 |
市场调查报告书
商品编码
1881283
全球DDoS防护与缓解安全市场:依产品、解决方案类型、应用领域、部署模式、组织规模、产业与地区划分-预测至2030年DDoS Protection & Mitigation Security Market by Solution Type, Offering, Application Area - Global Forecast to 2030 |
||||||
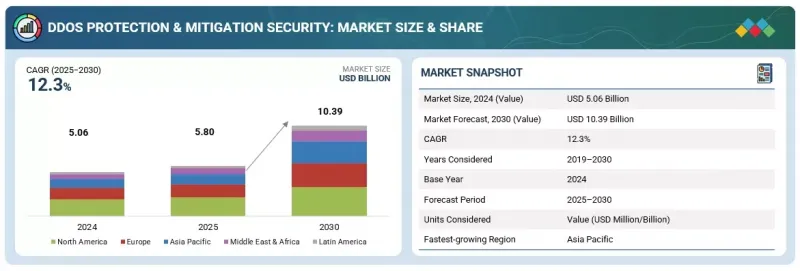
DDoS防护和缓解安全市场规模预计将从2025年的58亿美元成长到2030年的103.9亿美元,预测期内复合年增长率为12.3%。
| 调查范围 | |
|---|---|
| 调查期 | 2019-2030 |
| 基准年 | 2024 |
| 预测期 | 2025-2030 |
| 目标单元 | 价值(百万美元/十亿美元) |
| 部分 | 透过提供的解决方案类型、应用领域、部署模式、组织规模、产业和地区进行分类。 |
| 目标区域 | 北美洲、欧洲、亚太地区、中东和非洲、拉丁美洲 |
金融服务、医疗保健和IT/ITES等市场对科技的快速应用正在创造成长机会。将人工智慧 (AI) 和机器学习功能融入DDoS攻击缓解解决方案可望提升威胁侦测能力。资安管理服务需求旺盛,尤其是在中小企业中,这为服务提供者开闢了新的成长领域。其他技术创新领域包括协同防御系统和云端安全系统,这些都推动了对客製化、高弹性DDoS防护的需求,以保障各行业的业务活动。
在预测期内,网路流量分析器细分市场预计将在全球DDoS防护和缓解安全市场中保持最大的市场份额。网路分析器利用串流监控、异常侦测和行为分析等先进技术,在识别流量异常模式方面发挥关键作用。透过建立正常网路活动的基准值,它们可以检测出可能预示潜在DDoS攻击的偏差,帮助IT团队在威胁升级并影响关键业务运作之前立即做出回应。此外,现代网路分析器能够更清晰地展现网路行为,从而实现对合法流量的精确过滤和有效的速率限制,以阻止恶意请求。这些工具对于维护服务可用性、优化网路效能以及降低与流量型和应用层DDoS攻击相关的风险至关重要。随着企业不断优先考虑即时监控和数据驱动的威胁侦测,高效能网路流量分析器的普及预计将保持强劲势头,从而巩固其市场主导地位。
受源自大规模殭尸网路的DDoS攻击日益增多的推动,殭尸网路侦测与缓解领域预计将在预测期内实现最快成长。这些解决方案利用进阶分析、人工智慧和机器学习技术来识别和缓解恶意殭尸网路活动,这些活动会操纵网路流量并使系统瘫痪。透过持续监控包括TCP和UDP在内的多种通讯协定的网路资料封包,殭尸网路侦测系统可以侦测与受感染设备和协同攻击模式相关的异常情况。这种能力使组织能够在殭尸网路被用于DDoS攻击之前识别它们,从而实现早期疗育和缓解。此外,自动化分析工具可以即时区分合法流量和恶意流量,从而提高侦测准确率并减少误报。一旦识别出殭尸网路威胁,缓解系统可以立即采取行动,隔离并消除恶意流量。殭尸网路攻击的日益复杂化以及物联网设备的广泛应用,使得殭尸网路侦测与缓解成为现代网路安全基础设施的重要组成部分,从而推动了该细分市场的快速成长。
亚太地区DDoS防护和缓解安全市场预计将在预测期内保持最高成长率,这主要得益于全部区域快速的数位转型、日益普及的云端运算以及连网设备的激增。中国、印度、日本和澳洲等国家正在推动这一成长,因为物联网技术的广泛应用和行动主导的商业生态系统增加了遭受DDoS攻击的风险。此外,该地区的企业,尤其是中小企业,越来越意识到主动网路防御的重要性,促使他们投资于可扩展且经济高效的DDoS防护解决方案。将人工智慧(AI)和机器学习整合到DDoS防护系统中,可实现即时威胁侦测和自动缓解,从而提高整体效率。云端基础设施的显着扩张、数据流量的成长以及政府主导的数位化措施也促进了市场成长。儘管面临日益复杂的网路威胁以及各国网路安全成熟度不一等挑战,但由于对保护关键数位资产和确保业务永续营运的日益重视,亚太地区预计仍将实现显着成长。
本报告对全球 DDoS 防护和缓解安全市场进行了分析,并按产品、解决方案类型、应用领域、部署模式、组织规模、垂直行业和地区进行了细分,同时也介绍了参与该市场的公司的概况。
目录
第一章 引言
第二章执行摘要
第三章重要考察
第四章 市场概览
- 介绍
- 市场动态
- 未满足的需求和差距
- 相互关联的市场与跨产业机会
- 一级/二级/三级公司的策略性倡议
第五章 产业趋势
- 波特五力分析
- 总体经济指标
- 供应链分析
- 生态系分析
- 定价分析
- 重大会议和活动
- 影响客户业务的趋势/干扰因素
- 投资和资金筹措方案
- 案例研究分析
- DDoS攻击防御技术
- 美国关税对2025年DDoS防护与缓解安全市场的影响
第六章:技术进步、人工智慧影响、专利、创新与未来应用
- 关键新兴技术
- 互补技术
- 邻近技术
- DDoS防护与缓解安全市场的未来展望
- 专利分析
- 人工智慧/生成式人工智慧对DDoS防护和缓解安全市场的影响
第七章 监理环境
- 监管状态
- 监管机构、政府机构和其他组织
第八章:顾客状况与购买行为
- 决策流程
- 买方相关人员和采购评估标准
- 采购过程中的关键相关人员
- 采购标准
- 招募障碍和内部挑战
9. DDoS防护与缓解安全市场(依产品/服务分类)
- 介绍
- 硬体解决方案
- 软体解决方案
- 服务
10. DDoS防护与缓解安全市场(依解决方案类型划分)
- 介绍
- 网路流量分析器
- 威胁缓解系统
- 殭尸网路侦测与管理
- 其他的
11. DDoS防护与缓解安全市场(依应用领域划分)
- 介绍
- 网路安全
- 应用程式安全
- 云端安全
- 端点安全
12. 依部署模式分類的DDoS防护与缓解安全市场
- 介绍
- 本地部署
- 云
13. DDoS防护与缓解安全市场(依组织规模划分)
- 介绍
- 大公司
- 小型企业
14. DDoS防护与缓解安全市场(依产业划分)
- 介绍
- 政府和国防部
- 银行、金融服务和保险
- 製造业
- 能源与公共产业
- 资讯科技与资讯科技服务
- 通讯
- 卫生保健
- 教育
- 零售
- 其他的
15. 按地区分類的DDoS防护和缓解安全市场
- 介绍
- 北美洲
- 北美:宏观经济展望
- 美国
- 加拿大
- 欧洲
- 欧洲:宏观经济展望
- 英国
- 德国
- 其他的
- 亚太地区
- 亚太地区:宏观经济展望
- 中国
- 日本
- 印度
- 其他的
- 中东和非洲
- 中东与非洲:宏观经济展望
- 沙乌地阿拉伯
- 阿拉伯聯合大公国
- 南非
- 其他的
- 拉丁美洲
- 拉丁美洲:宏观经济展望
- 巴西
- 墨西哥
- 其他的
第十六章 竞争格局
- 介绍
- 主要参与企业的策略/优势,2022-2025年
- 2020-2024年收入分析
- 2024年市占率分析
- 公司估值矩阵:主要参与企业,2024 年
- 公司估值矩阵:Start-Ups/中小企业,2024 年
- 竞争场景
- 品牌/产品对比
- 估值与财务指标,2025 年
第十七章:公司简介
- 主要参与企业
- NETSCOUT
- AKAMAI TECHNOLOGIES
- RADWARE
- CLOUDFLARE
- FORTINET
- HUAWEI
- LINK11
- IMPERVA(A THALES COMPANY)
- BT
- A10 NETWORKS
- 其他公司
- FASTLY
- F5
- CORERO
- ALLOT
- STRATACORE
- SUCURI
- NSFOCUS
- LUMEN TECHNOLOGIES
- 小型企业/Start-Ups
- STACKPATH
- SECEON
- HALTDOS
- DDOS-GUARD
- INDUSFACE
- ACTIVEREACH
- MLYTICS
- NEXUSGUARD
- RIOREY
- PHOENIXNAP
- COMODO SECURITY SOLUTIONS
第十八章调查方法
第十九章:邻近及相关市场
第20章附录
The DDoS protection & mitigation security market is estimated to grow from USD 5.80 billion in 2025 to USD 10.39 billion by 2030 at a compound annual growth rate (CAGR) of 12.3% during the forecast period.
| Scope of the Report | |
|---|---|
| Years Considered for the Study | 2019-2030 |
| Base Year | 2024 |
| Forecast Period | 2025-2030 |
| Units Considered | Value (USD Million/Billion) |
| Segments | By Offering , Solution Type, Application Area, Deployment Mode, Organization Size, Vertical |
| Regions covered | North America, Europe, Asia Pacific, Middle East & Africa, Latin America |
The rapid adoption of technologies across markets such as BFSI, healthcare, and IT & ITeS creates growth opportunities. Incorporating artificial intelligence and machine learning capabilities into DDoS protection solutions promises to improve threat detection. Managed security services are in demand, especially by small and medium enterprises, which present new growth frontiers for providers. Other areas where technological innovations are rising include cooperative defense systems and cloud security systems, with an increasing demand for tailored and elastic DDoS protection to safeguard business activities across industries.

"By solution type, the network traffic analyzers segment is estimated to account for the largest market size during the forecast period."
The network traffic analyzers segment is anticipated to hold the largest market size in the DDoS protection and mitigation security market during the forecast period. Network analyzers play a crucial role in identifying abnormal patterns in traffic by using advanced techniques such as flow monitoring, anomaly detection, and behavioral analytics. By establishing a baseline for normal network activity, these tools can detect deviations that may indicate potential DDoS attacks, allowing IT teams to take immediate action before the threat escalates and impacts critical business operations. Moreover, modern network analyzers enhance visibility into network behavior, enabling precise filtering of legitimate traffic and effective rate limiting to block malicious requests. These tools are integral to maintaining service availability and optimizing network performance while mitigating risks associated with volumetric and application-layer DDoS attacks. As organizations continue to prioritize real-time monitoring and data-driven threat detection, the adoption of high-performance network traffic analyzers is expected to remain strong, reinforcing their dominance in the market.
"By solution type, the botnet detection & mitigation segment is estimated to register the fastest growth rate during the forecast period."
The botnet detection & mitigation segment is projected to record the fastest growth during the forecast period, driven by the rising number of DDoS attacks originating from large-scale botnet networks. These solutions leverage advanced analytics, artificial intelligence, and machine learning to identify and mitigate malicious bot activities that manipulate network traffic or overwhelm systems. By continuously monitoring network data packets across multiple protocols such as TCP and UDP, botnet detection systems can spot anomalies linked to infected devices or coordinated attack patterns. Such capabilities allow organizations to identify botnets before they are weaponized for DDoS assaults, ensuring early intervention and reduced damage. In addition, automated analysis tools categorize legitimate and illegitimate traffic in real time, improving detection accuracy and reducing false positives. Once a botnet threat is identified, mitigation systems immediately deploy countermeasures to isolate and neutralize the malicious traffic. The growing sophistication of bot-driven attacks and the expanding use of IoT devices make botnet detection and mitigation an essential part of modern cybersecurity infrastructure, driving rapid growth in this market segment.
