 |
市场调查报告书
商品编码
1852199
工业控制系统安全:市场份额分析、行业趋势、统计数据和成长预测(2025-2030 年)Industrial Control Systems Security - Market Share Analysis, Industry Trends & Statistics, Growth Forecasts (2025 - 2030) |
||||||
※ 本网页内容可能与最新版本有所差异。详细情况请与我们联繫。
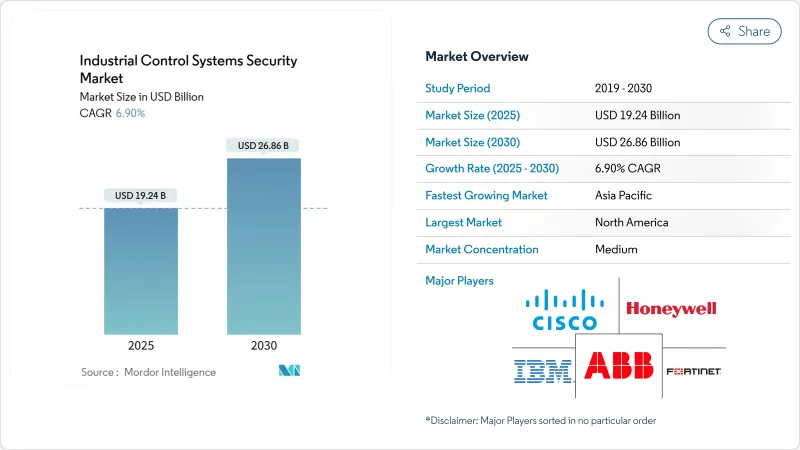
预计到 2025 年,工业控制系统安全市场规模将达到 192.4 亿美元,到 2030 年将达到 268.6 亿美元,预测期(2025-2030 年)复合年增长率为 6.90%。
董事会层级优先考虑操作技术网路弹性、IT-OT网路整合以及日益猖獗的勒索软体活动,这些因素共同推动了持续的需求。北美凭藉NERC CIP-013和CIRCIA的快速事件通报要求等法规,维持领先地位。亚太地区正经历快速成长,电力公司和离散製造业正在对其SCADA资产进行现代化改造,并大规模连接工业物联网(IIoT)设备。儘管解决方案仍然是重要的收入驱动因素,但託管安全服务也呈现两位数的成长,这表明在OT技能人才日益短缺的情况下,企业正在转向全天候外包监控。网路分段和深度封包检测是目前部署的主流技术,而随着託管历史资料库和远端维护入口网站的兴起,云端/远端存取保护也正在蓬勃发展。
全球工业控制系统安全市场趋势与洞察
加速工业物联网主导的营运技术连接,变革製造业安全
预计到2025年,全球将有750亿连网型设备,其中三分之一将安装在工厂内,这将使传统生产线面临前所未有的网路风险。欧洲和日本的离散製造企业正在整合视觉系统、机器人和预测性维护感测器,这需要进行东西向流量检测和零信任分段。这种日益增长的资料流给传统的边界防御带来了压力,迫使企业在乙太网路/IP、PROFINET和Modbus网路中部署通讯协定感知型侦测工具。供应商正在积极应对,推出适用于资源受限控制器的轻量级代理和深度检测(DPI)感测器,这些感测器能够在不中断生产週期的情况下分析专有的工业框架。随着IT和OT团队共同管理资产,对能够映射普渡安全等级0-3级并自动部署策略的统一仪錶板的需求日益增长。预算负责人正越来越多地将安全支出与整体设备效率(OEE)指标挂钩,从而强化以避免停机为核心的投资回报率(ROI)评估。
监理合规推动关键基础设施安全投资
北美NERC的CIP-013指令和欧盟的NIS2指令都规定了具有约束力的义务,涵盖从供应链风险管理到72小时事件报告等各个面向。公共产业、交通网和化工厂正在加速采购,以避免可能超过年收入2%的罚款。这些法规也将网路安全讨论从工程团队提升到执行委员会层面,缩短了提供可审核报告和证据收集服务的供应商的销售週期。整合商可以透过捆绑资产发现、配置监控和安全檔案传输功能,同时满足两项标准,并简化跨司法管辖区的合规性。保险公司要求在保单续保前提供ICS分段证明,并降低保费,这进一步推动了ICS安全市场的发展动能。
旧有系统整合难题阻碍了安全实施
现代防火墙和异常检测引擎必须适应已有20年历史、缺乏加密韧体和基于角色的存取控制的PLC。改装通常需要分阶段停机,这会影响电力分配和合约规定的服务等级协议。 46%的资产所有者需要长达六个月的时间来修补关键漏洞,延长了漏洞暴露的时间窗口。成本效益的考量延缓了全面微隔离计划,导致一些营运商转向部分实施方案,例如只读被动监控,这种方案虽然提供了可见性,但却保留了写入存取路径。
细分市场分析
预计到2024年,解决方案将占据68%的收入份额,市场规模将达到131亿美元。防火墙、通讯协定感知型入侵防御系统(IPS)、身分网关和漏洞扫描器构成了第一波普及浪潮的基石。随着供应商缩短签章更新周期并整合人工智慧分析技术以即时标记零日漏洞,相关支出正在稳步增长。工业控制系统安全市场目前正在涌现整合平台,这些平台能够以普渡大学层级采集日誌,并添加上下文资讯以更快地进行根本原因分析。
服务板块预计在2024年达到61亿美元,并将在2030年之前维持11.2%的复合年增长率,成为成长最快的板块。託管式侦测和回应服务将远端一级故障排查与现场事件处理人员结合,使工厂能够在满足72小时报告义务的同时保持运作。整合和部署合作伙伴负责连接不同的供应商技术堆迭,将资产清单对应到ISA/IEC 62443区域,然后配置分层控制。咨询团队透过攻击链模拟来评估成熟度,并制定与资本支出更新周期一致的分阶段蓝图。支援和维护合约确保韧体更新和定期规则集调整,帮助一家受严格监管的能源公司将平均修补时间缩短30%以上。
