 |
市场调查报告书
商品编码
1849895
北美网路安全:市场份额分析、行业趋势、统计数据和成长预测(2025-2030 年)North America Cyber Security - Market Share Analysis, Industry Trends & Statistics, Growth Forecasts (2025 - 2030) |
||||||
※ 本网页内容可能与最新版本有所差异。详细情况请与我们联繫。
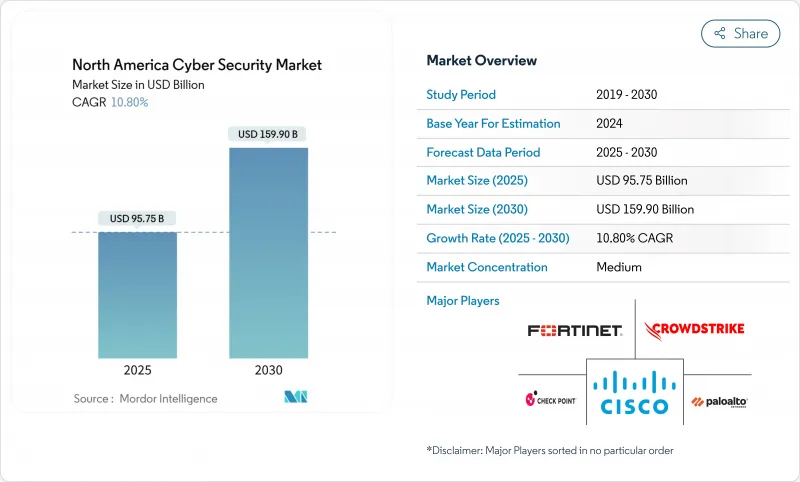
预计到 2025 年,北美网路安全市场规模将达到 957.5 亿美元,到 2030 年将达到 1,599 亿美元,预测期(2025-2030 年)的复合年增长率为 10.80%。
严格的联邦和州法规、高级威胁的普遍存在以及关键行业数位转型计划的加速推进是推动成长的关键因素。美国所有50个州强制要求揭露资料外洩事件,以及美国证券交易委员会(SEC)新的报告规则,迫使企业投资于预防性控制措施,而非仅依赖被动的事件回应模式。此外,联邦政府向后量子密码学的过渡(要求政府机构和承包商在2030年至2035年之间对其加密系统进行全面升级)也刺激了相关支出。虽然美国占据了区域需求的大部分,但加拿大正经历最快的成长,这主要得益于C-26法案对关键系统提出的更高要求,从而推动了供应商活动的活性化。随着企业将保全行动以弥补技能缺口,託管服务和专业服务的成长也正在加速。
北美网路安全市场趋势与洞察
强制性资料外洩揭露和攻击激增
美国证券交易委员会(SEC)因SolarWinds事件相关的揭露缺陷,对四家上市科技公司处以700万美元的罚款。此外,在2024财年,SEC还采取了583项执法行动,并投入82亿美元用于补救措施。这些措施促使各公司董事会将网路安全视为核心合规职能,而非可自由支配的IT支出。同时,墨西哥在2024财年记录了4,240万次恶意软体攻击试验,相当于每天11.6万次。随着美国各州实施通知法规,联邦法规要求在重大事件发生后的四个工作天内进行揭露,各公司正将预算转向持续监控、自动侦测和漏洞遏制平台,以缩短回应週期并限制责任。
云端迁移与零信任部署势头强劲
随着联邦行政命令和 NIST SP 800-207 将以身分为中心的架构确立为公共部门的预设架构,零信任模型已取代了以边界为中心的策略。如今,60% 的北美公司已积极实施零信任计划,94% 的公司至少部署了其中一项要素。这项转变与持续的云端运算浪潮密不可分,后者正在再形成网路边缘和身份验证流程。在混合云或多重云端环境中实施零信任的组织报告称,透过减少事件处理和策略维护的负担,其投资回报率高达 152%。云端迁移和零信任工具的整合正在推动对安全存取服务边缘 (SASE) 以及身分和存取管理平台的需求,从而增强了专注于多重云端管治的託管安全服务提供者 (MSSP) 的结构化服务机会。
网路安全专业人员严重短缺
即使2024年就业人数下降2.7%之后,北美地区的网路安全职位仍将成长4%,到2025年将有542,687个职缺。儘管37%的公司面临预算冻结,但仍有90%的公司表示有严重的技能缺口,尤其是在人工智慧驱动的分析和零信任配置方面。光是墨西哥到2025年就需要35,000名专业人员,65%的当地企业将人才短缺列为主要障碍,导致其在先进技术方面的支出增加了80%以弥补这一缺口。技能短缺使公司面临长时间的延误,而人手不足导致的直接资料外洩成本平均高达400万美元,这凸显了将技术和专业知识整合到订阅套餐中的託管检测和响应服务的迫切需求。
