监管机构的审查力度加大,企业面临越来越大的压力,必须加强网路防御以避免大规模的经济和营运中断。人工智慧 (AI) 和机器学习的应用正在重塑网路安全范式,实现快速威胁侦测、预测分析和持续监控。这些技术提高了复杂工作流程的可见性,并提升了回应的准确性。政府的强制性规定和合规要求正在加速关键工业运作中网路安全的普及,使网路安全成为基础设施现代化和长期风险管理策略的核心组成部分。
| 市场覆盖范围 | |
|---|---|
| 开始年份 | 2025 |
| 预测年份 | 2026-2035 |
| 起始值 | 217亿美元 |
| 预测金额 | 511亿美元 |
| 复合年增长率 | 9.1% |
到2025年,网路安全领域将占据32.7%的市场。强劲的需求源自于保护互联繫统间即时资料交换通讯通道日益增长的需求。由于业务连续性高度依赖可靠的网络,因此保护资料流对于维护安全性、生产力和系统稳定性至关重要。
预计到 2025 年,云端部署部分将占 57.6% 的市场份额,从 2026 年到 2035 年的复合年增长率将达到 10.2%。基于云端的网路安全解决方案对拥有分散式营运的组织尤其具有吸引力,因为它们可以在多个设施中提供集中式保护,而无需大量的初始投资。
预计到 2025 年,美国工业网路安全市场规模将达到 71 亿美元。早期采用互联技术以及对工业系统安全的大力投资巩固了其市场领先地位,使其成为工业网路安全支出最高的地区。
目录
第一章调查方法
第二章执行摘要
第三章业界考察
- 生态系分析
- 供应商情况
- 利润率
- 成本结构
- 每个阶段的附加价值
- 影响价值链的因素
- 中断
- 产业影响因素
- 司机
- 关键基础设施遭受网路攻击的频率增加
- 工业IoT(IIoT) 和智慧製造的日益普及
- 工业控制系统(ICS)日益数位化
- 严格的政府法规和合规要求
- 产业潜在风险与挑战
- 工业网路安全专业人员短缺
- 中小企业网路安全意识不足
- 市场机会
- 对人工智慧驱动的威胁侦测解决方案的需求日益增长
- 拓展新兴经济体的工业网路安全
- 工业领域对资安管理服务的需求不断增长
- 对即时威胁情报和监控解决方案的需求
- 司机
- 成长潜力分析
- 监管环境
- 北美洲
- NIST网路安全框架(CSF)2.0
- NERC CIP
- ISA/IEC 62443
- NIST SP 800-82
- 欧洲
- NIS2 指令
- IEC 62443
- DORA
- 网路安全基础
- 亚太地区
- 中国网路安全法(CSL)
- 经济产业省网路安全管理指南
- 新加坡网路安全法
- SOCI法案
- 拉丁美洲
- ANEEL网路安全标准
- ANATEL 安全条例
- 智利网路安全基本法
- 中东和非洲
- 基本网路安全措施 (ECC)
- 2012年第5号联邦法规(阿联酋)
- 网路犯罪法(沙乌地阿拉伯)
- 北美洲
- 波特五力分析
- PESTEL 分析
- 科技与创新趋势
- 当前技术趋势
- 新兴技术
- 价格趋势
- 按地区
- 副产品
- 成本細項分析
- 案例研究
- IT 和 OT 攻击统计数据
- 针对IT的网路攻击
- 针对营运技术 (OT) 的网路攻击
- IT-OT融合与混合攻击
- 来自先进产业和新兴产业的威胁
- IT/OT攻击的影响分析
- 技能和人才趋势
- 劳动供需
- 工业网路安全技能缺口
- 培训和认证项目
- 政府和产业为技能发展所采取的倡议
- 未来前景与机会
- 永续性和环境方面
- 永续实践
- 减少废弃物策略
- 生产中的能源效率
- 环保倡议
- 碳足迹考量
第四章 竞争情势
- 介绍
- 公司市占率分析
- 北美洲
- 欧洲
- 亚太地区
- 拉丁美洲
- 中东和非洲
- 主要市场公司的竞争分析
- 竞争定位矩阵
- 战略展望矩阵
- 重大进展
- 併购
- 伙伴关係与合作
- 新产品发布
- 企业扩张计画和资金筹措
第五章 按组件分類的市场估算与预测,2022-2035年
- 解决方案
- 硬体
- 软体
- 服务
- 託管服务
- 专业服务
第六章 2022-2035年按产品分類的市场估算与预测
- SCADA
- 身分和存取管理 (IAM)
- 统一威胁管理 (UTM)
- 预防资料外泄(DLP)
- IDS/IPS
- SIEM
- DDoS
- 其他的
7. 2022-2035年各车型市场估计与预测
- 云
- 本地部署
- 杂交种
第八章 依公司规模分類的市场估计与预测,2022-2035年
- 小型企业
- 大公司
第九章 证券市场估价与预测,2022-2035年
- 网路安全
- 端点安全
- 应用程式安全
- 云端安全
- 无线安全
- 其他的
第十章 2022-2035年各产业市场估计与预测
- 车
- 电子设备
- 食品/饮料
- 能源与电力
- 石油和天然气
- 化学
- 资讯科技/通讯
- 航太与国防
- 其他的
第十一章 2022-2035年各地区市场估计与预测
- 北美洲
- 美国
- 加拿大
- 欧洲
- 德国
- 英国
- 法国
- 义大利
- 西班牙
- 俄罗斯
- 北欧国家
- 比荷卢经济联盟
- 亚太地区
- 中国
- 印度
- 日本
- 韩国
- ANZ
- 新加坡
- 马来西亚
- 印尼
- 越南
- 泰国
- 拉丁美洲
- 巴西
- 墨西哥
- 阿根廷
- 哥伦比亚
- 中东和非洲
- 南非
- 沙乌地阿拉伯
- 阿拉伯聯合大公国
第十二章:公司简介
- 世界公司
- Siemens
- Honeywell
- Palo Alto Networks
- Cisco Systems
- Microsoft
- IBM
- Fortinet
- Schneider Electric
- Rockwell Automation
- Claroty
- Nozomi Networks
- Dragos
- Tenable
- ABB
- Thales
- 本地公司
- Armis
- Darktrace
- TXOne Networks
- Waterfall Security
- Radiflow
- Industrial Defender
- Trend Micro
- ABS Group
- Check Point
- Forescout
- 新兴企业
- Fox-IT
- ONEKEY
- ACURITY
- Keeper Security
- Underwriters Laboratories
The Global Industrial Cybersecurity Market was valued at USD 21.7 billion in 2025 and is estimated to grow at a CAGR of 9.1% to reach USD 51.1 billion by 2035.

