 |
市场调查报告书
商品编码
1641855
威胁情报保全服务:市场占有率分析、产业趋势与统计、成长预测(2025-2030 年)Threat Intelligence Security Services - Market Share Analysis, Industry Trends & Statistics, Growth Forecasts (2025 - 2030) |
||||||
※ 本网页内容可能与最新版本有所差异。详细情况请与我们联繫。
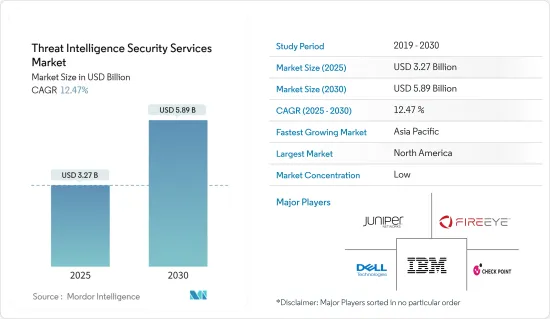
威胁情报保全服务市场规模预计在 2025 年为 32.7 亿美元,预计到 2030 年将达到 58.9 亿美元,预测期内(2025-2030 年)的复合年增长率为 12.47%。
主要亮点
- 保全服务提供者正在加强其威胁识别能力,以应对从进阶持续性威胁(APT)到新型攻击和新兴恶意软体的一系列挑战。虽然出现了新的进阶持续性威胁类别,但必须注意的是,这些威胁通常是由恶意软体、网路钓鱼等传送系统和资料外洩的组合造成的。这些威胁的特征是性质未知、目标有限、适应性强。
- 政府对资料安全的重视程度不断提高、高级威胁的激增、云端运算的兴起、自带设备 (BYOD) 模式的快速普及以及利用巨量资料分析获取威胁情报等因素正在推动这一增长。市场成长。随着无线运算和宽频等技术的进步以及公司开发更先进的威胁情报解决方案,对威胁情报安全解决方案的需求只会增加。
- 此外,全球威胁情报安全市场预计将见证对网路流量分析、恶意软体传播器以及安全资讯和事件管理 (SIEM) 等工具的需求激增。
- 各种规模的组织越来越多地转向託管服务来加强其网路安全态势。除了提供主动保护之外,这些服务还有助于识别您组织的漏洞、推荐解决方案并提供一系列附加服务。
- 然而,该产业面临威胁情报安全工具采购和实施成本高等挑战,阻碍了该产业的成长轨迹。
威胁情报保全服务市场趋势
网路安全事件快速增加推动市场
- 企业正在使用威胁情报安全工具来识别和打击网路攻击风险,推动全球市场趋势。同时,公司正在转向网路定义软体和恶意软体侦测工具来强化其 IT 系统。
- 而且,及时的威胁情报不仅可以帮助企业避免网路攻击,还可以透过加强各级安全检查来帮助企业从巨额财务损失中挽回损失,从而推动市场需求。
- 随着新威胁瞄准设备和企业,物联网社群和软体开发人员正在转向各种技术解决方案来减轻物联网应用的网路风险。随着越来越多的企业采用物联网来提高生产力,网路犯罪分子将目标从传统电脑转移到物联网设备。
- 威胁情报安全解决方案在防御威胁和保护您的环境方面发挥着至关重要的作用。此外,由于 BYOD 模型的快速采用以及巨量资料分析与威胁情报安全框架的集成,这些解决方案的全球市场呈现出良好的投资前景。
亚太地区将经历最高成长
- 预计亚太地区将在预测期内实现最高成长。这种快速成长的驱动力是技术进步、新兴国家的崛起、安全意识的增强以及日益复杂的威胁。此外,该地区正逐渐融入正在进行的 IT 革命,并正在加大对科技的投资。
- 此外,该地区的成长受到技术进步、新兴经济体的崛起、对安全的日益重视以及不断演变的威胁的推动。该地区与正在进行的 IT 革命的契合以及强劲的技术投资进一步推动了这一成长。
- 此外,资料库量的突然增加、特权使用者帐户和登入异常、非典型的网域名称系统请求以及无法解释的系统变更是这种成长的主要驱动因素。
- 随着企业面临的网路安全漏洞风险越来越大,许多企业开始转向威胁情报服务。随着云端平台、物联网和其他网路技术的兴起,这种变化尤其明显。
威胁情报保全服务产业概况
威胁情报市场竞争激烈,由几家大公司组成。从市场占有率来看,目前市场主要被少数几家大公司占据。这些拥有突出市场份额的领先公司正致力于扩大海外基本客群,并利用策略合作措施来提高市场占有率和盈利。
- 2023 年 10 月 Check Point 软体技术有限公司(「Check Point」)今天宣布推出其全新的、预防优先的保全行动套件 Check Point。
- 2023 年 8 月 Fortinet 将推出首款 Secure SD 系列伺服器,该伺服器采用新的安全处理单元 5 (SP5) ASIC,以经济实惠的价格提供业界领先的 AI 驱动的威胁预防效能、扩充性和能源效率。 - 推出FortiGate 90G 、WAN 设备和 NGFW。
其他福利:
- Excel 格式的市场预测 (ME) 表
- 3 个月的分析师支持
目录
第 1 章 简介
- 研究假设和市场定义
- 研究范围
第二章调查方法
第三章执行摘要
第四章 市场洞察
- 市场概况
- 价值链/供应链分析
- 产业吸引力-波特五力分析
- 新进入者的威胁
- 购买者/消费者的议价能力
- 供应商的议价能力
- 替代品的威胁
- 竞争对手之间的竞争
第五章 市场动态
- 市场驱动因素
- 网路安全事件急剧增加
- M2M/IoT 连线的增加要求企业采取更强有力的网路安全措施
- 市场限制
- 网路安全专家短缺
- 高度依赖传统身分验证方法且缺乏准备
第六章 市场细分
- 依部署方式
- 云
- 本地
- 按最终用户
- BFSI
- 卫生保健
- IT
- 零售
- 生命科学
- 按地区
- 北美洲
- 美国
- 加拿大
- 欧洲
- 德国
- 英国
- 法国
- 亚洲
- 中国
- 日本
- 韩国
- 澳洲和纽西兰
- 拉丁美洲
- 中东和非洲
- 北美洲
第七章 竞争格局
- 供应商市场占有率
- 公司简介
- Juniper Networks Inc.
- Dell Inc.
- Check Point Software Technologies Ltd
- FireEye Inc.
- IBM Corporation
- AlienVault Inc.
- Farsight Security Inc.
- LogRhythm Inc.
- F-Secure Corporation
- Webroot Inc.
- Fortinet Inc.
- McAfee LLC
- Symantec Corporation
- LookingGlass Cyber Solutions Inc.
第八章 市场机会与未来趋势
The Threat Intelligence Security Services Market size is estimated at USD 3.27 billion in 2025, and is expected to reach USD 5.89 billion by 2030, at a CAGR of 12.47% during the forecast period (2025-2030).

Key Highlights
