 |
市场调查报告书
商品编码
1403753
云端安全软体:市场占有率分析、产业趋势/统计、2024-2029 年成长预测Cloud Security Software - Market Share Analysis, Industry Trends & Statistics, Growth Forecasts 2024 - 2029 |
||||||
※ 本网页内容可能与最新版本有所差异。详细情况请与我们联繫。
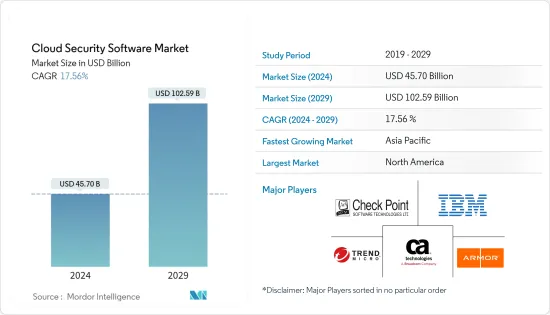
云端安全软体市场规模预计到 2024 年为 457 亿美元,预计到 2029 年将达到 1,025.9 亿美元,在预测期内(2024-2029 年)复合年增长率为 17.56%。
主要亮点
- 随着资料产生的增加和技术变得更加复杂,企业越来越依赖云端服务进行营运和资料管理。云端服务的日益普及直接影响了对云端安全解决方案的需求。
- 云端技术和云端基础的资源可以帮助缓解致命网路安全威胁的增加。云端安全需要一组对于应用程式、基础架构和资料的安全性至关重要的策略和控制。云端处理平台上经常发生资料遗失、外洩和不安全的应用程式介面 (API) 等威胁。网路环境和相关技术的发展为新威胁铺平了道路。网路攻击具有高度标靶化、持久性和技术复杂性。
- BFSI 产业是关键基础设施领域之一,由于庞大的客户群和财务资讯受到威胁,因此面临多次资料外洩和网路攻击。网路犯罪分子正在大量利用有害的网路攻击来削弱金融业,因为这是一个风险相对较低、易于检测的行业,并且是一个利润丰厚的商业模式。Masu。这些攻击威胁包括特洛伊木马、恶意软体、ATM 恶意软体、勒索软体、手机银行恶意软体、资料外洩、组织渗透、资料窃取和财务外洩。
- 提供安全解决方案的供应商正在积极与其他託管安全服务提供者合作。例如,2022 年 10 月,Google云端宣布对其可信任云端生态系统进行重大扩展。与 20 多个合作伙伴的新整合专注于实现更好的资料主权管理、支援零信任模型、统一身分管理以及提高世界和企业的端点安全性。我们强调这项服务。
- 然而,与遗留基础设施的各种复杂整合等因素可能会限制预测期内的整体市场成长。
- 由于COVID-19的爆发,云端安全市场大幅成长。云端基础的服务和工具在后 COVID-19 时期出现了显着增长,因为公司越来越多地在各国封锁期间引入远端工作访问,预计会出现增长。疫情期间云端基础服务的使用增加,迫使数百万人在不熟悉且不太安全的环境中工作,从而成为网路攻击的热点。因此,云端安全解决方案在此次疫情期间发挥了至关重要的作用,并且预计将继续激增。
云端安全软体市场趋势
医疗保健领域将显着成长
- 医疗保健组织正变得越来越分散,远距临床办公室、临床实验、復健设施、外包和异地工作人员,每个办公室和个人都透过各种设备存取应用程式和资源。它应该是唯一的且无缝可访问的。医疗保健组织正在认识到云端技术提供的优势,包括弹性、扩充性以及可用性。
- 随着医疗保健的进步,例如电子健康记录和其他患者详细资讯在每家医院进行登记,潜在的资料漏洞正在增加,使得实施网路安全成为首要任务。我是。
- 透过利用人工智慧、资料主导的安全监控和行为分析,云端基础的安全变得更加有效。例如,微软的统一智慧型安全图每天收集数十亿个资料点,并使用机器学习和人工智慧来分析和识别不断发展的网路安全攻击。
- 2022 年 4 月,美国食品药物管理局发布了医疗设备网路安全指南草案「医疗设备网路安全、上市前应用内容和品质系统注意事项」。该指南草案强调在整个产品生命週期中保护医疗设备。这些建议可实现高效的上市前审查流程,并有助于确保所售医疗设备能够充分抵御网路安全威胁。
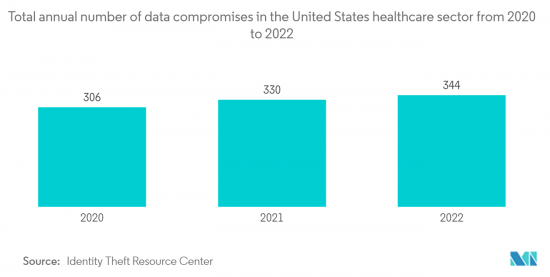
- 根据《2023 年 5 月医疗保健资料外泄报告》,该月大部分资料外泄都是骇客 IT 事件,其中许多是勒索软体攻击、资料窃取和勒索企图。本月约 81.33% 的资料外洩是骇客和 IT 事件,这些事件约占所有外洩记录的 99.54%。这些事件导致约 18,956,101 人受保护的健康资讯外洩或被盗。资料外洩的平均规模为 310,756 起,中位数为 3,833 起。
亚太地区将经历最高的成长
- 在亚太地区,各种物联网设备的使用不断增加,数位转型的范围和速度不断扩大,使得目前的网路基础设施广泛遭受网路攻击。近年来,社群媒体、网路和行动用户均迅速成长,为该地区网路安全的强劲成长做出了贡献。预计这将在预测期内推动该地区的市场成长机会。
- 此外,该地区各国政府正在製定新的网路安全法,以减少网路钓鱼、恶意软体和其他网路安全威胁的影响。例如,韩国资讯通信技术部宣布计划在 2023 年投资 6,700 亿韩元(6.07 亿美元),以加强该国的网路安全能力,以应对日益增多的新数位威胁。该国计划透过与主要云端和资料中心公司合作并即时收集威胁资讯来开发能够快速响应网路安全威胁的基础设施。
- 近期,印度电网多次遭到中国袭击。 2022年4月,印度电力部门在长期操作中遭到骇客攻击。该组织主要依赖 Shadowpad,这是一种据说是由中国国家安全部承包开发的特洛伊木马。
