 |
市场调查报告书
商品编码
1437959
EDR(端点检测与反应):市场占有率分析、产业趋势与统计、成长预测(2024-2029)Endpoint Detection and Response - Market Share Analysis, Industry Trends & Statistics, Growth Forecasts (2024 - 2029) |
||||||
※ 本网页内容可能与最新版本有所差异。详细情况请与我们联繫。
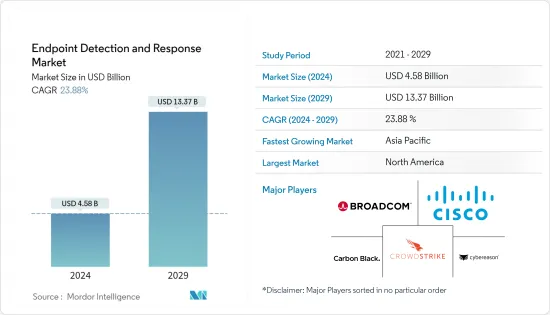
EDR(端点侦测与回应)市场规模预计到 2024 年为 45.8 亿美元,预计到 2029 年将达到 133.7 亿美元,在预测期内(2024-2029 年)将以 23.88% 的复合年增长率成长。
主要亮点
- 企业已经能够透过进阶恶意软体侦测来保护其网路免受常见的网路安全威胁。随着远端工作活动的显着增加,端点侦测和回应 (EDR) 领域的组织因提供安全可靠的端点软体而受到严格审查。
- EDR 工具是能够快速调查并遏制端点威胁并向安全团队发出潜在危险活动警报的技术平台。端点包括员工工作站或笔记型电脑、伺服器、云端系统、智慧型手机或物联网设备。端点资料,例如流程执行、终端通讯和用户端登录,通常由 EDR 系统集中,然后分析资料以检测异常和可疑威胁,并记录有关有害行为的资料。这为安全团队提供了调查和解决问题所需的知识。您也可以在端点上执行手动和自动任务以消除威胁,例如擦拭巾设备和重新映像设备,或将其与网路隔离。
- 透过制定保护 IT 流程和系统安全、保护客户关键资料并遵守政府法规的策略,公共和私人银行机构正在专注于实施最新技术来防止网路攻击。此外,客户期望的提高、技术力的提高和监管要求正迫使银行机构采取主动的安全方法。随着科技的普及和网路银行业务、行动银行等数位化管道的拓展,网路银行业务已成为客户银行服务的首选。银行非常需要利用复杂的身份验证和存取控制流程。
- 随着云端和云端基础的操作的采用增加,组织仍然容易受到安全性较差的云端资料库的影响,从简单的错误配置到硬体晶片中的漏洞。有多种工具可以广泛使用,使潜在的攻击者能够识别在互联网上配置错误的云端资源。因此,组织采用有效的安全解决方案至关重要。此外,快速侦测和回应在应对此类威胁方面也发挥关键作用。
- 许多政府实施的封锁对端点检测和回应 (EDR) 的采用产生了积极影响。新冠肺炎 (COVID-19) 疫情感染疾病,企业开始专注于先进的解决方案,以安全可靠地进行非接触式活动。人工智慧驱动的解决方案、计算技术、自动化以及云端基础的端点检测和回应是 BFSI、医疗保健和政府等行业使用的技术范例。此外,随着业务数位化,对可靠、人工智慧整合和即时报告的 EDR 解决方案的需求不断增长。
- 将安全活动外包给第三方 EDR 网路营运商有几个缺点,包括安全性和第三方基础设施失控。服务公司的网路架构必须安全且最新,才能有效应对最新的高阶威胁。 EDR服务供应商的基础设施可能包含来自多个公司的敏感客户和员工讯息,使其容易受到频繁且复杂的攻击。因此,企业可能会犹豫是否允许这些服务供应商存取其有价值的资料。
EDR(端点检测与反应)市场趋势
引入自带设备 (BYOD) 并增加远端工作
- 混合工作模式的日益普及和快速采用使员工可以在任何地方使用任何设备完成工作。同时,混合和远端工作政策强调了有效资料保护和端点安全解决方案的重要性。
- 正如联邦政府推动实施 CMMC 2.0 所表明的那样,商业和公共部门的组织比以往任何时候都更有能力实现合规性并采用行业框架建立的网路安全和资料保护标准,这已变得非常重要。
- 自带设备 (BYOD) 模式为部署该模式的企业带来了多种威胁。有些是关于公司资料的,有些是关于隐私问题的。以下是实施 BYOD 的一些最常见的危险。放置在装置上的诈欺程式可能会造成安全问题,因为它们会损害组织资讯和系统的完整性、可用性和机密性。威胁行为者可以利用程式来执行恶意目的并取得对装置位置、网路设定、檔案、应用程式和资料的存取权。加密病毒可以破坏资料的可用性和完整性。预计此类威胁将推动所研究的市场。
- 企业在製定保护设备和资料的规则时必须评估其安全需求。例如,合规性是许多公司的主要关注点。在端点上实施风险和合规性解决方案对于正确保护敏感资讯至关重要。此外,BYOD 规则应包括对各种危机情况的计画回应,例如装置遗失或员工裁员。
- 据 CapRelo 称,去年 48.4% 的全球受访者表示,在决定未来工作时,远距工作的机会很重要。 87.4%的受访者表示远距工作对于未来的职涯决策至关重要。
- 此外,据 HP, Inc. 称,全球 41% 的远端员工表示,他们去年存取了客户资料。远距工作时通常可以存取的其他形式的资料包括业务资料、财务资讯和人力资源资料。 IT安全漏洞的出现是因为企业防火墙无法保护分散的员工团队。这将推动所研究市场的需求。
亚太地区将经历最高成长
- 该地区网路犯罪的增加将为端点检测解决方案提供机会。日本电玩巨头卡普空 (Capcom) 报告称遭受了网路攻击。 Capcom 面临 880 万美元的赎金要求,以换取归还赃物,但该公司拒绝支付。然而,一个名为 Ragnar Locker 的俄罗斯网路犯罪组织涉嫌参与盗窃约 35 万份机密文件。
- 政府当局对 POS 终端的重视也推动了该地区 POS 终端市场的成长。例如,在城乡都市区和农村地区引入 POS 终端是印度政府数位印度倡议的核心。印度储备银行最近也拨款8,000万美元,用于增加农村地区(主要是印度东北部各邦)付款终端的部署。这些努力将推动市场。
- 随着 IT 配置从本地转移到公司外部,安全性已成为云端引进週期每个阶段的关键考虑因素。中小型企业 (SME) 的网路安全预算有限,更喜欢云端部署,这样他们可以专注于核心竞争力,而不是在安全基础设施上投入资金。此外,引入公共云端服务将信任边界扩展到组织之外,使安全性成为云端基础设施的关键部分。然而,云端基础的解决方案的使用增加使得企业更容易实施网路安全措施。
