 |
市场调查报告书
商品编码
1432458
勒索软体保护:市场占有率分析、产业趋势/统计、成长预测(2024-2029)Ransomware Protection - Market Share Analysis, Industry Trends & Statistics, Growth Forecasts (2024 - 2029) |
||||||
※ 本网页内容可能与最新版本有所差异。详细情况请与我们联繫。
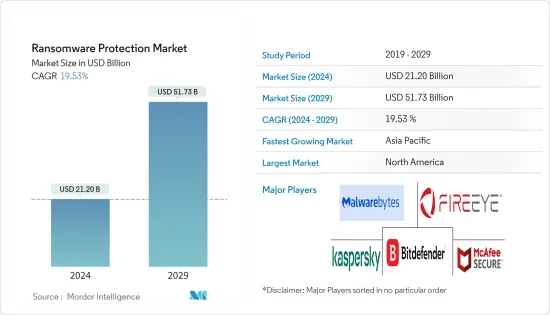
勒索软体保护市场规模预计到 2024 年将达到 212 亿美元,预计到 2029 年将达到 517.3 亿美元,在预测期内(2024-2029 年)复合年增长率为 19.53%。
由于企业数位化不断提高、勒索软体即服务(RaaS) 的使用不断增加以及比特币等加密货币的引入,全球勒索软体防护市场正在不断扩大。然而,由于缺乏对网路攻击的了解和财务限制,业务扩展受到限制。另一方面,随着企业寻求更多层次的安全保护以及云端基础的服务的更广泛应用,新的商机将会出现。
主要亮点
- 近年来,随着勒索软体保护即服务的需求不断增加,全球勒索软体保护市场预计将显着成长。比特币、以太币等加密货币的出现增加了对勒索软体防护解决方案的需求,因为由于加密货币的不可追踪性,大多数赎金都以加密货币的形式索取。此外,产业受到技术发展的影响,针对PC以外的行动装置的勒索软体防护解决方案也不断涌现。
- 此外,勒索软体策略、技术和程序 (TTP) 的发展增加了对高阶保护机制的需求。勒索软体即服务 (RaaS) 模型、多态恶意软体以及针对关键基础设施的针对性攻击的激增需要自适应且先进的防御解决方案。勒索软体防护市场正在透过提供全面的网路安全套件来应对这些挑战,其中包括威胁情报、端点保护、网路安全以及资料备份和復原。
- 此外,企业受到社会攻击影响的可能性几乎是物理漏洞影响的三倍,凸显了对员工进行持续网路安全教育的必要性。因此,企业正在转向勒索软体防护解决方案,大大推动了所研究市场对解决方案的需求。
- 勒索软体攻击的增加是由 COVID-19 大流行造成的。多年来,勒索软体一直是网路窃贼首选的攻击策略。组织已经看到这些攻击的规模和复杂性不断增长。据国际刑警组织称,COVID-19 极大地改变了危险环境,从针对个人和小型企业的攻击转变为针对关键基础设施、政府和大型组织的攻击。
勒索软体防护市场趋势
云端部署在勒索软体防护中发挥重要作用
- 云端储存不能免于勒索软体威胁,也不安全。勒索软体肯定会影响云端存储,特别是如果云端储存供应商没有积极使用勒索软体保护技术。事实上,勒索软体可以影响任何网路连线策略。这包括安全恆温器、摄影机和门铃等物联网设备,以及充当 PC、文件、电子邮件、资料伺服器和云端储存的云端基础的伺服器。
- 云端储存厂商应不断评估、测试和升级其安全解决方案,并采用分层防御方法。组织应要求商家共用侦测、隔离和删除勒索软体的精确且具体的步骤。
- 组织还可以在所有装置上部署勒索软体防护软体,包括云端伺服器和云端储存。该软体必须具有针对勒索软体攻击的冗余和容错移转保护。组织还需要製定、实施和实践资料备份和搜寻策略和计划。并且(组织)应该实施所有资料的连续备份,作为这些灾难搜寻策略的一部分。
- 此外,云端安全的独特之处在于它更依赖健全的设计和架构,而不是入侵侦测或安全分析。骇客不是侵入网路并锁定係统,而是利用云端错误配置来操纵云端控制平面 API 并从底层窃取资料。
北美在勒索软体防护市场中占最大份额
- 该地区以入侵和网路攻击而闻名。例如,SamSam 勒索软体被用来攻击亚特兰大的IT基础设施,渗透网路并隐藏其存在,同时捕获凭证并在传播到多台电脑后将其锁定。这导致该市线上服务大规模中断,估计该市损失了至少 260 万美元的清理和回应成本。