到2024年,网路安全将占收入的37%,营运商将优先考虑实体和虚拟隔离设备,这些设备能够过滤通讯协定并将流量镜像到被动收集器。零信任架构隔离人机介面 (HMI)、历史资料库和工程工作站,防止IT子网路之间的横向移动。威胁情报源被注入到工业级入侵指标 (IOC) 中,帮助安全营运中心 (SOC) 团队阻止恶意的营运技术 (OT) 特定命令序列。
随着工厂采用数位孪生技术和供应商辅助维护门户,云端/远端存取安全预计将以 12.5% 的复合年增长率 (CAGR) 实现最高成长。多因素身份验证网关、即时会话仲介和持续态势评估有助于应对互联网暴露端点带来的日益增长的风险。端点安全工具透过无代理监控来强化 PLC、RTU 和感测器,从而追踪韧体状态和记忆体完整性。应用层防御利用动态程式码分析来侦测 MES 和批次执行软体中的不安全调用,而资料库防火墙则保护时间序列运作资料免遭洩露。
区域分析
到2024年,北美将占全球销售额的33%。美国联邦在重大资料外洩事件后加强了监管力度,敦促资产所有者采纳美国网路安全和基础设施安全局(CISA)的「Shield Up」建议,并在规定期限内提交漏洞报告。对人手不足的泵站和风电场进行安全远端存取的投资正在加速。加拿大国家网路威胁评估警告称,敌对国家可能会扰乱能源出口,并敦促各省监管机构与北美电力可靠性委员会(NERC)的网路安全改进计划(CIP)框架保持一致。
亚太地区2025年至2030年的复合年增长率将达8.3%,位居全球之首。中国正将网路安全防护扩展到数千个变电站,将本土防火墙品牌与全球分析引擎结合。日本正在升级其机器人深度封包检测。韩国正在利用其5G骨干网,要求对控制指令进行毫秒加密和身分迭加。印度正在水力发电发电工程中更换串口转乙太网路转换器,并插入检测分接器,为国家级安全营运中心(SOC)提供资料。随着本地人才储备的成熟,东协中小企业正依赖厂商託管的安全营运中心。
随着NIS2将执法范围扩大到中型关键营业单位,欧洲仍然是至关重要的市场。德国联邦资讯安全局(BSI)推动跨行业漏洞咨询资讯共用,而法国国家资讯安全局(ANSSI)则制定了分段检查清单。英国公用事业公司正在试行基于人工智慧的预测异常引擎,以满足英国天然气和电力市场监管局(Ofgem)的弹性目标。西班牙和义大利可再生能源的成长推动了对认证仲介的需求,以管理逆变器原始设备製造商(OEM)的现场维护。拉丁美洲以及中东和非洲地区正在稳步采取防御措施。巴西公用事业公司正在实施PLC韧体的供应链认证,而墨西哥湾沿岸的管道营运商正在部署欺骗电网以阻止侦察。
其他福利:
- Excel格式的市场预测(ME)表
- 3个月的分析师支持
目录
第一章 引言
- 研究假设和市场定义
- 调查范围
第二章调查方法
第三章执行摘要
第四章 市场情势
- 市场概览
- 市场驱动因素
- 加速离散製造业中工业物联网主导的营运技术连结(欧盟和日本)
- 关键基础设施营运商必须遵守NERC CIP-013和欧盟NIS2标准
- 亚洲电力和水务公司老旧SCADA/DCS资产现代化改造
- 美国和中东地区石油和天然气管道遭受勒索软体攻击激增
- 分散式可再生能源的发展需要远端存取保护
- 采用云端託管历史资料库和远端维护平台
- 市场限制
- 传统PLC维修成本高且停机时间长
- 东协中型製造商缺乏营运技术技能和网路安全人才
- 专有工业通讯协定的互通性有限
- 重复的IT/OT工具栈会延误采购(「安全疲劳」)
- 价值/供应链分析
- 监理与技术展望
- 波特五力分析
- 供应商的议价能力
- 买方的议价能力
- 新进入者的威胁
- 替代品的威胁
- 竞争对手之间的竞争
- 投资分析
第五章 市场规模与成长预测
- 按组件
- 解决方案
- 防火墙和入侵防御系统
- 身分和存取管理
- 防毒和反恶意软体
- 安全和漏洞管理
- 预防资料外泄和恢復
- 其他解决方案
- 服务
- 咨询与评估
- 整合与部署
- 支援与维护
- 託管安全服务
- 解决方案
- 按安全类型
- 网路安全
- 端点安全
- 应用程式安全
- 资料库安全
- 云端/远端存取安全