- 为了满足客户的各种需求并扩大市场占有率,端点检测公司正在开发新的解决方案。随着员工透过行动和行动装置远端连接到企业网络,端点安全将成为焦点并成为新的外围防御。
- 例如,今年11月,企业网路安全解决方案供应商Seqrite宣布推出其旗舰产品Endpoint Security的增强版。它被称为端点安全 8.0 (EPS 8.0),声称可以保护连接的设备免受网路威胁。 Seqrite 声称,该版本进一步提高了系统的规模,以管理中小企业领域的大量端点。该公司表示,这将使客户能够减少部署足迹和相关的维护工作。此版本即时保护 Linux,并包括为监管机构、审核和客户提供增强的合规性报告。
EDR(端点侦测与回应)产业概述
由于参与者数量不断增加,端点检测和回应市场适度分散。对大型组织来说,保护个人资料安全已成为这个快节奏世界中最重要的任务。 Carbon Black、Cisco Systems 和 Symantec 等领先公司正在开发 EDR 工具来适应此类组织。
2022 年 10 月,下一代行动安全和预防资料外泄独立软体供应商 (ISV) SyncDog, Inc. 推出更智慧、更复杂的行动和云端策略产品以推动销售。宣布与 3Eye Technologies 建立製造合作伙伴关係。目标。 SyncDog 的安全系统工作区为企业和政府机构提供了更安全和可扩展的解决方案,以解决支援员工使用行动装置的所有挑战。它还提供了一个即时的机会来帮助组织遵守联邦政府的 CMMC 2.0 框架以及其他安全和监管隐私标准。
2022 年 8 月,Raytheon Technologies 旗下部门 Raytheon Intelligence & Space 与云端交付端点、云端工作负载、身分和资料保护供应商 CrowdStrike 合作,将其互补的端点安全技术引入 RI&S。多重抗药性)。此次合作将使 RI&S 的 MSSP 服务与 CrowdStrike Falcon 平台结合,可供 RI&S 的所有联邦、州、商业和非营利託管服务客户使用。
其他福利
- Excel 格式的市场预测 (ME) 表
- 3 个月分析师支持
目录
第一章简介
- 研究假设和市场定义
- 调查范围
第二章调查方法
第三章执行摘要
第四章市场动态
- 市场概况
- 产业价值链分析
- 产业吸引力-波特五力分析
- 新进入者的威胁
- 买方议价能力
- 供应商的议价能力
- 替代产品的威胁
- 竞争公司之间的敌意强度
- COVID-19 对市场的影响
- 市场驱动因素
- 企业行动性扩展
- 引入自带设备 (BYOD) 并增加远端工作
- 市场挑战
- 创新成本增加
- 端点检测和响应不足以保护行动设备
第五章市场区隔
- 按成分
- 解决方案
- 服务
- 依部署类型
- 云端基础
- 本地
- 按解决方案类型
- 工作站
- 行动装置
- 伺服器
- POS终端
- 按组织规模
- 中小企业
- 大公司
- 按最终用户产业
- BFSI
- 资讯科技和电信
- 製造业
- 卫生保健
- 零售
- 其他最终用户产业
- 按地区
- 北美洲
- 美国
- 加拿大
- 欧洲
- 德国
- 英国
- 法国
- 其他欧洲国家
- 亚太地区
- 中国
- 日本
- 印度
- 其他亚太地区
- 中东和非洲
- 拉丁美洲
- 北美洲
第六章 竞争形势
- 公司简介
- Carbon Black Inc.
- Cisco Systems Inc.
- CrowdStrike Inc.
- Broadcom Inc.(Symantec Corporation)
- Cybereason Inc.
- Deep Instinct
- Digital Guardian
- FireEye Inc.
- OpenText Corporation
- McAfee Inc.
- RSA Security(DELL EMC)
第七章 投资分析
第八章 市场未来展望
The Endpoint Detection and Response Market size is estimated at USD 4.58 billion in 2024, and is expected to reach USD 13.37 billion by 2029, growing at a CAGR of 23.88% during the forecast period (2024-2029).

Key Highlights
- Businesses have been able to safeguard their networks from common cyber security threats due to sophisticated malware detection. Because of the considerable increase in remote working activities, organizations in the endpoint detection and response (EDR) sector are under scrutiny for offering safe and trustworthy endpoint software.