Growth is driven by the rising frequency, sophistication, and potential impact of cyber incidents targeting operational systems. As industrial operations become increasingly interconnected, protecting critical infrastructure has become a top strategic priority. Many industrial environments still face significant security gaps, which has intensified regulatory oversight and increased pressure on organizations to strengthen cyber defenses to avoid large-scale economic and operational disruption. The adoption of artificial intelligence and machine learning is reshaping cybersecurity frameworks by enabling faster threat detection, predictive analysis, and continuous monitoring. These technologies improve visibility across complex workflows and enhance response accuracy. Government mandates and compliance requirements are accelerating cybersecurity implementation across critical industrial operations, making cybersecurity a core element of infrastructure modernization and long-term risk management strategies.
| Market Scope | |
|---|---|
| Start Year | 2025 |
| Forecast Year | 2026-2035 |
| Start Value | $21.7 Billion |
| Forecast Value | $51.1 Billion |
| CAGR | 9.1% |
The network security segment held a 32.7% share in 2025. Strong demand is driven by the need to secure communication channels that support real-time data exchange across interconnected systems. As operational continuity depends heavily on reliable networks, protecting data flows has become essential for maintaining safety, productivity, and system stability.
The cloud deployment segment accounted for 57.6% share in 2025 and is expected to grow at a CAGR of 10.2% from 2026 to 2035. Cloud-based cybersecurity solutions enable centralized protection across multiple facilities without requiring extensive upfront investment, making them especially attractive for organizations with distributed operations.
U.S. Industrial Cybersecurity Market reached USD 7.1 billion in 2025. Market leadership is supported by early adoption of connected technologies and strong investment in securing industrial systems, resulting in the highest regional spending on industrial cybersecurity.
Key companies operating in the Global Industrial Cybersecurity Market include Schneider Electric, IBM, Cisco Systems, Honeywell, Palo Alto Networks, ABB, Rockwell Automation, Thales, Microsoft, and Claroty. Companies in the Global Industrial Cybersecurity Market strengthen their competitive position through continuous innovation and integrated security offerings. Firms invest heavily in AI-driven threat detection, real-time monitoring, and predictive analytics to enhance protection capabilities. Strategic partnerships and ecosystem collaborations help expand solution compatibility across industrial platforms. Companies focus on scalable cloud-based architectures to support distributed operations efficiently. Expanding service portfolios to include consulting, risk assessment, and managed security services improves customer retention. Compliance-focused solutions aligned with regulatory requirements further strengthen trust.