- 此外,2023 年 9 月,FBI 警告美国企业警惕连续多次针对同一组织的双重勒索软体攻击。美国联邦调查局也表示,不同的勒索软体工具以不同的组合使用,这可能会给目标公司带来可怕的后果。 「双重勒索软体变体的使用导致了资料加密、洩漏以及因支付赎金而造成的经济损失。
- 来自其他国家试图影响美国关键基础设施的威胁持续增加,WannaCry 就是此类针对性勒索软体之一。因参与 WannaCry 攻击而被起诉。此类行动迫使组织透过更新服务来改善其安全领域并加强IT安全。
- 此外,2023 年 11 月,提供即时网路保护的 Malwarebytes 宣布推出 ThreatDown 系列产品,为 IT 受限的组织提供有效且易于使用的网路安全。
勒索软体保护产业概述
勒索软体保护市场由多个参与者组成。从市场占有率来看,目前该市场由少数参与者主导。这些拥有压倒性市场份额的大公司正致力于扩大海外基本客群。这些公司正在利用策略合作措施来扩大市场占有率并提高盈利。
- 2023 年 1 月 - 晶片製造商英特尔和网路安全公司 Check Point Software Technologies 之间的现有合作伙伴关係已扩展,以针对当今最常见的安全风险之一勒索软体提供硬体级保护。
- 2023 年 6 月 - CTERA 宣布发布 CTERA Ransom Protect,这是一款整合到 CTERA 世界檔案系统中的新型人工智慧驱动的网路保护引擎。 CTERA Ransom Protect 使用檔案系统内建的活动感测器在几秒钟内侦测并阻止攻击,这些感测器为经过大型攻击流资料集训练的高级机器学习演算法提供支援。它还提供了立即缓解攻击并从攻击中恢復的工具。
其他福利:
- Excel 格式的市场预测 (ME) 表
- 3 个月的分析师支持
目录
第一章简介
- 市场定义和范围
- 研究场所
第二章调查方法
第三章执行摘要
第四章市场洞察
- 市场概况
- 产业相关人员分析
- 产业吸引力-波特五力分析
- 供应商的议价能力
- 消费者议价能力
- 新进入者的威胁
- 替代品的威胁
- 竞争公司之间的敌对关係
第五章市场动态
- 市场概况
- 市场驱动因素
- 网路钓鱼攻击和有针对性的安全漏洞增加
- 勒索软体作为服务模式的出现
- 使用加密货币作为支付方式
- 云端部署对于勒索软体防护的重要性
- 市场限制因素
- 用于勒索软体防护的免费端点解决方案的可用性
第六章市场区隔
- 部署
- 本地
- 在云端
- 目的
- 端点保护
- 电子邮件保护
- 网路安全
- 其他用途
- 地区
- 北美洲
- 美国
- 加拿大
- 欧洲
- 德国
- 英国
- 法国
- 西班牙
- 其他欧洲国家
- 亚太地区
- 中国
- 日本
- 印度
- 澳洲
- 其他亚太地区
- 拉丁美洲
- 巴西
- 墨西哥
- 阿根廷
- 其他拉丁美洲
- 中东/非洲
- 阿拉伯聯合大公国
- 沙乌地阿拉伯
- 南非
- 其他中东和非洲
- 北美洲
第七章 竞争形势
- 公司简介
- McAfee, LLC
- AO Kaspersky Lab
- Bitdefender
- FireEye, Inc.
- Malwarebytes
- SentinelOne
- Sophos Ltd.
- Symantec Corporation
- Trend Micro Incorporated
- Zscaler, Inc
第八章投资分析
第九章 市场机会及未来趋势
The Ransomware Protection Market size is estimated at USD 21.20 billion in 2024, and is expected to reach USD 51.73 billion by 2029, growing at a CAGR of 19.53% during the forecast period (2024-2029).

