 |
市场调查报告书
商品编码
1849997
证券交易即服务 (SECaaS):市场份额分析、行业趋势、统计数据和成长预测(2025-2030 年)SECaaS - Market Share Analysis, Industry Trends & Statistics, Growth Forecasts (2025 - 2030) |
||||||
※ 本网页内容可能与最新版本有所差异。详细情况请与我们联繫。
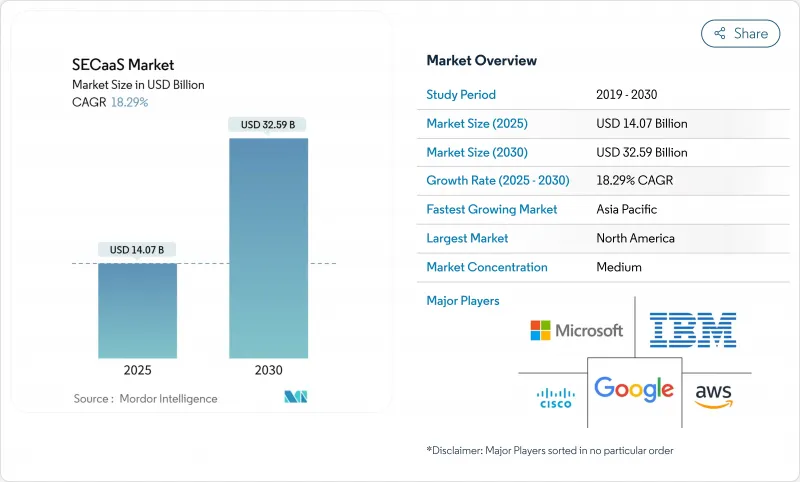
预计到 2025 年,SECaaS 市场规模将达到 140.7 亿美元,到 2030 年将达到 325.9 亿美元,年复合成长率为 18.3%。
企业董事会对网路韧性的日益重视、按需付费模式的普及以及工作负载向公共云端云和混合云端的稳步迁移,正推动采购预算转向云端交付的安全管理。那些已用整合式安全服务边缘平台取代以设备为中心的防御机制的组织发现,计量收费模式能够帮助他们将防御等级与实际流量保持一致。随着远距办公政策和云端原生应用程式的普及,身分、设备和 API 流量将整合到一个统一的策略框架中,这种需求将进一步加速成长。如今,安全即服务 (SECaaS) 市场正受益于人工智慧驱动的分析技术,这些技术能够缩短攻击者停留时间,并提供全端可观测性,从而将威胁情报转化为自动化的闭合迴路回应。
全球证券交易即服务 (SECaaS) 市场趋势与洞察
中小企业和大型企业采用云端技术的速度激增
随着企业放弃以边界为中心的防御技术,转而采用以身分为先的防御策略,不断增长的云端预算直接流入安全、通讯和即服务 (SECaaS) 市场。预计到 2028 年,印度公共云端服务市场规模将超过 242 亿美元,其中保全服务成长最快,复合年增长率高达 19%。中小企业无需投资建造专用安全营运中心 (SOC) 即可获得企业级安全防护,从而加快了其多租户平台供应商的部署。 98% 的金融机构已在使用至少一种云端服务,大多数机构将受监管的工作负载扩展到具有严格存取控制策略的第三方云端平台。随着每个新工作负载迁移到云端,SECaaS 订阅的附加率也会自动成长,从而在整个供应商领域产生复合式收入效应。
网路威胁日益复杂
攻击者现在利用人工智慧生成的网路钓鱼、自主恶意软体和大规模凭证洩漏宣传活动来突破基于特征码的工具的防御。银行正在透过将机器学习分析融入核心安全营运中心 (SOC) 工作流程,并将多年网路安全预算中越来越多的部分分配给云端原生威胁侦测引擎来应对这项挑战。医疗保健机构的资料外洩事件激增 256%,因此他们强制要求第三方服务必须符合 SOC 2 和 HIPAA 标准。威胁情报源集中化,侦测模型持续更新,自动化回应行动在几秒钟内即可在全球范围内编配。
资料居住和主权问题
跨境资料流动法规对统一采用云端技术构成挑战。欧洲的《一般资料保护规范》(GDPR) 和即将推出的《数位营运弹性法案》(Digital Operational Resilience Act) 迫使许多金融机构在区域边界内管理客户数据,限制了其全球云端部署选择。儘管多重云端策略看似诱人,但主权控制权的差异会导致安全架构碎片化和成本重复。新型主权云端服务承诺实现本地化处理,但企业仍担心可能被供应商锁定。
细分市场分析
身分和存取管理 (IAM) 仍然是安全、控制和即服务 (SECaaS) 市场的核心,预计到 2024 年将占总收入的 24.6%,因为云端优先架构将身分提升为预设控制层面。此细分市场的持续重要性反映了对最小权限原则的日益重视以及第三方开发者帐户的爆炸性增长。现代 IAM 套件的功能已超越了员工单一登入 (SSO),能够管理容器编排器产生的非个人身份,从而推动了授权数量和每位使用者平均收入的成长。云端存取安全仲介) 细分市场正以 19.0% 的复合年增长率成长,这主要得益于对检测未经授权的 SaaS 存取以及将预防资料外泄规则直接应用于 SaaS 到 SaaS 流量的需求。这些解决方案支柱的结合将推动向统一保全服务边缘的转型,在该边缘架构中,内联检测、存取控制和资料分类将共存于全球边缘网路中。安全邮件闸道和安全性 Web 闸道功能正在迁移到这些整合堆迭中,新一代 SIEM 正在重构其摄取管道以利用超大规模物件存储,从而降低每Terabyte 的成本并消除部署摩擦。
