 |
市场调查报告书
商品编码
1433840
安全编配:市场占有率分析、产业趋势/统计、成长预测(2024-2029)Security Orchestration - Market Share Analysis, Industry Trends & Statistics, Growth Forecasts (2024 - 2029) |
||||||
※ 本网页内容可能与最新版本有所差异。详细情况请与我们联繫。
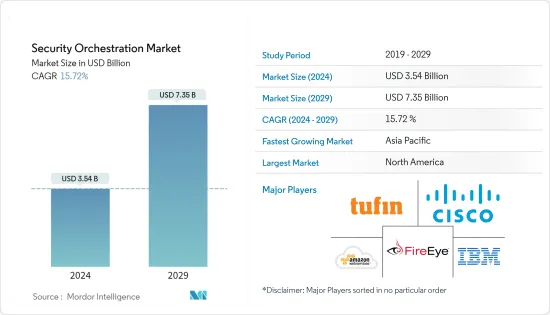
全球安全编配市场规模预计将在 2024 年达到 35.4 亿美元,并在 2024-2029 年预测期内以 15.72% 的复合年增长率增长,到 2029 年将达到 73.5 亿美元。
跨组织部署安全编配可以协助管理安全警报并防止严重的网路攻击。随着网路攻击变得更加复杂,安全供应商正在开发更好的编配平台,以提供主动且全面的安全架构来处理关键业务应用程式。
主要亮点
- 影响中小型企业的BYOD趋势急剧增加,以及云端基础的解决方案的快速部署和发展,导致安全漏洞和安全事件的增加,使组织难以应用安全编配.它正在加速。
- 随着越来越多的公司采用安全编配平台来监控和管理电脑网路流量,网路取证的应用预计将增加并推动市场需求。
- 随着连网型设备的普及以及各种 IT 服务和解决方案的日益采用,每天产生的资料量进一步增加,导致需要有效管理和遏制的潜在漏洞数量增加。范围是巨大的。
- 这些解决方案还支援主动策略执行和审核合规性报告,包括 ITIL、PCI、健康保险流通和责任法案 (HIPAA)、萨班斯-奥克斯利法案 (SOX) 和 Gramm-Leach-Bliley 法案。遵守审核合规要求。这些因素正在推动市场成长。
主要市场趋势
IT通讯产业预计将录得显着成长
- IT通讯业提供广泛的全球和国内服务来连接数百万客户。这种多样化的生态系统严重依赖基础设施、网路和资料库来执行其所有业务,因此经常容易受到网路攻击。
- 电讯提供者通常储存客户的个人信息,例如姓名、地址和财务资料。敏感资料是相关人员和网路犯罪分子窃取资金、勒索客户或发动进一步攻击的主要目标。这要求业界更多地关注现代解决方案、正确的工具、训练有素的人员以及立即回应威胁的能力。
- SOAR 工具可协助 IT 团队定义、标准化和自动化组织的事件回应活动。大多数 IT 组织使用这些工具来自动化保全行动和流程、回应事件以及管理漏洞和威胁。此外,安全编配还可以缩短参与企业安全的 IT 专业人员的威胁回应和解决时间。
- 透过云端和物联网增强资料连接已成为 IT 部门面临的主要挑战,而安全性已成为整个行业组织保护自己免受资料外洩的首要任务。此外,COVID-19大流行导致资讯和通讯技术公司重新考虑其业务流程,以便在整个疫情期间为客户提供可靠的服务,特别是在通讯网路需求倍增的情况下,迫切需要提高网路效能。因此,企业正在采用这些安全编配解决方案来提高市场成长率。
北美占最大市场占有率
- 北美在安全编配市场上占据主导地位,这要归功于该地区许多着名的安全编配供应商,例如IBM公司、DXC科技公司、思科系统公司和FireEye公司。最终用户产业的成长、政府在关键基础设施上的支出、建立的研发中心以及对先进安全技术的需求等因素预计将推动该地区的市场成长。
- 该地区网路攻击的增加进一步促进了市场的成长。 2021年,美国国家安全局(NSA)、网路安全和基础设施安全局(CISA)、联邦调查局(FBI)分别负责国防工业基地、紧急服务、食品和农业以及政府等16个机构。美国关键基础设施部门。包括设施和资讯技术部门在内的14 个部门报告称目睹了涉及勒索软体的事件。
- 此外,组织承认网路复杂性在过去几年中有所增加,并将在未来五年内继续增加。这增加了对网路安全的需求,以防止骇客和网路攻击保护产业流程,而这正是安全编配发挥作用的地方。