- 此外,由于技术进步,中国的连网设备数量正在增加。它是全球重要的物联网(IoT)市场。此外,5G 和支援 5G 的设备将显着提高设备互连性。因此,连接设备的整体适应性增加,这直接增加了市场对安全产品的需求。此外,网站可能更容易被第三方操纵或欺骗,与网站通讯的使用者的敏感资料可能更容易被外国情报机构拦截。
- 2023年7月,专注于云端运算和网路安全的IT基础设施解决方案供应商深信服科技与泰国云端安全和网路安全保全服务供应商Cloudsec Asia宣布建立策略合作伙伴关係,提供全面的託管服务。深信服科技与Cloudsec Asia之间的合作旨在满足企业组织对有效网路威胁管理日益增长的需求。利用两家公司的专业知识将有助于组织主动减轻和侦测网路威胁,同时克服网路安全管理相关的时间限制、资源有限和技术复杂性等挑战。我们提供託管服务
云端安全软体产业概况
由于多年来网路攻击的增加,云端安全软体市场已经变得碎片化。企业越来越意识到并专注于储存在云端中的资料。因此,提供了 NortonLifeLock (Broadcom Inc.)、CA Technologies (Broadcom Inc.)、Microsoft Corporation、Armor Defense Inc. 等的产品。
2023 年 4 月,Uptycs 提供了审核整合 CNAPP ,我们宣布了一个有时可以澄清可疑行为的功能。结果是一个“警报系统”,允许安全团队在威胁行为者访问云皇冠上的宝石:资料和服务之前识别并阻止他们。
其他福利:
- Excel 格式的市场预测 (ME) 表
- 3 个月的分析师支持
目录
第一章简介
- 研究前提和结果
- 调查范围
第二章调查方法
第三章执行摘要
第四章市场动态
- 市场概况
- 产业吸引力-波特五力分析
- 供应商的议价能力
- 买家/消费者的议价能力
- 新进入者的威胁
- 替代品的威胁
- 竞争公司之间敌对关係的强度
- 评估 COVID-19 的行业影响和復苏
第五章市场动态
- 市场驱动因素
- 实践数位转型
- 透过行动和其他设备扩大数位服务的使用
- 市场挑战
- 与遗留基础设施的复杂集成
- 网路安全相关实践的关键创新与进展分析
- 主要行业标准和框架
- 主要使用案例
第六章市场区隔
- 透过软体
- 云端身分管理
- 网路/电子邮件安全
- SIEM
- CASB
- 漏洞/风险管理
- 其他软体
- 按组织规模
- 中小企业
- 大公司
- 按最终用户
- 资讯科技与电信
- BFSI
- 零售/消费品
- 卫生保健
- 製造业
- 政府机关
- 其他最终用户
- 按地区
- 北美洲
- 美国
- 加拿大
- 欧洲
- 双子座
- 英国
- 法国
- 其他欧洲国家
- 亚太地区
- 印度
- 中国
- 日本
- 其他亚太地区
- 拉丁美洲
- 中东/非洲
- 北美洲
第七章竞争形势
- 公司简介
- IBM Corporation
- Symantec(Broadcom)
- Palo Alto Networks
- Cisco
- McAfee
- HPE
- Checkpoint
- Zscaler
- Fortinet
- Sophos
第八章投资分析
第九章 市场机会及未来趋势

The Cloud Security Software Market size is estimated at USD 45.70 billion in 2024, and is expected to reach USD 102.59 billion by 2029, growing at a CAGR of 17.56% during the forecast period (2024-2029).
Key Highlights
- The growing data generation and increasing complexity of technologies have resulted in a heavy dependence of organizations on cloud services for operations and data management. This growth in the adoption of cloud services directly impacts the demand for cloud security solutions.