第二代漏洞管理工具直接整合到 CI/CD 管线中,从而实现了程式码、建置和运行时之间的闭环回馈。这种转变将安全态势与开发人员的工作流程紧密结合,并使安全合规即服务 (SECaaS) 市场与更广泛的平台化趋势保持一致。供应商现在提供预先核准的基础设施即程式码 (IaC) 范本、策略即程式码库和管线插件,确保风险可见性是固有的,而非附加的。最有效的销售策略围绕着可衡量的平均故障检测时间 (MTTD) 缩短、仪錶板主导的合规性以及将五点解决方案整合到一次合作中所带来的可证明的投资回报率 (ROI) 展开。
到2024年,公有云部署将占安全、控制和即服务 (SECaaS) 市场59.8%的份额,企业将利用公有云提供的交钥匙式全球接入点和弹性扩展能力。然而,随着监管机构在承包主权、延迟和性能标准之间权衡取舍,混合云的采用率正以19.8%的复合年增长率增长。目前,企业通常在公有云中部署身分仲介和策略引擎,同时在客户管理的基础架构上执行内嵌解密节点来处理敏感工作负载。这种架构多样性需要一个编配层,能够一次传播策略并使其在所有位置生效。
对于无法将流量元元资料暴露于共用环境的国防和关键基础设施营运商而言,私有云端即服务 (SECaaS) 执行个体将继续存在。新兴的产业蓝图允许在不违反资料持久性法规的前提下,跨信任域对入侵指标进行受控同步,这种方法由工业控制供应商与国家电脑紧急应变小组 (CERT) 合作率先提出。在预测期内,多重云端策略自动化将成为基本要求,这将推动云端平台和安全供应商之间的合作,旨在简化身分联合、金钥管理和遥测规范化。
区域分析
北美地区预计在2024年仍将占全球收入的37.1%,这反映出该地区聚集了众多超大规模资料中心营运商、网路安全创新者和早期采用者。美国网路安全与基础设施安全局 (CISA) 的联邦指导意见鼓励企业摒弃传统的VPN隧道,转而采用零信任的云端原生存取模式。金融机构目前在第三方实质审查调查中强制要求对安全服务边缘进行控制,从而增强了整个供应链的网路效应。加拿大和墨西哥正乘势而上,将区域资料保护法融入跨国资料流,并推动平台扩张。
在亚太地区,云端迁移蓝图正在协助各国实现数位经济目标,预计到2030年,其复合年增长率将达到19.4%。印度的公共云端收入已位居全球成长速度前列,而澳洲的IRAP框架正在向认证供应商开放政府采购管道。日本通讯业者在5G边缘部署方面处于领先地位,鼓励工业客户在远端工厂预先配置线上测试。儘管资料法规因地区而异,但能够证明其具备一致且区域适应性的加密金钥管理能力的供应商在竞标中拥有决定性优势。
欧洲市场对云端存取即服务(SECaaS)的需求持续强劲,这主导《一般资料保护规范》(GDPR)和《数位营运弹性法案》(Digital Operational Resilience Act)的实施,后者要求金融机构实施即时控制检验。德国和英国在投资融合平台方面处于领先地位,这些平台统一了云端存取、电子邮件安全和预防资料外泄。法国和义大利则透过国家网路弹性计画加快采购步伐,该计画拨款支持中小企业采用相关技术。此外,儘管拉丁美洲和中东及非洲地区的云端采用率领先,但随着经济情势趋于稳定,快速扩展的网路骨干网路和法律规范预计将推动SECaaS的普及。
其他福利:
- Excel格式的市场预测(ME)表
- 3个月的分析师支持
目录
第一章 引言
- 研究假设和市场定义
- 调查范围
第二章调查方法
第三章执行摘要
第四章 市场情势
- 市场概览
- 市场驱动因素
- 小型企业和大型企业对云端技术的采用率激增
- 网路威胁日益复杂
- 向远距办公和自带设备办公 (BYOD) 环境过渡
- 严格的全球资料保护条例
- DevSecOps 中 API主导的安全即程式码的需求
- 快速部署零信任保全服务边缘
- 市场限制
- 资料驻留和主权问题
- 管理多供应商订阅的复杂性
- 对延迟敏感的工作负载绕过了云端内联安全机制
- 缺乏基于使用量的收费标准
- 价值链分析
- 监管环境
- 技术展望
- 波特五力分析
- 供应商的议价能力
- 买方的议价能力
- 新进入者的威胁
- 替代品的威胁
- 竞争对手之间的竞争
- 投资分析
