 |
市场调查报告书
商品编码
1721385
云端保全市场 (~2035年):保全类型·零组件·展开·终端用户·企业规模·主要各地区的产业趋势与全球预测Cloud Security Market Till 2035: Distribution by Type of Security, by Type of Component, by Type of Deployment, by Type of End-User, by Company Size, and Key Geographical Regions Industry Trends and Global Forecasts. |
||||||
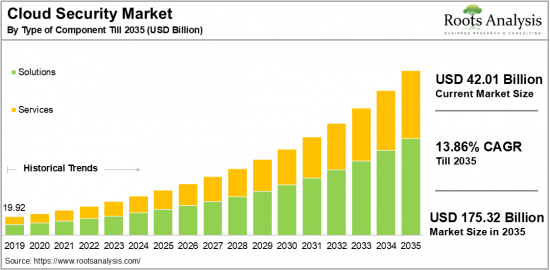
预计到 2035 年,全球云端安全市场规模将从目前的 420.1 亿美元成长至 1,753.2 亿美元,预测期内复合年增长率为 13.86%。
云端保全的市场机会:各市场区隔
保全类别
- 业务连续性与灾难復原
- 云端资料库安全
- 云端加密
- 资料遗失防护 (DLP)
- 电子邮件与 Web 安全
- 身分和存取管理 (IAM)
- 网路安全
- 安全资讯与事件管理 (SIEM)
- 虚拟化
各元件类型
- 服务
- 解决方案
各部署
- 混合
- 私人
- 公共
各终端用户
- 银行
- 能源&公共事业
- 金融
- 政府机关
- IT·通讯
- 医疗保健&生命科学
- 製造
- 零售
- 保全·保险 (BFSI)
- 其他
不同企业规模
- 大企业
- 中小企业
各地区
- 北美
- 美国
- 加拿大
- 墨西哥
- 其他的北美各国
- 欧洲
- 奥地利
- 比利时
- 丹麦
- 法国
- 德国
- 爱尔兰
- 义大利
- 荷兰
- 挪威
- 俄罗斯
- 西班牙
- 瑞典
- 瑞士
- 英国
- 其他欧洲各国
- 亚洲
- 中国
- 印度
- 日本
- 新加坡
- 韩国
- 其他亚洲各国
- 南美
- 巴西
- 智利
- 哥伦比亚
- 委内瑞拉
- 其他的南美各国
- 中东·北非
- 埃及
- 伊朗
- 伊拉克
- 以色列
- 科威特
- 沙乌地阿拉伯
- UAE
- 其他的中东·北非各国
- 全球其他地区
- 澳洲
- 纽西兰
- 其他的国家
云端安全市场:成长与趋势
云端安全(云端运算安全)包括一系列旨在保护与云端运算相关的应用程式、资料和基础设施的控制措施和策略。它可以防止资料外洩、敏感资讯遗失以及应用程式介面 (API) 漏洞等问题。云端客户和云端服务供应商对安全环境的需求日益增长,这推动了云端安全服务的普及。
由于云端服务(尤其是云端储存在各行各业的广泛应用),云端安全产业正在经历显着成长。随着企业纷纷转向云端平台以获得更好的可扩展性、成本节约和远端办公支持,对强大的安全解决方案的需求也日益增长,以保护敏感资料和应用程式。推动这一成长的关键因素包括网路威胁的增加、合规性需求以及防止资料外洩的需求。云端安全性涵盖一系列解决方案,包括身分识别和存取管理、资料加密、云端运算中的威胁侦测以及合规性管理。
本报告提供全球云端保全的市场调查、彙整市场概要,背景,市场影响因素的分析,市场规模的转变·预测,各种区分·各地区的详细分析,竞争情形,主要企业简介等资讯。
目录
章节I:报告概要
第1章 序文
第2章 调查手法
第3章 市场动态
第4章 宏观经济指标
章节II:定性性的洞察
第5章 摘要整理
第6章 简介
第7章 法规情势
章节III:市场概要
第8章 主要企业的总括的资料库
第9章 竞争情形
第10章 閒置频段分析
第11章 竞争分析
第12章 云端保全市场上Start-Ups生态系统
第4章 企业简介
第13章 企业简介
- 章概要
- Amazon
- Amazon Web Services
- Armor Defense
- Broadcom
- CA Technologies
- Check Point Software Technologies
- Cisco Systems
- Extreme Networks
- F5
- Fortinet
- Forcepoint
- IBM
- Imperva
- Intel
- Kaspersky Labs
- McAfee
- Microsoft
- Okta
第5章 市场趋势
第14章 大趋势分析
第15章 未满足需求分析
第16章 专利分析
第17章 最近的趋势
第6章 市场机会分析
第18章 全球云端保全市场
第19章 保全类别的市场机会
第20章 各零件的市场机会
第21章 各部署的市场机会
第22章 各终端用户的市场机会
第23章 北美云端保全的市场机会
第24章 欧洲的云端保全的市场机会
第25章 亚洲的云端保全的市场机会
第26章 中东·北非的云端保全的市场机会
第27章 南美的云端保全的市场机会
第28章 全球其他地区的云端保全的市场机会
第29章 市场集中分析:各主要企业分布
第30章 邻近市场分析
第7章 策略工具
第31章 主要成功策略
第32章 波特的五力分析
第33章 SWOT分析
第34章 价值链分析
第35章 ROOTS的策略性建议
第8章 其他的垄断的洞察
第36章 来自1次调查的洞察
第37章 报告书的结论
第9章 附录
第38章 表格形式资料
第39章 企业·团体一览
第40章 客制化的机会
第41章 ROOTS订阅服务
第42章 着者详细内容
GLOBAL CLOUD SECURITY MARKET: OVERVIEW
As per Roots Analysis, the global cloud security market size is estimated to grow from USD 42.01 billion in the current year to USD 175.32 billion by 2035, at a CAGR of 13.86% during the forecast period, till 2035.
