 |
市场调查报告书
商品编码
1403057
安全与漏洞管理 -市场占有率分析、产业趋势与统计、2024-2029 年成长预测Security and Vulnerability Management - Market Share Analysis, Industry Trends & Statistics, Growth Forecasts 2024 - 2029 |
||||||
※ 本网页内容可能与最新版本有所差异。详细情况请与我们联繫。
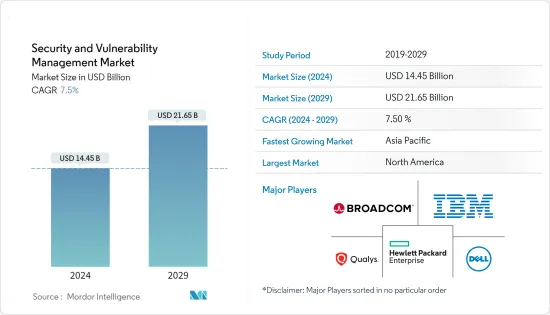
安全和漏洞管理市场规模预计到 2024 年将达到 144.5 亿美元,到 2029 年将达到 216.5 亿美元,在预测期内(2024-2029 年)复合年增长率为 7.5%。
主要亮点
- 防止资讯安全持续遭到破坏是所有产业组织面临的挑战。安全专业人员必须继续应对风险,防御传入攻击,并利用技术、策略和程序来保护敏感资料。这导致了市场成长。
- 此外,随着企业加速数位转型工作,他们必须快速对核心业务应用程式进行更改,而不影响本地、SDN 和云端环境的安全性。为了管理此流程,IT 和安全团队必须了解整个网路基础架构并对其进行精细控制。
- 根据美国与国际研究中心和麦克菲的数据,网路犯罪,包括资料损坏或破坏、金钱盗窃、财产损失和智慧财产权窃盗,目前给世界造成了约6,000 亿美元的损失(占全球GDP 的0.8%) 。 ) 每年。预计这些因素将推动安全和漏洞管理软体和服务的成长。
- 随着行动装置和高速网路的出现,BYOD 趋势在职场变得越来越普遍。例如,据戴尔称,大约 60% 的员工使用智慧型手机进行业务。这种趋势进一步促进了用户身份验证的市场成长。
- 随着越来越多的设备连接到互联网,网路世界中新威胁和攻击的发生和传播可能会增加。 WannaCry 和 Petya 攻击影响了全球 150 多个国家,凸显了作为端点的装置的脆弱性。
- 鑑于 COVID-19 大流行,各种规模的组织都在迅速建立远距工作安排,以帮助防止感染传播并允许员工在家工作。这意味着安装远端连接系统和安全设备,例如 VPN(虚拟私人网路)、Citrix虚拟桌面伺服器、远端桌面连接、檔案共用和 FTP 伺服器。这对供应商来说既是挑战也是机会。
安全和漏洞管理市场趋势
BFSI 细分市场预计将占据主要市场占有率
- 在全球范围内,金融机构是网路攻击最重要的目标。现在大多数金融服务已经数位化,网路安全对金融机构来说变得越来越重要。该领域的攻击数量正在增加,因为网路攻击现在可以针对交易系统和网站。作为世界上最大的金融市场之一,美国成为很大一部分网路攻击的目标。
- 由于BFSI部门服务的客户数量众多,资料外洩和网路攻击事件接连发生。资料外洩会导致补救措施的成本增加以及有价值的客户资讯的遗失。例如,台湾远东国际银行最近因恶意软体遭受了约6,000万美元的损失。
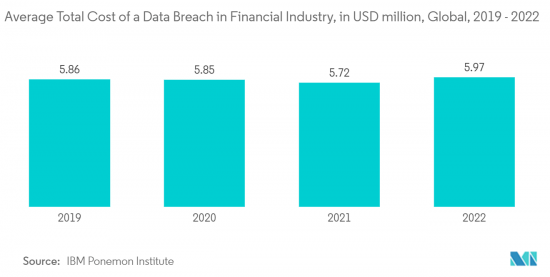
- 据IBM称,全球金融业资料外洩的平均成本为597万美元,高于去年的572万美元。私人和公共银行机构致力于实施先进技术来防御网路攻击,以保护其 IT 流程和系统、保护客户的关键资讯并遵守政府法规。
- 随着科技变得更加普及,网路和手机银行等数位管道比传统银行服务越来越受客户青睐,银行正在改善其身分验证和存取控製程式。需要改进。
- 2022 年 10 月,Temenos 将使银行能够在更可靠、安全和不断发展的自助服务平台上管理和管理金融犯罪缓解以及可组合银行服务。我们已经推出了可以处理此问题的 SaaS 服务。 Temenos 的 FCM 即服务提供符合全球产业法规的预先建置配置。银行可以透过自我配置和自动升级来降低总拥有成本、改善客户服务并实现更快的合规性和价值实现时间。
亚太地区预计成长最快
- 亚太地区网路安全攻击和 BYOD资料外洩的频率逐渐增加。因此,该地区有利于安全和漏洞管理解决方案的发展和需求。根据 ESET Enterprise 的研究,该地区近五分之一的商业组织近年来经历了六次或更多的安全漏洞。为了应对该地区网路攻击的增加,主要行业参与者正在专注于加强其防御能力。该地区各国政府也一直对该领域表现出兴趣。
