 |
市场调查报告书
商品编码
1537622
零信任安全:市场占有率分析、产业趋势/统计、成长预测(2024-2029)Zero Trust Security - Market Share Analysis, Industry Trends & Statistics, Growth Forecasts (2024 - 2029) |
||||||
※ 本网页内容可能与最新版本有所差异。详细情况请与我们联繫。
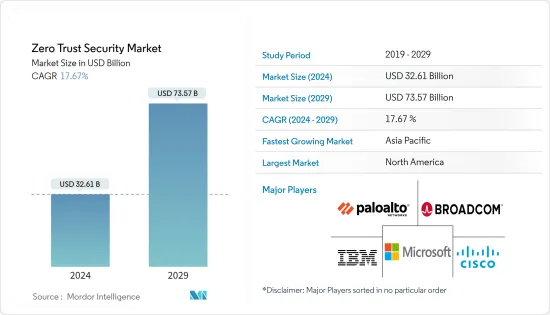
零信任安全市场规模预计到 2024 年为 326.1 亿美元,预计到 2029 年将达到 735.7 亿美元,在预测期内(2024-2029 年)复合年增长率为 17.67%。
向云端运算的转变迫使企业重新考虑其安全状况。零信任支援安全存取云端基础的应用程式和资料,非常适合云端优先计划。组织需要开发强大的资料保护机制,以遵守 GDPR 和 CCPA 等严格的资料隐私法,而零信任可以实现合规性。企业正在各领域更广泛地利用零信任框架作为基本安全策略。传统的基于边界的范式正在被放弃。各大科技公司正在收购零信任安全业务,以改善保全服务。
主要亮点
- 为了成功实施零信任安全,企业越来越多地与网路安全供应商和託管安全服务提供者 (MSSP) 合作。这些伙伴关係提供知识和资源来应对确保更广泛安全边界的挑战。云端运算的使用日益广泛,提供了灵活性、扩充性和成本效率,正在彻底改变企业的运作方式。敏感资讯和关键应用程式不再局限于本地资料中心,安全范围已经扩大。
- 企业经常使用许多云端供应商,导致其资料和应用程式分散。这种多重云端策略使得保护扩展的安全边界变得更加困难。在共用责任方法中,云端服务提供者 (CSP) 保护基础设施,客户负责保护资料和应用程式。这种责任分工强调了全面安全计画的必要性。员工和第三方合作伙伴从各种位置和装置存取云端服务。这需要持续监控和安全存取控制。
- 适应不断变化的安全边界(资料和使用者分布在许多位置和设备上)对于网路安全的未来至关重要。零信任安全提供了一个可扩展的架构,可以领先于新威胁并解决当前问题。随着企业不断重新评估其安全策略以应对这些变化,以及创新解决方案不断重塑网路安全格局,全球零信任安全市场可望持续成长。
- 对于拥有旧有系统的公司来说,实施零信任安全需要很长的过渡期。因此,彻底的安全措施的部署可能会被推迟。升级或更换遗留系统以符合零信任方法需要时间、金钱和精力。因此,有些公司可能不愿采取零信任措施。随着组织逐渐在现代系统和应用程式中使用零信任安全,遗留元件可能会出现安全缺陷,从而抵消了网路其他部分的零信任优势。
- 在后 COVID-19 环境中,零信任安全变得更加重要。远距工作、云端、新威胁和合规性要求凸显了对灵活、主动的安全方法的需求。采用零信任的组织能够更好地应对疫情后的挑战,并在不断发展的数位环境中保护其最重要的资产。
零信任安全市场趋势
中小企业实现显着成长
- 中小企业在经济格局中发挥核心作用,有助于增强金融包容性,并向贫困阶级和服务不足的市场提供商品和服务。这些公司是创新的重要推动者,具有很高的成长潜力。例如,根据欧盟委员会预计,2023年欧盟将有约2,440万家中小企业(SME),中小企业构成欧洲经济的支柱。
- 即使采用混合模式,大多数中小企业仍然没有为未来职场环境和员工政策的灵活性做好准备。在家工作、混合工作安排和以家庭为中心的劳动力结构的增加正在帮助快速过渡到更安全的策略。为了确保永续性,小型企业需要识别市场机会和消费者需求。
- 云端基础的环境可确保长期永续性和弹性,推动中小型企业对各种网路安全策略的需求。零信任安全性可确保强大且安全的工作环境,并且只有在信任得到检验的情况下,任何存取组织网路架构的尝试才会成功。当使用者存取应用程式时,系统会验证使用者和装置并持续监控信任。这使您能够保护组织的应用程式和环境免受任何使用者、装置或位置的影响,这对于中小型企业的未来发展至关重要。
- 许多老牌和新兴网路安全公司正在向中小型企业提供零信任网路存取(ZTNA) 服务,以满足不断增长的需求。云端发送服务将零信任解决方案扩展到云端原生企业和企业,拥抱云端采用,并使中小型企业能够提高生产力、增强安全性、提高可见度并显着减少所带来的攻击面。
亚太地区预计将出现显着成长
- 过去十年,亚洲的技术力得到了提高,许多公司将数位转型作为其主要目标之一。数位转型革命开始得更早,但疫情加速了其速度。特别是,它影响了组织处理 IT 生态系统和安全的方式。
- 亚太地区预计将主导全球製造业,年增率最高,尤其是中国。与大流行前相比,该国的生产力取得了显着增长。
- 中国继续优先考虑数位化并改善网路安全态势。 ZAT 的解决方案可保护他们的数位业务并帮助他们遵守监管标准。中国企业越来越认识到 ZAT 解决方案的价值,而中国市场是亚太地区采用 ZAT 解决方案的关键驱动力。