- 按控制系统类型
- 监控与数据采集(SCADA)
- 分散式控制系统(DCS)
- 可程式逻辑控制器(PLC)
- 其他控制系统
- 按最终用户行业划分
- 车
- 化工/石油化工
- 电力与公用事业
- 石油和天然气
- 食品/饮料
- 製药
- 用水和污水
- 采矿和金属
- 运输/物流
- 其他行业
- 按地区
- 北美洲
- 美国
- 加拿大
- 墨西哥
- 欧洲
- 英国
- 德国
- 法国
- 义大利
- 其他欧洲地区
- 亚太地区
- 中国
- 日本
- 印度
- 韩国
- 亚太其他地区
- 中东
- 以色列
- 沙乌地阿拉伯
- 阿拉伯聯合大公国
- 土耳其
- 其他中东地区
- 非洲
- 南非
- 埃及
- 其他非洲地区
- 南美洲
- 巴西
- 阿根廷
- 其他南美洲国家
- 北美洲
第六章 竞争情势
- 市场集中度
- 策略趋势
- 市占率分析
- 公司简介
- Honeywell International Inc.
- Cisco Systems Inc.
- IBM Corporation
- Fortinet Inc.
- ABB Ltd.
- Rockwell Automation Inc.
- Dragos Inc.
- Nozomi Networks Inc.
- Palo Alto Networks Inc.
- Check Point Software Technologies Ltd.
- Darktrace Holdings Limited
- Broadcom Inc.(Symantec)
- Trellix
- Schneider Electric SE
- Siemens AG
- Kaspersky Lab
- GE Vernova(GE Digital)
- Claroty Ltd.
- Trend Micro Inc.
- AhnLab Inc.
第七章 市场机会与未来展望
The Industrial Control Systems Security Market size is estimated at USD 19.24 billion in 2025, and is expected to reach USD 26.86 billion by 2030, at a CAGR of 6.90% during the forecast period (2025-2030).

Board-level prioritization of operational technology cyber-resilience, convergence of IT-OT networks, and escalating ransomware activity underpin sustained demand. North America retains leadership thanks to regulations such as NERC CIP-013 and the rapid incident-reporting mandate in CIRCIA. Asia-Pacific delivers the steepest growth as utilities and discrete manufacturers modernize SCADA assets and connect IIoT devices at scale. Solutions remain the revenue backbone, yet double-digit expansion of managed security services shows enterprises shifting toward 24/7 outsourced monitoring amid an acute OT-skilled labor shortage. Network segmentation and deep-packet inspection dominate current deployments, while cloud/remote-access protection gains momentum with the rise of hosted historians and remote maintenance portals.