The opportunity for cloud security market has been distributed across the following segments:

Type of Security
- Business Continuity and Disaster Recovery
- Cloud Database Security
- Cloud Encryption
- Data Loss Prevention (DLP)
- Email and Web Security
- Identity and Access Management (IAM)
- Network Security
- Security Information and Event Management (SIEM)
- Virtualization
Type of Component
- Services
- Solutions
Type of Deployment
- Hybrid
- Private
- Public
Type of End User
- Banking
- Energy and Utilities
- Finance
- Government
- IT and Telecommunication
- Healthcare and Life Sciences
- Manufacturing
- Retail
- Security and Insurance (BFSI)
- Others
Company Size
- Large Enterprises
- Small and Medium-sized Enterprises (SMEs)
Geographical Regions
- North America
- US
- Canada
- Mexico
- Other North American countries
- Europe
- Austria
- Belgium
- Denmark
- France
- Germany
- Ireland
- Italy
- Netherlands
- Norway
- Russia
- Spain
- Sweden
- Switzerland
- UK
- Other European countries
- Asia
- China
- India
- Japan
- Singapore
- South Korea
- Other Asian countries
- Latin America
- Brazil
- Chile
- Colombia
- Venezuela
- Other Latin American countries
- Middle East and North Africa
- Egypt
- Iran
- Iraq
- Israel
- Kuwait
- Saudi Arabia
- UAE
- Other MENA countries
- Rest of the World
- Australia
- New Zealand
- Other countries
CLOUD SECURITY MARKET: GROWTH AND TRENDS
Cloud security, or cloud computing security, involves various controls and policies aimed at protecting applications, data, and the infrastructure associated with cloud computing. It prevents issues like data breaches, the loss of sensitive information, and weaknesses in application programming interfaces (APIs). The rising demand for secure environments from both cloud clients and providers is driving the increased adoption of cloud security services.
The cloud security sector is witnessing significant growth, driven by the widespread use of cloud services, particularly cloud storage, across diverse industries. Businesses are moving to cloud platforms for better scalability, cost savings, and support for remote work, which heightens the need for robust security solutions to safeguard sensitive data and applications. Key elements fueling this growth include an increase in cyber threats, the need for compliance with regulations, and the necessity to protect against data breaches. Cloud security includes a variety of solutions, such as identity and access management, data encryption, threat detection within cloud computing, and compliance management.
CLOUD SECURITY MARKET: KEY SEGMENTS
Market Share by Type of Security
Based on the type of security, the global cloud security market is segmented into business continuity and disaster recovery, cloud database security, cloud encryption, data loss prevention (DLP), email and web security, identity and access management (IAM), network security, security information and event management (SIEM), virtualization. According to our estimates, currently, cloud database security segment captures the majority share of the market. This can be attributed to the increasing amount of data generated across various industries and a heightened awareness of data protection stemming from significant data breaches. However, cloud encryption segment is anticipated to grow at a higher CAGR during the forecast period.
Market Share by Type of Component
Based on the type of component, the cloud security market is segmented into services and solutions. According to our estimates, currently, solutions segment captures the majority share of the market. This can be attributed to the escalating complexity of cyber threats and the need for comprehensive security strategies. These strategies encompass various cybersecurity solutions for cloud environments, such as IAM, DLP, SIEM, and encryption. However, services segment is anticipated to grow at a higher CAGR during the forecast period.
Market Share by Type of Deployment
Based on the type of deployment, the cloud security market is segmented into hybrid, private and public. According to our estimates, currently, private cloud segment captures the majority share of the market. This can be attributed to the organizations' desire for greater control and security over their sensitive information as businesses progressively shift critical applications to private infrastructures, which ensures reliability and adherence to regulatory requirements. However, hybrid cloud segment is anticipated to grow at a higher CAGR during the forecast period.