细分市场分析
2024年,解决方案在北美网路安全市场占据65.5%的份额,预计到2030年将以13.8%的复合年增长率成长。服务领域的成长趋势直接缓解了技能短缺问题,同时使企业能够更快地获得人工智慧主导的分析平台。针对量子安全密码评估和零信任蓝图所製定的专业服务也不断成长。 eSentire目前保护着250万名患者的数据,凸显了受监管产业的需求。
北美託管式网路安全服务市场在医疗保健和中型製造业领域成长最为迅猛。透过将网路安全视为营运支出,基于服务的消费模式有助于企业整合庞大的工具集并获得董事会的核准。透过整合人工智慧、威胁情报和专家经验,供应商能够赢得长期稳定的合同,并提高经常性收入的可见性。
儘管到2024年,本地部署仍将占北美网路安全市场规模的56.2%,但随着混合办公模式暴露出以边界为中心的安全漏洞,云端安全支出正以17.2%的复合年增长率增长。联邦政府的零信任指令以及「云端优先战略」行政命令正在加速国防和民用机构采用云端原生技术。私人企业则受益于资本支出减少、统一的策略编配和持续合规。
大型企业采用以资料主权为驱动的混合模式,而中小企业则转向完全託管的云端安全服务边缘。 Oracle的零信任云端控制框架展示了身分管治、微隔离和加密如何整合以强化攻击面。随着多重云端复杂性的增加,能够自动建立策略和修復错误配置的供应商正日益受到青睐。
北美网路安全市场按产品类型(解决方案和服务)、部署类型(云端和本地部署)、组织规模(中小企业和大型企业)、最终用户(银行、金融服务和保险 (BFSI)、医疗保健、IT 和电信等)以及国家/地区进行细分。市场预测以美元计价。
其他福利:
- Excel格式的市场预测(ME)表
- 3个月的分析师支持
目录
第一章 引言
- 研究假设和市场定义
- 调查范围
第二章调查方法
第三章执行摘要
第四章 市场情势
- 市场概览
- 市场驱动因素
- 强制性资料外洩揭露法和攻击数量激增
- 云端迁移与零信任部署势头强劲
- 物联网/工业物联网终端正在各行各业迅速普及
- 美国联邦政府量子密码技术过渡期限
- 网路保险承保的保费和管理影响
- 人工智慧驱动的安全营运平台缩短了平均回应时间
- 市场限制
- 网路安全专业人员严重短缺
- 多厂商工具栈高成本且复杂
- 传统OT系统扩大了未託管的攻击面
- 运作分析的能源消耗限制了其应用。
- 产业价值链分析
- 监管环境
- 技术展望
- 产业吸引力-波特五力分析
- 新进入者的威胁
- 供应商的议价能力
- 买方的议价能力
- 替代品的威胁
- 竞争对手之间的竞争
- 影响市场的宏观经济因素
第五章 市场规模与成长预测
- 报价
- 解决方案
- 应用程式安全
- 云端安全
- 资料安全
- 身分和存取管理
- 基础设施保护
- 综合风险管理
- 网路安全设备
- 端点安全
- 其他解决方案
- 服务
- 专业服务
- 託管服务
- 解决方案
- 透过部署模式
- 云
- 本地部署
- 按组织规模
- 小型企业
- 大公司
- 最终用户
- BFSI
- 卫生保健
- 资讯科技和通讯
- 工业与国防
- 零售
- 能源与公共产业
- 製造业
- 其他最终用户
- 按国家/地区
- 美国
- 加拿大
- 墨西哥
第六章 竞争情势
- 市场集中度
- 策略趋势
- 市占率分析
- 公司简介
- Palo Alto Networks, Inc.