Global Industrial Control Systems Security Market Trends and Insights
Accelerating IIoT-driven OT Connectivity Transforms Manufacturing Security
One-third of the 75 billion connected devices expected in 2025 will sit inside factories, exposing legacy production lines to unprecedented cyber risk. European and Japanese discrete manufacturers are integrating vision systems, robotics, and predictive-maintenance sensors that require east-west traffic inspection and zero-trust segmentation. This intensified data flow strains traditional perimeter defenses and forces deployment of protocol-aware detection tools inside Ethernet/IP, PROFINET, and Modbus networks. Vendors respond with lightweight agents for resource-constrained controllers and DPI sensors that parse proprietary industrial frames without disrupting cycle times. As IT and OT teams co-manage assets, demand rises for unified dashboards that map Purdue levels 0-3 and automate policy rollouts. Budget holders increasingly tie security spend to overall equipment effectiveness metrics, reinforcing ROI narratives around avoided downtime.
Regulatory Compliance Drives Critical-Infrastructure Security Investment
NERC CIP-013 in North America and the EU's NIS2 Directive impose binding obligations ranging from supply-chain risk management to 72-hour incident reporting. Utilities, transport networks, and chemical plants accelerate procurements to avoid fines that can exceed 2% of annual turnover. The regulations also elevate cyber discussions from engineering teams to executive committees, compressing sales cycles for vendors offering audit-ready reporting and evidence collection. Integrators bundle asset-discovery, configuration-monitoring, and secure-file-transfer capabilities to meet both standards concurrently, simplifying multi-jurisdiction compliance. Momentum in the ICS security market is further boosted by insurers demanding proof of ICS segmentation before renewing coverage or lowering premiums.
Legacy System Integration Challenges Hinder Security Implementation
Modern firewalls and anomaly-detection engines must adapt to 20-year-old PLCs that lack encrypted firmware or role-based access controls. Retrofitting often requires staged shutdowns that jeopardize output quotas and contractual service-level agreements. Forty-six percent of asset owners need up to six months to patch a critical vulnerability, prolonging exposure windows. Cost-benefit debates delay full micro-segmentation projects, pushing some operators toward partial implementations like read-only passive monitoring, which offers visibility yet leaves write-access pathways unguarded.
Other drivers and restraints analyzed in the detailed report include:
- Aging Infrastructure Modernization Creates Security Imperatives
- Ransomware Targeting Critical Infrastructure Drives Security Urgency
- Cybersecurity Talent Gap Constrains Security Implementation
For complete list of drivers and restraints, kindly check the Table Of Contents.
Segment Analysis
In 2024, the industrial control systems security market size attributed USD 13.1 billion to solutions, equal to a 68% revenue share. Firewalls, protocol-aware IPS, identity gateways, and vulnerability scanners formed the backbone of first-wave deployments. Spending grows steadily as vendors embed artificial-intelligence analytics that cut signature-update cycles and flag zero-day behaviors in real time. The industrial control systems security market now witnesses converged platforms that ingest logs across Purdue levels, enriching context for quicker root-cause correlation.
The services segment, valued at USD 6.1 billion in 2024, records the fastest 11.2% CAGR through 2030. Managed detection and response offerings combine remote tier-1 triage and on-site incident-handlers, allowing plants to maintain uptime while meeting 72-hour reporting mandates. Integration and deployment partners bridge heterogeneous vendor stacks, mapping asset inventories against ISA/IEC 62443 zones before configuring layered controls. Consulting teams benchmark maturity via kill-chain simulations, then craft phased roadmaps tied to capex refresh cycles. Support and maintenance contracts secure firmware updates and periodic rule-set tuning, reducing mean time to patch by more than 30% in highly regulated energy utilities.
Network security anchors 37% of 2024 revenues as operators prioritize physical and virtual segmentation appliances that filter protocol commands and mirror traffic to passive collectors. Zero-trust architectures isolate HMIs, historians, and engineering workstations, preventing lateral movement from IT subnets. Threat-intelligence feeds inject industrial IOCs, helping SOC teams block malicious OT-specific command sequences.
Cloud/remote-access security posts a 12.5% forecast CAGR, the highest among categories, as plants adopt digital twins and vendor-assisted maintenance portals. Multi-factor identity gateways, just-in-time session brokers, and continuous posture assessment counter the heightened risk from internet-exposed endpoints. Endpoint security tools harden PLCs, RTUs, and sensors with agentless monitoring that tracks firmware states and memory integrity. Application-layer defenses use dynamic code analysis to spot unsafe calls within MES and batch-execution software, while database firewalls safeguard time-series operational data against exfiltration.
