 |
市场调查报告书
商品编码
1435977
深层封包检测与处理:市场占有率分析、产业趋势与统计、成长预测(2024-2029)Deep Packet Inspection and Processing - Market Share Analysis, Industry Trends & Statistics, Growth Forecasts (2024 - 2029) |
||||||
※ 本网页内容可能与最新版本有所差异。详细情况请与我们联繫。
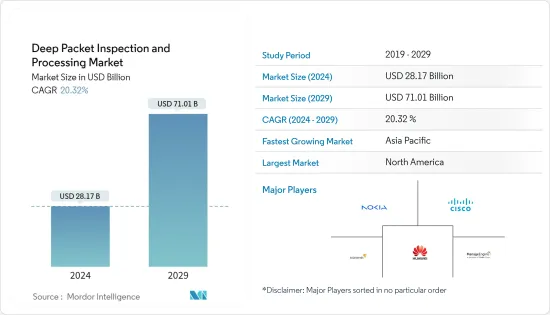
深层封包检测和处理市场规模预计到 2024 年为 281.7 亿美元,在预测期内(2024-2029 年)预计到 2029 年将达到 710.1 亿美元,复合年增长率为 20.32%。
DPI 结合了签章匹配技术和资料分析演算法来识别对通讯流的影响。基于硬体的中间盒在电脑网路中很普及,但它们的部署和管理成本通常很高。
主要亮点
- 在最近的趋势中,研究人员提案了两种实用的方法来实现云端基础的DPI 中间盒来解决这些问题。外包的 DPI 中间盒对加密流量执行有效负载检查,同时维护通讯资料和检查规则的隐私。
- 云端采用、远端工作、BYOD 和 SaaS 应用程式等技术的普及增加了可用于网路攻击的途径数量。应用程式已成为网路犯罪分子的有吸引力的目标,但确保、保护和控制连接它们的网路是网路安全供应商面临的主要挑战。
- 相较之下,欧盟的 DPI 的使用方式完全不同。它被用作打击贩毒和儿童色情製品系统的一部分。一旦欧盟明确了自己的意图,它就迅速实施了管理资料使用的法律。这种考虑属于一般资料保护规范 (GDPR),这是保护欧盟公民及其敏感资料的综合法律。
- 随着行动装置带来的全球 IP 流量的成长,物联网 (IoT) 和云端运算的出现需要仔细关注和强大的工具来确保企业网路的安全运作。据思科系统公司称,到 2021 年,全球 IP资料流量预计将达到每月 278,108 Petabyte。
- 许多云端服务都可以透过互联网访问,因此提高系统可存取性是云端迁移的关键驱动力。然而,云端伺服器和应用程式经常受到来自世界各地的各种方法的攻击。深层封包检测和处理对于阻止不良流量同时让良好流量通过而不会造成太多中断至关重要。超越这个基于边界的防御层也很重要。有多种方法可以在公共云端环境中成功部署基于深层封包检测的安全控制,包括使用为此目的而建置的供应商解决方案。另一个产品系列是基于在客户端点上运行的代理程式。
- 此外,攻击者开始利用资讯激增,提高大众对感染疾病-19 相关新闻的警觉性。网路钓鱼、垃圾邮件宣传活动和恶意网站/网域显着增加。为了减少 VPN 的负载并降低建立恶意软体命令与控制 (C2) 通道的可能性,F-Secure 建议在 VPN 集中器和其他网路週边设备上使用深层封包检测。建议。使用此类支架时,某些消耗大量频宽的线上服务(例如串流媒体和各种游戏服务)可能会被阻止。我们还建议您仅允许在已知和核准的连接埠上通讯,例如 HTTPS。大流行显着提高了采用率。
深层封包检测和处理市场趋势
随着企业网路流量的增加,软体解决方案经历了显着成长
- 近年来,DPI(深层封包检测)软体已发展成为解决新网路挑战的强大工具,并在当今的网路和网路基础设施中发挥核心作用。由于大多数网路流量现在都已加密,因此可靠的 DPI 软体引擎需要一个复杂的套件来对流量进行分类。
- DPI 是基于包含从资料包的资料部分提取的资讯的签章资料库来识别流量并对其进行分类,从而比仅基于标头资讯的分类具有更多的控制权。P2P(P2P) 流量等应用程式为宽频服务供应商带来了越来越多的问题。
- P2P 流量通常由提供檔案共用的应用程式使用。 P2P 经常传输大型媒体文件,增加了流量负载并需要额外的网路容量。 DPI 允许通讯业者超额销售可用频宽,同时防止网路拥塞并将频宽公平地分配给所有用户。
- 网路必须能够解析内容、组装足够的应用讯息并识别已知的流量使用情况和模式。 DPI 功能分为四类:通讯协定分析/应用程式感知、反恶意软体/防毒、入侵侦测和防御 (IDS/IPS) 以及 URL 过滤。
- 根据 Enea AB 的一项研究,70% 的受访者(高科技产品经理)要求对企业和物联网/工业网路中的连接设备进行分类。此外,加密的使用增加以及严格的 TLS 1.3 安全通讯协定(5G 的强制要求)的采用威胁到许多供应商的关键流量的可见性。这需要深层封包检查和处理来支援未来的市场成长。
- 此外,大多数供应商表示拥有或正在开发云端解决方案,其中一半计划提供安全存取服务边缘 (SASE) 解决方案,将安全性和网路整合到云端基础的服务中。随着市场的成长,这就需要使用 DPI 软体。
北美占据主要市场占有率
- 北美帐户占据了最大份额,因为该地区的成长是由互联网普及不断提高以及跨行业云端基础和物联网应用程式的增加所推动的。此外,北美因 DPI 采用而发生的安全漏洞数量居世界首位。
- 网路犯罪分子越来越多地以企业和医疗保健组织为目标,以获取受害者的资料。个人资料经常用于社交工程攻击,与传统的网路攻击相比,社会工程攻击更有可能欺骗受害者。美国记录的资料外洩总合中有 79% 发生在商业和医疗保健领域(资料来源:身分盗窃资源中心)。
