 |
市场调查报告书
商品编码
1404510
异常侦测:市场占有率分析、产业趋势/统计、成长预测,2024-2029Anomaly Detection - Market Share Analysis, Industry Trends & Statistics, Growth Forecasts 2024 - 2029 |
||||||
※ 本网页内容可能与最新版本有所差异。详细情况请与我们联繫。
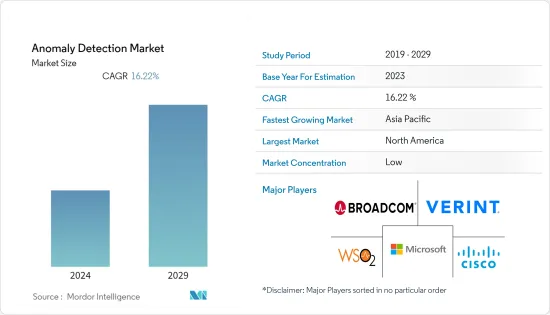
上年度异常侦测市场价值为 57.8 亿美元,预计将达到 137.5 亿美元,在预测期内的未来五年复合年增长率为 16.22%。
传统的统计方法正在被 GAN、VAE 和 RNN 等现代技术所取代,这些技术增强了对各种系统中异常情况的识别。此外,大规模资料储存设备和即时分析的需求不断增长,导致异常侦测系统的采用增加。
主要亮点
- 异常侦测是识别指示业务或流程中的异常变化的异常,而不是遵循可预测的资料或模式。除了诈欺侦测、系统健康监控和入侵侦测之外,异常侦测还可用于其他目的。
- 随着连接设备数量的迅速增加,这些设备产生的资料量变得巨大,使得管理这些资讯成为一项重大挑战。异常侦测可能会克服这一差距并在预测期内促进市场成长。
- 资料外洩通常意味着消费者的个人资讯被盗。诈骗可以进行诈欺购买、修改清单资讯、建立虚假评论、更改帐户资料等,并将付款发送到受损的银行帐户。
- 由于这种增长,异常侦测市场预计将在预测期内增长,银行、金融服务、医疗保健、製造、IT 和通讯、国防和政府等行业将使用多种连网设备。
- 预测期内异常侦测成长的主要挑战将是成本上升和来自开放原始码替代品的竞争,这将使组织难以采用工具和解决方案,同时也使组织难以在其他领域采用工具和解决方案。预计开放原始码模式将出现人才短缺和非对称故障等问题。
- COVID-19 的出现、封锁和强加的限制迫使许多组织将传统的工作方法转向远端工作。安全和风险经理必须进一步保护其组织,以确保线上服务和数位平台抵御网路犯罪的能力。组织越来越多地采用基于异常的入侵侦测系统。
异常侦测市场趋势
BFSI 预计将占据大部分市场占有率
- 由于其广泛的网路框架和重要的客户资讯,BFSI 部门面临多次资料外洩和网路攻击。因此,该行业的公司正在探索替代解决方案,异常侦测市场可能会在预测期内加强。
- 银行业务包括银行员工、客户和外国代理人进行的各种活动和交易。鑑于这些活动的复杂性,需要持续监控,以确保银行及其最终客户不会受到此类恶意活动的严重打击。由于这些原因,组织正在开发解决方案和服务来侦测异常。
- 银行业务包括银行员工、客户和独立机构定期和临时的一系列活动和交易。解释这些活动的本质是非常困难的。需要持续监控,以避免各种对银行及其客户产生不利影响的不当和违规活动。因此,在该领域提供解决方案和服务的公司有巨大的机会来缓解这些异常情况。
- 此外,数位化的进步使银行和金融机构能够透过线上入口网站更有效地提供银行服务,从而能够提供更好的客户服务。因此,大量资料正在积累,因此安全可靠地处理重要资讯至关重要。
北美市场占最大份额
- 美国联邦贸易委员会 (FTC) 指出,美国与付款和银行服务相关的资讯盗窃现象普遍存在,可能会导致更多地采用异常侦测解决方案和服务。
- 北美地区率先倡导了自带设备 (BYOD) 文化,并广泛采用。因此,企业开始寻找能够确保业务相关资讯安全的解决方案和服务,这可能会导致该地区异常侦测市场的扩大。
- 区域公司为客户提供异常侦测领域的广泛解决方案,提供更先进的功能和特性。
- 由于全部区域互联设备数量不断增加以及诈骗和网路攻击发生率不断增加,对异常侦测的需求也很强劲,从而加速了该领域的市场成长。
- 采用在线演算法、学习增量方法和滑动技术等异常侦测系统是最新的基于批处理窗口的异常侦测技术之一,用于各个领域以有效地传输资料,并且它受到对电容资料存储单元和数据存储单元的需求的刺激。即时资料分析。
异常侦测产业概述
Cisco、WSO2 和 Microsoft 等主要企业在异常侦测市场的竞争中占据主导地位。整体而言,产业内竞争企业之间的敌意相对较高。透过策略联盟、併购和收购,市场参与者可以在向客户提供更好的解决方案和产品方面保持立足点。
其他福利:
- Excel 格式的市场预测 (ME) 表
- 3 个月分析师支持
目录
第一章简介
- 研究假设和市场定义
- 调查范围
第二章调查方法
第三章执行摘要
第四章市场洞察
- 市场概况
- 产业吸引力-波特五力分析
- 供应商的议价能力
- 买家/消费者的议价能力
- 新进入者的威胁
- 替代品的威胁
- 竞争公司之间的敌对关係
第五章市场动态
- 市场驱动因素
- 网路犯罪增加
- 在软体测试中更多采用异常侦测解决方案
- 市场抑制因素
- 开放原始码替代品构成威胁
第六章市场区隔
- 按类型
- 解决方案
- 服务
- 按最终用户产业
- BFSI
- 製造业
- 卫生保健
- 资讯科技/通讯
- 其他的
- 按发展
- 本地
- 云
- 按地区
- 北美洲
- 美国
- 加拿大
- 欧洲
- 英国
- 德国
- 法国
- 其他欧洲国家
- 亚太地区
- 澳洲
- 日本
- 印度
- 其他亚太地区
- 其他地区
- 北美洲
第七章竞争形势
- 公司简介
- Verint Systems Inc.