Market Share by Type of End-User
Based on the type of end-user, the cloud security market is segmented into banking, energy and utilities, finance, government, IT and telecommunication, healthcare and life sciences, manufacturing, retail, security and insurance (BFSI), and others. According to our estimates, currently, banking segment captures the majority share of the market. This can be attributed to the major financial and reputational risks that arise from security breaches in the banking industry. The critical necessity for strong security measures in this sector is a result of the large volume of monetary transactions and sensitive customer information processed on a daily basis. However, healthcare and life sciences segment is anticipated to grow at a higher CAGR during the forecast period.
Market Share by Company Size
Based on the company, the cloud security market is segmented into large and small and medium enterprise. According to our estimates, currently, large enterprises segment captures the majority share of the market. However, small and medium enterprise segment is anticipated to grow at a higher CAGR during the forecast period.
Market Share by Geographical Regions
Based on the geographical regions, the cloud security market is segmented into North America, Europe, Asia, Latin America, Middle East and North Africa, and Rest of the World. According to our estimates, currently, North America captures the majority share of the market. This can be attributed to the presence of several leading cloud service providers and cybersecurity firms in the region, such as AWS, Microsoft Azure, and Google Cloud, which play a crucial role in fostering innovation and market growth. Additionally, the stringent regulatory environment in the area, which includes legislation like the General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA), drives organizations to heavily invest in cloud security solutions to ensure compliance.
Example Players in Cloud Security Market
- Amazon
- Amazon Web Services
- Armor Defense
- Broadcom
- CA Technologies
- Check Point Software Technologies
- Cisco Systems
- Extreme Networks
- F5
- Fortinet
- Forcepoint
- IBM
- Imperva
- Intel
- Kaspersky Labs
- McAfee
- Microsoft
- Okta
- Palo Alto Networks
- Pandasecurity
- Proofpoint
- Sophos
- Splunk
- Symantec
- Trellix
- Trend Micro
- Zscaler
CLOUD SECURITY MARKET: RESEARCH COVERAGE
The report on the cloud security market features insights on various sections, including:
- Market Sizing and Opportunity Analysis: An in-depth analysis of the cloud security market, focusing on key market segments, including [A] type of security, [B] type of component, [C] type of deployment, [D] type of end user, [E] company size, [F] geographical regions.
- Competitive Landscape: A comprehensive analysis of the companies engaged in the Cloud security market, based on several relevant parameters, such as [A] year of establishment, [B] company size, [C] location of headquarters, [D] ownership structure.
- Company Profiles: Elaborate profiles of prominent players engaged in the Cloud security market, providing details on [A] location of headquarters, [B]company size, [C] company mission, [D] company footprint, [E] management team, [F] contact details, [G] financial information, [H] operating business segments, [I] cloud security portfolio, [J] moat analysis, [K] recent developments, and an informed future outlook.
- Megatrends: An evaluation of ongoing megatrends in cloud security industry.
- Patent Analysis: An insightful analysis of patents filed / granted in the cloud security domain, based on relevant parameters, including [A] type of patent, [B] patent publication year, [C] patent age and [D] leading players.
- Recent Developments: An overview of the recent developments made in the cloud security market, along with analysis based on relevant parameters, including [A] year of initiative, [B] type of initiative, [C] geographical distribution and [D] most active players.
- Porter's Five Forces Analysis: An analysis of five competitive forces prevailing in the cloud security market, including threats of new entrants, bargaining power of buyers, bargaining power of suppliers, threats of substitute products and rivalry among existing competitors.
- SWOT Analysis: An insightful SWOT framework, highlighting the strengths, weaknesses, opportunities and threats in the domain. Additionally, it provides Harvey ball analysis, highlighting the relative impact of each SWOT parameter.
KEY QUESTIONS ANSWERED IN THIS REPORT
- How many companies are currently engaged in cloud security market?
- Which are the leading companies in this market?
- What factors are likely to influence the evolution of this market?
- What is the current and future market size?
- What is the CAGR of this market?
- How is the current and future market opportunity likely to be distributed across key market segments?
- Which type of cloud security is expected to dominate the market?
REASONS TO BUY THIS REPORT
- The report provides a comprehensive market analysis, offering detailed revenue projections of the overall market and its specific sub-segments. This information is valuable to both established market leaders and emerging entrants.
- Stakeholders can leverage the report to gain a deeper understanding of the competitive dynamics within the market. By analyzing the competitive landscape, businesses can make informed decisions to optimize their market positioning and develop effective go-to-market strategies.
- The report offers stakeholders a comprehensive overview of the market, including key drivers, barriers, opportunities, and challenges. This information empowers stakeholders to stay abreast of market trends and make data-driven decisions to capitalize on growth prospects.