- EDR tools are technological platforms that enable rapid investigation and containment of endpoint threats and warn security teams of potentially dangerous behaviors. Endpoints include an employee's workstation or laptop, a server, a cloud system, a smartphone, or an IoT device. Endpoint data such as process execution, terminal communication, and client logins are often aggregated by EDR systems, which then analyze the data to detect anomalies and suspected threats and record data regarding harmful behavior. This provides security teams with the knowledge they need to investigate and resolve concerns. They also enable manual and automated tasks on the endpoint to neutralize threats, such as wiping and reimaging the device or isolating it from the network.
- With a strategy to secure their IT processes and systems, secure customer critical data, and comply with government regulations, public and private banking institutes are focusing on implementing the latest technology to prevent cyber attacks. Besides, with greater customer expectations, rising technological capabilities, and regulatory requirements, banking institutions are pushed to adopt a proactive security approach. With the growing technological penetration and digital channels, such as internet banking, mobile banking, etc., online banking has become customers' preferred choice for banking services. There is a significant need for banks to leverage advanced authentication and access control processes.
- With the increasing adoption of cloud and cloud-based operations, poorly secured cloud databases remain weak for organizations, ranging from simple misconfiguration issues to vulnerabilities in hardware chips. Multiple tools are available widely, which enable potential attackers to identify misconfigured cloud resources on the internet. Hence, for organizations, adopting effective security solutions is of utmost importance. Moreover, quick detection and response also play a vital role in addressing such threats.
- The lockdown imposed by many governments has positively affected the adoption of endpoint detection and response (EDR). Following the effects of COVID-19, businesses are focused on advanced solutions to safely and securely undertake contactless activities. AI-powered solutions, computing technology, automation, and cloud-based endpoint detection and response are examples of these technologies used in industries such as BFSI, healthcare, government, and others. Furthermore, as businesses digitalize, there is an increasing demand for an EDR solution that is dependable, AI-integrated, and has real-time reporting capabilities.