Table of Contents
Chapter 1 Methodology
- 1.1 Market scope and definition
- 1.2 Research design
- 1.2.1 Research approach
- 1.2.2 Data collection methods
- 1.3 Data mining sources
- 1.3.1 Global
- 1.3.2 Regional/Country
- 1.4 Base estimates and calculations
- 1.4.1 Base year calculation
- 1.4.2 Key trends for market estimation
- 1.5 Primary research and validation
- 1.5.1 Primary sources
- 1.6 Forecast
- 1.7 Research assumptions and limitations
Chapter 2 Executive Summary
- 2.1 Industry 360° synopsis
- 2.2 Key market trends
- 2.2.1 Regional
- 2.2.2 Component
- 2.2.3 Product
- 2.2.4 Deployment Model
- 2.2.5 Enterprise Size
- 2.2.6 Security
- 2.2.7 Industry
- 2.3 TAM analysis, 2026-2035
- 2.4 CXO perspectives: Strategic imperatives
- 2.4.1 Executive decision points
- 2.4.2 Critical success factors
- 2.5 Future outlook and recommendations
Chapter 3 Industry Insights
- 3.1 Industry ecosystem analysis
- 3.1.1 Supplier landscape
- 3.1.2 Profit margin
- 3.1.3 Cost structure
- 3.1.4 Value addition at each stage
- 3.1.5 Factor affecting the value chain
- 3.1.6 Disruptions
- 3.2 Industry impact forces
- 3.2.1 Growth drivers
- 3.2.1.1 Rising frequency of cyberattacks on critical infrastructure
- 3.2.1.2 Increasing adoption of industrial IoT (IIoT) and smart manufacturing
- 3.2.1.3 Growing digitalization of industrial control systems (ICS)
- 3.2.1.4 Strict government regulations and compliance mandates
- 3.2.2 Industry pitfalls and challenges
- 3.2.2.1 Lack of skilled industrial cybersecurity professionals
- 3.2.2.2 Limited cybersecurity awareness among SMEs
- 3.2.3 Market opportunities
- 3.2.3.1 Growing demand for AI-driven threat detection solutions
- 3.2.3.2 Expansion of industrial cybersecurity in emerging economies
- 3.2.3.3 Rising need for managed security services in industries
- 3.2.3.4 Demand for real-time threat intelligence and monitoring solutions
- 3.2.1 Growth drivers
- 3.3 Growth potential analysis
- 3.4 Regulatory landscape
- 3.4.1 North America
- 3.4.1.1 NIST Cybersecurity Framework (CSF) 2.0
- 3.4.1.2 NERC CIP
- 3.4.1.3 ISA/IEC 62443
- 3.4.1.4 NIST SP 800-82
- 3.4.2 Europe
- 3.4.2.1 NIS2 Directive
- 3.4.2.2 IEC 62443
- 3.4.2.3 DORA
- 3.4.2.4 Cyber Essentials
- 3.4.3 Asia Pacific
- 3.4.3.1 China's Cybersecurity Law (CSL)
- 3.4.3.2 METI Cybersecurity Management Guidelines
- 3.4.3.3 Singapore Cybersecurity Act
- 3.4.3.4 SOCI Act
- 3.4.4 Latin America
- 3.4.4.1 ANEEL Cybersecurity Norms
- 3.4.4.2 ANATEL Security Regulations
- 3.4.4.3 Chile Framework Law on Cybersecurity
- 3.4.5 Middle East & Africa
- 3.4.5.1 Essential Cybersecurity Controls (ECC)
- 3.4.5.2 Federal Decree-Law No. 5/2012 (UAE)
- 3.4.5.3 Cybercrime Law (Saudi Arabia)
- 3.4.1 North America
- 3.5 Porter's analysis
- 3.6 PESTEL analysis
- 3.7 Technology and innovation landscape
- 3.7.1 Current technological trends
- 3.7.2 Emerging technologies
- 3.8 Price trends
- 3.8.1 By region
- 3.8.2 By product
- 3.9 Cost breakdown analysis
- 3.10 Case studies
- 3.11 IT and OT attacks statistics
- 3.11.1 IT-focused cyberattacks
- 3.11.2 OT-focused cyberattacks
- 3.11.3 IT-OT convergence & hybrid attacks
- 3.11.4 Advanced & emerging industrial threats
- 3.11.5 Impact analysis of IT & OT attacks
- 3.12 Skills & talent landscape
- 3.12.1 Workforce availability and demand
- 3.12.2 Skill gaps in industrial cybersecurity
- 3.12.3 Training and certification programs
