 |
市场调查报告书
商品编码
1432877
物联网安全:市场占有率分析、产业趋势/统计、成长预测(2024-2029)IoT Security - Market Share Analysis, Industry Trends & Statistics, Growth Forecasts (2024 - 2029) |
||||||
※ 本网页内容可能与最新版本有所差异。详细情况请与我们联繫。
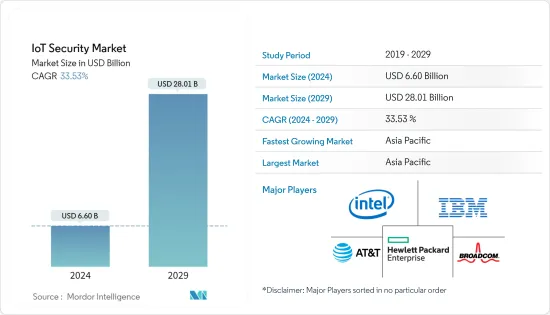
物联网安全市场规模预计到2024年将达到66亿美元,预计2029年将达到280.1亿美元,在预测期内(2024-2029年)复合年增长率为33.53%。
新的应用程式和经营模式,加上装置成本的下降,正在推动物连网的采用率,进而影响连网型设备的数量,例如联网汽车、机器、仪表、穿戴式装置和家用电器。
主要亮点
- 随着我们越来越依赖连网型设备连网型设备,需要确保它们的安全。据爱立信称,2016 年估计有 4 亿个蜂窝连接的物联网设备,预计到 2022 年将达到 15 亿。这一强劲成长预计将受到业界对部署连网型生态系统的日益关注以及 3GPP蜂巢式物联网技术日益标准化的推动。
- 例如,2019 年,赛门铁克公司宣布推出新服务,使其Cloud Workload Protection (CWP) 解决方案和Amazon 的AMZN GuardDuty 能够为Amazon Web Services (AWS) 工作负载和存储提供自动修復和存储,并提供增强的威胁情报。这项新服务预计将帮助企业应对复杂的安全形势,并使 AWS 客户能够自动化和简化云端安全的关键组件。
- 资料外洩的增加和智慧城市的出现是推动市场的因素之一。
- 然而,缺乏技术纯熟劳工和对物联网安全解决方案重要性认识不足等因素阻碍了市场成长。
物联网安全市场趋势
网路安全可望创最快增速
- 物联网网路是全球企业的主要目标和最关心的问题。网路安全部分涵盖防火墙、伺服器、VPN、IDS、IPS、WIDPS、网关和网路硬体等各个子子区隔。企业中越来越多地采用 BYOD 和物联网,这增加了对企业网路攻击的安全性疑虑。例如,根据 IT Candor 的数据,2018 年全球网路硬体市场规模为 1,810 亿美元。光是企业网路硬体就价值 520 亿美元。
- 根据 IBM X-Force 威胁情报报告,2018 年物联网漏洞数量比五年前报告的数量增加了 5,400%。 2016 年发生的 Mirai 攻击是利用物联网攻击伺服器的一个着名例子。该恶意软体使用殭尸网络,招募超过 150,000 台设备,每秒向供应商的伺服器发送 1TB 的资料。
- 迄今为止,大多数基于物联网的攻击都是以 DDoS 的形式发生的。根据赛门铁克的报告,三种类型的 DDoS 相关恶意软体(LightAidra、Kaiten 和 Mirai)占 2018 年物联网攻击的近 80%。
- 市场上的许多供应商都专注于提供解决网路安全相关问题的解决方案。例如,Palo Alto Networks 透过防火墙提供物联网安全作为整合服务。此功能归功于 Palo Alto Networks 最近收购了 Zingbox。预计各供应商的此类措施将在预测期内减轻网路威胁并推动网路安全领域的市场需求。
亚太地区占最大市场占有率份额
- 亚太地区是物联网采用率最高的地区,这得益于该地区正在建造的智慧城市计划。亚太地区的大规模工业化和行动装置用户数量的增加也表明该地区预计将经历强劲增长。
- 根据思科的 VNI 报告,到 2022 年,该地区的网路用户数量可能达到 26 亿(占人口的 62%),而 2017 年为 17 亿(占人口的 41%)。该地区的连网装置/连线数量预计将从 2017 年的 86 亿增加到 2022 年的 131 亿。然而,根据 FireEye 的报告,与世界其他地区相比,亚太地区成为高阶网路攻击目标的可能性高出 35%。