- Fortinet, Inc.
- CrowdStrike Holdings, Inc.
- Cisco Systems, Inc.
- Check Point Software Technologies Ltd.
- Zscaler, Inc.
- Okta, Inc.
- Cloudflare, Inc.
- SentinelOne, Inc.
- Tenable Holdings, Inc.
- Rapid7, Inc.
- Qualys, Inc.
- Proofpoint, Inc.
- Trend Micro Incorporated
- Sophos Group plc
- CyberArk Software Ltd.
- Imperva, Inc.
- F5, Inc.
- Forcepoint LLC
- Darktrace plc
- Bitdefender LLC
- Varonis Systems, Inc.
- Arctic Wolf Networks, Inc.
- Elastic NV
- Mandiant(Google Cloud)
第七章 投资分析
第八章:市场机会与未来趋势
- 閒置频段与未满足需求评估
The North America Cyber Security Market size is estimated at USD 95.75 billion in 2025, and is expected to reach USD 159.90 billion by 2030, at a CAGR of 10.80% during the forecast period (2025-2030).

Stringent federal and state regulations, the spread of sophisticated threats, and accelerated digital-transformation programs across critical industries are the primary growth engines. Mandatory breach-disclosure laws in all 50 U.S. states and new Securities and Exchange Commission reporting rules compel firms to invest in preventive controls instead of purely reactive incident response models. Spending is further fueled by the federal transition to post-quantum cryptography, which requires agencies and contractors to overhaul encryption systems by 2030-2035. The United States retains the lion's share of regional demand, yet Canada registers the fastest expansion as Bill C-26 tightens critical-system requirements and stimulates vendor activity. Across offerings, solutions still represent 65.5% of revenue, although managed and professional services are growing faster as enterprises outsource security operations to close skills gaps.
North America Cyber Security Market Trends and Insights
Mandatory Breach Disclosure Laws and Surging Attack Volumes
Regulatory scrutiny intensified when the SEC levied USD 7 million in penalties on four listed technology companies for deficient SolarWinds-related disclosures, underscoring that incomplete cyber-risk reporting now carries tangible financial consequences. Coupled with 583 enforcement actions and USD 8.2 billion in remedies during fiscal 2024, the climate pushes boards to treat cybersecurity as a core compliance function rather than a discretionary IT spend. At the same time, Mexico logged 42.4 million malware attempts in 2024-116,000 per day-reflecting the wider regional surge in threat volume that now hits manufacturing hardest. Because every U.S. state enforces a notification statute and federal rules require disclosure within four business days of a material incident, enterprises have shifted budgets toward continuous monitoring, automated detection, and breach-containment platforms that shorten response cycles and cap liability.
Cloud Migration and Zero-Trust Adoption Momentum
Zero-trust models replaced perimeter-centric strategies once federal Executive Orders and NIST SP 800-207 established identity-focused architectures as the public-sector default. Today, 60% of North American enterprises have an active zero-trust program, and 94% have deployed at least one element; the transition is inseparable from sustained cloud-adoption waves that re-shape network edges and authentication flows. Organizations implementing zero-trust within hybrid or multi-cloud environments report 152% ROI through diminished incident handling and policy-maintenance burdens, a finding that resonates with finance and healthcare entities balancing regulatory mandates with cost discipline. The confluence of cloud migration and zero-trust tooling propels demand for secure access service edge (SASE) and identity-and-access-management platforms, reinforcing a structural service opportunity for MSSPs that specialize in multi-cloud governance.
Acute Shortage of Skilled Cyber-Security Professionals
North America entered 2025 with 542,687 open cybersecurity positions, a 4% increase even after employer headcount cuts of 2.7% in 2024. Budget freezes struck 37% of firms, but 90% still reported material skill gaps, particularly in AI-enabled analytics and zero-trust configuration. Mexico alone needs 35,000 specialists by 2025, yet 65% of local organizations cite talent scarcity as their top barrier, triggering an 80% uptick in advanced-technology spending to compensate. Skills shortages expose enterprises to prolonged dwell times, and breaches blamed on understaffed teams averaged USD 4 million in direct losses, adding pressure to adopt managed detection and response services that wrap technology and expertise in subscription packages.