The Industrial Control Systems ICS Security Market Report is Segmented by Component (Solutions, Services), Security Type (Network Security, Endpoint Security, Application Security, and More), Control System Type (SCADA, Distributed Control System (DCS), and More), End-User Industry (Automotive, Chemical & Petrochemical, Power and Utilities, and More), and Geography. The Market Forecasts are Provided in Terms of Value (USD).
Geography Analysis
North America generated 33% of 2024 global revenue. Federal scrutiny intensified after headline breaches, prompting asset owners to adopt CISA's Shields-Up advisories and submit vulnerability reports within stipulated windows. Investments accelerate around secure remote access for sparsely staffed pumping stations and wind farms. Canada's National Cyber Threat Assessment warns that hostile states could disrupt energy exports, pushing provincial regulators to align with NERC CIP frameworks.
Asia-Pacific records the highest 8.3% CAGR from 2025 to 2030. China scales cyber-hygiene across thousands of new substations, blending domestic firewall brands with global analytics engines. Japan upgrades robot-dense automotive lines, coupling deep-packet inspection appliances with OT-aware SIEM integrations. South Korea leverages its 5G backbone, necessitating encryption and identity overlays for millisecond-latency control commands. India replaces serial-to-Ethernet converters in hydro projects, inserting inspection taps that feed national-level SOCs. ASEAN SMEs rely on vendor-hosted SOCs as local talent pipelines mature.
Europe remains a pivotal market as NIS2 expands enforcement to medium-sized critical entities. Germany's BSI drives cross-sector vulnerability advisory sharing, while France's ANSSI prescribes segmentation checklists. United Kingdom utilities pilot AI-based predictive anomaly engines to meet Ofgem resilience targets. Renewable-energy growth in Spain and Italy sparks demand for authentication brokers that manage inverter OEMs during field maintenance. Latin America and Middle East & Africa steadily adopt defenses; Brazilian utilities implement supply-chain attestation for PLC firmware, and Gulf pipeline operators deploy deception grids to deter reconnaissance.
- Honeywell International Inc.
- Cisco Systems Inc.
- IBM Corporation
- Fortinet Inc.
- ABB Ltd.
- Rockwell Automation Inc.
- Dragos Inc.
- Nozomi Networks Inc.
- Palo Alto Networks Inc.
- Check Point Software Technologies Ltd.
- Darktrace Holdings Limited
- Broadcom Inc. (Symantec)
- Trellix
- Schneider Electric SE
- Siemens AG
- Kaspersky Lab
- GE Vernova (GE Digital)
- Claroty Ltd.
- Trend Micro Inc.
- AhnLab Inc.
Additional Benefits:
- The market estimate (ME) sheet in Excel format
- 3 months of analyst support
TABLE OF CONTENTS
1 INTRODUCTION
- 1.1 Study Assumptions and Market Definition
- 1.2 Scope of the Study
2 RESEARCH METHODOLOGY
3 EXECUTIVE SUMMARY
4 MARKET LANDSCAPE
- 4.1 Market Overview
- 4.2 Market Drivers
- 4.2.1 Accelerating IIoT-driven OT Connectivity in Discrete Manufacturing (EU and Japan)
- 4.2.2 Mandatory NERC CIP-013 and EU NIS2 Compliance for Critical Infrastructure Operators
- 4.2.3 Modernization of Ageing SCADA/DCS Assets in Asian Power and Water Utilities
- 4.2.4 Surge in Ransomware Attacks on Oil and Gas Pipelines (US and Middle East)
- 4.2.5 Growth of Distributed Renewables Requiring Remote-Access Protection