- 託管安全服务、硬体支援、咨询和培训等安全服务应用可能会成为该地区的催化剂。随着与网路攻击相关的财务成本、监管成本和声誉损害的增加,没有征兆表明对网路安全服务的需求将会放缓。此外,根据 IBM Security 的一项研究,整个东协每家公司因安全漏洞造成的平均成本已增加至 271 万美元。成本上升和勒索软体显着增加显着增加了对可靠服务的需求。
- 澳洲、印尼、日本、马来西亚、菲律宾、新加坡、斯里兰卡和泰国等国家都积极采用安全和漏洞管理解决方案,因为它们制定了详细且最新的网路安全策略。这些策略通常伴随法律和业务框架以及专门机构,以满足关键基础设施保护和紧急应变需求。
- 相反,寮国、缅甸和巴基斯坦等国家正在製定有关网路安全方面的整体资讯通讯技术总体规划。这为供应商提供了提高其产品在这些国家/地区的知名度的机会。
- 此外,政府和相关监管机构加强安全性预计也将推动预测期内供应商解决方案的采用。例如,2022年3月,随着网路威胁在全球范围内增长,澳洲联邦政府宣布2022-23年度联邦拨款99亿澳元(约63.9亿美元),用于加强网路安全和威胁情报能力,该预算已公布。 100 亿澳元(64.6 亿美元)将用于名为 REDSPICE(弹性、效果、防御、空间、情报、网路、推动者)的计画。
安全与漏洞管理产业概述
安全和漏洞管理市场竞争适中,由多家大型参与者组成。为了在市场上获得更好的立足点,参与企业正在采取产品创新、合作和併购等策略。
2022 年 10 月,微软发布了 Azure DDoS IP 防护,这是中小型组织的 Azure DDoS 防护的新 SKU,以及企业级 DDoS 防护。 DDoS(分散式阻断服务)是一种攻击类型,攻击者向应用程式发送超出应用程式处理能力的请求。这会影响应用程式的可访问性以及向用户提供的服务。
2022年4月,HCL Technologies表示,透过扩大与微软的策略合作伙伴关係,将能为全球客户提供安全功能。总部位于诺伊达的 HCL Technologies 拥有 Microsoft 合作伙伴可以追求的四项高阶安全专业知识。 HCL Technologies 收购的四个 Microsoft Azure 领域是身分识别和存取管理高阶专业化、威胁防护高阶专业化、资讯治理和保护高阶专业化以及云端安全高阶专业化。
其他福利:
- Excel 格式的市场预测 (ME) 表
- 3 个月分析师支持
目录
第一章简介
- 研究假设和市场定义
- 调查范围
第二章调查方法
第三章执行摘要
第四章市场洞察
- 市场概览(根据 COVID-19 市场影响)
- 产业吸引力-波特五力分析
- 供应商的议价能力
- 买家/消费者的议价能力
- 新进入者的威胁
- 竞争公司之间敌对关係的强度
- 替代品的威胁
- 产业价值链分析
第五章市场动态
- 市场动态介绍
- 市场驱动因素
- 网路攻击增加
- 企业越来越多采用云端运算
- 市场抑制因素
- 对 SVM 解决方案缺乏认识
- 可扩展性和实施成本
第六章市场区隔
- 按组织规模
- 中小企业
- 大公司
- 按最终用户产业
- 航太,国防与情报
- BFSI
- 医疗保健
- 製造业
- 零售
- 资讯科技/通讯
- 其他最终用户产业
- 按地区
- 北美洲
- 欧洲
- 亚太地区
- 拉丁美洲
- 中东/非洲
第七章竞争形势
- 公司简介
- IBM Corporation
- Qualys Inc.
- Hewlett Packard Enterprise Company
- Dell EMC
- Tripwire Inc.
- Broadcom Inc.(Symantec Corporation)
- McAfee Inc.
- Micro Focus International PLC
- Rapid7 Inc.
- Fujitsu Limited
- Alien Vault Inc.