"By region, Asia Pacific is projected to record the highest growth rate during the forecast period."
The Asia Pacific DDoS protection & mitigation security market is estimated to witness the highest growth rate during the forecast period, fueled by rapid digital transformation, increasing cloud adoption, and the surge in connected devices across the region. Countries such as China, India, Japan, and Australia are leading this growth, supported by the widespread deployment of Internet of Things (IoT) technologies and mobile-driven business ecosystems that heighten vulnerability to DDoS attacks. The region is also witnessing growing awareness among enterprises regarding the importance of proactive cyber defense, prompting investments in scalable, cost-effective DDoS protection solutions, particularly among small and medium-sized enterprises (SMEs). The integration of artificial intelligence and machine learning into DDoS protection systems has enabled real-time threat detection and automated mitigation, improving overall efficiency. The substantial expansion of cloud infrastructure, rising data traffic, and government-led digital initiatives further contribute to the market's growth. Despite challenges such as complex cyber threats and varying levels of cybersecurity maturity across countries, the Asia Pacific region is poised for significant expansion due to its increasing focus on protecting critical digital assets and ensuring business continuity.
In-depth interviews have been conducted with chief executive officers (CEOs), Directors, and other executives from various key organizations operating in the DDoS protection & mitigation security market.
- By Company Type: Tier 1 - 70%, Tier 2 - 20%, and Tier 3 - 10%
- By Designation: Directors - 73%, Managers - 18%, and Others - 9%
- By Region: North America - 30%, Europe - 25%, Asia Pacific - 35%, RoW - 10%
The major players in the DDoS protection & mitigation security market include NetScout (US), Akamai (US), Radware (Israel), Huawei (China), Fortinet (US), Imperva (US), F5 (US), Cloudflare (US), BT (UK), and A10 Networks (US). These players have adopted various growth strategies, such as partnerships, agreements and collaborations, new product launches, enhancements, and acquisitions, to expand their DDoS protection & mitigation security market footprint.
Research Coverage
The market study covers the DDoS protection & mitigation security market size across different segments. It aims to estimate the market size and the growth potential across various segments, including offering (with hardware solutions, software solutions, services), solution type, application area, deployment mode, organization size, vertical, and region. The study includes an in-depth competitive analysis of the leading market players, their company profiles, key observations related to product and business offerings, recent developments, and market strategies.
Key Benefits of Buying the Report
The report will help market leaders and new entrants with information on the closest approximations of the global DDoS protection and mitigation security market's revenue numbers and subsegments. This report will help stakeholders understand the competitive landscape and gain more insights to better position their businesses and plan suitable go-to-market strategies. Moreover, the report will provide insights for stakeholders to understand the market's pulse and provide them with information on key market drivers, restraints, challenges, and opportunities.
The report provides insights into the following pointers:
Analysis of key drivers (rise in multi-vector DDoS attacks, DDoS attacks during holidays, ease of availability of DDoS-for-hire services, high demand for cloud-based and hybrid DDoS protection and mitigation security solutions), restraints (budget constraints among SMEs, easy availability of free and pirated DDoS protection and mitigation security solutions), opportunities (increase in the number of DDoS threats across IoT ecosystem, need for DDoS defense solutions for 5G ecosystem, highly regulated verticals and gaming sector to create attractive opportunities for DDoS vendors, rising DDoS threats on cryptocurrency exchange entities), and challenges (sweep period of attacks, large-scale traffic defense with zero latency, and SSL encrypted attacks in DDoS area, dearth of security skills among security professionals and lack of pre-planning among enterprises, DDoS-for-hire services that are easy to find and created for minimum charges).
1. Product Development/Innovation: Detailed insights on upcoming technologies, research & development activities, and new product & service launches in the DDoS protection & mitigation security market.
2. Market Development: The report provides comprehensive information about lucrative markets and analyzes the DDoS protection & mitigation security market across various regions.
3. Market Diversification: Exhaustive information about new products & services, untapped geographies, recent developments, and investments in the DDoS protection & mitigation security market.
4. Competitive Assessment: In-depth assessment of market shares, growth strategies and service offerings of leading include NetScout (US), Akamai (US), Radware (Israel), Huawei (China), Fortinet (US), Imperva (US), F5 (US), Cloudflare (US), BT (UK), A10 Networks (US), Link11 (Germany), Fastly (US), Corero (UK), AIIoT (Israel), Stratacore (US), Sucuri (US), NSFOCUS (China), Lumen Technologies (US), StackPath (US), Seceon (US), Haltdos (India), DDoS-Guard (Russia), Indusface (India), activereach (US), Mlytics (Singapore), Nexusguard (Singapore), RioRey (US), and PheonixNAP (US), and Comodo Security Solutions (US).
TABLE OF CONTENTS
1 INTRODUCTION
- 1.1 STUDY OBJECTIVES
- 1.2 MARKET DEFINITION
- 1.3 STUDY SCOPE
- 1.3.1 MARKET SEGMENTATION AND REGIONS COVERED
- 1.3.2 INCLUSIONS & EXCLUSIONS
- 1.4 YEARS CONSIDERED
- 1.5 CURRENCY CONSIDERED
- 1.6 STAKEHOLDERS
- 1.7 SUMMARY OF CHANGES
2 EXECUTIVE SUMMARY
- 2.1 KEY INSIGHTS AND MARKET HIGHLIGHTS
- 2.2 KEY MARKET PARTICIPANTS: MAPPING OF STRATEGIC DEVELOPMENTS
- 2.3 DISRUPTIONS SHAPING MARKET
- 2.4 HIGH GROWTH SEGMENTS
- 2.5 SNAPSHOT: GLOBAL MARKET SIZE, GROWTH RATE, AND FORECAST
3 PREMIUM INSIGHTS
- 3.1 ATTRACTIVE OPPORTUNITIES FOR PLAYERS IN DDOS PROTECTION & MITIGATION SECURITY MARKET
- 3.2 DDOS PROTECTION & MITIGATION SECURITY MARKET, BY OFFERING AND ORGANIZATION SIZE
- 3.3 DDOS PROTECTION & MITIGATION SECURITY MARKET, BY APPLICATION AREA
- 3.4 DDOS PROTECTION & MITIGATION SECURITY MARKET, BY VERTICAL
4 MARKET OVERVIEW
- 4.1 INTRODUCTION
- 4.2 MARKET DYNAMICS
- 4.2.1 DRIVERS
- 4.2.1.1 Rising frequency and complexity of DDoS attacks
- 4.2.1.2 Growing internet penetration and connectivity
- 4.2.2 RESTRAINTS
- 4.2.2.1 Limited integration across multi-vendor environments
- 4.2.2.2 Regulatory and data sovereignty constraints
- 4.2.3 OPPORTUNITIES
- 4.2.3.1 AI-driven predictive mitigation and automated threat correlation
- 4.2.3.2 Growing partnerships between ISPs, cloud providers, and security vendors
- 4.2.4 CHALLENGES
- 4.2.4.1 Lack of skilled cybersecurity professionals
- 4.2.4.2 Cost and complexity of solutions
- 4.2.1 DRIVERS
- 4.3 UNMET NEEDS AND WHITE SPACES
- 4.4 INTERCONNECTED MARKETS AND CROSS-SECTOR OPPORTUNITIES
- 4.5 STRATEGIC MOVES BY TIER-1/2/3 PLAYERS
5 INDUSTRY TRENDS
- 5.1 PORTER'S FIVE FORCES ANALYSIS
- 5.1.1 THREAT OF NEW ENTRANTS
- 5.1.2 THREAT OF SUBSTITUTES
- 5.1.3 BARGAINING POWER OF SUPPLIERS
- 5.1.4 BARGAINING POWER OF BUYERS
- 5.1.5 INTENSITY OF COMPETITIVE RIVALRY
- 5.2 MACROECONOMICS INDICATORS
- 5.2.1 INTRODUCTION
- 5.2.2 GDP TRENDS AND FORECAST
- 5.2.3 TRENDS IN GLOBAL DDOS PROTECTION & MITIGATION SECURITY INDUSTRY
- 5.3 SUPPLY CHAIN ANALYSIS
- 5.4 ECOSYSTEM ANALYSIS
- 5.5 PRICING ANALYSIS
- 5.5.1 AVERAGE SELLING PRICE TREND OF KEY PLAYERS, BY OFFERING, 2024
- 5.5.2 INDICATIVE PRICING ANALYSIS OF DDOS PROTECTION AND MITIGATION SECURITY, BY OFFERING, 2024
- 5.6 KEY CONFERENCES AND EVENTS
- 5.7 TRENDS/DISRUPTIONS IMPACTING CUSTOMER BUSINESS
- 5.8 INVESTMENT AND FUNDING SCENARIO
- 5.9 CASE STUDY ANALYSIS
- 5.9.1 XTEL COMMUNICATIONS CHOSE NETSCOUT TO IMPROVE VISIBILITY INTO NETWORK TRAFFIC
- 5.9.2 PENTELEDATA SELECTED RADWARE'S AMS FOR TECHNICAL INTEGRATION WITH KENTIK TECHNOLOGIES
- 5.9.3 CNI CHOSE CORERO TO PROTECT ITS CUSTOMERS FROM DDOS ATTACKS
- 5.10 DDOS PREVENTION TECHNIQUES
- 5.11 IMPACT OF 2025 US TARIFF - DDOS PROTECTION AND MITIGATION SECURITY MARKET
- 5.11.1 INTRODUCTION
- 5.11.2 KEY TARIFF RATES
- 5.11.3 PRICE IMPACT ANALYSIS
- 5.11.4 IMPACT ON COUNTRY/REGION
- 5.11.4.1 North America
- 5.11.4.2 Europe
- 5.11.4.3 Asia Pacific
- 5.11.5 IMPACT ON END-USE INDUSTRIES
6 TECHNOLOGICAL ADVANCEMENTS, AI-DRIVEN IMPACT, PATENTS, INNOVATIONS, AND FUTURE APPLICATIONS
- 6.1 KEY EMERGING TECHNOLOGIES
- 6.1.1 TRAFFIC FILTERING
- 6.1.2 RATE LIMITING
- 6.1.3 WEB APPLICATION FIREWALL (WAF)
- 6.2 COMPLEMENTARY TECHNOLOGIES
- 6.2.1 ARTIFICIAL INTELLIGENCE (AI)
- 6.2.2 MACHINE LEARNING (ML)
- 6.3 ADJACENT TECHNOLOGIES
- 6.3.1 LOAD BALANCERS
- 6.3.2 CONTENT DELIVERY NETWORKS (CDNS)
- 6.4 FUTURE LANDSCAPE OF DDOS PROTECTION AND MITIGATION SECURITY MARKET
- 6.4.1 DDOS PROTECTION AND MITIGATION SECURITY TECHNOLOGY ROADMAP TILL 2030
- 6.4.1.1 Short-term roadmap (2025-2026)
- 6.4.1.2 Mid-term roadmap (2027-2028)
- 6.4.1.3 Long-term roadmap (2029-2030)
- 6.4.1 DDOS PROTECTION AND MITIGATION SECURITY TECHNOLOGY ROADMAP TILL 2030
- 6.5 PATENT ANALYSIS
- 6.5.1 METHODOLOGY
- 6.5.2 KEY PATENTS
- 6.6 IMPACT OF AI/GEN AI ON DDOS PROTECTION AND MITIGATION SECURITY MARKET
- 6.6.1 USE CASES OF GENERATIVE AI IN DDOS PROTECTION AND MITIGATION SECURITY
- 6.6.2 BEST PRACTICES
- 6.6.2.1 BFSI
- 6.6.2.2 Government
- 6.6.2.3 Healthcare
- 6.6.3 CASE STUDIES OF GENERATIVE AI IMPLEMENTATION
- 6.6.3.1 GenAI-enhanced traffic intelligence for large-scale cloud infrastructure
- 6.6.3.2 AI-automated incident analysis for multi-national financial group
- 6.6.3.3 GenAI-driven botnet attribution for government cyber defense agency
- 6.6.4 CLIENT READINESS AND IMPACT ASSESSMENT
- 6.6.4.1 Client A: Global digital commerce platform
- 6.6.4.2 Client B: Major public sector department
- 6.6.4.3 Client C: Large healthcare network
7 REGULATORY LANDSCAPE
- 7.1 REGULATORY LANDSCAPE
- 7.1.1 REGULATORY BODIES, GOVERNMENT AGENCIES, AND OTHER ORGANIZATIONS
- 7.1.1.1 National Credit Union Administration
- 7.1.1.2 Federal Financial Institutions Examination Council
- 7.1.1.3 General Data Protection Regulation (GDPR)
- 7.1.1.4 Payment Card Industry Data Security Standard (PCI-DSS)
- 7.1.1.5 Health Insurance Portability And Accountability Act (HIPAA)
- 7.1.1.6 Gramm-Leach-Bliley (GLB) Act
- 7.1.1.7 Sarbanes-Oxley (SOX) Act
- 7.1.1.8 SOC 2
- 7.1.1.9 SWIFT CSP
- 7.1.1 REGULATORY BODIES, GOVERNMENT AGENCIES, AND OTHER ORGANIZATIONS
8 CUSTOMER LANDSCAPE AND BUYER BEHAVIOR
- 8.1 DECISION-MAKING PROCESS
- 8.2 BUYER STAKEHOLDERS AND BUYING EVALUATION CRITERIA