- 据美国国家资讯通讯技术研究所 (NIICT) 称,针对物联网设备的网路攻击正在显着增加。根据 NICT 的预测,到 2020 年,网路攻击的设备数量可能会达到 300 亿台,而 2015 年为 150 亿台。此类案例促使政府和相关组织实施物联网安全解决方案以减少损害。
- 随着物联网趋势的不断发展,中国的技术创新正在导致中国消费者对智慧家庭市场的需求不断增加。国家智慧家庭核心系统由照明控制系统、安防系统、娱乐系统(音讯)、家电等组成。
物联网安全产业概述
物联网安全市场的竞争是温和的,由在全球市场运营的一些重要市场参与者组成。从市场占有率来看,目前少数参与者占据市场主导地位。然而,随着工业服务安全存取的进步,新参与者正在增加其市场份额,从而扩大其在新兴国家的业务足迹。市场主要企业包括赛门铁克公司、IBM公司、Check Point软体技术有限公司、英特尔公司、惠普企业公司、思科系统公司、Fortinet公司、Trustwave Holdings、泰雷兹集团(Gemalto NV)等。
- 2019 年 9 月 - Trustwave 宣布推出云端基础的网路安全平台,该平台将作为该公司资安管理服务、产品和其他网路安全产品的基础。 Trustwave Fusion 平台专为支援营运型企业拥抱数位转型并应对不断变化的安全环境而建置。
- 2019 年 6 月 - Symantec, Inc. 宣布推出适用于 Symantec Cloud Workload Protection (CWP) 解决方案和 Amazon Guard Duty 的新服务,为 AWS 工作负载和储存提供自动修復和增强的威胁情报。这项新服务可协助企业应对复杂的安全形势,并使 AWS 客户能够自动化和简化云端安全的关键元件。
其他福利
- Excel 格式的市场预测 (ME) 表
- 3 个月分析师支持
目录
第一章简介
- 调查先决条件
- 调查范围
第二章调查方法
第三章执行摘要
第四章市场动态
- 市场概况
- 市场促进因素与市场约束因素介绍
- 市场驱动因素
- 资料外洩增加
- 智慧城市的出现
- 市场限制因素
- 设备的复杂性不断增加,加上缺乏普遍的立法
- 产业价值链分析
- 产业吸引力-波特五力分析
- 买家/消费者的议价能力
- 供应商的议价能力
- 新进入者的威胁
- 替代品的威胁
- 竞争公司之间敌对关係的强度
第五章市场区隔
- 按安全类型
- 网路安全
- 端点安全
- 按解决方案
- 软体
- 按服务
- 按最终用户产业
- 车
- 卫生保健
- 政府机关
- 製造业
- 能源/电力
- 零售
- BFSI
- 其他最终用户产业
- 地区
- 北美洲
- 美国
- 加拿大
- 欧洲
- 英国
- 德国
- 法国
- 其他欧洲国家
- 亚太地区
- 中国
- 日本
- 印度
- 韩国
- 其他亚太地区
- 拉丁美洲
- 墨西哥
- 巴西
- 其他拉丁美洲
- 中东/非洲
- 阿拉伯聯合大公国
- 沙乌地阿拉伯
- 其他中东和非洲
- 北美洲
第六章 竞争形势
- 公司简介
- Broadcom Inc.(Symantec Corporation)
- IBM Corporation
- Check Point Software Technologies Ltd.
- Intel Corporation
- Hewlett Packard Enterprise Co.
- Cisco Systems Inc.
- Fortinet Inc.
- Trustwave Holdings
- Thales Group(Gemalto NV)
- AT&T Inc.
- Palo Alto Networks Inc.
第七章 投资分析
第八章 市场机会及未来趋势
The IoT Security Market size is estimated at USD 6.60 billion in 2024, and is expected to reach USD 28.01 billion by 2029, growing at a CAGR of 33.53% during the forecast period (2024-2029).

