 |
市场调查报告书
商品编码
1687447
欺敌技术:市场占有率分析、产业趋势与统计、成长预测(2025-2030 年)Deception Technology - Market Share Analysis, Industry Trends & Statistics, Growth Forecasts (2025 - 2030) |
||||||
※ 本网页内容可能与最新版本有所差异。详细情况请与我们联繫。
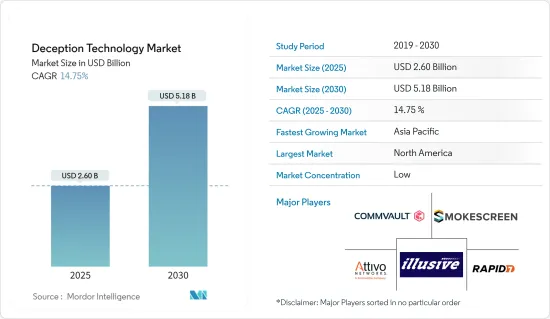
2025 年欺敌技术市场规模预估为 26 亿美元,预计到 2030 年将达到 51.8 亿美元,预测期内(2025-2030 年)的复合年增长率为 14.75%。
主要亮点
- 欺敌技术是一种用于侦测和防御针对性攻击的先进安全解决方案。欺骗是透过故意干扰、虚假反应、误导和伪造来实现的。
- 网路威胁程度的不断提高增加了侦测和减轻已经渗透到您的网路的高阶风险的需要。这推动了欺敌技术的采用。
- 目前的安全工具可以有效地标记异常,但其影响和潜在风险需要更加清晰。这些工具会产生大量警报,其中许多警报对于安全团队来说只是浪费时间进行调查。在必须解决真正威胁的同时,评估这些虚假威胁却浪费了资源。透过改变攻击的不对称性,欺骗技术使安全团队能够专注于其网路的真正威胁。这样的场景正在帮助欺敌技术在预测期内获得发展动力。
- 许多欺骗解决方案的核心都是人工智慧和机器学习(ML)。这些功能可使欺骗技术保持不断动态,并使他们无需不断创建新的欺骗宣传活动,从而有助于减少营运开销并减少对安全团队的影响。
- 在 COVID-19 疫情期间,影响个人、企业和组织的网路攻击激增。结果,一些受影响的公司正在投资升级其过时的系统,从而助长了欺骗技术市场。例如,美国国防安全保障部已就与疫情有关的新兴网路犯罪分子和高阶持续威胁团体发出警告。国际刑事警察组织(INTERPOL)就故意针对医疗设施的犯罪者发出警告。
欺敌技术的市场趋势
网路安全预计将高速成长
- 零时差攻击是一种有针对性的攻击,攻击者发现软体中的漏洞,然后与其他骇客一起利用漏洞,直到组织意识到这一点。零时差攻击最初没有留下任何侦测机会。
- 2021年,Mandiant威胁情报发现了80个零日漏洞。利用零日漏洞的主要行为者仍然是由中国团体领导的国家支持的组织。我们也发现,出于经济动机而利用零日漏洞的行为者比例显着增加,前年发现的利用零日漏洞的行为者中,有近三分之一是出于经济动机。
- 此外,威胁行为者最常利用微软、苹果和谷歌产品中的零日漏洞,这反映了这些製造商的受欢迎程度。过去一年中,零时差漏洞利用显着增加,利用这些漏洞的行为者也更加多样化,这扩大了几乎所有行业和地区的公司的风险组合,特别是那些依赖这些广泛使用的系统的公司。
- 研究表明,零时差攻击的增加是由多种因素造成的。例如,云端託管、行动和物联网 (IoT) 技术的持续采用正在增加互联网连接系统和设备的数量和复杂性。换句话说,软体越多,软体缺陷就越多。这一趋势也受到了漏洞仲介行业的兴起的推动,私营部门组织、研究人员和威胁组织向零日漏洞研究和开发投入了更多资源。
- 随着零时差攻击和 APT 的兴起,世界各地的组织都在部署欺敌技术,以便儘早发现攻击并最大限度地减少对敏感资料的影响。因此,如图所示,预计预测期内资料外洩成本的增加将推动欺敌技术市场的发展。
北美预计将占据主要市场占有率
- 由于金融服务、医疗保健和政府机构等受到严格监管的行业越来越多地采用欺敌技术解决方案,预计北美地区将占据全球欺敌技术市场的很大份额。美国几个州,最着名的是《加州消费者隐私法案》(CCPA),已经颁布了隐私法,大大推动了终端用户产业对欺骗技术解决方案的需求。
- 加州通过了独立于《加州消费者隐私法案》的立法,以解决物联网设备的预设密码和物联网漏洞问题。为此,国家网路安全和通讯整合中心 (NCCIC) 推出了技术警报 (TA),为 MSP 客户网路和系统管理员提供资讯和指导,以侦测其网路和系统上的恶意活动并降低相关风险。
- 本 TA 概述了 APT 参与者在 MSP 网路环境中使用的 TTP、缓解提案以及报告事件的详细资讯。适当基础设施的高可用性、大量全球金融机构的存在、高频率的网路攻击以及技术的不断采用,预计将推动北美地区欺骗技术市场的成长。