- 此外,该地区正在见证混合和多重云端环境中采用的新云端工具的爆炸性增长,而现有云端平台也在不断调整以适应新的混合现实。
竞争形势
安全编配市场竞争非常激烈,有几家主要公司进入该市场。从市场占有率来看,目前该市场由少数大公司主导。此外,随着云端网路领域的出现,大多数公司都在增加在SOAR市场的占有率,并在后续市场上开拓客户。此外,公司正在选择不同的策略,例如协作和解决方案推出,以促进市场成长率。
- 2023 年 3 月 - IBM 和 Cohesity 建立了新的合作伙伴关係,以满足组织在混合云端环境中提高资料安全性和可靠性的基本需求。 IBM Storage Defender 旨在透过单一视窗跨各种储存平台使用 AI 和事件监控,以保护组织的资料层免受勒索软体、人为错误和攻击等威胁。
- 2023 年 2 月 - Morado Intelligence 是一家威胁情报公司,支援客户对网路威胁情报和保全行动最佳化的需求;CyberFusion 为企业和 MSSP/MDR 提供低程式码 SOAR 和威胁情报自动化 Cyware,为建置ISAC 和ISAO 的威胁情报共用解决方案已建立合作伙伴关係。此次合作的主要目标是使用 Cyware 的高级 TIP 和 SOAR 模组实现威胁资料的有效摄取、丰富、分析和回应,从而更轻鬆地满足 Morado 强大的客户组合需求。仅此而已。
其他福利:
- Excel 格式的市场预测 (ME) 表
- 3 个月分析师支持
目录
第一章 简介
- 调查先决条件
- 调查范围
第二章调查方法
第三章执行摘要
第四章市场洞察
- 市场概况
- 产业吸引力-波特五力分析
- 新进入者的威胁
- 买家/消费者的议价能力
- 供应商的议价能力
- 替代品的威胁
- 竞争公司之间敌对关係的强度
- COVID-19 对市场的影响
第五章市场动态
- 市场驱动因素
- 保全行动自动化以实现无缝工作流程的趋势不断增强
- 需要个人化的网路安全技术来解决网路复杂性
- 市场限制因素
- 专家缺乏认识
- 技术简介
第六章市场区隔
- 类型
- 软体
- 服务
- 最终用户产业
- BFSI
- 资讯科技通讯
- 政府国防
- 电子商务
- 其他最终用户产业
- 地区
- 北美洲
- 美国
- 加拿大
- 欧洲
- 英国
- 法国
- 德国
- 欧洲其他地区
- 亚太地区
- 中国
- 日本
- 澳洲
- 其他亚太地区
- 其他地区
- 拉丁美洲
- 中东/非洲
- 北美洲
第七章 竞争形势
- 公司简介
- IBM Corporation
- Tufin Software Technologies Ltd
- DXC Technology Company
- Cisco System Inc.
- Swimlane LLC
- RSA Security LLC
- FireEye Inc.
- DFLabs SpA
- Palo Alto Networks Inc.
- Siemplify Ltd
- Accenture PLC
- Amazon Web Services Inc.
- Cyberbit Ltd
- Forescout Technologies Inc.
第八章投资分析
第九章 市场机会及未来趋势
The Security Orchestration Market size is estimated at USD 3.54 billion in 2024, and is expected to reach USD 7.35 billion by 2029, growing at a CAGR of 15.72% during the forecast period (2024-2029).