- Outsourcing security activities to a third-party EDR network operator has several drawbacks, including the security of the third-party infrastructure and a loss of control. If the service company's cyber architecture is to be effective in combating the most recent sophisticated threats, it must be safe and up-to-date. The infrastructure of an EDR service provider may contain sensitive customer and employee information from multiple companies, making it more vulnerable to frequent and complex attacks. As a result, businesses may be hesitant to give these service providers access to valuable data.
Endpoint Detection and Response (EDR) Market Trends
Bring your Own Device (BYOD) Adoption and Increased Remote Working
- Due to the growing popularity and quick adoption of hybrid work models, employees are empowered to perform their job from wherever they are and on whatever device they have. On the other hand, hybrid and remote work policies underline the significance of effective data protection and endpoint security solutions.
- As indicated by the federal government's push to implement CMMC 2.0, the ability of both commercial and public sector organizations to achieve compliance and adopt the cybersecurity and data protection standards established in industry frameworks is more important than ever.
- Bring-your-own device (BYOD) models pose several threats to the enterprise in which they are implemented. Some are about corporate data, while others are about privacy concerns. The following are some of the most typical hazards of implementing BYOD: Unauthorized programs placed on a device might raise security concerns since they jeopardize the integrity, availability, and confidentiality of an organization's information and systems. Threat actors can utilize programs to carry out the malicious purpose and potentially get access to the device's location, network settings, files, applications, and data. Crypto virus can disrupt data availability and integrity. Such threats are expected to drive the studied market.
- Businesses should evaluate security requirements while developing rules to protect devices and data. For example, in many companies, compliance is a significant concern; implementing risk and compliance solutions on endpoints may be crucial for appropriately protecting sensitive information. Furthermore, BYOD rules should include a planned reaction to various crisis scenarios, such as lost devices or fired staff.
- According to CapRelo, last year, 48.4% of global respondents said the opportunity to work remotely is significant when making future job decisions. 87.4% of respondents responded that remote work is essential to future career decisions.
- Further, according to HP, Inc., 41% of remote employees worldwide said they had access to client data last year. Other forms of data commonly accessible when working remotely are operational data, financial information, and human resource data. Because the corporate firewall did not secure distributed workers, this caused IT security vulnerabilities. This would drive the demand for the studied market.
Asia Pacific to Witness the Highest Growth
- The rise in cybercrimes in the region would provide opportunities for Endpoint detection solutions. A cyberattack was reported by Japanese video game giant Capcom. Capcom was confronted with a USD 8.8 million ransom demand in exchange for returning stolen goods, but the business refused to pay. However, it is suspected a Russian cybercriminal group called Ragnar Locker was behind the theft of around 350,000 confidential documents.
- The emphasis on POS terminals by governmental authorities is also pushing the growth of the POS terminals market in the region. For instance, deploying POS terminals in semi-urban and rural areas is central to the Indian government's Digital India initiative. Also, recently, the Reserve Bank of India earmarked USD 80 million to increase the deployment of payment terminals in rural areas, focusing on states in the country's Northeast region. These initiatives will drive the market.
- Security has been a critical consideration at each step of the cloud adoption cycle as IT provision has moved from on-premise to outside of the company's walls. Small and medium enterprises (SMEs) prefer cloud deployment as it allows them to focus on their core competencies rather than invest their capital in security infrastructure since they have limited cybersecurity budgets. Furthermore, deploying public cloud service extends the boundary of trust beyond the organization, making security a vital part of the cloud infrastructure. However, the increasing usage of cloud-based solutions has significantly simplified enterprises' adoption of cybersecurity practices.
- To meet the various demands of the customers and increase market share, endpoint detection firms are developing new solutions. As employees connect to company networks from remote locations via mobile and portable devices, endpoint security will take center stage and become the new perimeter defense.
- For instance, in November this year, Seqrite, a provider of enterprise cybersecurity solutions, unveiled the enhanced version of its flagship offering, Endpoint Security. It's called End Point Security 8.0 (EPS 8.0), and it claims to safeguard connected devices from cyber threats. Seqrite claims that this release has further improved the scale of the system to manage a high number of endpoints for the SME segment. According to the corporation, this will assist clients in reducing their deployment footprint and related maintenance tasks. This version protects Linux in real-time and includes expanded compliance reporting for regulators, auditors, and customers.