ADDITIONAL BENEFITS
- Complimentary Excel Data Packs for all Analytical Modules in the Report
- 10% Free Content Customization
- Detailed Report Walkthrough Session with Research Team
- Free Updated report if the report is 6-12 months old or older
TABLE OF CONTENTS
SECTION I: REPORT OVERVIEW
1. PREFACE
- 1.1. Introduction
- 1.2. Market Share Insights
- 1.3. Key Market Insights
- 1.4. Report Coverage
- 1.5. Key Questions Answered
- 1.6. Chapter Outlines
2. RESEARCH METHODOLOGY
- 2.1. Chapter Overview
- 2.2. Research Assumptions
- 2.3. Database Building
- 2.3.1. Data Collection
- 2.3.2. Data Validation
- 2.3.3. Data Analysis
- 2.4. Project Methodology
- 2.4.1. Secondary Research
- 2.4.1.1. Annual Reports
- 2.4.1.2. Academic Research Papers
- 2.4.1.3. Company Websites
- 2.4.1.4. Investor Presentations
- 2.4.1.5. Regulatory Filings
- 2.4.1.6. White Papers
- 2.4.1.7. Industry Publications
- 2.4.1.8. Conferences and Seminars
- 2.4.1.9. Government Portals
- 2.4.1.10. Media and Press Releases
- 2.4.1.11. Newsletters
- 2.4.1.12. Industry Databases
- 2.4.1.13. Roots Proprietary Databases
- 2.4.1.14. Paid Databases and Sources
- 2.4.1.15. Social Media Portals
- 2.4.1.16. Other Secondary Sources
- 2.4.2. Primary Research
- 2.4.2.1. Introduction
- 2.4.2.2. Types
- 2.4.2.2.1. Qualitative
- 2.4.2.2.2. Quantitative
- 2.4.2.3. Advantages
- 2.4.2.4. Techniques
- 2.4.2.4.1. Interviews
- 2.4.2.4.2. Surveys
- 2.4.2.4.3. Focus Groups
- 2.4.2.4.4. Observational Research
- 2.4.2.4.5. Social Media Interactions
- 2.4.2.5. Stakeholders
- 2.4.2.5.1. Company Executives (CXOs)
- 2.4.2.5.2. Board of Directors
- 2.4.2.5.3. Company Presidents and Vice Presidents
- 2.4.2.5.4. Key Opinion Leaders
- 2.4.2.5.5. Research and Development Heads
- 2.4.2.5.6. Technical Experts
- 2.4.2.5.7. Subject Matter Experts
- 2.4.2.5.8. Scientists
- 2.4.2.5.9. Doctors and Other Healthcare Providers
- 2.4.2.6. Ethics and Integrity
- 2.4.2.6.1. Research Ethics
- 2.4.2.6.2. Data Integrity
- 2.4.3. Analytical Tools and Databases
- 2.4.1. Secondary Research
3. MARKET DYNAMICS
- 3.1. Forecast Methodology
- 3.1.1. Top-Down Approach
- 3.1.2. Bottom-Up Approach
- 3.1.3. Hybrid Approach
- 3.2. Market Assessment Framework
- 3.2.1. Total Addressable Market (TAM)
- 3.2.2. Serviceable Addressable Market (SAM)
- 3.2.3. Serviceable Obtainable Market (SOM)
- 3.2.4. Currently Acquired Market (CAM)
- 3.3. Forecasting Tools and Techniques
- 3.3.1. Qualitative Forecasting
- 3.3.2. Correlation
- 3.3.3. Regression
- 3.3.4. Time Series Analysis
- 3.3.5. Extrapolation
- 3.3.6. Convergence
- 3.3.7. Forecast Error Analysis
- 3.3.8. Data Visualization
- 3.3.9. Scenario Planning
- 3.3.10. Sensitivity Analysis
- 3.4. Key Considerations
- 3.4.1. Demographics
- 3.4.2. Market Access
- 3.4.3. Reimbursement Scenarios
- 3.4.4. Industry Consolidation
- 3.5. Robust Quality Control
- 3.6. Key Market Segmentations
- 3.7. Limitations
4. MACRO-ECONOMIC INDICATORS
- 4.1. Chapter Overview
- 4.2. Market Dynamics
- 4.2.1. Time Period
- 4.2.1.1. Historical Trends
- 4.2.1.2. Current and Forecasted Estimates
- 4.2.2. Currency Coverage
- 4.2.2.1. Overview of Major Currencies Affecting the Market
- 4.2.2.2. Impact of Currency Fluctuations on the Industry
- 4.2.3. Foreign Exchange Impact
- 4.2.3.1. Evaluation of Foreign Exchange Rates and Their Impact on Market
- 4.2.3.2. Strategies for Mitigating Foreign Exchange Risk
- 4.2.4. Recession
- 4.2.4.1. Historical Analysis of Past Recessions and Lessons Learnt
- 4.2.4.2. Assessment of Current Economic Conditions and Potential Impact on the Market
- 4.2.5. Inflation
- 4.2.5.1. Measurement and Analysis of Inflationary Pressures in the Economy
- 4.2.5.2. Potential Impact of Inflation on the Market Evolution
- 4.2.6. Interest Rates
- 4.2.6.1. Overview of Interest Rates and Their Impact on the Market
- 4.2.6.2. Strategies for Managing Interest Rate Risk
- 4.2.7. Commodity Flow Analysis
- 4.2.7.1. Type of Commodity