- 2023 年 8 月,亚洲领先的通讯技术集团新加坡电信宣布建立策略合作伙伴关係,首次在亚洲提供 Zscaler 安全解决方案。透过此次合作,新加坡电信的 MSSE 将为内部资源和技能不足的企业提供一体化数位安全解决方案,以保护其数位资产免受网路威胁。
- 新加坡电信的託管安全服务边缘 (MSSE) 由专门的网路安全专家提供售前和售后支援、部署、平台咨询、维护和 24/7 威胁缓解等资源。随着企业继续以前所未有的速度数数位化,网路威胁的风险也在增加。
零信任安全产业概述
零信任安全市场是分散的,有以下全球和区域公司。思科系统公司、帕洛阿尔托网路公司、IBM 公司、博通公司(赛门铁克公司)和微软公司的产品差异化程度较高,产品渗透率不断提高,竞争水平较高。一揽子解决方案提供,使整合的产品看起来像是产品服务的一部分。
- 2023 年 9 月,博通收购了 VMware。透过收购 VMware,博通能够将赛门铁克的安全产品组合与 VMware 的 SD-WAN 功能结合。透过整合赛门铁克、VMware SD-WAN 和 Carbon Black 的一些安全功能,Broadcom 进入了单一供应商安全存取服务边际(SASE) 行业,如果成功,将占领整个 SASE 行业的份额和收益。 Broadcom 目前的 Symantec SASE 和保全服务边缘 (SSE) 产品组合包括安全 Web 闸道 (SWG)、预防资料外泄(DLP)、云端存取安全仲介(CASB)、零信任网路存取(ZTNA)、SSL 检查,包含下列组件网路隔离。
- 2023 年 7 月,Accenture与 Palo Alto Networks 合作加强零信任安全。为了协助企业改善网路安全状况并加速实施业务转型倡议,两家公司将联手使用 SASE 解决方案共同提供安全存取服务边缘解决方案。 Palo Alto Networks 和Accenture提供全面的託管 SASE 解决方案来应对企业挑战。透过将全球最大的系统整合商的优势与 SASE 解决方案相结合,世界各地的企业可以加速业务转型,并从改进的网路效能、一致的安全策略和实施中受益。
其他好处:
- Excel 格式的市场预测 (ME) 表
- 3 个月分析师支持
目录
第一章 简介
- 研究假设和市场定义
- 调查范围
第二章调查方法
第三章执行摘要
第四章市场洞察
- 市场概况
- 产业吸引力-波特五力分析
- 供应商的议价能力
- 买方议价能力
- 新进入者的威胁
- 替代品的威胁
- 竞争公司之间的敌对关係
- COVID-19 的影响
- 产业价值链分析
- 技术简介
- 零信任网络
- 零信任设备
- 零信任资料
- 零信任身份
- 零信任应用程式(可见性和分析)
第五章市场动态
- 市场驱动因素
- 资料外洩增加
- 您组织的安全范围不仅限于职场
- 市场限制因素
- 遗留应用程式、基础架构和作业系统使得采用零信任模型变得困难
第六章 市场细分
- 按发展
- 本地
- 云
- 按组织规模
- 小型企业
- 大公司
- 按最终用户产业
- 资讯科技/通讯
- BFSI
- 製造业
- 卫生保健
- 能源/电力
- 零售业
- 政府机构
- 其他最终用户产业
- 按地区
- 北美洲
- 欧洲
- 亚洲
- 澳洲/纽西兰
- 拉丁美洲
- 中东/非洲
第七章 竞争格局
- 公司简介
- Cisco Systems Inc.
- Palo Alto Networks Inc.
- Broadcom Inc.(Symantec Corporation)
- Microsoft Corporation
- IBM Corporation
- Google Inc.
- Check Point Software Technologies Ltd
- Blackberry Limited
- Akamai Technologies Inc.
- Delinea(Centrify Corporation)
- Okta Inc.
- Fortinet Inc.
- Sophos Group PLC
- Cyxtera Technologies Inc.
第八章投资分析
第9章市场的未来
The Zero Trust Security Market size is estimated at USD 32.61 billion in 2024, and is expected to reach USD 73.57 billion by 2029, growing at a CAGR of 17.67% during the forecast period (2024-2029).