Endpoint Detection and Response (EDR) Industry Overview
The endpoint detection and response market is moderately fragmented due to the increasing number of players. For large organizations, storing personal data securely in this fast-paced world has become the most critical task. Giants like Carbon Black, Cisco Systems, and Symantec are developing EDR tools to cater to such organizations.
In October 2022, SyncDog, Inc., the Independent Software Vendor (ISV) for next-generation mobile security and data loss prevention, announced a collaboration with 3Eye Technologies to produce a smarter, more sophisticated product for its mobility and cloud strategy to drive sales objectives. SyncDog's Secure Systems Workspace provides businesses and government organizations with a more secure and scalable solution for addressing all of the challenges of enabling employees on mobile devices-with immediate opportunities to help organizations comply with the federal government's CMMC 2.0 framework and other security and regulatory privacy standards.
In August 2022, Raytheon Intelligence & Space, a Raytheon Technologies division, partnered with CrowdStrike, a cloud-delivered endpoint, cloud workload, identity, and data protection provider, to incorporate its complementary endpoint security technologies into RI&S' managed detection and response (MDR) service. With this collaboration, RI&S' MSSP services will be available to all of RI&S' federal, state, commercial, and non-profit managed services customers in conjunction with the CrowdStrike Falcon platform.
Additional Benefits:
- The market estimate (ME) sheet in Excel format
- 3 months of analyst support
TABLE OF CONTENTS
1 INTRODUCTION
- 1.1 Study Assumptions and Market Definition
- 1.2 Scope of the Study
2 RESEARCH METHODOLOGY
3 EXECUTIVE SUMMARY
4 MARKET DYNAMICS
- 4.1 Market Overview
- 4.2 Industry Value Chain Analysis
- 4.3 Industry Attractiveness - Porter's Five Forces Analysis
- 4.3.1 Threat of New Entrants
- 4.3.2 Bargaining Power of Buyers/Consumers
- 4.3.3 Bargaining Power of Suppliers
- 4.3.4 Threat of Substitute Products
- 4.3.5 Intensity of Competitive Rivalry
- 4.4 Impact of COVID-19 on the Market
- 4.5 Market Drivers
- 4.5.1 Increasing Expansion of Enterprise Mobility
- 4.5.2 Bring your Own Device (BYOD) Adoption and Increased Remote Working
- 4.6 Market Challenges
- 4.6.1 Higher Innovation Costs
- 4.6.2 Endpoint Detection and Response Falling Short of Protecting Mobile Devices
5 MARKET SEGMENTATION
- 5.1 By Component
- 5.1.1 Solutions
- 5.1.2 Services
- 5.2 By Deployment Type
- 5.2.1 Cloud-based
- 5.2.2 On-premise
- 5.3 By Solution Type
- 5.3.1 Workstations
- 5.3.2 Mobile Devices
- 5.3.3 Servers
- 5.3.4 Point of Sale Terminals
- 5.4 By Organization Size
- 5.4.1 Small and Medium Enterprises
- 5.4.2 Large Enterprises
- 5.5 By End-User Industry
- 5.5.1 BFSI
- 5.5.2 IT and Telecom
- 5.5.3 Manufacturing
- 5.5.4 Healthcare
- 5.5.5 Retail
- 5.5.6 Other End-User Industries
- 5.6 By Geography
- 5.6.1 North America
- 5.6.1.1 United States
- 5.6.1.2 Canada
- 5.6.2 Europe
- 5.6.2.1 Germany
- 5.6.2.2 United Kingdom
- 5.6.2.3 France
- 5.6.2.4 Rest of Europe
- 5.6.3 Asia Pacific
- 5.6.3.1 China
- 5.6.3.2 Japan
- 5.6.3.3 India
- 5.6.3.4 Rest of Asia Pacific
- 5.6.4 Middle East and Africa
- 5.6.5 Latin America
- 5.6.1 North America
6 COMPETITIVE LANDSCAPE
- 6.1 Company Profiles*
- 6.1.1 Carbon Black Inc.
- 6.1.2 Cisco Systems Inc.
- 6.1.3 CrowdStrike Inc.
- 6.1.4 Broadcom Inc. (Symantec Corporation)
- 6.1.5 Cybereason Inc.
- 6.1.6 Deep Instinct
- 6.1.7 Digital Guardian
- 6.1.8 FireEye Inc.
- 6.1.9 OpenText Corporation
- 6.1.10 McAfee Inc.
- 6.1.11 RSA Security (DELL EMC)