- Security service providers are enhancing their threat identification capabilities to combat a range of challenges, from advanced persistent threats (APTs) to novel attacks and emerging malware. While a new category, the advanced persistent threat, has emerged, it is crucial to note that these threats often stem from a combination of malware, delivery systems like phishing, and data exfiltration. These threats are characterized by being unknown, low-targeted, and adaptive.
- Factors such as the increasing emphasis on data security by governments of various countries, a surge in advanced threats, widespread adoption of the cloud, the rapid adoption of bring-your-own-device (BYOD) models, and the utilization of big data analytics for threat intelligence are expected to propel the market's growth. As technologies like wireless computing and broadband advance and enterprises develop more sophisticated threat intelligence solutions, the demand for threat intelligence security solutions will only rise.
- Furthermore, the global threat intelligence security market is poised to witness a surge in demand for tools like network traffic analysis, malware dissemblers, and security information and event management (SIEM).
- Organizations, irrespective of size, are increasingly turning to management services to bolster their cybersecurity posture. These services not only provide proactive protection but also help identify organizational vulnerabilities, recommend solutions, and offer a suite of additional services.
- However, the industry faces challenges, notably in the form of high procurement and installation costs for threat intelligence security tools, which can impede its growth trajectory.
Threat Intelligence Security Services Market Trends
Rapidly Increasing Cyber Security Incidents to Drive the Market
- Enterprises utilize threat intelligence security tools to identify and combat cyber attack risks, bolstering global market trends. Concurrently, businesses are increasingly turning to network-defining software and malware detection tools to fortify their IT systems.
- Furthermore, timely threat intelligence not only averts cyber attacks but also aids in recovering significant financial losses as companies ramp up security checks across all levels, fueling market demand.
- As emerging threats target devices and enterprises, the IoT community and software developers are pivoting toward a diverse array of technology solutions to mitigate cyber risks in IoT applications. With a rising number of companies embracing IoT for heightened productivity, cybercriminals are shifting their focus from traditional computers to IoT devices.
- Threat intelligence security solutions play a pivotal role in preempting threats and safeguarding environments. Moreover, the global market for these solutions presents lucrative investment prospects, driven by the swift adoption of the BYOD model and the integration of big data analytics into threat intelligence security frameworks.