- 推动北美欺骗技术成长的关键趋势包括智慧型手机设备的兴起以及产生包含有价值资讯的样本资料的社交应用程式的日益普及。这大大增加了网路威胁的风险。
- 此外,知名市场供应商的存在以及各个组织中资料量的增加正在推动该地区对欺骗技术解决方案的需求。此外,各个终端用户领域对 5G、AI、云端和物联网等先进技术的早期采用正在迅速推动对欺敌技术解决方案的需求。
欺敌技术产业概况
欺敌技术市场高度分散,主要公司包括 Illusive Networks、Commvault Systems Inc.、Smokescreen Technologies Pvt.有限公司、Attivo Networks Inc. (Sentinelone Inc.) 和 Rapid7 LLC。市场参与者正在采用伙伴关係、创新、合併和收购等策略来增强其产品供应并获得永续的竞争优势。
2023年2月,Rapid7与南佛罗里达大学(USF)宣布成立网路威胁情报研究所,以支持四所学院的教师和学生进行跨领域研究活动。
2022 年 9 月,Commvault 宣布全面推出 Metallic ThreatWise,这是一种警报系统,可在未知威胁和零时差威胁发生之前发现它们,从而最大限度地减少对受损资料和业务的影响。
其他福利:
- Excel 格式的市场预测 (ME) 表
- 3 个月的分析师支持
目录
第 1 章 简介
- 研究假设和市场定义
- 研究范围
第二章调查方法
第三章执行摘要
第四章 市场洞察
- 市场概况
- 产业吸引力-波特五力分析
- 供应商的议价能力
- 买家的议价能力
- 新进入者的威胁
- 替代品的威胁
- 竞争对手之间的竞争
- 产业价值链分析
- COVID-19 市场影响
第五章 市场动态
- 市场驱动因素
- 零时差攻击和有针对性的 APT 的兴起
- 需要有效的解决方案来儘早发现攻击者
- 市场限制
- 遗留诱饵系统的使用率很高
第六章 市场细分
- 按部署
- 云
- 本地
- 按组织规模
- 中小企业
- 大型企业
- 按服务
- 託管服务
- 专业服务
- 作者:Deception Stack
- 资料安全
- 应用程式安全
- 端点安全
- 网路安全
- 按最终用户
- 政府
- 医疗
- BFSI
- 防御
- 资讯科技/通讯
- 其他最终用户
- 按地区
- 北美洲
- 欧洲
- 亚太地区
- 拉丁美洲
- 中东和非洲
第七章 竞争格局
- 公司简介
- Illusive Networks
- Commvault Systems Inc.
- Smokescreen Technologies Pvt. Ltd
- Attivo Networks Inc.(Sentinelone Inc.)
- Rapid7 LLC
- Ridgeback Network Defense Inc.
- Akamai Technologies Inc.
- Acalvio Technologies Inc.
- CounterCraft SL
- CyberTrap Software GmbH
- Fidelis Cybersecurity Inc.(Skyview Capital LLC)
- LogRhythm Inc.
- WatchGuard Technologies Inc.
- NTT Security Limited(Nippon Telegraph and Telephone Corporation)
- Broadcom Inc.(Symantec Corporation)
第八章投资分析
第九章:市场的未来
The Deception Technology Market size is estimated at USD 2.60 billion in 2025, and is expected to reach USD 5.18 billion by 2030, at a CAGR of 14.75% during the forecast period (2025-2030).