- HIPAA 隐私规则制定了保护受保护健康资讯 (PHI)、个人健康记录和其他个人健康资讯的国家标准。这遵循了引入运行高级深层封包检测(DPI) 逻辑的伺服器以从原始流量中识别和提取相关资料区段的趋势。
- 以国家/地区来看,美国的资料外洩成本仍然高于其他国家。国内资料外洩造成的损失平均为 864 万美元,几乎是全球平均值的两倍,而且这一金额在过去 14 年里成长了 130% 以上。
- 此 DPI 技术可在 macOS 上使用,并内建于 Endpoint Protector 用户端中,以拦截透过 Web 浏览器檔案传输。此类功能可以监控文件目标以及将特定 URL 列入白名单和黑名单。白名单仅允许将檔案传输到特定网域和 URL,而黑名单选项可让您封锁对特定网站的存取。
深层封包检测和处理行业概述
随着企业不断创新新的硬体和软体解决方案,深层封包检测和处理市场变得支离破碎,并且新进入者不断加入该市场以满足激烈的竞争。深层封包检测和处理市场正在出现多项创新,包括新一代防火墙 (NGFW) 的开发,该防火墙可以检查 OSI 模型中多达七个应用层的网路封包。在这种情况下,参与者之间会展开激烈的竞争,以提供独特的解决方案。主要公司包括诺基亚(阿尔卡特朗讯)、SolarWinds Worldwide, LLC、思科系统公司和华为技术有限公司。市场的最新发展包括:
2023 年 2 月,思科宣布计画收购以色列云端安全企业 Lightspin。思科和 Lightspin 将能够实现他们的通用目标,即透过提供从建置到运行的端到端安全性和可观察性,帮助客户实现云端基础设施现代化。
2022 年 8 月,SafeRide Technologies 宣布发布新的入侵侦测和防御软体 (IDPS),以保护汽车乙太网路免受网路攻击。新解决方案已整合到 SafeRide 的 vSentry Edge AI 软体中。 vSentry Edge AI 监控来自多个域的 CAN 和乙太网路通讯,并执行深度资料包检查和有效负载分析。
其他福利
- Excel 格式的市场预测 (ME) 表
- 3 个月分析师支持
目录
第一章简介
- 研究假设和市场定义
- 调查范围
第二章调查方法
第三章执行摘要
第四章市场动态
- 市场概况
- 产业价值链分析
- 产业吸引力-波特五力分析
- 买方议价能力
- 供应商的议价能力
- 新进入者的威胁
- 替代产品的威胁
- 竞争公司之间的敌意强度
- 监管影响
- 评估 COVID-19 对市场的影响
- 市场驱动因素
- 更多采用监管和资料保护法
- 先进采用云端基础的安全技术
- 市场限制因素
- DPI 让现有防火墙和其他安全相关软体变得更加复杂和笨重
第五章市场区隔
- 解决方案
- 硬体
- 软体
- 介绍
- 本地
- 云
- 最终用户
- 通讯和资讯技术
- BFSI
- 卫生保健
- 零售
- 其他最终用户
- 地区
- 北美洲
- 美国
- 加拿大
- 欧洲
- 德国
- 英国
- 法国
- 其他欧洲国家
- 亚太地区
- 中国
- 日本
- 澳洲
- 其他亚太地区
- 拉丁美洲
- 中东和非洲
- 北美洲
第六章 竞争形势
- 公司简介
- Nokia Corporation(Alcatel Lucent)
- Allot Ltd.
- Bivio Networks, Inc.
- Huawei Technologies Co., Ltd.
- Enea AB(Qosmos SA)
- WiseSpot Company Limited
- SolarWinds Worldwide, LLC.
- NetFort Technologies Limited(Rapid7)
- Netify
- AppNeta, Inc.
- ManageEngine(Zoho Corporation)
- Cisco Systems, Inc.
- ipoque GmbH
第七章 投资分析
第八章市场机会与未来趋势
The Deep Packet Inspection and Processing Market size is estimated at USD 28.17 billion in 2024, and is expected to reach USD 71.01 billion by 2029, growing at a CAGR of 20.32% during the forecast period (2024-2029).

DPI combines signature matching technology with a data analysis algorithm to determine a communication stream impact. Hardware-based middleboxes are prevalent in computer networks, which usually incur high deployment and management expenses.