Asia-Pacific to Witness the Highest Growth
- Asia-Pacific is poised to achieve its peak growth during the forecast period. This surge is underpinned by technological advancements, the rise of new economies, heightened security awareness, and the escalating sophistication of threats. Additionally, the region is witnessing a deepening integration into the ongoing IT revolutions and increased investments in technology.
- Moreover, the region's growth is bolstered by technological advancements, the emergence of new economies, a growing emphasis on security, and an evolving threat landscape. This growth is further fueled by Asia-Pacific's alignment with the ongoing IT revolutions and its robust investments in technology.
- Furthermore, the upsurge in database volumes, anomalies in privileged user accounts and logins, atypical domain name system requests, and unexplained system changes are key drivers of this growth.
- As enterprises face heightened risks of cybersecurity breaches, many are turning to threat intelligence services. This shift is particularly pronounced due to the widespread adoption of cloud platforms, IoT, and other networking technologies.
Threat Intelligence Security Services Industry Overview
The threat intelligence market is highly competitive and consists of several major players. In terms of market share, few of the major players currently dominate the market. These major players, with prominent shares in the market, are focusing on expanding their customer base across foreign countries and are leveraging strategic collaborative initiatives to increase their market share and profitability.
- October 2023: Check Point Software Technologies Ltd announced the launch of Check Point Horizon Playblocks prevention-first security operations security suite, which includes the managed detection/prevention and response (MDR/MPR) SOC service, where it augments security by enabling products, people, and processes to work together to stop the proliferation of attacks.
- August 2023: Fortinet Inc. announced the FortiGate 90G, the first Secure SD-WAN appliance and NGFW with the new security processing unit 5 (SP5) ASIC that delivers industry-leading AI-powered threat protection performance, scalability, and power efficiency at a cost-effective price.
Additional Benefits:
- The market estimate (ME) sheet in Excel format
- 3 months of analyst support
TABLE OF CONTENTS
1 INTRODUCTION
- 1.1 Study Assumptions and Market Definition
- 1.2 Scope of the Study
2 RESEARCH METHODOLOGY
3 EXECUTIVE SUMMARY
4 MARKET INSIGHTS
- 4.1 Market Overview
- 4.2 Value Chain / Supply Chain Analysis
- 4.3 Industry Attractiveness - Porter's Five Forces Analysis
- 4.3.1 Threat of New Entrants
- 4.3.2 Bargaining Power of Buyers/Consumers
- 4.3.3 Bargaining Power of Suppliers
- 4.3.4 Threat of Substitute Products
- 4.3.5 Intensity of Competitive Rivalry
5 MARKET DYNAMICS
- 5.1 Market Drivers
- 5.1.1 Rapidly Increasing Cyber Security Incidents
- 5.1.2 Growing M2M/IoT Connections Demands for Strengthened Cyber Security in Enterprises
- 5.2 Market Restraints
- 5.2.1 Lack of Cyber Security Professionals
- 5.2.2 High Reliance on Traditional Authentication Methods and Low Preparedness
6 MARKET SEGMENTATION
- 6.1 By Deployment Mode
- 6.1.1 Cloud
- 6.1.2 On-premise
- 6.2 By End User
- 6.2.1 BFSI
- 6.2.2 Healthcare
- 6.2.3 IT
- 6.2.4 Retail
- 6.2.5 Life Sciences
- 6.3 By Geography
- 6.3.1 North America
- 6.3.1.1 United States
- 6.3.1.2 Canada
- 6.3.2 Europe
- 6.3.2.1 Germany
- 6.3.2.2 United Kingdom
- 6.3.2.3 France
- 6.3.3 Asia
- 6.3.3.1 China
- 6.3.3.2 Japan
- 6.3.3.3 South Korea
- 6.3.4 Australia and New Zealand
- 6.3.5 Latin America
- 6.3.6 Middle East and Africa
- 6.3.1 North America
7 COMPETITIVE LANDSCAPE
- 7.1 Vendor Market Share
- 7.2 Company Profiles
- 7.2.1 Juniper Networks Inc.
- 7.2.2 Dell Inc.
- 7.2.3 Check Point Software Technologies Ltd
- 7.2.4 FireEye Inc.
- 7.2.5 IBM Corporation
- 7.2.6 AlienVault Inc.
- 7.2.7 Farsight Security Inc.
- 7.2.8 LogRhythm Inc.
- 7.2.9 F-Secure Corporation
- 7.2.10 Webroot Inc.
- 7.2.11 Fortinet Inc.
- 7.2.12 McAfee LLC
- 7.2.13 Symantec Corporation
- 7.2.14 LookingGlass Cyber Solutions Inc.