- 3.12.4 Government and industry initiatives for skill development
- 3.13 Future outlook & opportunities
- 3.14 Sustainability and Environmental Aspects
- 3.14.1 Sustainable practices
- 3.14.2 Waste reduction strategies
- 3.14.3 Energy efficiency in production
- 3.14.4 Eco-friendly initiatives
- 3.14.5 Carbon footprint considerations
Chapter 4 Competitive Landscape, 2025
- 4.1 Introduction
- 4.2 Company market share analysis
- 4.2.1 North America
- 4.2.2 Europe
- 4.2.3 Asia Pacific
- 4.2.4 LATAM
- 4.2.5 MEA
- 4.3 Competitive analysis of major market players
- 4.4 Competitive positioning matrix
- 4.5 Strategic outlook matrix
- 4.6 Key developments
- 4.6.1 Mergers & acquisitions
- 4.6.2 Partnerships & collaborations
- 4.6.3 New product launches
- 4.6.4 Expansion plans and funding
Chapter 5 Market Estimates & Forecast, By Component, 2022 - 2035 ($Bn)
- 5.1 Key trends
- 5.2 Solution
- 5.2.1 Hardware
- 5.2.2 Software
- 5.3 Services
- 5.3.1 Managed services
- 5.3.2 Professional services
Chapter 6 Market Estimates & Forecast, By Product, 2022 - 2035 ($Bn)
- 6.1 Key trends
- 6.2 SCADA
- 6.3 Identity and Access Management (IAM)
- 6.4 Unified Threat Management (UTM)
- 6.5 Data Loss Prevention (DLP)
- 6.6 IDS/IPS
- 6.7 SIEM
- 6.8 DDoS
- 6.9 Others
Chapter 7 Market Estimates & Forecast, By Deployment Model, 2022 - 2035 ($Bn)
- 7.1 Key trends
- 7.2 Cloud
- 7.3 On-premises
- 7.4 Hybrid
Chapter 8 Market Estimates & Forecast, By Enterprise Size, 2022 - 2035 ($Bn)
- 8.1 Key trends
- 8.2 SMEs
- 8.3 Large enterprises
Chapter 9 Market Estimates & Forecast, By Security, 2022 - 2035 ($Bn)
- 9.1 Key trends
- 9.2 Network security
- 9.3 Endpoint security
- 9.4 Application security
- 9.5 Cloud security
- 9.6 Wireless security
- 9.7 Others
Chapter 10 Market Estimates & Forecast, By Industry, 2022 - 2035 ($Bn)
- 10.1 Key trends
- 10.2 Automotive
- 10.3 Electronics
- 10.4 Food & beverages
- 10.5 Energy & power
- 10.6 Oil & gas
- 10.7 Chemical
- 10.8 IT & Telecommunications
- 10.9 Aerospace & Defense
- 10.10 Others
Chapter 11 Market Estimates & Forecast, By Region, 2022 - 2035 ($Bn)
- 11.1 Key trends
- 11.2 North America
- 11.2.1 US
- 11.2.2 Canada
- 11.3 Europe
- 11.3.1 Germany
- 11.3.2 UK
- 11.3.3 France
- 11.3.4 Italy
- 11.3.5 Spain
- 11.3.6 Russia
- 11.3.7 Nordics
- 11.3.8 Benelux
- 11.4 Asia Pacific
- 11.4.1 China
- 11.4.2 India
- 11.4.3 Japan
- 11.4.4 South Korea
- 11.4.5 ANZ
- 11.4.6 Singapore
- 11.4.7 Malaysia
- 11.4.8 Indonesia
- 11.4.9 Vietnam
- 11.4.10 Thailand
- 11.5 Latin America
- 11.5.1 Brazil
- 11.5.2 Mexico
- 11.5.3 Argentina
- 11.5.4 Colombia
- 11.6 MEA
- 11.6.1 South Africa
- 11.6.2 Saudi Arabia
- 11.6.3 UAE
Chapter 12 Company Profiles
- 12.1 Global companies
- 12.1.1 Siemens
- 12.1.2 Honeywell
- 12.1.3 Palo Alto Networks
- 12.1.4 Cisco Systems
- 12.1.5 Microsoft
- 12.1.6 IBM
- 12.1.7 Fortinet
- 12.1.8 Schneider Electric
- 12.1.9 Rockwell Automation
- 12.1.10 Claroty
- 12.1.11 Nozomi Networks
- 12.1.12 Dragos
- 12.1.13 Tenable
- 12.1.14 ABB
- 12.1.15 Thales
- 12.2 Regional companies
- 12.2.1 Armis
- 12.2.2 Darktrace
- 12.2.3 TXOne Networks
- 12.2.4 Waterfall Security
- 12.2.5 Radiflow
- 12.2.6 Industrial Defender
- 12.2.7 Trend Micro
- 12.2.8 ABS Group
- 12.2.9 Check Point
- 12.2.10 Forescout
- 12.3 Emerging companies
- 12.3.1 Fox-IT
- 12.3.2 ONEKEY
- 12.3.3 ACURITY
- 12.3.4 Keeper Security
- 12.3.5 Underwriters Laboratories