The implementation of security orchestration across various organizations can help manage security alerts and prevent severe cyber-attacks. As the sophistication level in cyber-attacks is increasing, security vendors are trying to develop better orchestration platforms to provide proactive and holistic security architecture to handle critical business applications.
Key Highlights
- An increase in the security breaches and occurrences due to dramatic growth in the BYOD trend affecting SMEs, along with the rapid deployment and development of cloud-based solutions, is fueling the application of security orchestration among various organizations.
- A rise in the application of network forensics is expected to drive the market demand, as a growing number of companies are adopting the security orchestration platform to monitor and manage their computer network traffic.
- Growing adoption of various IT enabled services and solutions, due to the growing popularity of connected devices, has further boosted the amount of data generated daily, subsequently resulting in a vast scope for potential vulnerabilities that need effective management and containment.
- Implementation of these solutions has also enabled improved adherence to audit and compliance requirements easily, with proactive policy enforcement and audit and compliance reports, such as ITIL, PCI, Health Insurance Portability and Accountability Act (HIPAA), Sarbanes-Oxley Act (SOX), and Gramm-Leach-Bliley Act. These factors have been aiding the growth of the market.
Key Market Trends
IT and Telecommunication Sector is Projected to Record Significant Growth
- The IT and telecommunication industry offers a wide range of global and domestic services for connecting millions of customers. This diverse ecosystem is more prone to frequent cyber attacks, as they are highly dependent on their infrastructure, network, and databases to perform any operation.
- Telecom organizations typically store customers' personal information, such as names, addresses, and financial data. Information-sensitive data is a compelling target for insiders or cyber-criminals to steal money, blackmail customers, or launch further attacks. Therefore, the industry demands a greater focus on updated solutions, the right tools, highly trained personnel, and the ability to respond to threats immediately.
- SOAR tools aid IT teams in defining, standardizing, and automating organizations' incident response activities. Most IT organizations use these tools to automate security operations and processes, respond to incidents, and manage vulnerabilities and threats. Moreover, security orchestration reduces the threat response and resolution time for IT professionals working in enterprise security.
- With the increased data connectivity with the cloud as well as IoT taking center stage in the IT sector, security has been a top priority for the all the organizations in the industry to protect themselves from the data breaches. Further, COVID-19 pandemic has led Information and communication technology organizations to rethink their business processes and improve their network performance to provide their customers with reliable services throughout the pandemic, specially when the demand for telecom networks has doubled. Thus, companies are adopting these security orchestration solutions thereby driving the market growth rate.
North America Accounts for the Largest Market Share
- North America dominates the security orchestration market, owing to many prominent security orchestration vendors across the region, such as IBM Corporation, DXC Technology Company, Cisco System Inc., FireEye Inc., etc. Factors such as the growing end-user industries, government expenditure toward critical infrastructure, well-established R&D centers, and the demand for advanced security technology across the region are expected to drive market growth.
- The growing number of cyber attacks in the region further contributes to the market growth. In 2021, The National Security Agency (NSA), the Cybersecurity and Infrastructure Security Agency (CISA), and the Federal Bureau of Investigation (FBI) reportedly witnessed occurrences involving ransomware against 14 of the 16 critical infrastructure sectors in the United States, including the Defense Industrial Base, Emergency Services, Food and Agriculture, Government Facilities, and Information Technology Sectors.
- Also, various organizations have admitted that network complexity has increased over the past few years and will continue to increase over the next five years. Therefore, there is a high need for network security to stop hacking and cyber-attacks from securing industrial processes, and that is where security orchestration plays its part.
- Further, the region is witnessing an explosion of new cloud tools adopted for hybrid and multicloud environments, while at the same time, established cloud platforms are pivoting to fit into the new hybrid reality.