- Cloud technology and cloud-based resources help mitigate the rise in lethal cyber-security threats. Cloud security requires a set of policies and controls vital for the security of applications, infrastructure, and data. Threats, such as data loss, breaches, and insecure application programming interfaces (API), are frequent on the cloud computing platform. The evolution of the cyber environment and related technologies paved the way for new threats. Cyber-attacks are highly targeted, persistent, and technologically advanced.
- The BFSI industry is one of the critical infrastructure segments that face multiple data breaches and cyber-attacks, owing to the massive customer base that the sector serves and the financial information that is at stake. Cybercriminals are leveraging an abundance of harmful cyberattacks to immobilize the financial industry since it is a highly lucrative operating model with the added benefit of relatively low risk and detectability. These attacks' threat landscape ranges from Trojans, malware, ATM malware, ransomware, mobile banking malware, data breaches, institutional invasion, data thefts, fiscal breaches, etc.
- Vendors offering security solutions are actively involved in collaborating with other managed security service providers. For instance, in October 2022, Google Cloud declared a significant extension of its trusted cloud ecosystem. It highlighted new integrations and offerings with more than twenty partners focused on enabling more excellent data sovereignty controls, assisting Zero Trust models, unifying identity management, and improvising endpoint security for global businesses.
- However, factors like integrating various complexities with legacy infrastructure could limit the market's overall growth throughout the forecast period.
- Due to the outbreak of COVID-19, the cloud security market grew significantly. It was expected to witness massive growth during the post-COVID-19 period as cloud-based services and tools were increasingly adapted due to organizations deploying remote work access amid lockdowns in different countries. The rise in the usage of cloud-based services during this pandemic became a hotspot for cyberattacks as millions worked in unfamiliar, less secure circumstances. Thus, a cloud security solution played a vital role during this pandemic and is expected to witness a surge.