- Skybox Security Inc.
第八章投资分析
第九章 市场机会及未来趋势

The Security and Vulnerability Management Market size is estimated at USD 14.45 billion in 2024, and is expected to reach USD 21.65 billion by 2029, growing at a CAGR of 7.5% during the forecast period (2024-2029).
Key Highlights
- The task of defending against the continuous breach of information security lies with organizations in all sectors. Security professionals must continue to keep pace with the risks and leverage technologies, policies, and procedures that safeguard them against an incoming attack and secure sensitive data. This has led to the growth of the market.
- Also, as organizations accelerate their digital transformation initiatives, they need to quickly make changes to their core business applications without compromising security across on-premise, SDN, and cloud environments. To manage this process, IT and security teams must be able to see the whole network infrastructure and have fine-grained control over it.
- As per the Center for Strategic and International Studies and McAfee, cybercrimes, which include damage and destruction of data, stolen money, lost property, theft of intellectual property, and other areas, currently cost the world almost USD 600 billion each year, or 0.8% of global GDP. Such factors are expected to increase the growth of security and vulnerability management software and services.
- BYOD trends have become more and more common in workplaces as a result of the advent of mobile devices and high-speed Internet. For example, according to Dell, about 60% of employees use a smartphone for work. Such trends are further increasing the market growth for user authentication.
- The cyber-world is likely to see an increase in the occurrence and spread of new threats and attacks as more devices are getting connected to the Internet. The WannaCry and Petya attacks, which affected over 150 countries worldwide, have highlighted the vulnerability of devices as endpoints.
- In view of the COVID-19 pandemic, organizations of all sizes have undertaken initiatives for the quick establishment of remote working schemes to enable staff to work from their homes in order to prevent infection. This means setting up remote connectivity systems and security apparatuses such as VPNs (Virtual Private Networks), Citrix Virtual Desktop servers, remote desktop connections, file sharing, FTP servers, and several more. This presents some challenges as well as opportunities for the vendors.
Security and Vulnerability Management Market Trends
BFSI Segment is Expected to Hold the Major Market Share
- Globally, financial institutions are a top target for cyberattacks. Cybersecurity is becoming more important for financial firms as the majority of financial services are now digital. In this sector, cyberattacks can now target transaction systems and websites, which represents a growing number of attacks. The United States, as one of the world's largest financial markets, is the target of a sizable portion of cyberattacks.
- Given the high number of customers served by the BFSI sector, it has been subject to a series of data breaches and cyber-attacks. Data breaches result in increased costs for corrective measures and the loss of valuable customer information. For instance, in the recent past, Taiwan's Far Eastern International Bank incurred a loss of around USD 60 million due to malware.
- As per IBM, the average cost of data breaches in the finance industry worldwide was USD 5.97 million this year, up from USD 5.72 million last year. Private and public banking institutions are dedicated to the implementation of advanced technologies that will protect them from cyber attacks so as to ensure IT processes and systems, secure customer critical information, and comply with government regulations.
- Banks need to make use of improved authentication and access control procedures in view of the increased penetration of technology, along with digital channels such as Internet and mobile banking, which their customers are more likely to choose than traditional banking services.
- In October 2022, Temenos introduced a SaaS offering that allows banks to manage or handle Financial Crime Mitigation along with composable banking services on a much more reliable, secure, continually evolving, self-service platform. Temenos' FCM-as-a-Service offers pre-built configurations that are aligned with global industry regulations. Banks now have the ability to achieve lower total costs of ownership and improved customer service due to self-provisioning as well as automatic upgrades for rapid compliance and time to value.

Asia-Pacific is Expected to Grow at the Fastest Rate
- In Asia-Pacific, the frequency of cybersecurity assaults and BYOD data breaches is gradually increasing. The region is, therefore, favorable for the development and need for security and vulnerability management solutions. According to a survey from ESET Enterprise, nearly one in five commercial organizations in this region experienced more than six security breaches in recent years. The major industry participants are concentrating on bolstering their defensive capabilities due to the increased cyberattacks in this area. The countries' governments in this region have also consistently shown interest in this.
- Security service applications, such as managed security services, hardware support, consulting, and training, will act as catalysts in the region. There is no indication that the demand for cybersecurity services will decrease, given the rising financial expenses, regulatory costs, and reputational penalties related to cyberattacks. Additionally, according to IBM Security studies, the average cost of a security breach increased to USD 2.71 million per firm across ASEAN. Demand for reliable services has increased significantly as a result of rising costs and a significant increase in ransomware occurrences.