Competitive Landscape
The security orchestration market is highly competitive and consists of several major players. In terms of market share, few major players currently dominate the market. Moreover, due to the emergence of the cloud network segment, most companies are increasing their SOAR market presence, tapping customers across the subsequent markets. Further, the players are opting for various strategies, such as collaborations and solution launches, thereby contributing to the market growth rate. For instance:
- March 2023-IBM and Cohesity have formed a new partnership to meet organizations' essential need for better data security and reliability in hybrid cloud settings. IBM Storage Defender is being developed to use AI and event monitoring across various storage platforms through one single window to assist in safeguarding organizations' data layer from threats, including ransomware, human error, and attack.
- February 2023-Morado Intelligence, a threat intelligence company that assists clients with their needs for cyber threat intelligence and security operations optimisation, and Cyware, a provider of the technology platform to build low-code SOAR and threat intel automation powered Cyber Fusion Centres for businesses and MSSPs/MDRs, as well as threat intelligence sharing solutions for ISACs and ISAOs, have formed a partnership. The partnership's primary objective is to make it easier for Morado's robust client portfolio to use Cyware's advanced TIP & SOAR modules to effectively ingest, enhance, analyze, and respond on threat data.
Additional Benefits:
- The market estimate (ME) sheet in Excel format
- 3 months of analyst support
TABLE OF CONTENTS
1 INTRODUCTION
- 1.1 Study Assumptions
- 1.2 Scope of the Study
2 RESEARCH METHODOLOGY
3 EXECUTIVE SUMMARY
4 MARKET INSIGHTS
- 4.1 Market Overview
- 4.2 Industry Attractiveness - Porter's Five Forces Analysis
- 4.2.1 Threat of New Entrants
- 4.2.2 Bargaining Power of Buyers/Consumers
- 4.2.3 Bargaining Power of Suppliers
- 4.2.4 Threat of Substitute Products
- 4.2.5 Intensity of Competitive Rivalry
- 4.3 Impact of COVID-19 on the market
5 Market Dynamics
- 5.1 Market Drivers
- 5.1.1 Rising Trend of Automated Security Operation for Seamless Workflow
- 5.1.2 Need of Disparate Cybersecurity Technologies to Handle Network Complexity
- 5.2 Market Restraints
- 5.2.1 Lack of Awareness among Professionals
- 5.3 Technology Snapshot
6 MARKET SEGMENTATION
- 6.1 Type
- 6.1.1 Software
- 6.1.2 Services
- 6.2 End-user Industry
- 6.2.1 BFSI
- 6.2.2 IT and Telecommunication
- 6.2.3 Government and Defence
- 6.2.4 E-commerce
- 6.2.5 Other End-user Industries
- 6.3 Geography
- 6.3.1 North America
- 6.3.1.1 United States
- 6.3.1.2 Canada
- 6.3.2 Europe
- 6.3.2.1 United Kingdom
- 6.3.2.2 France
- 6.3.2.3 Germany
- 6.3.2.4 Rest of Europe
- 6.3.3 Asia-Pacific
- 6.3.3.1 China
- 6.3.3.2 Japan
- 6.3.3.3 Australia
- 6.3.3.4 Rest of Asia-Pacific
- 6.3.4 Rest of the World
- 6.3.4.1 Latin America
- 6.3.4.2 Middle-East & Africa
- 6.3.1 North America
7 COMPETITIVE LANDSCAPE
- 7.1 Company Profiles
- 7.1.1 IBM Corporation
- 7.1.2 Tufin Software Technologies Ltd
- 7.1.3 DXC Technology Company
- 7.1.4 Cisco System Inc.
- 7.1.5 Swimlane LLC
- 7.1.6 RSA Security LLC
- 7.1.7 FireEye Inc.
- 7.1.8 DFLabs SpA
- 7.1.9 Palo Alto Networks Inc.
- 7.1.10 Siemplify Ltd
- 7.1.11 Accenture PLC
- 7.1.12 Amazon Web Services Inc.
- 7.1.13 Cyberbit Ltd
- 7.1.14 Forescout Technologies Inc.