- 8.2.1 KEY STAKEHOLDERS IN BUYING PROCESS
- 8.2.2 BUYING CRITERIA
- 8.2.3 ADOPTION BARRIERS AND INTERNAL CHALLENGES
9 DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY OFFERING
- 9.1 INTRODUCTION
- 9.1.1 OFFERING: DDOS PROTECTION AND MITIGATION SECURITY MARKET DRIVERS
- 9.2 HARDWARE SOLUTIONS
- 9.2.1 FIREWALLS
- 9.2.1.1 Hardware firewalls filter and block malicious traffic to enable efficient server access for legitimate requests
- 9.2.2 INTRUSION DETECTION AND PREVENTION SYSTEMS (IDPS)
- 9.2.2.1 IDPS prevents DDoS attacks by continuously monitoring network traffic and actively blocking malicious requests
- 9.2.3 LOAD BALANCERS
- 9.2.3.1 Load balancers protect against DDoS attacks by distributing traffic across multiple servers
- 9.2.4 OTHER HARDWARE SOLUTIONS
- 9.2.1 FIREWALLS
- 9.3 SOFTWARE SOLUTIONS
- 9.3.1 GLOBAL RISE IN IOT DEVICES TO DRIVE MARKET
- 9.4 SERVICES
- 9.4.1 PROFESSIONAL SERVICES
- 9.4.2 DESIGN AND IMPLEMENTATION
- 9.4.2.1 Increase in need to improve network performance and reliability
- 9.4.3 CONSULTING AND ADVISORY
- 9.4.3.1 Growing concerns for cybersecurity and adoption of advanced technologies
- 9.4.4 TRAINING AND EDUCATION
- 9.4.4.1 Rising need for training and creating awareness of DDoS attacks
- 9.4.5 SUPPORT AND MAINTENANCE
- 9.4.5.1 Rising need for support for technical issues and guidance
- 9.4.6 MANAGED SERVICES
- 9.4.6.1 Need to increase business efficiency and operations
10 DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY SOLUTION TYPE
- 10.1 INTRODUCTION
- 10.1.1 SOLUTION TYPE: DDOS PROTECTION AND MITIGATION SECURITY MARKET DRIVERS
- 10.2 NETWORK TRAFFIC ANALYZERS
- 10.2.1 NETWORK LAYER ATTACKS TO INCREASE ADOPTION OF DDOS PROTECTION SOLUTIONS
- 10.3 THREAT MITIGATION SYSTEMS
- 10.3.1 RISE IN LAYER 7 ATTACKS TO INCREASE DEMAND FOR DDOS PROTECTION AND MITIGATION SECURITY SOLUTIONS
- 10.4 BOTNET DETECTION & MANAGEMENT
- 10.4.1 EVOLVING DISRUPTIVE TECHNOLOGIES AND EASY AVAILABILITY OF CLOUD-BASED APPLICATIONS TO DRIVE MARKET
- 10.5 OTHER SOLUTION TYPES
11 DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY APPLICATION AREA
- 11.1 INTRODUCTION
- 11.1.1 APPLICATION AREA: DDOS PROTECTION AND MITIGATION SECURITY MARKET DRIVERS
- 11.2 NETWORK SECURITY
- 11.2.1 INCREASING NEED TO ENHANCE NETWORK PERFORMANCE AND ELIMINATE DISRUPTIONS
- 11.3 APPLICATION SECURITY
- 11.3.1 RISING NEED TO MITIGATE DDOS ATTACKS AND MAINTAIN PROTECTION
- 11.4 CLOUD SECURITY
- 11.4.1 GREATER NEED FOR CLOUD-BASED APPLICATIONS SECURITY TO DRIVE MARKET
- 11.5 ENDPOINT SECURITY
- 11.5.1 INCREASING MOBILE DEVICES AND DIGITAL TRANSFORMATIONS TO DRIVE MARKET
12 DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY DEPLOYMENT MODE
- 12.1 INTRODUCTION
- 12.1.1 DEPLOYMENT MODE: DDOS PROTECTION AND MITIGATION SECURITY MARKET DRIVERS
- 12.2 ON-PREMISES
- 12.2.1 ON-PREMISES SERVICES PROVIDE FULL CONTROL OF DEPLOYED SOLUTIONS IT'S STAFF
- 12.3 CLOUD
- 12.3.1 CLOUD DEPLOYMENT HELPS MANAGE DNS, REROUTE TRAFFIC, AND SAFEGUARD WEBSITE TRAFFIC
13 DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY ORGANIZATION SIZE
- 13.1 INTRODUCTION
- 13.1.1 ORGANIZATION SIZE: DDOS PROTECTION AND MITIGATION SECURITY MARKET DRIVERS
- 13.2 LARGE ENTERPRISES
- 13.2.1 INCREASING SEVERITY OF DDOS DAMAGE CAUSED BY SINGLE ATTACK TO DRIVE MARKET
- 13.3 SMALL & MEDIUM-SIZED ENTERPRISES
- 13.3.1 GROWING NEED TO MITIGATE SECURITY ATTACKS TO ENHANCE MARKET GROWTH
14 DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY VERTICAL
- 14.1 INTRODUCTION
- 14.1.1 VERTICAL: DDOS PROTECTION AND MITIGATION SECURITY MARKET DRIVERS
- 14.2 GOVERNMENT AND DEFENSE
- 14.2.1 INCREASING NEED FOR DDOS PROTECTION AND MITIGATION SECURITY SOLUTIONS AND SERVICES TO HELP MARKET GROWTH
- 14.3 BANKING, FINANCIAL SERVICES, AND INSURANCE
- 14.3.1 FRAGILE DATA CENTER SECURITY AND RISK OF CLOUD STORAGE DATA LEAKS TO DRIVE MARKET
- 14.4 MANUFACTURING
- 14.4.1 EVOLVING VOLUMETRIC DDOS ATTACKS ON MANUFACTURING PROCESSES TO CONTRIBUTE TO MARKET GROWTH
- 14.5 ENERGY AND UTILITIES
- 14.5.1 INCREASING ADOPTION OF SMART SYSTEMS AND APPLICATIONS TO DRIVE MARKET
- 14.6 IT AND ITES
- 14.6.1 RISE OF ADVANCED TECHNOLOGIES TO FUEL MARKET
- 14.7 TELECOM
- 14.7.1 RISE IN NUMBER OF WEB AND MOBILE APPLICATIONS TO FUEL MARKET
- 14.8 HEALTHCARE
- 14.8.1 REGULATORY NORMS TO INCREASE DEPLOYMENT OF DDOS PROTECTION AND MITIGATION SECURITY SOLUTIONS
- 14.9 EDUCATION
- 14.9.1 NEED FOR CONFIDENTIALITY, INTEGRITY, AND EASY AVAILABILITY OF DATA AND RESOURCES TO AUGMENT MARKET GROWTH
- 14.10 RETAIL
- 14.10.1 GROWING CYBERATTACKS AND DATA THEFT TO INCREASE ADOPTION OF DDOS PROTECTION AND MITIGATION SECURITY SOLUTIONS
- 14.11 OTHER VERTICALS
15 DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY REGION
- 15.1 INTRODUCTION
- 15.2 NORTH AMERICA
- 15.2.1 NORTH AMERICA: MACROECONOMIC OUTLOOK
- 15.2.2 US
- 15.2.2.1 Presence of major vendors in US driving market growth
- 15.2.3 CANADA
- 15.2.3.1 Rapid technological advancements and increasing DDoS attacks on network infrastructure to drive market
- 15.3 EUROPE
- 15.3.1 EUROPE: MACROECONOMIC OUTLOOK
- 15.3.2 UK
- 15.3.2.1 Increasing demand for monitoring solutions among SMEs to drive market
- 15.3.3 GERMANY
- 15.3.3.1 Increasing investments in DDoS protection and mitigation solutions to drive market
- 15.3.4 REST OF EUROPE
- 15.4 ASIA PACIFIC
- 15.4.1 ASIA PACIFIC: MACROECONOMIC OUTLOOK
- 15.4.2 CHINA
- 15.4.2.1 Development of cybersecurity safeguard system to fuel market
- 15.4.3 JAPAN
- 15.4.3.1 Stringent laws and regulations for cybersecurity to drive market
- 15.4.4 INDIA
- 15.4.4.1 Increasing DDoS attacks leading to adoption of DDoS protection and mitigation security solutions
- 15.4.5 REST OF ASIA PACIFIC
- 15.5 MIDDLE EAST & AFRICA
- 15.5.1 MIDDLE EAST & AFRICA: MACROECONOMIC OUTLOOK
- 15.5.2 KSA
- 15.5.2.1 Increasing investments in mitigation security and growth in number of startups to drive market
- 15.5.3 UAE
- 15.5.3.1 Growing reliance on cloud-based applications to boost market
- 15.5.4 SOUTH AFRICA
- 15.5.4.1 Government initiatives and substantial foreign investments to drive market
- 15.5.5 REST OF MIDDLE EAST & AFRICA
- 15.6 LATIN AMERICA
- 15.6.1 LATIN AMERICA: MACROECONOMIC OUTLOOK
- 15.6.2 BRAZIL
- 15.6.2.1 Increasing focus on establishing effective cybersecurity strategies to drive market
- 15.6.3 MEXICO
- 15.6.3.1 Rising adoption of cloud-based services to drive market
- 15.6.4 REST OF LATIN AMERICA
16 COMPETITIVE LANDSCAPE
- 16.1 INTRODUCTION
- 16.2 KEY PLAYER STRATEGIES/RIGHT TO WIN, 2022-2025
- 16.3 REVENUE ANALYSIS, 2020-2024
- 16.4 MARKET SHARE ANALYSIS, 2024
- 16.4.1 MARKET RANKING ANALYSIS, 2024
- 16.5 COMPANY EVALUATION MATRIX: KEY PLAYERS, 2024
- 16.5.1 STARS
- 16.5.2 EMERGING LEADERS
- 16.5.3 PERVASIVE PLAYERS
- 16.5.4 PARTICIPANTS
- 16.5.5 COMPANY FOOTPRINT: KEY PLAYERS, 2024
- 16.5.5.1 Company footprint
- 16.5.5.2 Regional footprint
- 16.5.5.3 Offering footprint
- 16.5.5.4 Vertical footprint
- 16.6 COMPANY EVALUATION MATRIX: STARTUPS/SMES, 2024
- 16.6.1 PROGRESSIVE COMPANIES
- 16.6.2 RESPONSIVE COMPANIES
- 16.6.3 DYNAMIC COMPANIES
- 16.6.4 STARTING BLOCKS
- 16.6.5 COMPETITIVE BENCHMARKING: STARTUPS/SMES, 2024
- 16.6.5.1 Detailed list of key startups/SMEs
- 16.6.5.2 Competitive benchmarking of key startups/SMEs
- 16.7 COMPETITIVE SCENARIO
- 16.7.1 PRODUCT LAUNCHES & ENHANCEMENTS
- 16.7.2 DEALS
- 16.8 BRAND/PRODUCT COMPARISON
- 16.9 COMPANY VALUATION AND FINANCIAL METRICS, 2025
- 16.9.1 COMPANY VALUATION
- 16.9.2 FINANCIAL METRICS
17 COMPANY PROFILES
- 17.1 KEY PLAYERS
- 17.1.1 NETSCOUT
- 17.1.1.1 Business overview
- 17.1.1.2 Products/Solutions/Services offered
- 17.1.1.3 Recent developments
- 17.1.1.3.1 Product launches & enhancements
- 17.1.1.3.2 Deals
- 17.1.1.3.3 Expansions
- 17.1.1.4 MnM view
- 17.1.1.4.1 Right to win
- 17.1.1.4.2 Strategic choices
- 17.1.1.4.3 Weaknesses and competitive threats
- 17.1.2 AKAMAI TECHNOLOGIES
- 17.1.2.1 Business overview
- 17.1.2.2 Products/Solutions/Services offered
- 17.1.2.3 Recent developments
- 17.1.2.3.1 Product launches & enhancements
- 17.1.2.3.2 Deals
- 17.1.2.3.3 Expansions
- 17.1.2.4 MnM view
- 17.1.2.4.1 Right to win
- 17.1.2.4.2 Strategic choices
- 17.1.2.4.3 Weaknesses and competitive threats
- 17.1.3 RADWARE
- 17.1.3.1 Business overview
- 17.1.3.2 Products/Solutions/Services offered
- 17.1.3.3 Recent developments
- 17.1.3.3.1 Product launches & enhancements
- 17.1.3.3.2 Deals
- 17.1.3.4 MnM view
- 17.1.3.4.1 Right to win
- 17.1.3.4.2 Strategic choices
- 17.1.3.4.3 Weaknesses and competitive threats
- 17.1.4 CLOUDFLARE
- 17.1.4.1 Business overview
- 17.1.4.2 Products/Solutions/Services offered
- 17.1.4.3 MnM view
- 17.1.4.3.1 Key strengths
- 17.1.4.3.2 Strategic choices
- 17.1.4.3.3 Weaknesses and competitive threats
- 17.1.5 FORTINET
- 17.1.5.1 Business overview
- 17.1.5.2 Products/Solutions/Services offered
- 17.1.5.3 Recent developments
- 17.1.5.3.1 Deals
- 17.1.5.4 MnM view
- 17.1.5.4.1 Key strengths
- 17.1.5.4.2 Strategic choices
- 17.1.5.4.3 Weaknesses and competitive threats
- 17.1.6 HUAWEI
- 17.1.6.1 Business overview
- 17.1.6.2 Products/Solutions/Services offered
- 17.1.6.3 Recent developments
- 17.1.6.3.1 Deals
- 17.1.7 LINK11
- 17.1.7.1 Business overview
- 17.1.7.2 Products/Solutions/Services offered
- 17.1.7.3 Recent developments
- 17.1.7.3.1 Product launches & enhancements
- 17.1.7.3.2 Deals
- 17.1.8 IMPERVA (A THALES COMPANY)
- 17.1.8.1 Business overview
- 17.1.8.2 Products/Solutions/Services offered
- 17.1.8.3 Recent developments
- 17.1.8.3.1 Deals
- 17.1.9 BT
- 17.1.9.1 Business overview
- 17.1.9.2 Products/Solutions/Services offered
- 17.1.9.3 Recent developments
- 17.1.9.3.1 Deals
- 17.1.10 A10 NETWORKS
- 17.1.10.1 Business overview
- 17.1.10.2 Products/Solutions/Services offered
- 17.1.1 NETSCOUT
- 17.2 OTHER PLAYERS
- 17.2.1 FASTLY
- 17.2.2 F5
- 17.2.3 CORERO
- 17.2.4 ALLOT
- 17.2.5 STRATACORE
- 17.2.6 SUCURI
- 17.2.7 NSFOCUS
- 17.2.8 LUMEN TECHNOLOGIES
- 17.3 SMES/STARTUPS
- 17.3.1 STACKPATH
- 17.3.2 SECEON
- 17.3.3 HALTDOS
- 17.3.4 DDOS-GUARD
- 17.3.5 INDUSFACE
- 17.3.6 ACTIVEREACH
- 17.3.7 MLYTICS
- 17.3.8 NEXUSGUARD
- 17.3.9 RIOREY
- 17.3.10 PHOENIXNAP
- 17.3.11 COMODO SECURITY SOLUTIONS
18 RESEARCH METHODOLOGY
- 18.1 RESEARCH DATA
- 18.1.1 SECONDARY DATA
- 18.1.2 PRIMARY DATA
- 18.1.2.1 Primary interviews with experts
- 18.1.2.2 Breakdown of primary profiles
- 18.1.2.3 Key insights from industry experts
- 18.2 MARKET SIZE ESTIMATION
- 18.2.1 TOP-DOWN APPROACH
- 18.2.2 BOTTOM-UP APPROACH
- 18.2.3 DDOS PROTECTION AND MITIGATION SECURITY MARKET ESTIMATION: DEMAND-SIDE ANALYSIS
- 18.3 DATA TRIANGULATION
- 18.4 RISK ASSESSMENT
- 18.5 RESEARCH ASSUMPTIONS
- 18.6 RESEARCH LIMITATIONS
19 ADJACENT AND RELATED MARKETS
- 19.1 INTRODUCTION
- 19.2 CYBERSECURITY MARKET
- 19.2.1 MARKET DEFINITION
- 19.3 SECURITY AS A SERVICE MARKET
- 19.3.1 MARKET DEFINITION
20 APPENDIX
- 20.1 DISCUSSION GUIDE
- 20.2 KNOWLEDGESTORE: MARKETSANDMARKETS' SUBSCRIPTION PORTAL