- 4.2.7.2. Origins and Destinations
- 4.2.7.3. Values and Weights
- 4.2.7.4. Modes of Transportation
- 4.2.8. Global Trade Dynamics
- 4.2.8.1. Import Scenario
- 4.2.8.2. Export Scenario
- 4.2.9. War Impact Analysis
- 4.2.9.1. Russian-Ukraine War
- 4.2.9.2. Israel-Hamas War
- 4.2.10. COVID Impact / Related Factors
- 4.2.10.1. Global Economic Impact
- 4.2.10.2. Industry-specific Impact
- 4.2.10.3. Government Response and Stimulus Measures
- 4.2.10.4. Future Outlook and Adaptation Strategies
- 4.2.11. Other Indicators
- 4.2.11.1. Fiscal Policy
- 4.2.11.2. Consumer Spending
- 4.2.11.3. Gross Domestic Product (GDP)
- 4.2.11.4. Employment
- 4.2.11.5. Taxes
- 4.2.11.6. R&D Innovation
- 4.2.11.7. Stock Market Performance
- 4.2.11.8. Supply Chain
- 4.2.11.9. Cross-Border Dynamics
- 4.2.1. Time Period
SECTION II: QUALITATIVE INSIGHTS
5. EXECUTIVE SUMMARY
6. INTRODUCTION
- 6.1. Chapter Overview
- 6.2. Overview of Cloud Security Market
- 6.2.1. Type of Security
- 6.2.2. Type of Component
- 6.2.3. Type of Deployment
- 6.2.4. Type of End-User
- 6.3. Future Perspective
7. REGULATORY SCENARIO
SECTION III: MARKET OVERVIEW
8. COMPREHENSIVE DATABASE OF LEADING PLAYERS
9. COMPETITIVE LANDSCAPE
- 9.1. Chapter Overview
- 9.2. Cloud Security: Overall Market Landscape
- 9.2.1. Analysis by Year of Establishment
- 9.2.2. Analysis by Company Size
- 9.2.3. Analysis by Location of Headquarters
- 9.2.4. Analysis by Ownership Structure
10. WHITE SPACE ANALYSIS
11. COMPETITIVE COMPETITIVENESS ANALYSIS
12. STARTUP ECOSYSTEM IN THE CLOUD SECURITY MARKET
- 12.1. Cloud Security Market: Market Landscape of Startups
- 12.1.1. Analysis by Year of Establishment
- 12.1.2. Analysis by Company Size
- 12.1.3. Analysis by Company Size and Year of Establishment
- 12.1.4. Analysis by Location of Headquarters
- 12.1.5. Analysis by Company Size and Location of Headquarters
- 12.1.6. Analysis by Ownership Structure
- 12.2. Key Findings
SECTION IV: COMPANY PROFILES
13. COMPANY PROFILES
- 13.1. Chapter Overview
- 13.2. Amazon*
- 13.2.1. Company Overview
- 13.2.2. Company Mission
- 13.2.3. Company Footprint
- 13.2.4. Management Team
- 13.2.5. Contact Details
- 13.2.6. Financial Performance
- 13.2.7. Operating Business Segments
- 13.2.8. Service / Product Portfolio (project specific)
- 13.2.9. MOAT Analysis
- 13.2.10. Recent Developments and Future Outlook
- 13.3. Amazon Web Services
- 13.4. Armor Defense
- 13.5. Broadcom
- 13.6. CA Technologies
- 13.7. Check Point Software Technologies
- 13.8. Cisco Systems
- 13.9. Extreme Networks
- 13.10. F5
- 13.11. Fortinet
- 13.12. Forcepoint
- 13.13. IBM
- 13.14. Imperva
- 13.15. Intel
- 13.16. Kaspersky Labs
- 13.17. McAfee
- 13.18. Microsoft
- 13.19. Okta
SECTION V: MARKET TRENDS
14. MEGA TRENDS ANALYSIS
15. UNMET NEED ANALYSIS
16. PATENT ANALYSIS
17. RECENT DEVELOPMENTS
- 17.1. Chapter Overview
- 17.2. Recent Funding
- 17.3. Recent Partnerships
- 17.4. Other Recent Initiatives
SECTION VI: MARKET OPPORTUNITY ANALYSIS
18. GLOBAL CLOUD SECURITY MARKET
- 18.1. Chapter Overview
- 18.2. Key Assumptions and Methodology
- 18.3. Trends Disruption Impacting Market
- 18.4. Demand Side Trends
- 18.5. Supply Side Trends
- 18.6. Global Cloud Security Market, Historical Trends (Since 2019) and Forecasted Estimates (Till 2035)
- 18.7. Multivariate Scenario Analysis
- 18.7.1. Conservative Scenario
- 18.7.2. Optimistic Scenario
- 18.8. Investment Feasibility Index
- 18.9. Key Market Segmentations
19. MARKET OPPORTUNITIES BASED ON TYPE OF SECURITY
- 19.1. Chapter Overview
- 19.2. Key Assumptions and Methodology
- 19.3. Revenue Shift Analysis
- 19.4. Market Movement Analysis
- 19.5. Penetration-Growth (P-G) Matrix
- 19.6. Cloud Security Market for Business Continuity and Disaster Recovery: Historical Trends (Since 2019) and Forecasted Estimates (Till 2035)
- 19.7. Cloud Security Market for Cloud Database Security: Historical Trends (Since 2019) and Forecasted Estimates (Till 2035)