Other drivers and restraints analyzed in the detailed report include:
- Explosion of IoT/IIoT Endpoints Across Industry
- U.S. Federal Post-Quantum Cryptography Transition Deadlines
- Legacy OT Systems Expanding Unmanaged Attack Surface
For complete list of drivers and restraints, kindly check the Table Of Contents.
Segment Analysis
Solutions retained a 65.5% share of the North America cybersecurity market in 2024, yet services are on pace for 13.8% CAGR through 2030 as organizations outsource 24/7 monitoring to counter evolving threats. The services uptrend directly mitigates the skills shortage while giving firms rapid access to AI-driven analytics platforms. Professional services for quantum-safe cryptography assessments and zero-trust road-mapping have also risen. Managed detection and response illustrates this shift: eSentire now protects data for 2.5 million patients, underscoring demand in regulated fields.
The North America cybersecurity market size for managed services is expanding fastest among healthcare and mid-market manufacturing firms. Service-based consumption models help firms consolidate sprawling toolsets and secure board approval by treating cybersecurity as an operating expense. Vendors, in turn, bundle AI, threat intelligence, and human expertise, capturing sticky multiyear contracts and boosting recurring revenue visibility.
On-premise deployments still made up 56.2% of the North America cybersecurity market size in 2024, but cloud security spending is advancing at 17.2% CAGR as hybrid work exposes perimeter-centric gaps. Federal zero-trust mandates, coupled with executive orders on cloud-first strategies, accelerate cloud-native adoption in defense and civil agencies. For private-sector adopters, the pivot lowers capital expenditure, integrates policy orchestration, and enables continuous compliance.
Large enterprises operate hybrid models for data-sovereignty reasons, while SMEs leapfrog straight to fully managed cloud-security service edges. Oracle's framework for zero-trust cloud controls demonstrates how identity governance, micro-segmentation, and encryption converge to tighten attack surfaces. Vendors that automate policy creation and misconfiguration remediation find traction as multicloud complexity scales.
North America Cyber Security Market is Segmented by Offering (Solutions and Services), Deployment Mode (Cloud and On-Premise), Organization Size (Small and Medium Enterprises and Large Enterprises), End-User (BFSI, Healthcare, IT and Telecom, and More), and Country. The Market Forecasts are Provided in Terms of Value (USD).
List of Companies Covered in this Report:
- Palo Alto Networks, Inc.
- Fortinet, Inc.
- CrowdStrike Holdings, Inc.
- Cisco Systems, Inc.
- Check Point Software Technologies Ltd.
- Zscaler, Inc.
- Okta, Inc.
- Cloudflare, Inc.
- SentinelOne, Inc.
- Tenable Holdings, Inc.
- Rapid7, Inc.
- Qualys, Inc.
- Proofpoint, Inc.
- Trend Micro Incorporated
- Sophos Group plc
- CyberArk Software Ltd.
- Imperva, Inc.
- F5, Inc.
- Forcepoint LLC
- Darktrace plc
- Bitdefender LLC
- Varonis Systems, Inc.
- Arctic Wolf Networks, Inc.
- Elastic N.V.