Key Highlights
- A recent trend addresses those problems where researchers propose two practical approaches to implement a cloud-based DPI middlebox. The outsourced DPI middlebox performs payload inspection over encrypted traffic while preserving the privacy of both communication data and inspection rules.
- The proliferation of technologies, such as cloud deployment, remote working, BYOD, SaaS applications, etc., are increasing the paths available to cyberattacks. Applications have become inviting targets for cybercriminals, but securing, protecting, and controlling the networks that connect them is a huge challenge for network security providers.
- In contrast, DPI in the European Union is used very differently. It is used as part of mechanisms to clamp down on drug trafficking and child pornography. When the EU established its intent, they were quick to enforce laws that controlled the use of data. The consideration falls under the General Data Protection Regulation (GDPR), a comprehensive set of laws protecting EU citizens and their sensitive data.
- With the growing global IP traffic augmented by mobile devices, the emergence of the Internet of Things (IoT) and cloud computing require close attention and powerful tools to ensure secure operations on an enterprise network. According to CISCO Systems, the global IP data traffic is expected to reach 278,108 petabytes per month by 2021.
- Many cloud services are accessible to the entire internet, which means improved system accessibility is an important driver for cloud migrations. However, cloud servers and applications are regularly attacked using various methods from anywhere globally. Deep packet inspection and processing are essential to keep the bad traffic out while letting the good traffic through without too much interruption. It is also important to look beyond this perimeter-based defense layer. There are several approaches to successfully deploying a security control based on Deep Packet Inspection within a public cloud environment, such as using the vendor solutions already built for this exact purpose, and another product range is based on agents running on customer endpoints.