- 评估宏观经济趋势对市场的影响
第五章 市场规模与成长预测
- 透过解决方案
- 身分和存取管理 (IAM)
- 安全电子邮件网关
- 安全网路网关
- 云端存取安全仲介(CASB)
- 安全资讯和事件管理 (SIEM)
- 漏洞管理
- 其他解决方案
- 按部署模式
- 公共云端
- 私有云端
- 混合云端
- 按组织规模
- 大公司
- 小型企业
- 按最终用户行业划分
- BFSI
- 资讯科技和通讯
- 医疗保健和生命科学
- 政府和国防部
- 零售与电子商务
- 製造业
- 其他的
- 按地区
- 北美洲
- 美国
- 加拿大
- 墨西哥
- 欧洲
- 德国
- 英国
- 法国
- 义大利
- 西班牙
- 其他欧洲地区
- 亚太地区
- 中国
- 日本
- 印度
- 韩国
- 澳洲
- 亚太其他地区
- 南美洲
- 巴西
- 阿根廷
- 其他南美洲
- 中东和非洲
- 中东
- 沙乌地阿拉伯
- 阿拉伯聯合大公国
- 土耳其
- 其他中东地区
- 非洲
- 南非
- 埃及
- 奈及利亚
- 其他非洲地区
- 北美洲
第六章 竞争情势
- 市场集中度
- 策略趋势
- 市占率分析
- 公司简介
- Cisco Systems
- Zscaler
- Palo Alto Networks
- Microsoft
- Trend Micro
- Barracuda Networks
- IBM
- Proofpoint
- Sophos
- Forcepoint
- McAfee
- Symantec(Broadcom)
- Qualys
- Check Point Software
- Fortinet
- Cloudflare
- Okta
- Akamai
- Amazon Web Services
- Google Cloud
- CrowdStrike
- Rapid7
第七章 市场机会与未来展望
The SECaaS market size stands at USD 14.07 billion in 2025 and is forecast to reach USD 32.59 billion by 2030, expanding at an 18.3% CAGR.

Heightened board-level focus on cyber-resilience, the mainstreaming of consumption-based pricing, and the steady migration of workloads to public and hybrid clouds are steering procurement budgets toward cloud-delivered security controls. Organizations replacing appliance-centric defenses with converged Security Service Edge platforms find that the pay-as-you-go model keeps protection levels aligned with actual traffic volumes, a decisive advantage as edge locations proliferate. Demand accelerates further when remote-work policies and the proliferation of cloud-native applications bring identity, device, and API traffic under one policy framework. The SECaaS market now benefits from AI-infused analytics that shorten dwell time and provide full-stack observability, turning threat intelligence into automated, closed-loop response.