Cloud Security Software Market Trends
Healthcare Sector to Witness the Significant Growth
- Healthcare organizations have become more distributed, owing to remote clinical offices, trial sites, rehab facilities, outsourcing, and off-site workers, leading each office and individual to require unique yet seamless access to applications and resources via various devices. Healthcare organizations recognize the benefits provided by cloud technology, such as greater flexibility, scalability, and availability of systems and applications.
- With advancements in healthcare, such as electronic medical records and other patient details being registered with the respective hospitals, the potential vulnerability for the data has been increasing, owing to which the implementation of network security has been of primary importance.
- Using AI, data-driven security monitoring, and behavioral analytics makes cloud-based security more effective. For instance, Microsoft's integrated intelligent security graph collects billions of data points daily and uses machine learning and AI to analyze and identify evolving cybersecurity attacks.
- In April 2022, the U.S. Food and Drug Administration published a draft guidance, Cybersecurity in Medical Devices, Content of Premarket Submissions and Quality System Considerations, regarding medical device cybersecurity. The draft guidance emphasizes safeguarding medical devices throughout a product's life cycle. These recommendations can enable an efficient premarket review process and help assure that marketed medical devices are sufficiently resilient to cybersecurity threats.
- According to May 2023 Healthcare Data Breach Report, most of the month's data breaches were hacking IT incidents, many of which were ransomware attacks and data theft or extortion attempts. Around 81.33% of the month's data breaches were hacking, and IT incidents, and those incidents accounted for approximately 99.54% of all breached records. The protected health information of about 18,956,101 individuals was exposed or stolen in those incidents. The average data breach size was 310,756 records, and the median breach size was 3,833.

The Asia-Pacific to Witness the Highest Growth
- Due to the rise in the usage of various IoT devices and the increasing scope and speed of digital transformation in the Asia-Pacific region, the current network infrastructure is becoming widely exposed to cyberattacks. Social media, internet, and mobile users have all seen a drastic rise in recent years, contributing to the region's strong growth in cybersecurity. This is expected to fuel the market growth opportunity within the region throughout the forecast period.
- Moreover, the region's various governments are imposing new cybersecurity laws to reduce the impact of cyber phishing, malware, and other cybersecurity threats. For instance, South Korea's ICT ministry announced the plan to spend KRW 670 billion (USD 607 million) by 2023 to bolster the country's cybersecurity capabilities to respond to growing new digital threats. The country plans to develop infrastructure to quickly respond to cybersecurity threats by collaborating with major cloud and data center companies to collect threat information in real time, compared to the current system that relies on individual reports.
- Recently, there have been multiple attacks on Indian power grids by China. In April 2022, India's power sector was targeted by hackers in a long-term operation. The group primarily utilized the trojan ShadowPad, which is believed to have been developed by the contractors for China's Ministry of State Security.
- Also, due to the rise in technological advancements, there is an increase in the number of connected devices in China. It is a significant Internet of Things (IoT) market globally. Furthermore, 5G and 5G-enabled devices exponentially increase the devices' interconnectivity. As a result, it increases the overall adaptability of the connected devices, thereby directly augmenting the need for security products in the market. Moreover, the websites are thereby prone to be manipulated and impersonated by third parties, and sensitive user data communicated with the website can be intercepted more easily by foreign intelligence agencies.
- In July 2023, Sangfor Technologies Co., Ltd., a provider of IT infrastructure solutions specializing in Cloud Computing & Network Security, and Cloudsec Asia Co., Ltd., a provider of cloud security and cyber security services in Thailand, formed a strategic partnership primarily to deliver comprehensive managed services for cyber threat detection. The collaboration between Sangfor Technologies and Cloudsec Asia targets to address the rising demand for effective cyber threat management within business organizations. By leveraging their expertise, the companies would deliver a managed service that empowers organizations to proactively mitigate and detect cyber threats while overcoming challenges like time constraints, limited resources, and technological complexities associated with cybersecurity management.