The emerging applications and business models, coupled with the falling device costs, have been driving the adoption rate of IoT, which is, consequently, influencing the number of connected devices, such asconnected cars, machines, meters, wearable, and consumer electronics.
Key Highlights
- Increasing dependency on the connected devices is creating the need to keep the connected device secure. According to Ericsson, it is estimated that nearly 400 million IoT devices, with cellular connections in 2016, are projected to reach 1.5 billion by 2022. This robust growth is expected to be driven by the increased industry focus on deploying a connected ecosystem and the standardization of 3GPP cellular IoT technologies.
- In 2019, for instance, Symantec Corp. announced a new service that enables its Cloud Workload Protection (CWP) solution and AMZN GuardDuty from Amazon, to provide automated remediation and enhanced threat intelligence for Amazon Web Services (AWS) workloads and storage. This new service is anticipated to help enterprises to navigate the complex security landscape, allowing AWS customers to automate and streamline critical components of cloud security.
- Increasing number data breaches, emergence of smart cities, are some of the factors driving the market.
- .However, factors, such as the dearth of skilled workforce and less awareness about the importance of the IoT security solutions hinder the market growth.
IoT Security Market Trends
Network Security Is Expected to Witness the Fastest Growth Rate
- IoT networks are the prominent targets and the primary concern for enterprises across the world. The network security segment covers various subsegments, such as firewalls, servers, VPN, IDS, IPS, WIDPS, gateway, and network hardware. The growing trend of adopting BYOD and IoTs in enterprises is increasing the security concerns of attacks on enterprise networks. For instance, according to IT Candor, the size of the global network hardware market during fiscal 2018 was valued at USD 181 billion. Enterprise network hardware alone was valued at USD 52 billion.
- According to the IBM X-Force threat intelligence report, in 2018 it was recorded an increase of 5,400% in the number of IoT vulnerabilities over the number reported just five years earlier. Mirai attack, back in 2016, is a prominent example of using IoT to attack servers. The malware used botnet, which enlisted over 150,000 devices to send 1TB of data per second at the vendor's servers.
- To date, the majority of the IoT based attacks have occurred in DDoS form. According to Symantec's report, three kinds of DDoS associated malware, such as LightAidra, Kaiten, and Mirai, collectively accounted for nearly 80% of the 2018 year's IoT attacks.
- Many vendors in the market are emphasizing on providing solutions specific to tackle issues related to network security. For instance, Palo Alto Networks is delivering IoT security as an integrated service through the firewall; the capability was due to the recent acquisition of Zingbox by Palo Alto Networks.Such initiatives by various vendors are expected to mitigate the network threats over the forecast period and drive the market demand for the network security segment.
Asia-Pacific Occupies The Largest Market Share
- Asia-Pacific is the most prominent region for the adoption of IoT, owing to smart city projects being built in the region. The massive industrialization and the rising number of mobile device users in Asia-Pacific also indicate that the region is expected to witness significant growth.
- According to the Cisco VNI report, by 2022, the region may have 2.6 billion internet users (62% of the population), up from 1.7 billion (41% of the population) in 2017. The region is also estimated to have 13.1 billion networked devices/connections by 2022, up from 8.6 billion in 2017. Asia-Pacific, however, is 35% more likely to be targeted by advanced cyber attacks when compared to the world, according to a report by FireEye.
- According to the National Institute of Information and Communication Technology (NIICT), there has been a significant increase in the number of cyberattacks to IoT Devices. NICT predicts that the number of cyberattacks may reach 30 billion devices by 2020, when compared to 15 billion devices in 2015. Such instances are propelling the government and the related organizations to deploy IoT security solutions to mitigate the damages.
- With a rising trend toward IoT, China's technological innovation has led to increasing demand in the smart home market from Chinese consumers. The country's central smart home systems consist of lighting control systems, security systems, entertainment systems (audio and video), home appliances, and others.