- 19.8. Cloud Security Market for Cloud Encryption: Historical Trends (Since 2019) and Forecasted Estimates (Till 2035)
- 19.9. Cloud Security Market for Data Loss Prevention (DLP): Historical Trends (Since 2019) and Forecasted Estimates (Till 2035)
- 19.10. Cloud Security Market for Email and Web Security: Historical Trends (Since 2019) and Forecasted Estimates (Till 2035)
- 19.11. Cloud Security Market for Identity and Access Management (IAM): Historical Trends (Since 2019) and Forecasted Estimates (Till 2035)
- 19.12. Cloud Security Market for Network Security: Historical Trends (Since 2019) and Forecasted Estimates (Till 2035)
- 19.13. Cloud Security Market for Security Information and Event Management (SIEM): Historical Trends (Since 2019) and Forecasted Estimates (Till 2035)
- 19.14. Cloud Security Market for Virtualization: Historical Trends (Since 2019) and Forecasted Estimates (Till 2035)
- 19.15. Data Triangulation and Validation
- 19.15.1. Secondary Sources
- 19.15.2. Primary Sources
- 19.15.3. Statistical Modeling
20. MARKET OPPORTUNITIES BASED ON TYPE OF COMPONENT
- 20.1. Chapter Overview
- 20.2. Key Assumptions and Methodology
- 20.3. Revenue Shift Analysis
- 20.4. Market Movement Analysis
- 20.5. Penetration-Growth (P-G) Matrix
- 20.6. Cloud Security Market for Services: Historical Trends (Since 2019) and Forecasted Estimates (Till 2035)
- 20.7. Cloud Security Market for Solutions: Historical Trends (Since 2019) and Forecasted Estimates (Till 2035)
- 20.8. Data Triangulation and Validation
- 20.8.1. Secondary Sources
- 20.8.2. Primary Sources
- 20.8.3. Statistical Modeling
21. MARKET OPPORTUNITIES BASED ON TYPE OF DEPLOYMENT
- 21.1. Chapter Overview
- 21.2. Key Assumptions and Methodology
- 21.3. Revenue Shift Analysis
- 21.4. Market Movement Analysis
- 21.5. Penetration-Growth (P-G) Matrix
- 21.6. Cloud Security Market for Hybrid: Historical Trends (Since 2019) and Forecasted Estimates (Till 2035)
- 21.7. Cloud Security Market for Private: Historical Trends (Since 2019) and Forecasted Estimates (Till 2035)
- 21.8. Cloud Security Market for Public: Historical Trends (Since 2019) and Forecasted Estimates (Till 2035)
- 21.9. Data Triangulation and Validation
- 21.9.1. Secondary Sources
- 21.9.2. Primary Sources
- 21.9.3. Statistical Modeling
22. MARKET OPPORTUNITIES BASED ON TYPE OF END USER
- 22.1. Chapter Overview
- 22.2. Key Assumptions and Methodology
- 22.3. Revenue Shift Analysis
- 22.4. Market Movement Analysis
- 22.5. Penetration-Growth (P-G) Matrix
- 22.6. Cloud Security Market for Banking: Historical Trends (Since 2019) and Forecasted Estimates (Till 2035)
- 22.7. Cloud Security Market for Energy and Utilities: Historical Trends (Since 2019) and Forecasted Estimates (Till 2035)
- 22.8. Cloud Security Market for Finance: Historical Trends (Since 2019) and Forecasted Estimates (Till 2035)
- 22.9. Cloud Security Market for Government: Historical Trends (Since 2019) and Forecasted Estimates (Till 2035)
- 22.10. Cloud Security Market for IT and Telecommunication: Historical Trends (Since 2019) and Forecasted Estimates (Till 2035)
- 22.11. Cloud Security Market for Healthcare and Life Sciences: Historical Trends (Since 2019) and Forecasted Estimates (Till 2035)
- 22.12. Cloud Security Market for Manufacturing: Historical Trends (Since 2019) and Forecasted Estimates (Till 2035)
- 22.13. Cloud Security Market for Retail: Historical Trends (Since 2019) and Forecasted Estimates (Till 2035)
- 22.14. Cloud Security Market for Security and Insurance (BFSI): Historical Trends (Since 2019) and Forecasted Estimates (Till 2035)
- 22.15. Cloud Security Market for Others: Historical Trends (Since 2019) and Forecasted Estimates (Till 2035)
- 22.16. Data Triangulation and Validation
- 22.16.1. Secondary Sources
- 22.16.2. Primary Sources
- 22.16.3. Statistical Modeling
23. MARKET OPPORTUNITIES FOR CLOUD SECURITY IN NORTH AMERICA
- 23.1. Chapter Overview
- 23.2. Key Assumptions and Methodology