Cloud Security Software Industry Overview
The market for cloud security software is fragmented due to the rise in cyber-attacks over the years. Enterprises have become more aware and careful regarding their data stored in the cloud. Thus, they offer offerings from NortonLifeLock Inc. (Broadcom Inc.), CA Technologies (Broadcom Inc.), Microsoft Corporation, Armor Defense Inc., etc.
In April 2023, Uptycs, the provider of the first unified CNAPP and XDR platform, declared the ability to collect and analyze GitHub audit logs and user identity information from Okta and Azure Active Directory to reveal suspicious behavior as the developer moves code in and out of repositories and into production. The result is an "early warning system" that enables the security teams to identify and stop threat actors before they can access the cloud's crown jewel data and services.
Additional Benefits:
- The market estimate (ME) sheet in Excel format
- 3 months of analyst support
TABLE OF CONTENTS
1 INTRODUCTION
- 1.1 Study Assumptions & Deliverables
- 1.2 Scope of the Study
2 RESEARCH METHODOLOGY
3 EXECUTIVE SUMMARY
4 MARKET DYNAMICS
- 4.1 Market Overview
- 4.2 Industry Attractiveness - Porter's Five Forces Analysis
- 4.2.1 Bargaining Power of Suppliers
- 4.2.2 Bargaining Power of Buyers/Consumers
- 4.2.3 Threat of New Entrants
- 4.2.4 Threat of Substitutes
- 4.2.5 Intensity of Competitive Rivalry
- 4.3 An Assessment of the Impact and Recovery from COVID-19 on the Industry
5 MARKET DYNAMICS
- 5.1 Market Drivers
- 5.1.1 Adoption of Digital Transformation Practices
- 5.1.2 Growing Use of Digital Services Through Mobile and Other Devices
- 5.2 Market Challenges
- 5.2.1 Integration Complexities with Legacy Infrastructure
- 5.3 Analysis of Key Innovations and Advancements in Cybersecurity Related Practices
- 5.4 Key Industry Standards & Frameworks
- 5.5 Key Use Cases
6 MARKET SEGMENTATION
- 6.1 By Software
- 6.1.1 Cloud IAM
- 6.1.2 Web and Email Security
- 6.1.3 SIEM
- 6.1.4 CASB
- 6.1.5 Vulnerability and Risk Management
- 6.1.6 Other Software
- 6.2 By Organization Size
- 6.2.1 SME
- 6.2.2 Large Enterprises
- 6.3 By End User
- 6.3.1 IT & Telecom
- 6.3.2 BFSI
- 6.3.3 Retail & Consumer Goods
- 6.3.4 Healthcare
- 6.3.5 Manufacturing
- 6.3.6 Government
- 6.3.7 Other end-users
- 6.4 Geography
- 6.4.1 North America
- 6.4.1.1 United States
- 6.4.1.2 Canada
- 6.4.2 Europe
- 6.4.2.1 Gemany
- 6.4.2.2 United Kingdom
- 6.4.2.3 France
- 6.4.2.4 Rest of Europe
- 6.4.3 Asia-Pacific
- 6.4.3.1 India
- 6.4.3.2 China
- 6.4.3.3 Japan
- 6.4.3.4 Rest of Asia-Pacific
- 6.4.4 Latin America
- 6.4.5 Middle East and Africa
- 6.4.1 North America
7 COMPETITIVE LANDSCAPE
- 7.1 Company Profiles
- 7.1.1 IBM Corporation
- 7.1.2 Symantec (Broadcom)
- 7.1.3 Palo Alto Networks
- 7.1.4 Cisco
- 7.1.5 McAfee
- 7.1.6 HPE
- 7.1.7 Checkpoint
- 7.1.8 Zscaler
- 7.1.9 Fortinet
- 7.1.10 Sophos