Key Highlights
- Deception technology is an advanced security solution to detect and prevent targeted attacks. Deceptions are achieved through purposeful obstructions, incorrect responses, misdirection, and forgery.
- Owing to the higher level of cyber threats, there is an increasing need for organizations to detect and mitigate advanced risks that have already breached the network. It is boosting deception technology adoption.
- The current security tools have effectively flagged anomalies but need to be more significant in defining their impact and risk potential. These tools generate many alerts, most of which must be investigated by security teams despite many of them being a waste of time. The resources are spent wastefully assessing these false threats, while the real and present threats must be addressed. By altering the asymmetry of an attack, deception technology helps security teams focus on real threats to the network. Scenes like these have aided the deception technology to gain momentum over the forecast period.
- Many deception solutions have AI and machine learning (ML) built into their core. These features ensure that deception techniques are kept dynamic and help reduce the operational overheads and the impact on security teams by freeing them from continually creating new deception campaigns.
- There was a sharp rise in cyberattacks harming individuals, businesses, and organizations during the COVID-19 outbreak. Consequently, several impacted enterprises are investing in upgrading outdated systems, thereby contributing to the deception technology market. For instance, the US Department of Homeland Security warned about emerging pandemic-related cybercriminals and advanced persistent threat groups. Interpol released a warning about criminals deliberately targeting medical facilities.
Deception Technology Market Trends
Network Security is expected to grow at a higher pace
- A zero-day attack is a targeted attack in which the attacker discovers software vulnerabilities and exploits them with other hackers until the organization becomes aware of the vulnerability. The zero-day exploit leaves no opportunity for detection initially.
- In 2021, Mandiant Threat Intelligence found 80 zero-day exploits in the wild, which was more than twice as many as the year before. The main actors exploiting zero-day vulnerabilities continue to be state-sponsored organizations with Chinese groups as leaders. The proportion of financially motivated actors deploying zero-day exploits has also increased significantly, with nearly one in every three identified actors exploiting zero-day exploits in the year before being financially motivated.
- Further, threat actors most commonly exploited zero-day vulnerabilities in Microsoft, Apple, and Google products, which reflects the popularity of these manufacturers. The significant growth in zero-day exploitation in the previous year, as well as the diversification of actors exploiting them, broadens the risk portfolio for businesses in practically every industry area and geography, particularly those that rely on these widely used systems.
- According to the research, a variety of factors contribute to an increase in the number of zero-day exploits. For example, the continued adoption of cloud hosting, mobile, and Internet-of-Things (IoT) technologies increases the volume and complexity of Internet-connected systems and devices. In other words, more software leads to more software flaws. The rise of the exploit broker industry is also likely contributing to this trend, with more resources being moved into zero-day research and development by private organizations, researchers, and threat groups alike.
- Due to the increase in zero-day attacks and APTs, organizations worldwide are deploying deception technologies to detect attacks as early as possible and minimize their effect on sensitive data. Therefore, the growing costs of data breaches, as indicated in the graph, are expected to drive the deception technology market during the forecast period.
North America is Expected to Hold Major Market Share
- The North American region is expected to hold a significant share in the global deception technology market owing to the increasing adoption of deception technology solutions in highly regulated industries such as financial services, health care, and government. Several US states, most notably California with its California Consumer Privacy Act (CCPA), have enacted privacy laws, significantly driving the demand for deception technology solutions among end-user industries.
- California passed a law, separate from the California Consumer Privacy Act, addressing default passwords on IoT devices and IoT vulnerabilities. Owing to this, the National Cybersecurity and Communications Integration Center (NCCIC) introduced the Technical Alert (TA), which provides information and guidance to assist MSP customer network and system administrators with the detection of malicious activity on their networks and systems and the mitigation of associated risks.
- This TA provides an overview of the TTP that APT actors use in MSP network environments, suggestions for mitigation, and details on reporting incidents. The high availability of adequate infrastructure, the presence of numerous global financial institutions, the high frequency of cyber-attacks, and the increased adoption of technologies are expected to drive the growth of the deception technology market in the North American region.
- The major trends responsible for the growth of deception technology in the North American region include the growing number of smartphone devices and an increase in the adoption of social apps, which generate sample data that contains valuable information. This has significantly increased the risk of cyber threats.