The global ransomware protection market is expanding due to rising company digitization, increased use of ransomware-as-a-service (RaaS), and the introduction of cryptocurrencies like Bitcoin. However, a lack of knowledge about cyberattacks and financial limitations limit business expansion. On the other hand, new opportunities will arise as enterprises seek more multi-layer security protection and cloud-based services are used more widely.
Key Highlights
- Owing to the increase in the demand for ransomware protection in recent years as a service, the global ransomware protection market is projected to witness a significant growth rate. The advent of cryptocurrencies, such as Bitcoin, Etherium, increased the demand for ransomware protection solutions as a majority of the ransom is demanded in the form of cryptocurrency due to its untraceable nature. Moreover, the industry is impacted by technological developments and has seen the advent of ransomware protection solutions for mobile devices, too, apart from PCs.
- Moreover, the evolution of ransomware tactics, techniques, and procedures (TTPs) has heightened the need for advanced protection mechanisms. Ransomware-as-a-Service (RaaS) models, polymorphic malware, and targeted attacks on critical infrastructure have become prevalent, necessitating adaptive and sophisticated defense solutions. The ransomware protection market responds to these challenges by offering comprehensive cybersecurity suites that include threat intelligence, endpoint protection, network security, and data backup and recovery.
- Also, companies are nearly three times more susceptible to suffering breaches through social attacks than via actual vulnerabilities, emphasizing the need for ongoing employee cybersecurity education. It has led to the company looking towards ransomware protection solutions and has provided a considerable push for the solutions demand in the studied market.
- Worldwide, a rise in ransomware attacks was brought on by the global COVID-19 outbreak. For many years, ransomware has been the assault strategy of choice for online thieves. Organizations witnessed an increase in the size and sophistication of these attacks. According to Interpol, COVID-19 drastically changed the dangerous environment from attacks on people and small companies to essential infrastructure, governments, and large organizations.
Ransomware Protection Market Trends
Cloud Deployment Plays a Major Role in Ransomware Protection
- Cloud storage is not resistant to ransomware threats and is not foolproof. Ransomware can certainly affect cloud storage, especially if the cloud storage dealers are not proactively using anti-ransomware technology. In fact, ransomware can impact any and all internet-connected strategies. This includes IoT devices, like security thermostats, cameras, doorbells, and others like PCs, file, email, and data servers, and cloud-based servers, which performs as cloud storage.
- Cloud storage vendors should constantly be evaluating, testing, and upgrading their security solutions and using multilayered defense methods. Organizations should ask merchants to share their precise and specific ransomware detection, quarantine, and removal procedures.
- Organizations can also deploy anti-ransomware protection software on all devices, including cloud servers and cloud storage. That software should have redundancy and failover defense in case of a ransomware attack. Organizations are also required to have data backup and retrieval policies and plans that are really implemented and practiced. And (they should) conduct ongoing backups of all data as part of those disaster retrieval policies.
- Further, it depends on sound design and architecture rather than intrusion detection and security analysis, security in the cloud is unique. Hackers attempt to take advantage of cloud misconfigurations that allow them to operate against your cloud control plane APIs and steal data out from under rather than breaking into the network to lock out of systems.
North America Holds The Largest Market Share in Ransomware Protection Market
- The region is known for infiltration and cyber-attacks. For instance, the SamSam ransomware was used to attack Atlanta's IT infrastructure by infiltrating into the network, hiding its presence while it harvested credentials to spread to multiple computers before locking them up. It resulted in a mass shutdown of online city services and an estimated cost of at least USD 2.6 million in clean-up and response.
- Further, in September 2023, The FBI is warning businesses in the United States to be on the lookout for dual ransomware attacks, in which the same organization is targeted more than once in quick succession. The FBI also stated that a variety of ransomware tools are being used in various combinations, with potentially disastrous consequences for targeted businesses. "The use of dual ransomware variants resulted in data encryption, exfiltration, and financial losses as a result of ransom payments.
- There is a continued rise in the threats from other nations which try to affect the critical infrastructure of the US, WannaCry was one such target ransomware where Park Jin-hook, a North Korean national, was charged for being part of a WannaCry attack undertaken on behalf of the North Korean government. Such actions have pushed organizations to improve the security segment and strengthen their IT security by updating the services.