- Broadcom Inc.(Symantec Corporation)
- WSO2 Inc.
- Microsoft Corporation
- Cisco Systems Inc.
- IBM Corporation
- Wipro Limited
- Trend Micro Incorporated
- SAS Institute Inc.
- Happiest Minds Technologies Pvt. Ltd
- Guardian Analytics Inc.
第八章投资分析
第九章 市场机会及未来趋势

The anomaly detection market was valued at USD 5.78 billion in the previous year and is expected to register a CAGR of 16.22%, reaching USD 13.75 billion by the next five years during the forecast period. The traditional statistical approaches are being replaced with modern methods, such as Generative Adversarial Networks (GAN), variational autoencoders (Vaes), and Recurrent Neural Networks (RNNs), thereby enhancing the identification of anomalies across various systems. In addition, the adoption of anomaly detection systems has been increased by a growing demand for significant data storage devices and real-time analysis.
Key Highlights
- Anomaly detection is the identification of anomalies that indicate unusual shifts in operations and processes rather than following predictable data or patterns. In addition to fraud detection, system health monitoring, and intrusion detection, anomaly detection can be used for other purposes.
- As the number of connected devices increases rapidly, the amount of data generated by these devices is enormous, making it a critical task to manage this information, which could lead to the loss of valuable information. Anomaly detection could overcome this gap, increasing market growth during the forecast period.
- The breach of data usually means identity theft to the consumer. Fraudsters can make fraudulent purchases, modify listing information, create false reviews, or change account data to take payments into their bank accounts once compromised.
- The market for anomaly detection As a result of this increase, it is expected to grow during the forecast period, and several connected devices are in sectors such as banking, financial services, health care, manufacturing, information technology, telecommunications, defense, and government.
- The main challenges to the growth of anomaly detection during that period are expected to be rising costs and competition from opensource alternatives, which would make it more difficult for organizations to adopt tools and solutions while there is also a lack of qualified workers in areas such as solution development and incidence of asymmetrical faults within Open Source models.
- The emergence of COVID-19, the lockdown, and the restrictions imposed forced many organizations to shift their traditional working methodologies to remote working. Security and risk managers must safeguard their organizations even more to ensure the resilience of online services and digital platforms against cybercrime. Organizations are increasingly adopting anomaly-based intrusion detection systems.
Anomaly Detection Market Trends
BFSI is Expected to Hold a Significant Part of the Market Share
- It faces several data breaches and cyber attacks due to its extensive network framework and essential customer information in the BFSI sector. Consequently, companies within the industry have been looking for alternate solutions that will likely strengthen the anomaly detection market during the forecast period.
- The banking operation includes various activities and transactions carried out by staff, customers, and foreign agents. Given the complexities of these activities, continuous monitoring is required to ensure that a bank or its end customers are hit significantly by any such malicious activity. For these reasons, solutions and services for detecting anomalies are being developed by organizations.
- Several periodic and occasional activities and transactions carried out by staff, clients, and independent agencies shall be included in banking operations. It is very difficult to describe the nature of these activities. It calls for continuous monitoring to avoid an adverse effect on the bank or its customers due to various inappropriate and random actions. Therefore, firms offering solutions and services in this area have a huge opportunity to mitigate these anomalies.
- In addition, the increase in digitization has enabled banks and financial institutions to offer banking services more efficiently through online portals, allowing them to provide better customer service. This has led to the development of large quantities of data, making it vital that critical information be handled safely and securely.

North America Holds the Largest Share in the Market
- The Federal Trade Commission pointed out that identity theft related to payment and banking services in the United States is widespread, which could lead to increased adoption of Anomaly Detection Solutions and Services.