- 20.3 CUSTOMIZATION OPTIONS
- 20.4 RELATED REPORTS
- 20.5 AUTHOR DETAILS
List of Tables
- TABLE 1 INCLUSIONS & EXCLUSIONS
- TABLE 2 USD EXCHANGE RATES, 2020-2024
- TABLE 3 IMPACT OF PORTER'S FIVE FORCES ON DDOS PROTECTION AND MITIGATION SECURITY MARKET
- TABLE 4 ROLE OF COMPANIES IN ECOSYSTEM
- TABLE 5 AVERAGE SELLING PRICE OF KEY PLAYERS, BY OFFERING, 2024
- TABLE 6 INDICATIVE PRICING ANALYSIS OF DDOS PROTECTION AND MITIGATION SECURITY, BY OFFERING, 2024
- TABLE 7 DDOS PROTECTION AND MITIGATION SECURITY MARKET: LIST OF KEY CONFERENCES AND EVENTS, 2025
- TABLE 8 US-ADJUSTED RECIPROCAL TARIFF RATES
- TABLE 9 EXPECTED CHANGE IN PRICES AND LIKELY IMPACT ON END-USE MARKET DUE TO TARIFF IMPACT
- TABLE 10 LIST OF MAJOR PATENTS, 2015-2024
- TABLE 11 NORTH AMERICA: LIST OF REGULATORY BODIES, GOVERNMENT AGENCIES, AND OTHER ORGANIZATIONS
- TABLE 12 EUROPE: LIST OF REGULATORY BODIES, GOVERNMENT AGENCIES, AND OTHER ORGANIZATIONS
- TABLE 13 ASIA PACIFIC: LIST OF REGULATORY BODIES, GOVERNMENT AGENCIES, AND OTHER ORGANIZATIONS
- TABLE 14 REST OF THE WORLD: LIST OF REGULATORY BODIES, GOVERNMENT AGENCIES, AND OTHER ORGANIZATIONS
- TABLE 15 INFLUENCE OF STAKEHOLDERS ON BUYING PROCESS FOR TOP THREE VERTICALS (%)
- TABLE 16 KEY BUYING CRITERIA FOR TOP THREE VERTICALS
- TABLE 17 DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY OFFERING, 2019-2024 (USD MILLION)
- TABLE 18 DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY OFFERING, 2025-2030 (USD MILLION)
- TABLE 19 HARDWARE SOLUTIONS: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 20 HARDWARE SOLUTIONS: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 21 FIREWALLS: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 22 FIREWALLS: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 23 INTRUSION DETECTION AND PREVENTION SYSTEMS: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 24 INTRUSION DETECTION AND PREVENTION SYSTEMS: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 25 LOAD BALANCERS: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 26 LOAD BALANCERS: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 27 OTHER HARDWARE SOLUTIONS: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 28 OTHER HARDWARE SOLUTIONS: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 29 SOFTWARE SOLUTIONS: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 30 SOFTWARE SOLUTIONS: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 31 SERVICES: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY TYPE, 2019-2024 (USD MILLION)
- TABLE 32 SERVICES: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY TYPE, 2025-2030 (USD MILLION)
- TABLE 33 SERVICES: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 34 SERVICES: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 35 PROFESSIONAL SERVICES: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 36 PROFESSIONAL SERVICES: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 37 PROFESSIONAL SERVICES: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY TYPE, 2019-2024 (USD MILLION)
- TABLE 38 PROFESSIONAL SERVICES: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY TYPE, 2025-2030 (USD MILLION)
- TABLE 39 DESIGN AND IMPLEMENTATION: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 40 DESIGN AND IMPLEMENTATION: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 41 CONSULTING AND ADVISORY: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 42 CONSULTING AND ADVISORY: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 43 TRAINING AND EDUCATION: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 44 TRAINING AND EDUCATION: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 45 SUPPORT AND MAINTENANCE: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 46 SUPPORT AND MAINTENANCE: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 47 MANAGED SERVICES: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 48 MANAGED SERVICES: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 49 DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY SOLUTION TYPE, 2019-2024 (USD MILLION)
- TABLE 50 DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY SOLUTION TYPE, 2025-2030 (USD MILLION)
- TABLE 51 NETWORK TRAFFIC ANALYZERS: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 52 NETWORK TRAFFIC ANALYZERS: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 53 THREAT MITIGATION SYSTEMS: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 54 THREAT MITIGATION SYSTEMS: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 55 BOTNET DETECTION & MANAGEMENT: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 56 BOTNET DETECTION & MANAGEMENT: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 57 OTHER SOLUTION TYPES: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 58 OTHER SOLUTION TYPES: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 59 DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY APPLICATION AREA, 2019-2024 (USD MILLION)
- TABLE 60 DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY APPLICATION AREA, 2025-2030 (USD MILLION)
- TABLE 61 NETWORK SECURITY: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 62 NETWORK SECURITY: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 63 APPLICATION SECURITY: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 64 APPLICATION SECURITY: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 65 CLOUD SECURITY: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 66 CLOUD SECURITY: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 67 ENDPOINT SECURITY: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 68 ENDPOINT SECURITY: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 69 DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY DEPLOYMENT MODE, 2019-2024 (USD MILLION)
- TABLE 70 DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY DEPLOYMENT MODE, 2025-2030 (USD MILLION)
- TABLE 71 ON-PREMISES: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 72 ON-PREMISES: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 73 CLOUD: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 74 CLOUD: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 75 DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY ORGANIZATION SIZE, 2019-2024 (USD MILLION)
- TABLE 76 DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY ORGANIZATION SIZE, 2025-2030 (USD MILLION)
- TABLE 77 LARGE ENTERPRISES: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 78 LARGE ENTERPRISES: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 79 SMALL & MEDIUM-SIZED ENTERPRISES: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 80 SMALL & MEDIUM-SIZED ENTERPRISES: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 81 DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 82 DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 83 GOVERNMENT AND DEFENSE: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 84 GOVERNMENT AND DEFENSE: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 85 BFSI: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 86 BFSI: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 87 MANUFACTURING: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 88 MANUFACTURING: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 89 ENERGY AND UTILITIES: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 90 ENERGY AND UTILITIES: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 91 IT AND ITES: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 92 IT AND ITES: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 93 TELECOM: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 94 TELECOM: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 95 HEALTHCARE: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 96 HEALTHCARE: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 97 EDUCATION: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 98 EDUCATION: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 99 RETAIL: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 100 RETAIL: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 101 OTHER VERTICALS: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 102 OTHER VERTICALS: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 103 DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 104 DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 105 NORTH AMERICA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY OFFERING, 2019-2024 (USD MILLION)
- TABLE 106 NORTH AMERICA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY OFFERING, 2025-2030 (USD MILLION)
- TABLE 107 NORTH AMERICA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY HARDWARE SOLUTION, 2019-2024 (USD MILLION)
- TABLE 108 NORTH AMERICA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY HARDWARE SOLUTION, 2025-2030 (USD MILLION)
- TABLE 109 NORTH AMERICA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY SERVICE, 2019-2024 (USD MILLION)
- TABLE 110 NORTH AMERICA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY SERVICE, 2025-2030 (USD MILLION)
- TABLE 111 NORTH AMERICA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY PROFESSIONAL SERVICE, 2019-2024 (USD MILLION)
- TABLE 112 NORTH AMERICA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY PROFESSIONAL SERVICE, 2025-2030 (USD MILLION)
- TABLE 113 NORTH AMERICA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY SOLUTION TYPE, 2019-2024 (USD MILLION)
- TABLE 114 NORTH AMERICA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY SOLUTION TYPE, 2025-2030 (USD MILLION)
- TABLE 115 NORTH AMERICA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY APPLICATION AREA, 2019-2024 (USD MILLION)
- TABLE 116 NORTH AMERICA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY APPLICATION AREA, 2025-2030 (USD MILLION)
- TABLE 117 NORTH AMERICA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY DEPLOYMENT MODE, 2019-2024 (USD MILLION)
- TABLE 118 NORTH AMERICA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY DEPLOYMENT MODE, 2025-2030 (USD MILLION)
- TABLE 119 NORTH AMERICA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY ORGANIZATION SIZE, 2019-2024 (USD MILLION)
- TABLE 120 NORTH AMERICA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY ORGANIZATION SIZE, 2025-2030 (USD MILLION)
- TABLE 121 NORTH AMERICA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 122 NORTH AMERICA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 123 NORTH AMERICA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY COUNTRY, 2019-2024 (USD MILLION)
- TABLE 124 NORTH AMERICA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY COUNTRY, 2025-2030 (USD MILLION)
- TABLE 125 US: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY OFFERING, 2019-2024 (USD MILLION)
- TABLE 126 US: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY OFFERING, 2025-2030 (USD MILLION)
- TABLE 127 US: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY HARDWARE SOLUTION, 2019-2024 (USD MILLION)