- In addition, the presence of prominent market vendors and increasing data volume in various organizations are driving the demand for deception technology solutions in the region. Furthermore, the early adoption of advanced technologies, such as 5G, AI, cloud, and IoT, in various end-user sectors is driving the demand for deception technology solutions at a rapid pace.
Deception Technology Industry Overview
The deception technology market is highly fragmented, with the presence of major players like Illusive Networks, Commvault Systems Inc., Smokescreen Technologies Pvt. Ltd., Attivo Networks Inc. (Sentinelone Inc.), and Rapid7 LLC. Players in the market are adopting strategies such as partnerships, innovations, mergers, and acquisitions to enhance their product offerings and gain a sustainable competitive advantage.
In February 2023, Rapid7 and the University of South Florida (USF) announced a partnership to create a cyber threat intelligence laboratory that will support interdisciplinary research efforts by faculty experts and students from four colleges and myriad disciplines.
In September 2022, Commvault announced the general availability of Metallic ThreatWise, an early warning system that proactively surfaces unknown and zero-day threats to minimize compromised data and business impact.
Additional Benefits:
- The market estimate (ME) sheet in Excel format
- 3 months of analyst support
TABLE OF CONTENTS
1 INTRODUCTION
- 1.1 Study Assumptions and Market Definition
- 1.2 Scope of the Study
2 RESEARCH METHODOLOGY
3 EXECUTIVE SUMMARY
4 MARKET INSIGHTS
- 4.1 Market Overview
- 4.2 Industry Attractiveness - Porter's Five Forces Analysis
- 4.2.1 Bargaining Power of Suppliers
- 4.2.2 Bargaining Power of Buyers
- 4.2.3 Threat of New Entrants
- 4.2.4 Threat of Substitutes
- 4.2.5 Intensity of Competitive Rivalry
- 4.3 Industry Value Chain Analysis
- 4.4 Impact of COVID-19 on the Market
5 MARKET DYNAMICS
- 5.1 Market Drivers
- 5.1.1 Growing Number of Zero-day and Targeted APT's
- 5.1.2 Need of Effective Solutions for Early Detection of Attackers
- 5.2 Market Restraints
- 5.2.1 High Usage of Legacy Honeypots
6 MARKET SEGMENTATION
- 6.1 By Deployment
- 6.1.1 Cloud
- 6.1.2 On-premise
- 6.2 By Organization Size
- 6.2.1 Small and Medium Enterprises
- 6.2.2 Large Enterprises
- 6.3 By Service
- 6.3.1 Managed Services
- 6.3.2 Professional Services
- 6.4 By Deception Stack
- 6.4.1 Data Security
- 6.4.2 Application Security
- 6.4.3 Endpoint Security
- 6.4.4 Network Security
- 6.5 By End-User
- 6.5.1 Government
- 6.5.2 Medical
- 6.5.3 BFSI
- 6.5.4 Defense
- 6.5.5 IT and Telecommunication
- 6.5.6 Other End-Users
- 6.6 By Geography
- 6.6.1 North America
- 6.6.2 Europe
- 6.6.3 Asia Pacific
- 6.6.4 Latin America
- 6.6.5 Middle East and Africa
7 COMPETITIVE LANDSCAPE
- 7.1 Company Profiles
- 7.1.1 Illusive Networks
- 7.1.2 Commvault Systems Inc.
- 7.1.3 Smokescreen Technologies Pvt. Ltd
- 7.1.4 Attivo Networks Inc. (Sentinelone Inc.)
- 7.1.5 Rapid7 LLC
- 7.1.6 Ridgeback Network Defense Inc.
- 7.1.7 Akamai Technologies Inc.
- 7.1.8 Acalvio Technologies Inc.
- 7.1.9 CounterCraft SL
- 7.1.10 CyberTrap Software GmbH
- 7.1.11 Fidelis Cybersecurity Inc. (Skyview Capital LLC)
- 7.1.12 LogRhythm Inc.
- 7.1.13 WatchGuard Technologies Inc.
- 7.1.14 NTT Security Limited (Nippon Telegraph and Telephone Corporation)
- 7.1.15 Broadcom Inc. (Symantec Corporation)