- Moreover, attackers started exploiting the burst of information and heightened public alertness for COVID-19-related news. Phishing, spam campaigns, and malicious websites/domains significantly increased. To relieve the load on VPNs and mitigate the chances of successful command and control (C2) channels for malware to be established, F-Secure recommends using deep packet inspection on VPN concentrators and other network perimeter devices. Certain bandwidth-heavy online services, such as streaming and various gaming services, can be blocked with such a stand. It is also recommended to allow communication on only known and approved ports, such as HTTPS. The pandemic is significantly increasing the adoption rate.
Deep Packet Inspection and Processing Market Trends
Software Solution to Witness Significant Growth With Increasing Enterprise Internet Traffic
- In recent years, DPI (Deep Packet Inspection) software has evolved into a powerful tool to meet new network challenges, playing a central role in today's internet and network infrastructure. As most internet traffic is now encrypted, a reliable DPI software engine needs a tool kit of advanced techniques to classify traffic.
- DPI identifies and classifies traffic based on the signature database that includes information extracted from the data part of a packet, allowing finer control than classification based only on header information. Applications such as peer-to-peer (P2P) traffic provide increasing problems for broadband service providers.
- Typically, P2P traffic is used by applications providing file sharing. Due to its frequently large size of media files being transferred, P2P drives the increasing traffic loads, which requires additional network capacity. DPI allows operators to oversell their available bandwidth while ensuring equitable bandwidth distribution to all users by preventing network congestion.
- The network must be able to parse through content, assemble enough of an application message, and identify traffic usage and patterns based on the information. DPI functions fall into four categories: Protocol analysis/application recognition, Anti-malware/anti-virus, Intrusion Detection and Prevention (IDS/IPS), and URL filtering.
- According to the Enea AB survey, 70 percent of respondents (high-tech product managers) require the classification of connected devices in the enterprise and IoT/industrial networks. And also, the increased use of encryption and the adoption of the stringent TLS 1.3 security protocol (mandatory in 5G) threatens essential traffic visibility for many vendors. This requires Deep packet inspection and processing catering to future market growth.
- Further, most vendors report that they have or are developing cloud solutions, with half planning to offer a Secure Access Service Edge (SASE) solution that integrates security and networking in a cloud-based service. This requires the use of DPI software, which adheres to market growth.
North America Accounts for the Significant Market Share
- North American accounts hold a significant share as the region's growth is driven by the rising internet penetration and increasing adoption of cloud-based and IoT applications across verticals. Moreover, North America tops the world regarding security breach incidents, which caters to DPI adoption.
- Cybercriminals increasingly target businesses and medical institutions to gain the victim's data. The personal data is then often used for socially engineering their attacks, which are more likely to trick the victim when compared to traditional cyber attacks. 79% of the total data breaches recorded in the United States were reported in the business and medical sectors (source: Identity Theft Resource Center).
- The HIPAA Privacy Rule established national standards to safeguard Protected Health Information (PHI), individual medical records, and other personal health information. This is following the trend towards deploying servers executing sophisticated Deep Packet Inspection (DPI) logic to identify and extract relevant data segments from the raw traffic.
- By countries data breaches in the United States continued to be more expensive than those in other nations. Data breaches in the country, on average, cost USD 8.64 million, which is nearly double that of the global average, and this increased by over 130% over the last 14 years.
- This DPI technology, available for macOS and embedded into the Endpoint Protector client, intercepts all file transfers through web browsers. With such a feature now, it is possible to monitor a file's destination and whitelist and blacklist specific URLs. Whitelisting allows file transfers only to specific domains and URLs, while with the blacklisting option, access to specific websites can be blocked.