- TABLE 128 US: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY HARDWARE SOLUTION, 2025-2030 (USD MILLION)
- TABLE 129 US: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY SERVICE, 2019-2024 (USD MILLION)
- TABLE 130 US: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY SERVICE, 2025-2030 (USD MILLION)
- TABLE 131 US: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY PROFESSIONAL SERVICE, 2019-2024 (USD MILLION)
- TABLE 132 US: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY PROFESSIONAL SERVICE, 2025-2030 (USD MILLION)
- TABLE 133 US: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY SOLUTION TYPE, 2019-2024 (USD MILLION)
- TABLE 134 US: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY SOLUTION TYPE, 2025-2030 (USD MILLION)
- TABLE 135 US: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY APPLICATION AREA, 2019-2024 (USD MILLION)
- TABLE 136 US: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY APPLICATION AREA, 2025-2030 (USD MILLION)
- TABLE 137 US: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY DEPLOYMENT MODE, 2019-2024 (USD MILLION)
- TABLE 138 US: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY DEPLOYMENT MODE, 2025-2030 (USD MILLION)
- TABLE 139 US: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY ORGANIZATION SIZE, 2019-2024 (USD MILLION)
- TABLE 140 US: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY ORGANIZATION SIZE, 2025-2030 (USD MILLION)
- TABLE 141 US: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 142 US: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 143 CANADA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY OFFERING, 2019-2024 (USD MILLION)
- TABLE 144 CANADA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY OFFERING, 2025-2030 (USD MILLION)
- TABLE 145 CANADA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY HARDWARE SOLUTION, 2019-2024 (USD MILLION)
- TABLE 146 CANADA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY HARDWARE SOLUTION, 2025-2030 (USD MILLION)
- TABLE 147 CANADA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY SERVICE, 2019-2024 (USD MILLION)
- TABLE 148 CANADA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY SERVICE, 2025-2030 (USD MILLION)
- TABLE 149 CANADA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY PROFESSIONAL SERVICE, 2019-2024 (USD MILLION)
- TABLE 150 CANADA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY PROFESSIONAL SERVICE, 2025-2030 (USD MILLION)
- TABLE 151 CANADA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY SOLUTION TYPE, 2019-2024 (USD MILLION)
- TABLE 152 CANADA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY SOLUTION TYPE, 2025-2030 (USD MILLION)
- TABLE 153 CANADA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY APPLICATION AREA, 2019-2024 (USD MILLION)
- TABLE 154 CANADA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY APPLICATION AREA, 2025-2030 (USD MILLION)
- TABLE 155 CANADA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY DEPLOYMENT MODE, 2019-2024 (USD MILLION)
- TABLE 156 CANADA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY DEPLOYMENT MODE, 2025-2030 (USD MILLION)
- TABLE 157 CANADA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY ORGANIZATION SIZE, 2019-2024 (USD MILLION)
- TABLE 158 CANADA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY ORGANIZATION SIZE, 2025-2030 (USD MILLION)
- TABLE 159 CANADA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 160 CANADA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 161 EUROPE: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY OFFERING, 2019-2024 (USD MILLION)
- TABLE 162 EUROPE: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY OFFERING, 2025-2030 (USD MILLION)
- TABLE 163 EUROPE: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY HARDWARE SOLUTION, 2019-2024 (USD MILLION)
- TABLE 164 EUROPE: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY HARDWARE SOLUTION, 2025-2030 (USD MILLION)
- TABLE 165 EUROPE: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY SERVICE, 2019-2024 (USD MILLION)
- TABLE 166 EUROPE: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY SERVICE, 2025-2030 (USD MILLION)
- TABLE 167 EUROPE: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY PROFESSIONAL SERVICE, 2019-2024 (USD MILLION)
- TABLE 168 EUROPE: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY PROFESSIONAL SERVICE, 2025-2030 (USD MILLION)
- TABLE 169 EUROPE: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY SOLUTION TYPE, 2019-2024 (USD MILLION)
- TABLE 170 EUROPE: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY SOLUTION TYPE, 2025-2030 (USD MILLION)
- TABLE 171 EUROPE: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY APPLICATION AREA, 2019-2024 (USD MILLION)
- TABLE 172 EUROPE: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY APPLICATION AREA, 2025-2030 (USD MILLION)
- TABLE 173 EUROPE: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY DEPLOYMENT MODE, 2019-2024 (USD MILLION)
- TABLE 174 EUROPE: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY DEPLOYMENT MODE, 2025-2030 (USD MILLION)
- TABLE 175 EUROPE: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY ORGANIZATION SIZE, 2019-2024 (USD MILLION)
- TABLE 176 EUROPE: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY ORGANIZATION SIZE, 2025-2030 (USD MILLION)
- TABLE 177 EUROPE: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 178 EUROPE: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 179 EUROPE: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY COUNTRY, 2019-2024 (USD MILLION)
- TABLE 180 EUROPE: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY COUNTRY, 2025-2030 (USD MILLION)
- TABLE 181 UK: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY OFFERING, 2019-2024 (USD MILLION)
- TABLE 182 UK: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY OFFERING, 2025-2030 (USD MILLION)
- TABLE 183 UK: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY HARDWARE SOLUTION, 2019-2024 (USD MILLION)
- TABLE 184 UK: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY HARDWARE SOLUTION, 2025-2030 (USD MILLION)
- TABLE 185 UK: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY SERVICE, 2019-2024 (USD MILLION)
- TABLE 186 UK: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY SERVICE, 2025-2030 (USD MILLION)
- TABLE 187 UK: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY PROFESSIONAL SERVICE, 2019-2024 (USD MILLION)
- TABLE 188 UK: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY PROFESSIONAL SERVICE, 2025-2030 (USD MILLION)
- TABLE 189 UK: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY SOLUTION TYPE, 2019-2024 (USD MILLION)
- TABLE 190 UK: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY SOLUTION TYPE, 2025-2030 (USD MILLION)
- TABLE 191 UK: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY APPLICATION AREA, 2019-2024 (USD MILLION)
- TABLE 192 UK: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY APPLICATION AREA, 2025-2030 (USD MILLION)
- TABLE 193 UK: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY DEPLOYMENT MODE, 2019-2024 (USD MILLION)
- TABLE 194 UK: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY DEPLOYMENT MODE, 2025-2030 (USD MILLION)
- TABLE 195 UK: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY ORGANIZATION SIZE, 2019-2024 (USD MILLION)
- TABLE 196 UK: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY ORGANIZATION SIZE, 2025-2030 (USD MILLION)
- TABLE 197 UK: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 198 UK: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 199 GERMANY: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY OFFERING, 2019-2024 (USD MILLION)
- TABLE 200 GERMANY: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY OFFERING, 2025-2030 (USD MILLION)
- TABLE 201 GERMANY: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY HARDWARE SOLUTION, 2019-2024 (USD MILLION)
- TABLE 202 GERMANY: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY HARDWARE SOLUTION, 2025-2030 (USD MILLION)
- TABLE 203 GERMANY: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY SERVICE, 2019-2024 (USD MILLION)
- TABLE 204 GERMANY: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY SERVICE, 2025-2030 (USD MILLION)
- TABLE 205 GERMANY: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY PROFESSIONAL SERVICE, 2019-2024 (USD MILLION)
- TABLE 206 GERMANY: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY PROFESSIONAL SERVICE, 2025-2030 (USD MILLION)
- TABLE 207 GERMANY: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY SOLUTION TYPE, 2019-2024 (USD MILLION)
- TABLE 208 GERMANY: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY SOLUTION TYPE, 2025-2030 (USD MILLION)
- TABLE 209 GERMANY: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY APPLICATION AREA, 2019-2024 (USD MILLION)
- TABLE 210 GERMANY: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY APPLICATION AREA, 2025-2030 (USD MILLION)
- TABLE 211 GERMANY: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY DEPLOYMENT MODE, 2019-2024 (USD MILLION)
- TABLE 212 GERMANY: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY DEPLOYMENT MODE, 2025-2030 (USD MILLION)
- TABLE 213 GERMANY: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY ORGANIZATION SIZE, 2019-2024 (USD MILLION)
- TABLE 214 GERMANY: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY ORGANIZATION SIZE, 2025-2030 (USD MILLION)
- TABLE 215 GERMANY: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 216 GERMANY: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 217 REST OF EUROPE: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY OFFERING, 2019-2024 (USD MILLION)
- TABLE 218 REST OF EUROPE: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY OFFERING, 2025-2030 (USD MILLION)
- TABLE 219 REST OF EUROPE: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY HARDWARE SOLUTION, 2019-2024 (USD MILLION)
- TABLE 220 REST OF EUROPE: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY HARDWARE SOLUTION, 2025-2030 (USD MILLION)
- TABLE 221 REST OF EUROPE: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY SERVICE, 2019-2024 (USD MILLION)
- TABLE 222 REST OF EUROPE: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY SERVICE, 2025-2030 (USD MILLION)
- TABLE 223 REST OF EUROPE: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY PROFESSIONAL SERVICE, 2019-2024 (USD MILLION)
- TABLE 224 REST OF EUROPE: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY PROFESSIONAL SERVICE, 2025-2030 (USD MILLION)
- TABLE 225 REST OF EUROPE: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY SOLUTION TYPE, 2019-2024 (USD MILLION)
- TABLE 226 REST OF EUROPE: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY SOLUTION TYPE, 2025-2030 (USD MILLION)
- TABLE 227 REST OF EUROPE: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY APPLICATION AREA, 2019-2024 (USD MILLION)
- TABLE 228 REST OF EUROPE: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY APPLICATION AREA, 2025-2030 (USD MILLION)