- North America is a pioneer in the bring-your-own-device (BYOD) culture, which has resulted in its wide-scale adoption. In doing so, the companies have started searching for solutions and services that enable them to guarantee the security of information relating to business, which could lead to an increase in the area's Anomaly Detection Market.
- Regional enterprises provide their clients with an extensive range of solutions in the area of anomaly detection and are providing more advanced features and functionalities.
- In addition, there is also a strong demand for anomaly detection and an acceleration of market growth in this area due to the increasing number of interconnected devices and rising incidences of fraud and cyber-attacks throughout the region.
- Adopting anomaly detection systems as online algorithms, learning incremental approaches, and sliding techniques are among the modern batch window-based anomaly detection techniques used by different sectors to stream data efficiently has been stimulated by the need for large data storage units and real-time data analysis.
Anomaly Detection Industry Overview
Some key players, such as Cisco Systems Inc., WSO2 Inc., Microsoft Corporation, etc., govern the anomaly detection market competition. Overall, the competitive rivalry within the industry is relatively high. Through strategic partnerships, mergers, and acquisitions, the companies in the market can maintain their foothold to provide better solutions and products to their customers.
Cisco announced its vision for Cisco Networking Cloud, an integrated management platform experience for both on-premise and cloud operating models, in June this year. These innovations include SSO, API key exchange/repository, sustainable data center networking solutions, and expanded network assurance with Cisco ThousandEyes.Cisco Networking Cloud will dramatically simplify IT with a more flexible Cisco Catalyst switch stack, improved visibility into data center power and energy consumption, and new AI data center blueprints to enhance performance and visibility for network operators.
Through Google Cloud Contact Center AI integration with Verint's customer engagement Platform, the two companies have announced an enhanced partnership to help improve contact center performance in March this year. Combining its customer experience automation solutions with Google Cloud's Contact Center AICCAI platform is as seamless as the Verint Platform's unique open architecture. Through this collaboration, organizations can use Verint's solutions to close the Engagement capacity gap with CX automation. This robust platform-to-platform approach offers essential capabilities for organizations seeking best-of-breed solutions.
Additional Benefits:
- The market estimate (ME) sheet in Excel format
- 3 months of analyst support
TABLE OF CONTENTS
1 INTRODUCTION
- 1.1 Study Assumptions and Market Definition
- 1.2 Scope of the Study
2 RESEARCH METHODOLOGY
3 EXECUTIVE SUMMARY
4 MARKET INSIGHTS
- 4.1 Market Overview
- 4.2 Industry Attractiveness - Porter's Five Forces Analysis
- 4.2.1 Bargaining Power of Suppliers
- 4.2.2 Bargaining Power of Buyers/Consumers
- 4.2.3 Threat of New Entrants
- 4.2.4 Threat of Substitute Products
- 4.2.5 Intensity of Competitive Rivalry
5 MARKET DYNAMICS
- 5.1 Market Drivers
- 5.1.1 Increasing Number of Cyber Crimes
- 5.1.2 Increasing Adoption of Anomaly Detection Solutions in Software Testing
- 5.2 Market Restraints
- 5.2.1 Open Source Alternatives Pose as a Threat
6 MARKET SEGMENTATION
- 6.1 By Type
- 6.1.1 Solutions
- 6.1.2 Service
- 6.2 By End-user Industry
- 6.2.1 BFSI
- 6.2.2 Manufacturing
- 6.2.3 Healthcare
- 6.2.4 IT and Telecommunications
- 6.2.5 Other End-user Industries
- 6.3 By Deployment
- 6.3.1 On-premise
- 6.3.2 Cloud
- 6.4 By Geography
- 6.4.1 North America
- 6.4.1.1 United States
- 6.4.1.2 Canada
- 6.4.2 Europe
- 6.4.2.1 United Kingdom
- 6.4.2.2 Germany
- 6.4.2.3 France
- 6.4.2.4 Rest of Europe
- 6.4.3 Asia Pacific
- 6.4.3.1 Australia
- 6.4.3.2 Japan
- 6.4.3.3 India
- 6.4.3.4 Rest of Asia Pacific
- 6.4.4 Rest of the World
- 6.4.1 North America
7 COMPETITIVE LANDSCAPE
- 7.1 Company Profiles
- 7.1.1 Verint Systems Inc.
- 7.1.2 Broadcom Inc. (Symantec Corporation)
- 7.1.3 WSO2 Inc.
- 7.1.4 Microsoft Corporation
- 7.1.5 Cisco Systems Inc.
- 7.1.6 IBM Corporation
- 7.1.7 Wipro Limited
- 7.1.8 Trend Micro Incorporated
- 7.1.9 SAS Institute Inc.
- 7.1.10 Happiest Minds Technologies Pvt. Ltd
- 7.1.11 Guardian Analytics Inc.