- Mandiant (Google Cloud)
Additional Benefits:
- The market estimate (ME) sheet in Excel format
- 3 months of analyst support
TABLE OF CONTENTS
1 INTRODUCTION
- 1.1 Study Assumptions and Market Definition
- 1.2 Scope of the Study
2 RESEARCH METHODOLOGY
3 EXECUTIVE SUMMARY
4 MARKET LANDSCAPE
- 4.1 Market Overview
- 4.2 Market Drivers
- 4.2.1 Mandatory breach-disclosure laws and surging attack volumes
- 4.2.2 Cloud migration and zero-trust adoption momentum
- 4.2.3 Explosion of IoT/IIoT endpoints across industry
- 4.2.4 U.S. federal post-quantum cryptography transition deadlines
- 4.2.5 Cyber-insurance underwriting tying premiums to controls
- 4.2.6 AI-powered SecOps platforms cutting mean-time-to-respond
- 4.3 Market Restraints
- 4.3.1 Acute shortage of skilled cyber-security professionals
- 4.3.2 High cost and complexity of multi-vendor tool stacks
- 4.3.3 Legacy OT systems expanding unmanaged attack surface
- 4.3.4 Energy footprint of always-on analytics limiting adoption
- 4.4 Industry Value Chain Analysis
- 4.5 Regulatory Landscape
- 4.6 Technological Outlook
- 4.7 Industry Attractiveness - Porter's Five Forces Analysis
- 4.7.1 Threat of New Entrants
- 4.7.2 Bargaining Power of Suppliers
- 4.7.3 Bargaining Power of Buyers
- 4.7.4 Threat of Substitutes
- 4.7.5 Intensity of Competitive Rivalry
- 4.8 Impact of Macroeconomic Factors on the Market
5 MARKET SIZE AND GROWTH FORECASTS (VALUES)
- 5.1 By Offering
- 5.1.1 Solutions
- 5.1.1.1 Application Security
- 5.1.1.2 Cloud Security
- 5.1.1.3 Data Security
- 5.1.1.4 Identity and Access Management
- 5.1.1.5 Infrastructure Protection
- 5.1.1.6 Integrated Risk Management
- 5.1.1.7 Network Security Equipment
- 5.1.1.8 Endpoint Security
- 5.1.1.9 Other Solutions
- 5.1.2 Services
- 5.1.2.1 Professional Services
- 5.1.2.2 Managed Services
- 5.1.1 Solutions
- 5.2 By Deployment Mode
- 5.2.1 Cloud
- 5.2.2 On-Premise
- 5.3 By Organization Size
- 5.3.1 Small and Medium Enterprises (SMEs)
- 5.3.2 Large Enterprises
- 5.4 By End-user
- 5.4.1 BFSI
- 5.4.2 Healthcare
- 5.4.3 IT and Telecom
- 5.4.4 Industrial and Defense
- 5.4.5 Retail
- 5.4.6 Energy and Utilities
- 5.4.7 Manufacturing
- 5.4.8 Other End-users
- 5.5 By Country
- 5.5.1 United States
- 5.5.2 Canada
- 5.5.3 Mexico
6 COMPETITIVE LANDSCAPE
- 6.1 Market Concentration
- 6.2 Strategic Moves
- 6.3 Market Share Analysis
- 6.4 Company Profiles (includes Global level Overview, Market level overview, Core Segments, Financials as available, Strategic Information, Market Rank/Share for key companies, Products and Services, and Recent Developments)
- 6.4.1 Palo Alto Networks, Inc.
- 6.4.2 Fortinet, Inc.
- 6.4.3 CrowdStrike Holdings, Inc.
- 6.4.4 Cisco Systems, Inc.
- 6.4.5 Check Point Software Technologies Ltd.
- 6.4.6 Zscaler, Inc.
- 6.4.7 Okta, Inc.
- 6.4.8 Cloudflare, Inc.
- 6.4.9 SentinelOne, Inc.
- 6.4.10 Tenable Holdings, Inc.
- 6.4.11 Rapid7, Inc.
- 6.4.12 Qualys, Inc.
- 6.4.13 Proofpoint, Inc.
- 6.4.14 Trend Micro Incorporated
- 6.4.15 Sophos Group plc
- 6.4.16 CyberArk Software Ltd.
- 6.4.17 Imperva, Inc.
- 6.4.18 F5, Inc.
- 6.4.19 Forcepoint LLC
- 6.4.20 Darktrace plc
- 6.4.21 Bitdefender LLC
- 6.4.22 Varonis Systems, Inc.
- 6.4.23 Arctic Wolf Networks, Inc.
- 6.4.24 Elastic N.V.
- 6.4.25 Mandiant (Google Cloud)
7 INVESTMENT ANALYSIS
8 MARKET OPPORTUNITIES AND FUTURE TRENDS
- 8.1 White-Space and Unmet-Need Assessment