- TABLE 229 REST OF EUROPE: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY DEPLOYMENT MODE, 2019-2024 (USD MILLION)
- TABLE 230 REST OF EUROPE: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY DEPLOYMENT MODE, 2025-2030 (USD MILLION)
- TABLE 231 REST OF EUROPE: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY ORGANIZATION SIZE, 2019-2024 (USD MILLION)
- TABLE 232 REST OF EUROPE: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY ORGANIZATION SIZE, 2025-2030 (USD MILLION)
- TABLE 233 REST OF EUROPE: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 234 REST OF EUROPE: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 235 ASIA PACIFIC: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY OFFERING, 2019-2024 (USD MILLION)
- TABLE 236 ASIA PACIFIC: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY OFFERING, 2025-2030 (USD MILLION)
- TABLE 237 ASIA PACIFIC: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY HARDWARE SOLUTION, 2019-2024 (USD MILLION)
- TABLE 238 ASIA PACIFIC: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY HARDWARE SOLUTION, 2025-2030 (USD MILLION)
- TABLE 239 ASIA PACIFIC: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY SERVICE, 2019-2024 (USD MILLION)
- TABLE 240 ASIA PACIFIC: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY SERVICE, 2025-2030 (USD MILLION)
- TABLE 241 ASIA PACIFIC: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY PROFESSIONAL SERVICE, 2019-2024 (USD MILLION)
- TABLE 242 ASIA PACIFIC: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY PROFESSIONAL SERVICE, 2025-2030 (USD MILLION)
- TABLE 243 ASIA PACIFIC: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY SOLUTION TYPE, 2019-2024 (USD MILLION)
- TABLE 244 ASIA PACIFIC: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY SOLUTION TYPE, 2025-2030 (USD MILLION)
- TABLE 245 ASIA PACIFIC: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY APPLICATION AREA, 2019-2024 (USD MILLION)
- TABLE 246 ASIA PACIFIC: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY APPLICATION AREA, 2025-2030 (USD MILLION)
- TABLE 247 ASIA PACIFIC: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY DEPLOYMENT MODE, 2019-2024 (USD MILLION)
- TABLE 248 ASIA PACIFIC: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY DEPLOYMENT MODE, 2025-2030 (USD MILLION)
- TABLE 249 ASIA PACIFIC: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY ORGANIZATION SIZE, 2019-2024 (USD MILLION)
- TABLE 250 ASIA PACIFIC: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY ORGANIZATION SIZE, 2025-2030 (USD MILLION)
- TABLE 251 ASIA PACIFIC: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 252 ASIA PACIFIC: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 253 ASIA PACIFIC: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY COUNTRY, 2019-2024 (USD MILLION)
- TABLE 254 ASIA PACIFIC: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY COUNTRY, 2025-2030 (USD MILLION)
- TABLE 255 CHINA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY OFFERING, 2019-2024 (USD MILLION)
- TABLE 256 CHINA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY OFFERING, 2025-2030 (USD MILLION)
- TABLE 257 CHINA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY HARDWARE SOLUTION, 2019-2024 (USD MILLION)
- TABLE 258 CHINA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY HARDWARE SOLUTION, 2025-2030 (USD MILLION)
- TABLE 259 CHINA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY SERVICE, 2019-2024 (USD MILLION)
- TABLE 260 CHINA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY SERVICE, 2025-2030 (USD MILLION)
- TABLE 261 CHINA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY PROFESSIONAL SERVICE, 2019-2024 (USD MILLION)
- TABLE 262 CHINA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY PROFESSIONAL SERVICE, 2025-2030 (USD MILLION)
- TABLE 263 CHINA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY SOLUTION TYPE, 2019-2024 (USD MILLION)
- TABLE 264 CHINA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY SOLUTION TYPE, 2025-2030 (USD MILLION)
- TABLE 265 CHINA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY APPLICATION AREA, 2019-2024 (USD MILLION)
- TABLE 266 CHINA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY APPLICATION AREA, 2025-2030 (USD MILLION)
- TABLE 267 CHINA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY DEPLOYMENT MODE, 2019-2024 (USD MILLION)
- TABLE 268 CHINA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY DEPLOYMENT MODE, 2025-2030 (USD MILLION)
- TABLE 269 CHINA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY ORGANIZATION SIZE, 2019-2024 (USD MILLION)
- TABLE 270 CHINA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY ORGANIZATION SIZE, 2025-2030 (USD MILLION)
- TABLE 271 CHINA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 272 CHINA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 273 JAPAN: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY OFFERING, 2019-2024 (USD MILLION)
- TABLE 274 JAPAN: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY OFFERING, 2025-2030 (USD MILLION)
- TABLE 275 JAPAN: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY HARDWARE SOLUTION, 2019-2024 (USD MILLION)
- TABLE 276 JAPAN: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY HARDWARE SOLUTION, 2025-2030 (USD MILLION)
- TABLE 277 JAPAN: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY SERVICE, 2019-2024 (USD MILLION)
- TABLE 278 JAPAN: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY SERVICE, 2025-2030 (USD MILLION)
- TABLE 279 JAPAN: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY PROFESSIONAL SERVICE, 2019-2024 (USD MILLION)
- TABLE 280 JAPAN: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY PROFESSIONAL SERVICE, 2025-2030 (USD MILLION)
- TABLE 281 JAPAN DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY SOLUTION TYPE, 2019-2024 (USD MILLION)
- TABLE 282 JAPAN: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY SOLUTION TYPE, 2025-2030 (USD MILLION)
- TABLE 283 JAPAN: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY APPLICATION AREA, 2019-2024 (USD MILLION)
- TABLE 284 JAPAN: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY APPLICATION AREA, 2025-2030 (USD MILLION)
- TABLE 285 JAPAN DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY DEPLOYMENT MODE, 2019-2024 (USD MILLION)
- TABLE 286 JAPAN: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY DEPLOYMENT MODE, 2025-2030 (USD MILLION)
- TABLE 287 JAPAN: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY ORGANIZATION SIZE, 2019-2024 (USD MILLION)
- TABLE 288 JAPAN: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY ORGANIZATION SIZE, 2025-2030 (USD MILLION)
- TABLE 289 JAPAN: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 290 JAPAN: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 291 INDIA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY OFFERING, 2019-2024 (USD MILLION)
- TABLE 292 INDIA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY OFFERING, 2025-2030 (USD MILLION)
- TABLE 293 INDIA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY HARDWARE SOLUTION, 2019-2024 (USD MILLION)
- TABLE 294 INDIA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY HARDWARE SOLUTION, 2025-2030 (USD MILLION)
- TABLE 295 INDIA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY SERVICE, 2019-2024 (USD MILLION)
- TABLE 296 INDIA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY SERVICE, 2025-2030 (USD MILLION)
- TABLE 297 INDIA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY PROFESSIONAL SERVICE, 2019-2024 (USD MILLION)
- TABLE 298 INDIA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY PROFESSIONAL SERVICE, 2025-2030 (USD MILLION)
- TABLE 299 INDIA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY SOLUTION TYPE, 2019-2024 (USD MILLION)
- TABLE 300 INDIA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY SOLUTION TYPE, 2025-2030 (USD MILLION)
- TABLE 301 INDIA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY APPLICATION AREA, 2019-2024 (USD MILLION)
- TABLE 302 INDIA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY APPLICATION AREA, 2025-2030 (USD MILLION)
- TABLE 303 INDIA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY DEPLOYMENT MODE, 2019-2024 (USD MILLION)
- TABLE 304 INDIA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY DEPLOYMENT MODE, 2025-2030 (USD MILLION)
- TABLE 305 INDIA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY ORGANIZATION SIZE, 2019-2024 (USD MILLION)
- TABLE 306 INDIA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY ORGANIZATION SIZE, 2025-2030 (USD MILLION)
- TABLE 307 INDIA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 308 INDIA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 309 REST OF ASIA PACIFIC: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY OFFERING, 2019-2024 (USD MILLION)
- TABLE 310 REST OF ASIA PACIFIC: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY OFFERING, 2025-2030 (USD MILLION)
- TABLE 311 REST OF ASIA PACIFIC: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY HARDWARE SOLUTION, 2019-2024 (USD MILLION)
- TABLE 312 REST OF ASIA PACIFIC: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY HARDWARE SOLUTION, 2025-2030 (USD MILLION)
- TABLE 313 REST OF ASIA PACIFIC: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY SERVICE, 2019-2024 (USD MILLION)
- TABLE 314 REST OF ASIA PACIFIC: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY SERVICE, 2025-2030 (USD MILLION)
- TABLE 315 REST OF ASIA PACIFIC: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY PROFESSIONAL SERVICE, 2019-2024 (USD MILLION)
- TABLE 316 REST OF ASIA PACIFIC: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY PROFESSIONAL SERVICE, 2025-2030 (USD MILLION)
- TABLE 317 REST OF ASIA PACIFIC: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY SOLUTION TYPE, 2019-2024 (USD MILLION)
- TABLE 318 REST OF ASIA PACIFIC: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY SOLUTION TYPE, 2025-2030 (USD MILLION)
- TABLE 319 REST OF ASIA PACIFIC: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY APPLICATION AREA, 2019-2024 (USD MILLION)
- TABLE 320 REST OF ASIA PACIFIC: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY APPLICATION AREA, 2025-2030 (USD MILLION)
- TABLE 321 REST OF ASIA PACIFIC: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY DEPLOYMENT MODE, 2019-2024 (USD MILLION)
- TABLE 322 REST OF ASIA PACIFIC: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY DEPLOYMENT MODE, 2025-2030 (USD MILLION)
- TABLE 323 REST OF ASIA PACIFIC: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY ORGANIZATION SIZE, 2019-2024 (USD MILLION)
- TABLE 324 REST OF ASIA PACIFIC: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY ORGANIZATION SIZE, 2025-2030 (USD MILLION)
- TABLE 325 REST OF ASIA PACIFIC: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 326 REST OF ASIA PACIFIC: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 327 MIDDLE EAST & AFRICA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY OFFERING, 2019-2024 (USD MILLION)