Global SECaaS Market Trends and Insights
Surging Cloud Adoption among SMEs and Enterprises
Growing cloud budgets channel directly into the SECaaS market as firms retire perimeter-centric technologies in favor of identity-first defenses. Public-cloud services in India are forecast to exceed USD 24.2 billion by 2028, with security services advancing the quickest at a 19% CAGR. Small and mid-size businesses gain enterprise-grade protection without dedicated SOC investments, accelerating vendor pipelines for multi-tenant platforms. Financial institutions illustrate the shift: 98% already consume at least one class of cloud service, and most now extend regulated workloads to third-party clouds under tightly governed access policies. Each new workload moved to the cloud automatically expands the attach rate for SECaaS subscriptions, creating a compounding revenue effect across the vendor landscape.
Rising Sophistication of Cyber Threats
Adversaries now wield AI-generated phishing, autonomous malware, and large-scale credential-stuffing campaigns that overwhelm signature-based tools. Banks have responded by embedding machine-learning analytics inside core SOC workflows, dedicating a growing share of multi-year cyber budgets to cloud-native threat detection engines. Healthcare providers, facing a 256% spike in hacking-related breaches, now stipulate SOC 2 and HIPAA alignment as entry requirements for any third-party service. The SECaaS market offers autonomy at scale: threat-intelligence feeds are centralized, detection models are continuously retrained, and automated response actions are orchestrated across global points of presence in seconds.
Data-Residency and Sovereignty Concerns
Cross-border data-flow restrictions challenge uniform cloud adoption. Europe's GDPR and impending Digital Operational Resilience Act compel many financial institutions to maintain customer data within regional boundaries, limiting the choice of global cloud locations. Multi-cloud strategies appear attractive, yet variations in sovereignty controls create fragmented security architectures that duplicate cost. While emerging sovereign-cloud offerings promise localized processing, enterprises remain cautious about potential vendor lock-in.
Other drivers and restraints analyzed in the detailed report include:
- Shift to Remote-Work and BYOD Environments
- Stringent Global Data-Protection Regulations
- Multi-Vendor Subscription-Management Complexity
For complete list of drivers and restraints, kindly check the Table Of Contents.
Segment Analysis
Identity-and-Access Management remains the anchor of the SECaaS market, contributing 24.6% of 2024 revenue as cloud-first architectures elevate identity to the default control plane. The segment's enduring relevance reflects tighter least-privilege mandates and the explosion of third-party developer accounts. Advanced IAM suites now extend beyond workforce SSO to govern non-human identities generated by container orchestrators, elevating license counts and average revenue per user. Less visible yet faster moving, the Cloud Access Security Broker segment is growing at a 19.0% CAGR, fueled by the need to discover unsanctioned SaaS and enforce data-loss-prevention rules directly in SaaS-to-SaaS traffic. Combined, these solution pillars underpin the transition toward unified Security Service Edge offerings, where in-line inspection, access control, and data classification co-reside on a global edge fabric. Secure Email Gateway and Secure Web Gateway functions are migrating into these converged stacks, while next-generation SIEM refactors ingestion pipelines to exploit hyperscaler object-storage, thus slashing per-terabyte economics and removing deployment friction.
Second-generation vulnerability-management tools, embedded directly into CI/CD pipelines, close feedback loops between code, build, and runtime. This segue ties security posture tightly to developer workflows and allies the SECaaS market with the broader Platform Engineering movement. Vendors now package pre-approved IaC templates, policy-as-code libraries, and pipeline plugins so that risk visibility becomes intrinsic rather than bolted-on. The most effective sales narratives pivot on measurable MTTD reductions, dashboard-driven compliance, and the demonstrable ROI of consolidating five point solutions into one contract.
Public-cloud deployments represented 59.8% of the 2024 SECaaS market as organizations capitalized on turnkey global points of presence and elastic scale. Nevertheless, hybrid-cloud adoption is posting a 19.8% CAGR as regulated entities weigh data-sovereignty mandates against latency and performance criteria. Enterprises now commonly place identity brokers and policy engines in public cloud while running inline decryption nodes on customer-managed infrastructure for sensitive workloads. Such architectural pluralism requires orchestration layers that can propagate policy once and enforce everywhere-capabilities that have become a differentiator in vendor bake-offs.