- 23.3. Revenue Shift Analysis
- 23.4. Market Movement Analysis
- 23.5. Penetration-Growth (P-G) Matrix
- 23.6. Cloud Security Market in North America: Historical Trends (Since 2019) and Forecasted Estimates (Till 2035)
- 23.6.1. Cloud Security Market in the US: Historical Trends (Since 2019) and Forecasted Estimates (Till 2035)
- 23.6.2. Cloud Security Market in Canada: Historical Trends (Since 2019) and Forecasted Estimates (Till 2035)
- 23.6.3. Cloud Security Market in Mexico: Historical Trends (Since 2019) and Forecasted Estimates (Till 2035)
- 23.6.4. Cloud Security Market in Other North American Countries: Historical Trends (Since 2019) and Forecasted Estimates (Till 2035)
- 23.7. Data Triangulation and Validation
24. MARKET OPPORTUNITIES FOR CLOUD SECURITY IN EUROPE
- 24.1. Chapter Overview
- 24.2. Key Assumptions and Methodology
- 24.3. Revenue Shift Analysis
- 24.4. Market Movement Analysis
- 24.5. Penetration-Growth (P-G) Matrix
- 24.6. Cloud Security Market in Europe: Historical Trends (Since 2019) and Forecasted Estimates (Till 2035)
- 24.6.1. Cloud Security Market in Austria: Historical Trends (Since 2019) and Forecasted Estimates (Till 2035)
- 24.6.2. Cloud Security Market in Belgium: Historical Trends (Since 2019) and Forecasted Estimates (Till 2035)
- 24.6.3. Cloud Security Market in Denmark: Historical Trends (Since 2019) and Forecasted Estimates (Till 2035)
- 24.6.4. Cloud Security Market in France: Historical Trends (Since 2019) and Forecasted Estimates (Till 2035)
- 24.6.5. Cloud Security Market in Germany: Historical Trends (Since 2019) and Forecasted Estimates (Till 2035)
- 24.6.6. Cloud Security Market in Ireland: Historical Trends (Since 2019) and Forecasted Estimates (Till 2035)
- 24.6.7. Cloud Security Market in Italy: Historical Trends (Since 2019) and Forecasted Estimates (Till 2035)
- 24.6.8. Cloud Security Market in Netherlands: Historical Trends (Since 2019) and Forecasted Estimates (Till 2035)
- 24.6.9. Cloud Security Market in Norway: Historical Trends (Since 2019) and Forecasted Estimates (Till 2035)
- 24.6.10. Cloud Security Market in Russia: Historical Trends (Since 2019) and Forecasted Estimates (Till 2035)
- 24.6.11. Cloud Security Market in Spain: Historical Trends (Since 2019) and Forecasted Estimates (Till 2035)
- 24.6.12. Cloud Security Market in Sweden: Historical Trends (Since 2019) and Forecasted Estimates (Till 2035)
- 24.6.13. Cloud Security Market in Sweden: Historical Trends (Since 2019) and Forecasted Estimates (Till 2035)
- 24.6.14. Cloud Security Market in Switzerland: Historical Trends (Since 2019) and Forecasted Estimates (Till 2035)
- 24.6.15. Cloud Security Market in the UK: Historical Trends (Since 2019) and Forecasted Estimates (Till 2035)
- 24.6.16. Cloud Security Market in Other European Countries: Historical Trends (Since 2019) and Forecasted Estimates (Till 2035)
- 24.7. Data Triangulation and Validation
25. MARKET OPPORTUNITIES FOR CLOUD SECURITY IN ASIA
- 25.1. Chapter Overview
- 25.2. Key Assumptions and Methodology
- 25.3. Revenue Shift Analysis
- 25.4. Market Movement Analysis
- 25.5. Penetration-Growth (P-G) Matrix
- 25.6. Cloud Security Market in Asia: Historical Trends (Since 2019) and Forecasted Estimates (Till 2035)
- 25.6.1. Cloud Security Market in China: Historical Trends (Since 2019) and Forecasted Estimates (Till 2035)
- 25.6.2. Cloud Security Market in India: Historical Trends (Since 2019) and Forecasted Estimates (Till 2035)
- 25.6.3. Cloud Security Market in Japan: Historical Trends (Since 2019) and Forecasted Estimates (Till 2035)
- 25.6.4. Cloud Security Market in Singapore: Historical Trends (Since 2019) and Forecasted Estimates (Till 2035)
- 25.6.5. Cloud Security Market in South Korea: Historical Trends (Since 2019) and Forecasted Estimates (Till 2035)
- 25.6.6. Cloud Security Market in Other Asian Countries: Historical Trends (Since 2019) and Forecasted Estimates (Till 2035)