- TABLE 328 MIDDLE EAST & AFRICA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY OFFERING, 2025-2030 (USD MILLION)
- TABLE 329 MIDDLE EAST & AFRICA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY HARDWARE SOLUTION, 2019-2024 (USD MILLION)
- TABLE 330 MIDDLE EAST & AFRICA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY HARDWARE SOLUTION, 2025-2030 (USD MILLION)
- TABLE 331 MIDDLE EAST & AFRICA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY SERVICE, 2019-2024 (USD MILLION)
- TABLE 332 MIDDLE EAST & AFRICA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY SERVICE, 2025-2030 (USD MILLION)
- TABLE 333 MIDDLE EAST & AFRICA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY PROFESSIONAL SERVICE, 2019-2024 (USD MILLION)
- TABLE 334 MIDDLE EAST & AFRICA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY PROFESSIONAL SERVICE, 2025-2030 (USD MILLION)
- TABLE 335 MIDDLE EAST & AFRICA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY SOLUTION TYPE, 2019-2024 (USD MILLION)
- TABLE 336 MIDDLE EAST & AFRICA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY SOLUTION TYPE, 2025-2030 (USD MILLION)
- TABLE 337 MIDDLE EAST & AFRICA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY APPLICATION AREA, 2019-2024 (USD MILLION)
- TABLE 338 MIDDLE EAST & AFRICA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY APPLICATION AREA, 2025-2030 (USD MILLION)
- TABLE 339 MIDDLE EAST & AFRICA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY DEPLOYMENT MODE, 2019-2024 (USD MILLION)
- TABLE 340 MIDDLE EAST & AFRICA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY DEPLOYMENT MODE, 2025-2030 (USD MILLION)
- TABLE 341 MIDDLE EAST & AFRICA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY ORGANIZATION SIZE, 2019-2024 (USD MILLION)
- TABLE 342 MIDDLE EAST & AFRICA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY ORGANIZATION SIZE, 2025-2030 (USD MILLION)
- TABLE 343 MIDDLE EAST & AFRICA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 344 MIDDLE EAST & AFRICA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 345 MIDDLE EAST & AFRICA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY COUNTRY, 2019-2024 (USD MILLION)
- TABLE 346 MIDDLE EAST & AFRICA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY COUNTRY, 2025-2030 (USD MILLION)
- TABLE 347 KSA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY OFFERING, 2019-2024 (USD MILLION)
- TABLE 348 KSA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY OFFERING, 2025-2030 (USD MILLION)
- TABLE 349 KSA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY HARDWARE SOLUTION, 2019-2024 (USD MILLION)
- TABLE 350 KSA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY HARDWARE SOLUTION, 2025-2030 (USD MILLION)
- TABLE 351 KSA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY SERVICE, 2019-2024 (USD MILLION)
- TABLE 352 KSA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY SERVICE, 2025-2030 (USD MILLION)
- TABLE 353 KSA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY PROFESSIONAL SERVICE, 2019-2024 (USD MILLION)
- TABLE 354 KSA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY PROFESSIONAL SERVICE, 2025-2030 (USD MILLION)
- TABLE 355 KSA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY SOLUTION TYPE, 2019-2024 (USD MILLION)
- TABLE 356 KSA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY SOLUTION TYPE, 2025-2030 (USD MILLION)
- TABLE 357 KSA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY APPLICATION AREA, 2019-2024 (USD MILLION)
- TABLE 358 KSA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY APPLICATION AREA, 2025-2030 (USD MILLION)
- TABLE 359 KSA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY DEPLOYMENT MODE, 2019-2024 (USD MILLION)
- TABLE 360 KSA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY DEPLOYMENT MODE, 2025-2030 (USD MILLION)
- TABLE 361 KSA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY ORGANIZATION SIZE, 2019-2024 (USD MILLION)
- TABLE 362 KSA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY ORGANIZATION SIZE, 2025-2030 (USD MILLION)
- TABLE 363 KSA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 364 KSA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 365 LATIN AMERICA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY OFFERING, 2019-2024 (USD MILLION)
- TABLE 366 LATIN AMERICA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY OFFERING, 2025-2030 (USD MILLION)
- TABLE 367 LATIN AMERICA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY HARDWARE SOLUTION, 2019-2024 (USD MILLION)
- TABLE 368 LATIN AMERICA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY HARDWARE SOLUTION, 2025-2030 (USD MILLION)
- TABLE 369 LATIN AMERICA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY SERVICE, 2019-2024 (USD MILLION)
- TABLE 370 LATIN AMERICA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY SERVICE, 2025-2030 (USD MILLION)
- TABLE 371 LATIN AMERICA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY PROFESSIONAL SERVICE, 2019-2024 (USD MILLION)
- TABLE 372 LATIN AMERICA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY PROFESSIONAL SERVICE, 2025-2030 (USD MILLION)
- TABLE 373 LATIN AMERICA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY SOLUTION TYPE, 2019-2024 (USD MILLION)
- TABLE 374 LATIN AMERICA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY SOLUTION TYPE, 2025-2030 (USD MILLION)
- TABLE 375 LATIN AMERICA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY APPLICATION AREA, 2019-2024 (USD MILLION)
- TABLE 376 LATIN AMERICA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY APPLICATION AREA, 2025-2030 (USD MILLION)
- TABLE 377 LATIN AMERICA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY DEPLOYMENT MODE, 2019-2024 (USD MILLION)
- TABLE 378 LATIN AMERICA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY DEPLOYMENT MODE, 2025-2030 (USD MILLION)
- TABLE 379 LATIN AMERICA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY ORGANIZATION SIZE, 2019-2024 (USD MILLION)
- TABLE 380 LATIN AMERICA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY ORGANIZATION SIZE, 2025-2030 (USD MILLION)
- TABLE 381 LATIN AMERICA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 382 LATIN AMERICA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 383 LATIN AMERICA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY COUNTRY, 2019-2024 (USD MILLION)
- TABLE 384 LATIN AMERICA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY COUNTRY, 2025-2030 (USD MILLION)
- TABLE 385 BRAZIL: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY OFFERING, 2019-2024 (USD MILLION)
- TABLE 386 BRAZIL: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY OFFERING, 2025-2030 (USD MILLION)
- TABLE 387 BRAZIL: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY HARDWARE SOLUTION, 2019-2024 (USD MILLION)
- TABLE 388 BRAZIL: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY HARDWARE SOLUTION, 2025-2030 (USD MILLION)
- TABLE 389 BRAZIL: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY SERVICE, 2019-2024 (USD MILLION)
- TABLE 390 BRAZIL: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY SERVICE, 2025-2030 (USD MILLION)
- TABLE 391 BRAZIL: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY PROFESSIONAL SERVICE, 2019-2024 (USD MILLION)
- TABLE 392 BRAZIL: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY PROFESSIONAL SERVICE, 2025-2030 (USD MILLION)
- TABLE 393 BRAZIL: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY SOLUTION TYPE, 2019-2024 (USD MILLION)
- TABLE 394 BRAZIL: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY SOLUTION TYPE, 2025-2030 (USD MILLION)
- TABLE 395 BRAZIL: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY APPLICATION AREA, 2019-2024 (USD MILLION)
- TABLE 396 BRAZIL: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY APPLICATION AREA, 2025-2030 (USD MILLION)
- TABLE 397 BRAZIL: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY DEPLOYMENT MODE, 2019-2024 (USD MILLION)
- TABLE 398 BRAZIL: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY DEPLOYMENT MODE, 2025-2030 (USD MILLION)
- TABLE 399 BRAZIL: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY ORGANIZATION SIZE, 2019-2024 (USD MILLION)
- TABLE 400 BRAZIL: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY ORGANIZATION SIZE, 2025-2030 (USD MILLION)
- TABLE 401 BRAZIL: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 402 BRAZIL: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 403 MEXICO: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY OFFERING, 2019-2024 (USD MILLION)
- TABLE 404 MEXICO: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY OFFERING, 2025-2030 (USD MILLION)
- TABLE 405 MEXICO: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY HARDWARE SOLUTION, 2019-2024 (USD MILLION)
- TABLE 406 MEXICO: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY HARDWARE SOLUTION, 2025-2030 (USD MILLION)
- TABLE 407 MEXICO: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY SERVICE, 2019-2024 (USD MILLION)
- TABLE 408 MEXICO: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY SERVICE, 2025-2030 (USD MILLION)
- TABLE 409 MEXICO: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY PROFESSIONAL SERVICE, 2019-2024 (USD MILLION)
- TABLE 410 MEXICO: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY PROFESSIONAL SERVICE, 2025-2030 (USD MILLION)
- TABLE 411 MEXICO: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY SOLUTION TYPE, 2019-2024 (USD MILLION)
- TABLE 412 MEXICO: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY SOLUTION TYPE, 2025-2030 (USD MILLION)
- TABLE 413 MEXICO: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY APPLICATION AREA, 2019-2024 (USD MILLION)
- TABLE 414 MEXICO: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY APPLICATION AREA, 2025-2030 (USD MILLION)
- TABLE 415 MEXICO: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY DEPLOYMENT MODE, 2019-2024 (USD MILLION)
- TABLE 416 MEXICO: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY DEPLOYMENT MODE, 2025-2030 (USD MILLION)
- TABLE 417 MEXICO: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY ORGANIZATION SIZE, 2019-2024 (USD MILLION)
- TABLE 418 MEXICO: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY ORGANIZATION SIZE, 2025-2030 (USD MILLION)
- TABLE 419 MEXICO: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 420 MEXICO: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 421 REST OF LATIN AMERICA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY OFFERING, 2019-2024 (USD MILLION)
- TABLE 422 REST OF LATIN AMERICA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY OFFERING, 2025-2030 (USD MILLION)
- TABLE 423 REST OF LATIN AMERICA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY HARDWARE SOLUTION, 2019-2024 (USD MILLION)
- TABLE 424 REST OF LATIN AMERICA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY HARDWARE SOLUTION, 2025-2030 (USD MILLION)