- 4.2.6 Adoption of Cloud-hosted Historians and Remote Maintenance Platforms
- 4.3 Market Restraints
- 4.3.1 High Retrofit Costs and Downtime for Legacy PLCs
- 4.3.2 OT-Skilled Cyber-Talent Shortage in Mid-size ASEAN Manufacturers
- 4.3.3 Limited Interoperability of Proprietary Industrial Protocols
- 4.3.4 Procurement Delays from IT/OT Tool-Stack Overlap ("Security Fatigue")
- 4.4 Value / Supply-Chain Analysis
- 4.5 Regulatory and Technological Outlook
- 4.6 Porter's Five Forces Analysis
- 4.6.1 Bargaining Power of Suppliers
- 4.6.2 Bargaining Power of Buyers
- 4.6.3 Threat of New Entrants
- 4.6.4 Threat of Substitutes
- 4.6.5 Intensity of Competitive Rivalry
- 4.7 Investment Analysis
5 MARKET SIZE AND GROWTH FORECASTS (VALUE)
- 5.1 By Component
- 5.1.1 Solutions
- 5.1.1.1 Firewall and IPS
- 5.1.1.2 Identity and Access Management
- 5.1.1.3 Antivirus and Antimalware
- 5.1.1.4 Security and Vulnerability Management
- 5.1.1.5 Data Loss Prevention and Recovery
- 5.1.1.6 Other Solutions
- 5.1.2 Services
- 5.1.2.1 Consulting and Assessment
- 5.1.2.2 Integration and Deployment
- 5.1.2.3 Support and Maintenance
- 5.1.2.4 Managed Security Services
- 5.1.1 Solutions
- 5.2 By Security Type
- 5.2.1 Network Security
- 5.2.2 Endpoint Security
- 5.2.3 Application Security
- 5.2.4 Database Security
- 5.2.5 Cloud/Remote Access Security
- 5.3 By Control System Type
- 5.3.1 Supervisory Control and Data Acquisition (SCADA)
- 5.3.2 Distributed Control System (DCS)
- 5.3.3 Programmable Logic Controller (PLC)
- 5.3.4 Other Control Systems
- 5.4 By End-user Industry
- 5.4.1 Automotive
- 5.4.2 Chemical and Petrochemical
- 5.4.3 Power and Utilities
- 5.4.4 Oil and Gas
- 5.4.5 Food and Beverage
- 5.4.6 Pharmaceuticals
- 5.4.7 Water and Wastewater
- 5.4.8 Mining and Metals
- 5.4.9 Transportation and Logistics
- 5.4.10 Other Industries
- 5.5 By Geography
- 5.5.1 North America
- 5.5.1.1 United States
- 5.5.1.2 Canada
- 5.5.1.3 Mexico
- 5.5.2 Europe
- 5.5.2.1 United Kingdom
- 5.5.2.2 Germany
- 5.5.2.3 France
- 5.5.2.4 Italy
- 5.5.2.5 Rest of Europe
- 5.5.3 Asia-Pacific
- 5.5.3.1 China
- 5.5.3.2 Japan
- 5.5.3.3 India
- 5.5.3.4 South Korea
- 5.5.3.5 Rest of Asia-Pacific
- 5.5.4 Middle East
- 5.5.4.1 Israel
- 5.5.4.2 Saudi Arabia
- 5.5.4.3 United Arab Emirates
- 5.5.4.4 Turkey
- 5.5.4.5 Rest of Middle East
- 5.5.5 Africa
- 5.5.5.1 South Africa
- 5.5.5.2 Egypt
- 5.5.5.3 Rest of Africa
- 5.5.6 South America
- 5.5.6.1 Brazil
- 5.5.6.2 Argentina
- 5.5.6.3 Rest of South America
- 5.5.1 North America
6 COMPETITIVE LANDSCAPE
- 6.1 Market Concentration
- 6.2 Strategic Moves
- 6.3 Market Share Analysis
- 6.4 Company Profiles (includes Global-level Overview, Market-level overview, Core Segments, Financials, Strategic Information, Market Rank/Share, Products and Services, Recent Developments)
- 6.4.1 Honeywell International Inc.
- 6.4.2 Cisco Systems Inc.
- 6.4.3 IBM Corporation
- 6.4.4 Fortinet Inc.
- 6.4.5 ABB Ltd.
- 6.4.6 Rockwell Automation Inc.
- 6.4.7 Dragos Inc.
- 6.4.8 Nozomi Networks Inc.
- 6.4.9 Palo Alto Networks Inc.
- 6.4.10 Check Point Software Technologies Ltd.
- 6.4.11 Darktrace Holdings Limited
- 6.4.12 Broadcom Inc. (Symantec)
- 6.4.13 Trellix
- 6.4.14 Schneider Electric SE
- 6.4.15 Siemens AG
- 6.4.16 Kaspersky Lab
- 6.4.17 GE Vernova (GE Digital)
- 6.4.18 Claroty Ltd.
- 6.4.19 Trend Micro Inc.
- 6.4.20 AhnLab Inc.
7 MARKET OPPORTUNITIES AND FUTURE OUTLOOK
- 7.1 White-space and Unmet-Need Assessment