Deep Packet Inspection and Processing Industry Overview
The deep packet inspection and processing market is fragmented as the players are increasingly innovating new hardware and software solutions, and also new entrants are adding to this market that caters to the significant competition. Several innovations have been witnessed in the deep packet inspection and processing market, including developing Next-Generation Firewalls (NGFWs) that can investigate the network packets up to 7 application layers of the OSI model. Such instances provide intense rivalry among the players to provide unique solutions. Nokia (Alcatel Lucent), SolarWinds Worldwide, LLC, cisco systems, and Huawei Technologies are key players. Recent developments in the market are -
In February 2023, Cisco announced plans to purchase Lightspin, an Israeli cloud security business. Cisco and Lightspin will be able to achieve their mutual goal of assisting customers in modernizing their cloud infrastructures by providing end-to-end security and observability from construction to runtime.
In August 2022, SafeRide Technologies announced the release of new Intrusion Detection and Prevention Software (IDPS) to protect Automotive Ethernet networks against cyberattacks. The new solution was integrated into SafeRide's vSentry Edge AI software. vSentry Edge AI monitored the CAN and Ethernet communications from multiple domains, performing deep packet inspection and payload analysis.
Additional Benefits:
- The market estimate (ME) sheet in Excel format
- 3 months of analyst support
TABLE OF CONTENTS
1 INTRODUCTION
- 1.1 Study Assumptions and Market Definition
- 1.2 Scope of the Study
2 RESEARCH METHODOLOGY
3 EXECUTIVE SUMMARY
4 MARKET DYNAMICS
- 4.1 Market Overview
- 4.2 Industry Value Chain Analysis
- 4.3 Industry Attractiveness - Porter's Five Forces Analysis
- 4.3.1 Bargaining Power of Buyers/Consumers
- 4.3.2 Bargaining Power of Suppliers
- 4.3.3 Threat of New Entrants
- 4.3.4 Threat of Substitute Products
- 4.3.5 Intensity of Competitive Rivalry
- 4.4 Regulatory Implications
- 4.5 Assessment of COVID-19 Impact on the Market
- 4.6 Market Drivers
- 4.6.1 Increasing Adoption of Regulatory and Data Protection Laws
- 4.6.2 High Adoption of Cloud Based Security Technologies
- 4.7 Market Restraints
- 4.7.1 DPI Adds to the Complexity and Unwieldy Nature of Existing Firewalls and Other Security-Related Software
5 MARKET SEGMENTATION
- 5.1 Solution
- 5.1.1 Hardware
- 5.1.2 Software
- 5.2 Deployment
- 5.2.1 On-Premise
- 5.2.2 Cloud
- 5.3 End-User
- 5.3.1 Telecom and IT
- 5.3.2 BFSI
- 5.3.3 Healthcare
- 5.3.4 Retail
- 5.3.5 Other End-Users
- 5.4 Geography
- 5.4.1 North America
- 5.4.1.1 United States
- 5.4.1.2 Canada
- 5.4.2 Europe
- 5.4.2.1 Germany
- 5.4.2.2 United Kingdom
- 5.4.2.3 France
- 5.4.2.4 Rest of Europe
- 5.4.3 Asia-Pacific
- 5.4.3.1 China
- 5.4.3.2 Japan
- 5.4.3.3 Australia
- 5.4.3.4 Rest of Asia-Pacific
- 5.4.4 Latin America
- 5.4.5 Middle East and Africa
- 5.4.1 North America
6 COMPETITIVE LANDSCAPE
- 6.1 Company Profiles
- 6.1.1 Nokia Corporation (Alcatel Lucent)
- 6.1.2 Allot Ltd.
- 6.1.3 Bivio Networks, Inc.
- 6.1.4 Huawei Technologies Co., Ltd.
- 6.1.5 Enea AB (Qosmos SA)
- 6.1.6 WiseSpot Company Limited
- 6.1.7 SolarWinds Worldwide, LLC.
- 6.1.8 NetFort Technologies Limited (Rapid7
- 6.1.9 Netify
- 6.1.10 AppNeta, Inc.
- 6.1.11 ManageEngine (Zoho Corporation)
- 6.1.12 Cisco Systems, Inc.
- 6.1.13 ipoque GmbH