Private-cloud SECaaS instances persist for defense and critical-infrastructure operators who cannot expose traffic metadata to shared environments. Emerging industry blueprints allow controlled synchronization of indicators of compromise across trust domains without violating data-residency rules, an approach pioneered by industrial-control vendors working with national CERTs. Over the forecast horizon, multi-cloud policy automation will become table stakes, catalyzing alliances between cloud platforms and security vendors aimed at streamlining identity federation, key management, and telemetry normalization.
The SECaaS Market Report is Segmented by Solution (Identity and Access Management (IAM), Secure Email Gateway, and More), Deployment Model (Public Cloud, Private Cloud, and Hybrid Cloud), Organization Size (Large Enterprises and Small and Medium Enterprises (SMEs)), End-User Industry (BFSI, IT and Telecom, Healthcare and Life Sciences, and More), and Geography. The Market Forecasts are Provided in Terms of Value (USD).
Geography Analysis
North America retained 37.1% of global revenue in 2024, reflecting its concentration of hyperscalers, cybersecurity innovators, and early-adopter enterprises. Federal guidance from CISA urging the sunset of legacy VPN tunnels in favor of zero-trust, cloud-native access further cements demand. Financial institutions now mandate Security Service Edge controls during third-party due-diligence reviews, reinforcing network effects across supply chains. Canada and Mexico ride this momentum, integrating regional data-protection statutes with cross-border data flows to spur platform expansion.
Asia-Pacific is advancing at a 19.4% CAGR to 2030 as cloud-migration roadmaps underpin national digital-economy targets. India's public-cloud revenues already rank among the world's fastest-growing, and Australia's IRAP framework has opened government procurement channels for certified providers. Japan's telecom operators spearhead 5G edge rollouts, prompting industrial clients to pre-provision inline inspection to remote factories. Localized data regulations are diverse, but providers that can demonstrate consistent, region-aware encryption-key management gain a decisive bidding advantage.
Europe maintains robust demand, driven by GDPR and the emerging Digital Operational Resilience Act that obliges real-time control validation for financial entities. Germany and the United Kingdom lead investments in converged platforms that unify cloud access, email security, and data-loss prevention. France and Italy accelerate procurement through national cyber-resilience plans that allocate co-funding for SME adoption. Elsewhere, South America and the Middle East and Africa are earlier in their cloud journeys yet rapidly expanding internet backbones and regulatory frameworks, setting the stage for elevated SECaaS penetration rates as economic conditions stabilize.
- Cisco Systems
- Zscaler
- Palo Alto Networks
- Microsoft
- Trend Micro
- Barracuda Networks
- IBM
- Proofpoint
- Sophos
- Forcepoint
- McAfee
- Symantec (Broadcom)
- Qualys
- Check Point Software
- Fortinet
- Cloudflare
- Okta
- Akamai
- Amazon Web Services
- Google Cloud
- CrowdStrike
- Rapid7
Additional Benefits:
- The market estimate (ME) sheet in Excel format
- 3 months of analyst support
TABLE OF CONTENTS
1 INTRODUCTION
- 1.1 Study Assumptions and Market Definition