- Moreover, in November 2023, Malwarebytes, a company that provides real-time cyber protection, announced the launch of ThreatDown, a product family that provides effective, easy-to-use cybersecurity to IT-constrained organizations.
Ransomware Protection Industry Overview
The ransomware protection market consists of several players. In terms of market share, few of the players currently dominate the market. These major players with a prominent share of the market are focusing on expanding their customer base across foreign countries. These companies are leveraging strategic collaborative initiatives to increase their market share and increase their profitability.
- In January 2023 - A pre-existing alliance between chipmaker Intel and cybersecurity firm Check Point Software Technologies was extended to offer hardware-level defense against ransomware, one of the most common security dangers of the present.
- In June 2023 - CTERA announced the release of CTERA Ransom Protect, a new AI-powered cyber protection engine integrated into the CTERA global file system. CTERA Ransom Protect detects and blocks attacks in seconds, thanks to activity sensors built into the file system that feed an advanced machine learning algorithm trained on a large dataset of attack flows. It also provides tools for immediate mitigation and recovery.
Additional Benefits:
- The market estimate (ME) sheet in Excel format
- 3 months of analyst support
TABLE OF CONTENTS
1 INTRODUCTION
- 1.1 Market Definition and Scope
- 1.2 Study Assumptions
2 RESEARCH METHODOLOGY
3 EXECUTIVE SUMMARY
4 MARKET INSIGHTS
- 4.1 Market Overview
- 4.2 Industry Stakeholder Analysis
- 4.3 Industry Attractiveness - Porter's Five Forces Analysis
- 4.3.1 Bargaining Power of Suppliers
- 4.3.2 Bargaining Power of Consumers
- 4.3.3 Threat of New Entrants
- 4.3.4 Threat of Substitute Products
- 4.3.5 Intensity of Competitive Rivalry
5 MARKET DYNAMICS
- 5.1 Market Overview
- 5.2 Market Drivers
- 5.2.1 Increasing Number of Phishing Attacks and Targeted Security Breaches
- 5.2.2 Emergence of Ransomware as a Service Model
- 5.2.3 Use of Crypto Currencies as Payment Method
- 5.2.4 Cloud Deployment Plays a Major Role in Ransomware Protection
- 5.3 Market Restraints
- 5.3.1 Availability of Free Endpoint Solutions for Ransomware Protection
6 MARKET SEGMENTATION
- 6.1 Deployment
- 6.1.1 On-Premise
- 6.1.2 On-Cloud
- 6.2 Application
- 6.2.1 Endpoint Protection
- 6.2.2 Email Protection
- 6.2.3 Network Security
- 6.2.4 Other Applications
- 6.3 Geography
- 6.3.1 North America
- 6.3.1.1 United States
- 6.3.1.2 Canada
- 6.3.2 Europe
- 6.3.2.1 Germany
- 6.3.2.2 UK
- 6.3.2.3 France
- 6.3.2.4 Spain
- 6.3.2.5 Rest of Europe
- 6.3.3 Asia-Pacific
- 6.3.3.1 China
- 6.3.3.2 Japan
- 6.3.3.3 India
- 6.3.3.4 Australia
- 6.3.3.5 Rest of Asia-Pacific
- 6.3.4 Latin America
- 6.3.4.1 Brazil
- 6.3.4.2 Mexico
- 6.3.4.3 Argentina
- 6.3.4.4 Rest of Latin America
- 6.3.5 Middle East and Africa
- 6.3.5.1 UAE
- 6.3.5.2 Saudi Arabia
- 6.3.5.3 South Africa
- 6.3.5.4 Rest of Middle East and Africa
- 6.3.1 North America
7 COMPETITIVE LANDSCAPE
- 7.1 Company Profiles*
- 7.1.1 McAfee, LLC
- 7.1.2 AO Kaspersky Lab
- 7.1.3 Bitdefender
- 7.1.4 FireEye, Inc.
- 7.1.5 Malwarebytes
- 7.1.6 SentinelOne
- 7.1.7 Sophos Ltd.
- 7.1.8 Symantec Corporation
- 7.1.9 Trend Micro Incorporated
- 7.1.10 Zscaler, Inc