IoT Security Industry Overview
The IoT Securitymarket is moderately competitive and consists of a few significant market players operating across the globalmarket. In terms of market share, some of theplayers currently dominate the market. However, with the advancement in the security accessacross the industrialservices, new players are increasing their market presence thereby expanding their business footprint across the emerging economies. Some of the key players in the market areSymantec Corporation, IBM Corporation, Check Point Software Technologies Ltd.,Intel Corporation,Hewlett Packard Enterprise Company,Cisco Systems Inc.,Fortinet Inc.,Trustwave Holdings,Thales Group (Gemalto NV), among others.
- Sept 2019-Trustwave announced a cloud-based cybersecurity platform that serves as the foundation for the company's managed security services, products and other cybersecurity offerings. The Trustwave Fusion platform is purpose-built to meet the enterprise, where it is involved in operations as it embraces digital transformation and contend with a continuously evolving security landscape.
- June 2019 -Symantec Corp.announced a new service for Symantec's Cloud Workload Protection (CWP) solution and Amazon Guard Duty to provide automated remediation and enhanced threat intelligence for AWS workloads and storage. This new service will help enterprises to navigate the complex security landscape, allowing AWS customers to automate and streamline key components of cloud security.
Additional Benefits:
- The market estimate (ME) sheet in Excel format
- 3 months of analyst support
TABLE OF CONTENTS
1 INTRODUCTION
- 1.1 Study Assumptions
- 1.2 Scope of the Study
2 RESEARCH METHODOLOGY
3 EXECUTIVE SUMMARY
4 MARKET DYNAMICS
- 4.1 Market Overview
- 4.2 Introduction to Market Drivers and Restraints
- 4.3 Market Drivers
- 4.3.1 Increasing Number of Data Breaches
- 4.3.2 Emergence of Smart Cities
- 4.4 Market Restraints
- 4.4.1 Growing Complexity among Devices, Coupled with the Lack of Ubiquitous Legislation
- 4.5 Industry Value Chain Analysis
- 4.6 Industry Attractiveness - Porter's Five Force Analysis
- 4.6.1 Bargaining Power of Buyers/Consumers
- 4.6.2 Bargaining Power of Suppliers
- 4.6.3 Threat of New Entrants
- 4.6.4 Threat of Substitute Products
- 4.6.5 Intensity of Competitive Rivalry
5 MARKET SEGMENTATION
- 5.1 By Type of Security
- 5.1.1 Network Security
- 5.1.2 End-point Security
- 5.2 By Solution
- 5.2.1 Software
- 5.2.2 Services
- 5.3 By End-user Industry
- 5.3.1 Automotive
- 5.3.2 Healthcare
- 5.3.3 Government
- 5.3.4 Manufacturing
- 5.3.5 Energy & power
- 5.3.6 Retail
- 5.3.7 BFSI
- 5.3.8 Others End-user Industries
- 5.4 Geography
- 5.4.1 North America
- 5.4.1.1 United States
- 5.4.1.2 Canada
- 5.4.2 Europe
- 5.4.2.1 United Kingdom
- 5.4.2.2 Germany
- 5.4.2.3 France
- 5.4.2.4 Rest of Europe
- 5.4.3 Asia-Pacific
- 5.4.3.1 China
- 5.4.3.2 Japan
- 5.4.3.3 India
- 5.4.3.4 South Korea
- 5.4.3.5 Rest of Asia-Pacific
- 5.4.4 Latin America
- 5.4.4.1 Mexico
- 5.4.4.2 Brazil
- 5.4.4.3 Rest of Latin America
- 5.4.5 Middle East & Africa
- 5.4.5.1 United Arab Emirates
- 5.4.5.2 Saudi Arabia
- 5.4.5.3 Rest of Middle-East & Africa
- 5.4.1 North America
6 COMPETITIVE LANDSCAPE
- 6.1 Company Profiles
- 6.1.1 Broadcom Inc. (Symantec Corporation)
- 6.1.2 IBM Corporation
- 6.1.3 Check Point Software Technologies Ltd.
- 6.1.4 Intel Corporation
- 6.1.5 Hewlett Packard Enterprise Co.
- 6.1.6 Cisco Systems Inc.
- 6.1.7 Fortinet Inc.
- 6.1.8 Trustwave Holdings
- 6.1.9 Thales Group (Gemalto NV)
- 6.1.10 AT&T Inc.
- 6.1.11 Palo Alto Networks Inc.