- 1.2 Scope of the Study
2 RESEARCH METHODOLOGY
3 EXECUTIVE SUMMARY
4 MARKET LANDSCAPE
- 4.1 Market Overview
- 4.2 Market Drivers
- 4.2.1 Surging cloud adoption among SMEs and enterprises
- 4.2.2 Rising sophistication of cyber threats
- 4.2.3 Shift to remote-work and BYOD environments
- 4.2.4 Stringent global data-protection regulations
- 4.2.5 API-driven "security-as-code" demand in DevSecOps
- 4.2.6 Rapid rollout of zero-trust Security Service Edge
- 4.3 Market Restraints
- 4.3.1 Data-residency and sovereignty concerns
- 4.3.2 Multi-vendor subscription-management complexity
- 4.3.3 Latency-sensitive workloads bypassing inline cloud security
- 4.3.4 Lack of usage-based billing standards
- 4.4 Value Chain Analysis
- 4.5 Regulatory Landscape
- 4.6 Technological Outlook
- 4.7 Porter's Five Forces Analysis
- 4.7.1 Bargaining Power of Suppliers
- 4.7.2 Bargaining Power of Buyers
- 4.7.3 Threat of New Entrants
- 4.7.4 Threat of Substitutes
- 4.7.5 Intensity of Competitive Rivalry
- 4.8 Investment Analysis
- 4.9 Assessment of the Impact of Macroeconomic Trends on the Market
5 MARKET SIZE AND GROWTH FORECASTS (VALUE)
- 5.1 By Solution
- 5.1.1 Identity and Access Management (IAM)
- 5.1.2 Secure Email Gateway
- 5.1.3 Secure Web Gateway
- 5.1.4 Cloud Access Security Broker (CASB)
- 5.1.5 Security Information and Event Management (SIEM)
- 5.1.6 Vulnerability Management
- 5.1.7 Other Solutions
- 5.2 By Deployment Model
- 5.2.1 Public Cloud
- 5.2.2 Private Cloud
- 5.2.3 Hybrid Cloud
- 5.3 By Organization Size
- 5.3.1 Large Enterprises
- 5.3.2 Small and Medium Enterprises (SMEs)
- 5.4 By End-User Industry
- 5.4.1 BFSI
- 5.4.2 IT and Telecom
- 5.4.3 Healthcare and Life Sciences
- 5.4.4 Government and Defense
- 5.4.5 Retail and E-commerce
- 5.4.6 Manufacturing
- 5.4.7 Others
- 5.5 By Geography
- 5.5.1 North America
- 5.5.1.1 United States
- 5.5.1.2 Canada
- 5.5.1.3 Mexico
- 5.5.2 Europe
- 5.5.2.1 Germany
- 5.5.2.2 United Kingdom
- 5.5.2.3 France
- 5.5.2.4 Italy
- 5.5.2.5 Spain
- 5.5.2.6 Rest of Europe
- 5.5.3 Asia-Pacific
- 5.5.3.1 China
- 5.5.3.2 Japan
- 5.5.3.3 India
- 5.5.3.4 South Korea
- 5.5.3.5 Australia
- 5.5.3.6 Rest of Asia-Pacific
- 5.5.4 South America
- 5.5.4.1 Brazil
- 5.5.4.2 Argentina
- 5.5.4.3 Rest of South America
- 5.5.5 Middle East and Africa
- 5.5.5.1 Middle East
- 5.5.5.1.1 Saudi Arabia
- 5.5.5.1.2 United Arab Emirates
- 5.5.5.1.3 Turkey
- 5.5.5.1.4 Rest of Middle East
- 5.5.5.2 Africa
- 5.5.5.2.1 South Africa
- 5.5.5.2.2 Egypt
- 5.5.5.2.3 Nigeria
- 5.5.5.2.4 Rest of Africa
- 5.5.1 North America
6 COMPETITIVE LANDSCAPE
- 6.1 Market Concentration
- 6.2 Strategic Moves
- 6.3 Market Share Analysis
- 6.4 Company Profiles (includes Global-level Overview, Market-level Overview, Core Segments, Financials as available, Strategic Information, Market Rank/Share, Products and Services, Recent Developments)
- 6.4.1 Cisco Systems
- 6.4.2 Zscaler
- 6.4.3 Palo Alto Networks
- 6.4.4 Microsoft
- 6.4.5 Trend Micro
- 6.4.6 Barracuda Networks
- 6.4.7 IBM
- 6.4.8 Proofpoint
- 6.4.9 Sophos
- 6.4.10 Forcepoint
- 6.4.11 McAfee
- 6.4.12 Symantec (Broadcom)
- 6.4.13 Qualys
- 6.4.14 Check Point Software
- 6.4.15 Fortinet
- 6.4.16 Cloudflare
- 6.4.17 Okta
- 6.4.18 Akamai
- 6.4.19 Amazon Web Services
- 6.4.20 Google Cloud
- 6.4.21 CrowdStrike
- 6.4.22 Rapid7
7 MARKET OPPORTUNITIES AND FUTURE OUTLOOK
- 7.1 White-space and Unmet-Need Assessment