- TABLE 425 REST OF LATIN AMERICA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY SERVICE, 2019-2024 (USD MILLION)
- TABLE 426 REST OF LATIN AMERICA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY SERVICE, 2025-2030 (USD MILLION)
- TABLE 427 REST OF LATIN AMERICA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY PROFESSIONAL SERVICE, 2019-2024 (USD MILLION)
- TABLE 428 REST OF LATIN AMERICA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY PROFESSIONAL SERVICE, 2025-2030 (USD MILLION)
- TABLE 429 REST OF LATIN AMERICA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY SOLUTION TYPE, 2019-2024 (USD MILLION)
- TABLE 430 REST OF LATIN AMERICA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY SOLUTION TYPE, 2025-2030 (USD MILLION)
- TABLE 431 REST OF LATIN AMERICA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY APPLICATION AREA, 2019-2024 (USD MILLION)
- TABLE 432 REST OF LATIN AMERICA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY APPLICATION AREA, 2025-2030 (USD MILLION)
- TABLE 433 REST OF LATIN AMERICA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY DEPLOYMENT MODE, 2019-2024 (USD MILLION)
- TABLE 434 REST OF LATIN AMERICA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY DEPLOYMENT MODE, 2025-2030 (USD MILLION)
- TABLE 435 REST OF LATIN AMERICA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY ORGANIZATION SIZE, 2019-2024 (USD MILLION)
- TABLE 436 REST OF LATIN AMERICA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY ORGANIZATION SIZE, 2025-2030 (USD MILLION)
- TABLE 437 REST OF LATIN AMERICA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 438 REST OF LATIN AMERICA: DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 439 DDOS PROTECTION AND MITIGATION SECURITY MARKET: OVERVIEW OF STRATEGIES DEPLOYED BY KEY PLAYERS
- TABLE 440 DDOS PROTECTION AND MITIGATION SECURITY MARKET: DEGREE OF COMPETITION, 2024
- TABLE 441 DDOS PROTECTION AND MITIGATION SECURITY MARKET: REGIONAL FOOTPRINT, 2024
- TABLE 442 DDOS PROTECTION AND MITIGATION SECURITY MARKET: OFFERING FOOTPRINT, 2024
- TABLE 443 DDOS PROTECTION AND MITIGATION SECURITY MARKET: VERTICAL FOOTPRINT, 2024
- TABLE 444 DDOS PROTECTION AND MITIGATION SECURITY MARKET: KEY STARTUPS/SMES, 2024
- TABLE 445 DDOS PROTECTION AND MITIGATION SECURITY MARKET: COMPETITIVE BENCHMARKING OF KEY STARTUPS/SMES, 2024
- TABLE 446 DDOS PROTECTION AND MITIGATION SECURITY MARKET: PRODUCT LAUNCHES AND ENHANCEMENTS, APRIL 2023-AUGUST 2025
- TABLE 447 DDOS PROTECTION AND MITIGATION SECURITY MARKET: DEALS, FEBRUARY 2022-MAY 2024
- TABLE 448 NETSCOUT: COMPANY OVERVIEW
- TABLE 449 NETSCOUT: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 450 NETSCOUT: PRODUCT LAUNCHES & ENHANCEMENTS
- TABLE 451 NETSCOUT: DEALS
- TABLE 452 NETSCOUT: EXPANSIONS
- TABLE 453 AKAMAI TECHNOLOGIES: COMPANY OVERVIEW
- TABLE 454 AKAMAI TECHNOLOGIES: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 455 AKAMAI TECHNOLOGIES: PRODUCT LAUNCHES & ENHANCEMENTS
- TABLE 456 AKAMAI TECHNOLOGIES: DEALS
- TABLE 457 AKAMAI TECHNOLOGIES: EXPANSIONS
- TABLE 458 RADWARE: COMPANY OVERVIEW
- TABLE 459 RADWARE: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 460 RADWARE: PRODUCT LAUNCHES & ENHANCEMENTS
- TABLE 461 RADWARE: DEALS
- TABLE 462 CLOUDFLARE: COMPANY OVERVIEW
- TABLE 463 CLOUDFLARE: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 464 FORTINET: COMPANY OVERVIEW
- TABLE 465 FORTINET: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 466 FORTINET: DEALS
- TABLE 467 HUAWEI: COMPANY OVERVIEW
- TABLE 468 HUAWEI: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 469 HUAWEI: DEALS
- TABLE 470 LINK11: COMPANY OVERVIEW
- TABLE 471 LINK11: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 472 LINK11: PRODUCT LAUNCHES & ENHANCEMENTS
- TABLE 473 LINK11: DEALS
- TABLE 474 IMPERVA: COMPANY OVERVIEW
- TABLE 475 IMPERVA: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 476 IMPERVA: DEALS
- TABLE 477 BT: COMPANY OVERVIEW
- TABLE 478 BT: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 479 BT: DEALS
- TABLE 480 A10 NETWORKS: COMPANY OVERVIEW
- TABLE 481 A10 NETWORKS: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 482 PRIMARY INTERVIEWS WITH EXPERTS
- TABLE 483 RISK ASSESSMENT
- TABLE 484 CYBERSECURITY MARKET, BY OFFERING, 2019-2024 (USD MILLION)
- TABLE 485 CYBERSECURITY MARKET, BY OFFERING, 2025-2030 (USD MILLION)
- TABLE 486 CYBERSECURITY MARKET, BY SOLUTION TYPE, 2019-2024 (USD MILLION)
- TABLE 487 CYBERSECURITY MARKET, BY SOLUTION TYPE, 2025-2030 (USD MILLION)
- TABLE 488 CYBERSECURITY MARKET, BY SECURITY TYPE, 2019-2024 (USD MILLION)
- TABLE 489 CYBERSECURITY MARKET, BY SECURITY TYPE, 2025-2030 (USD MILLION)
- TABLE 490 CYBERSECURITY MARKET, BY DEPLOYMENT MODE, 2019-2024 (USD MILLION)
- TABLE 491 CYBERSECURITY MARKET, BY DEPLOYMENT MODE, 2025-2030 (USD MILLION)
- TABLE 492 CYBERSECURITY MARKET, BY ORGANIZATION SIZE, 2019-2024 (USD MILLION)
- TABLE 493 CYBERSECURITY MARKET, BY ORGANIZATION SIZE, 2025-2030 (USD MILLION)
- TABLE 494 CYBERSECURITY MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 495 CYBERSECURITY MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 496 CYBERSECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 497 CYBERSECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 498 SECURITY AS A SERVICE MARKET SIZE, BY COMPONENT, 2016-2020 (USD MILLION)
- TABLE 499 SECURITY AS A SERVICE MARKET SIZE, BY COMPONENT, 2021-2026 (USD MILLION)
- TABLE 500 SECURITY AS A SERVICE MARKET SIZE, BY SOLUTION, 2016-2020 (USD MILLION)
- TABLE 501 SECURITY AS A SERVICE MARKET SIZE, BY SOLUTION, 2021-2026 (USD MILLION)
- TABLE 502 SECURITY AS A SERVICE MARKET SIZE, BY SERVICE, 2016-2020 (USD MILLION)
- TABLE 503 SECURITY AS A SERVICE MARKET SIZE, BY SERVICE, 2021-2026 (USD MILLION)
- TABLE 504 SECURITY AS A SERVICE MARKET SIZE, BY APPLICATION, 2016-2020 (USD MILLION)
- TABLE 505 SECURITY AS A SERVICE MARKET SIZE, BY APPLICATION, 2021-2026 (USD MILLION)
- TABLE 506 SECURITY AS A SERVICE MARKET SIZE, BY ORGANIZATION SIZE, 2016-2020 (USD MILLION)
- TABLE 507 SECURITY AS A SERVICE MARKET SIZE, BY ORGANIZATION SIZE, 2021-2026 (USD MILLION)
- TABLE 508 SECURITY AS A SERVICE MARKET SIZE, BY VERTICAL, 2016-2020 (USD MILLION)
- TABLE 509 SECURITY AS A SERVICE MARKET SIZE, BY VERTICAL, 2021-2026 (USD MILLION)
- TABLE 510 SECURITY AS A SERVICE MARKET SIZE, BY REGION, 2016-2020 (USD MILLION)
- TABLE 511 SECURITY AS A SERVICE MARKET SIZE, BY REGION, 2021-2026 (USD MILLION)
List of Figures
- FIGURE 1 MARKET SEGMENTATION AND REGIONS COVERED
- FIGURE 2 STUDY YEARS CONSIDERED
- FIGURE 3 MARKET SCENARIO
- FIGURE 4 GLOBAL DDOS PROTECTION & MITIGATION SECURITY MARKET, 2025-2030 (USD MILLION)
- FIGURE 5 MAJOR STRATEGIES ADOPTED BY KEY PLAYERS IN DDOS PROTECTION & MITIGATION SECURITY MARKET, 2025
- FIGURE 6 DISRUPTIVE TRENDS INFLUENCING GROWTH OF DDOS PROTECTION & MITIGATION SECURITY MARKET
- FIGURE 7 HIGH-GROWTH SEGMENTS IN DDOS PROTECTION & MITIGATION SECURITY MARKET, 2025
- FIGURE 8 ASIA PACIFIC TO REGISTER HIGHEST GROWTH DURING FORECAST PERIOD
- FIGURE 9 RISING ADOPTION OF AI-DRIVEN CLOUD SECURITY SOLUTIONS ACTS AS OPPORTUNITY IN DDOS PROTECTION & MITIGATION SECURITY MARKET
- FIGURE 10 HARDWARE AND LARGE ENTERPRISES ACCOUNTED FOR LARGEST MARKET SHARE IN 2025
- FIGURE 11 APPLICATION SECURITY SEGMENT SET TO DOMINATE DDOS PROTECTION & MITIGATION SECURITY MARKET IN 2025
- FIGURE 12 BFSI VERTICAL TO ACCOUNT FOR LARGEST MARKET SHARE IN 2025
- FIGURE 13 DDOS PROTECTION AND MITIGATION SECURITY MARKET: DRIVERS, RESTRAINTS, OPPORTUNITIES, AND CHALLENGES
- FIGURE 14 DDOS PROTECTION AND MITIGATION SECURITY MARKET: PORTER'S FIVE FORCES ANALYSIS
- FIGURE 15 SUPPLY CHAIN ANALYSIS
- FIGURE 16 DDOS PROTECTION AND MITIGATION SECURITY MARKET: ECOSYSTEM ANALYSIS
- FIGURE 17 AVERAGE SELLING PRICE OF KEY PLAYERS, BY OFFERING, 2024 (USD)
- FIGURE 18 TRENDS/DISRUPTIONS IMPACTING CUSTOMER BUSINESS
- FIGURE 19 INVESTMENT AND FUNDING SCENARIO, 2019-2024
- FIGURE 20 LIST OF PATENTS APPLIED AND GRANTED, 2015-2024
- FIGURE 21 USE CASES OF GENERATIVE AI IN DDOS PROTECTION & MITIGATION SECURITY
- FIGURE 22 GENERATIVE AI BEST PRACTICES ACROSS MAJOR INDUSTRIES
- FIGURE 23 INFLUENCE OF STAKEHOLDERS ON BUYING PROCESS FOR TOP THREE VERTICALS
- FIGURE 24 KEY BUYING CRITERIA FOR TOP THREE VERTICALS
- FIGURE 25 SERVICES SEGMENT TO WITNESS HIGHEST CAGR DURING FORECAST PERIOD
- FIGURE 26 MANAGED SERVICES SEGMENT TO RECORD HIGHER CAGR DURING FORECAST PERIOD
- FIGURE 27 CONSULTING & ADVISORY SEGMENT TO RECORD HIGHEST GROWTH RATE DURING FORECAST PERIOD
- FIGURE 28 BOTNET DETECTION & MITIGATION SEGMENT TO RECORD HIGHEST GROWTH RATE DURING FORECAST PERIOD
- FIGURE 29 APPLICATION SECURITY SEGMENT TO WITNESS HIGHEST CAGR DURING FORECAST PERIOD
- FIGURE 30 CLOUD SEGMENT TO RECORD FASTER GROWTH DURING FORECAST PERIOD
- FIGURE 31 SMES SEGMENT TO RECORD HIGHER CAGR DURING FORECAST PERIOD
- FIGURE 32 BFSI SEGMENT TO RECORD HIGHEST GROWTH RATE DURING FORECAST PERIOD
- FIGURE 33 NORTH AMERICA TO LEAD MARKET FROM 2025 TO 2030
- FIGURE 34 ASIA PACIFIC TO REGISTER HIGHEST CAGR DURING FORECAST PERIOD
- FIGURE 35 NORTH AMERICA: DDOS PROTECTION AND MITIGATION SECURITY MARKET SNAPSHOT
- FIGURE 36 ASIA PACIFIC: DDOS PROTECTION AND MITIGATION SECURITY MARKET SNAPSHOT
- FIGURE 37 DDOS PROTECTION AND MITIGATION SECURITY MARKET: REVENUE ANALYSIS OF FIVE KEY PLAYERS, 2020-2024
- FIGURE 38 SHARE ANALYSIS OF LEADING COMPANIES IN DDOS PROTECTION AND MITIGATION SECURITY MARKET, 2024
- FIGURE 39 MARKET RANKING ANALYSIS OF TOP FIVE PLAYERS
- FIGURE 40 DDOS PROTECTION AND MITIGATION SECURITY MARKET: COMPANY EVALUATION MATRIX (KEY PLAYERS), 2024
- FIGURE 41 DDOS PROTECTION AND MITIGATION SECURITY MARKET: COMPANY FOOTPRINT, 2024
- FIGURE 42 DDOS PROTECTION AND MITIGATION SECURITY MARKET: COMPANY EVALUATION MATRIX (STARTUPS/SMES), 2024
- FIGURE 43 BRAND/PRODUCT COMPARISON
- FIGURE 44 COMPANY VALUATION, 2025 (USD BILLION)
- FIGURE 45 FINANCIAL METRICS, 2025
- FIGURE 46 NETSCOUT: COMPANY SNAPSHOT
- FIGURE 47 AKAMAI TECHNOLOGIES: COMPANY SNAPSHOT
- FIGURE 48 RADWARE: COMPANY SNAPSHOT
- FIGURE 49 CLOUDFLARE: COMPANY SNAPSHOT
- FIGURE 50 FORTINET: COMPANY SNAPSHOT
- FIGURE 51 HUAWEI: COMPANY SNAPSHOT
- FIGURE 52 BT: COMPANY SNAPSHOT
- FIGURE 53 A10 NETWORKS: COMPANY SNAPSHOT
- FIGURE 54 DDOS PROTECTION AND MITIGATION SECURITY MARKET: RESEARCH DESIGN
- FIGURE 55 BREAKDOWN OF PRIMARY INTERVIEWS, BY COMPANY TYPE, DESIGNATION, AND REGION
- FIGURE 56 KEY INSIGHTS FROM INDUSTRY EXPERTS
- FIGURE 57 DDOS PROTECTION AND MITIGATION SECURITY MARKET: TOP-DOWN AND BOTTOM-UP APPROACHES
- FIGURE 58 APPROACH 1 (SUPPLY SIDE): REVENUE OF VENDORS IN DDOS PROTECTION AND MITIGATION SECURITY MARKET
- FIGURE 59 APPROACH 2 (DEMAND SIDE): DDOS PROTECTION AND MITIGATION SECURITY MARKET
- FIGURE 60 MARKET SIZE ESTIMATION METHODOLOGY: DEMAND-SIDE ANALYSIS
- FIGURE 61 TECHNOLOGY/PRODUCT ROADMAP
- FIGURE 62 DDOS PROTECTION AND MITIGATION SECURITY MARKET: DATA TRIANGULATION