- 25.7. Data Triangulation and Validation
26. MARKET OPPORTUNITIES FOR CLOUD SECURITY IN MIDDLE EAST AND NORTH AFRICA (MENA)
- 26.1. Chapter Overview
- 26.2. Key Assumptions and Methodology
- 26.3. Revenue Shift Analysis
- 26.4. Market Movement Analysis
- 26.5. Penetration-Growth (P-G) Matrix
- 26.6. Cloud Security Market in Middle East and North Africa (MENA): Historical Trends (Since 2019) and Forecasted Estimates (Till 2035)
- 26.6.1. Cloud Security Market in Egypt: Historical Trends (Since 2019) and Forecasted Estimates (Till 205)
- 26.6.2. Cloud Security Market in Iran: Historical Trends (Since 2019) and Forecasted Estimates (Till 2035)
- 26.6.3. Cloud Security Market in Iraq: Historical Trends (Since 2019) and Forecasted Estimates (Till 2035)
- 26.6.4. Cloud Security Market in Israel: Historical Trends (Since 2019) and Forecasted Estimates (Till 2035)
- 26.6.5. Cloud Security Market in Kuwait: Historical Trends (Since 2019) and Forecasted Estimates (Till 2035)
- 26.6.6. Cloud Security Market in Saudi Arabia: Historical Trends (Since 2019) and Forecasted Estimates (Till 2035)
- 26.6.7. Cloud Security Market in United Arab Emirates (UAE): Historical Trends (Since 2019) and Forecasted Estimates (Till 2035)
- 26.6.8. Cloud Security Market in Other MENA Countries: Historical Trends (Since 2019) and Forecasted Estimates (Till 2035)
- 26.7. Data Triangulation and Validation
27. MARKET OPPORTUNITIES FOR CLOUD SECURITY IN LATIN AMERICA
- 27.1. Chapter Overview
- 27.2. Key Assumptions and Methodology
- 27.3. Revenue Shift Analysis
- 27.4. Market Movement Analysis
- 27.5. Penetration-Growth (P-G) Matrix
- 27.6. Cloud Security Market in Latin America: Historical Trends (Since 2019) and Forecasted Estimates (Till 2035)
- 27.6.1. Cloud Security Market in Argentina: Historical Trends (Since 2019) and Forecasted Estimates (Till 2035)
- 27.6.2. Cloud Security Market in Brazil: Historical Trends (Since 2019) and Forecasted Estimates (Till 2035)
- 27.6.3. Cloud Security Market in Chile: Historical Trends (Since 2019) and Forecasted Estimates (Till 2035)
- 27.6.4. Cloud Security Market in Colombia Historical Trends (Since 2019) and Forecasted Estimates (Till 2035)
- 27.6.5. Cloud Security Market in Venezuela: Historical Trends (Since 2019) and Forecasted Estimates (Till 2035)
- 27.6.6. Cloud Security Market in Other Latin American Countries: Historical Trends (Since 2019) and Forecasted Estimates (Till 2035)
- 27.7. Data Triangulation and Validation
28. MARKET OPPORTUNITIES FOR CLOUD SECURITY IN REST OF THE WORLD
- 28.1. Chapter Overview
- 28.2. Key Assumptions and Methodology
- 28.3. Revenue Shift Analysis
- 28.4. Market Movement Analysis
- 28.5. Penetration-Growth (P-G) Matrix
- 28.6. Cloud Security Market in Rest of the World: Historical Trends (Since 2019) and Forecasted Estimates (Till 2035)
- 28.6.1. Cloud Security Market in Australia: Historical Trends (Since 2019) and Forecasted Estimates (Till 2035)
- 28.6.2. Cloud Security Market in New Zealand: Historical Trends (Since 2019) and Forecasted Estimates (Till 2035)
- 28.6.3. Cloud Security Market in Other Countries
- 28.7. Data Triangulation and Validation
29. MARKET CONCENTRATION ANALYSIS: DISTRIBUTION BY LEADING PLAYERS
- 29.1. Leading Player 1
- 29.2. Leading Player 2
- 29.3. Leading Player 3
- 29.4. Leading Player 4
- 29.5. Leading Player 5
- 29.6. Leading Player 6
- 29.7. Leading Player 7
- 29.8. Leading Player 8
30. ADJACENT MARKET ANALYSIS
SECTION VII: STRATEGIC TOOLS
31. KEY WINNING STRATEGIES
32. PORTER FIVE FORCES ANALYSIS
33. SWOT ANALYSIS
34. VALUE CHAIN ANALYSIS
35. ROOTS STRATEGIC RECOMMENDATIONS
- 35.1. Chapter Overview
- 35.2. Key Business-related Strategies
- 35.2.1. Research & Development
- 35.2.2. Product Manufacturing
- 35.2.3. Commercialization / Go-to-Market
- 35.2.4. Sales and Marketing
- 35.3. Key Operations-related Strategies
- 35.3.1. Risk Management
- 35.3.2. Workforce
- 35.3.3. Finance
- 35.3.4. Others