- Countries like Australia, Indonesia, Japan, Malaysia, the Philippines, Singapore, Sri Lanka, and Thailand are more inclined to adopt security and vulnerability management solutions, as they have detailed and up-to-date cybersecurity strategies in place. In order to address the critical infrastructure protection and emergency response needs, those strategies are often accompanied by legal and operational frameworks as well as dedicated agencies.
- Conversely, general ICT master plans for cyber security aspects are being prepared in countries such as Laos, Myanmar, and Pakistan. This presents an opportunity for vendors to raise awareness about their products in these countries.
- Moreover, the rising initiatives by the government and the related regulatory bodies to strengthen security are anticipated to fuel the adoption of the vendors' solutions over the forecast period. For instance, in March 2022, in the face of a growing cyber threat landscape across the globe, Australia's Federal Government issued its 2022-23 federal budget with an amount of AUD 9.9 billion (USD 6.39 Billion) to strengthen cybersecurity and intelligence capabilities. The AUD 10 billion (USD 6.46 billion) will be spent under a program called REDSPICE, i.e., Resilience, Effects, Defence, Space, Intelligence, Cyber and Enablers.
Security and Vulnerability Management Industry Overview
The security and vulnerability management market is moderately competitive and consists of several major players. In order to gain a better foothold in the market, players are adopting strategies such as product innovation, partnerships, and mergers and acquisitions.
In October 2022, Microsoft introduced Azure DDoS IP Protection, a new SKU of Azure DDoS Protection for small and medium-sized organizations, and enterprise-grade DDoS protection. DDoS, or distributed denial of service, is a type of assault in which the attacker sends an application more requests than it can handle. This has an effect on the application's accessibility and capacity to serve users.
In April 2022, by extending its strategic alliance with Microsoft, HCL Technologies said it would be able to offer security capabilities to clients all around the world. The Noida-based business has earned each of the four advanced security specializations that Microsoft partners can pursue. The four Microsoft Azure domains that HCL Tech has completed are Identity and Access Management Advanced Specialization, Threat Protection Advanced Specialization, Information Governance and Protection Advanced Specialization, and Cloud Security Advanced Specialization.
Additional Benefits:
- The market estimate (ME) sheet in Excel format
- 3 months of analyst support
TABLE OF CONTENTS
1 INTRODUCTION
- 1.1 Study Assumptions and Market Definition
- 1.2 Scope of the Study
2 RESEARCH METHODOLOGY
3 EXECUTIVE SUMMARY
4 MARKET INSIGHT
- 4.1 Market Overview (Followed by Impact of COVID-19 on the market)
- 4.2 Industry Attractiveness - Porter's Five Forces Analysis
- 4.2.1 Bargaining Power of Suppliers
- 4.2.2 Bargaining Power of Buyers/Consumers
- 4.2.3 Threat of New Entrants
- 4.2.4 Intensity of Competitive Rivalry
- 4.2.5 Threat of Substitute Products
- 4.3 Industry Value Chain Analysis
5 MARKET DYNAMICS
- 5.1 Introduction to Market Dynamics
- 5.2 Market Drivers
- 5.2.1 Increasing Number of Cyber Attacks
- 5.2.2 Growing Adoption of Cloud Computing by Enterprises
- 5.3 Market Restraints
- 5.3.1 Lack of Awareness Toward SVM Solutions
- 5.3.2 Scalability and Deployment Costs
6 MARKET SEGMENTATION
- 6.1 By Size of the Organization
- 6.1.1 Small and Medium Enterprises
- 6.1.2 Large Enterprises
- 6.2 By End-user Vertical
- 6.2.1 Aerospace, Defense, and Intelligence
- 6.2.2 BFSI
- 6.2.3 Healthcare
- 6.2.4 Manufacturing
- 6.2.5 Retail
- 6.2.6 IT and Telecommunication
- 6.2.7 Other End-user Industries
- 6.3 By Geography
- 6.3.1 North America
- 6.3.2 Europe
- 6.3.3 Asia Pacific
- 6.3.4 Latin America
- 6.3.5 Middle East & Africa
7 COMPETITIVE LANDSCAPE
- 7.1 Company Profiles
- 7.1.1 IBM Corporation
- 7.1.2 Qualys Inc.
- 7.1.3 Hewlett Packard Enterprise Company
- 7.1.4 Dell EMC
- 7.1.5 Tripwire Inc.
- 7.1.6 Broadcom Inc. (Symantec Corporation)
- 7.1.7 McAfee Inc.
- 7.1.8 Micro Focus International PLC
- 7.1.9 Rapid7 Inc.
- 7.1.10 Fujitsu Limited
- 7.1.11 Alien Vault Inc.
- 7.1.12 Skybox Security Inc.