Organizations have had to review their security postures due to the move toward cloud computing. Zero Trust facilities secure access to cloud-based apps and data, which fits well with cloud-first plans. Organizations must develop robust data protection mechanisms to comply with strict data privacy laws like GDPR and CCPA, making Zero Trust a compliance enabler. Businesses use the Zero Trust framework in various sectors more widely as a fundamental security strategy. The conventional perimeter-based paradigm is being abandoned. Big technology corporations are buying Zero Trust security businesses to improve security services.
Key Highlights
- To successfully adopt zero-trust security, businesses are increasingly developing alliances with cybersecurity vendors and managed security service providers (MSSPs). These collaborations contribute knowledge and resources to handle the challenges of protecting the wider security perimeter. The growing use of cloud computing, which provides flexibility, scalability, and cost-efficiency, has completely changed how businesses function. Sensitive information and essential applications are no longer restricted to on-premises data centers, which also expanded the security perimeter.
- Businesses frequently use numerous cloud providers, which results in scattered data and applications. The enlarged security perimeter is more difficult to secure with this multi-cloud strategy. Under a shared responsibility approach, cloud service providers (CSPs) secure the infrastructure while customers are in charge of protecting their data and applications. This shared duty emphasizes the necessity of an all-encompassing security plan. Employees and third-party partners use a variety of locations and devices to access cloud services. So, there is a need for continuous monitoring and safe access controls.
- Adapting to the changing security perimeter, where data and users are dispersed across numerous locations and devices, is essential for the future of cybersecurity. Zero-trust security offers a scalable architecture to keep ahead of new threats and address current issues. The global zero-trust security market has been anticipated to experience sustained growth as enterprises continue to reevaluate their security policies in response to these shifts, with innovative solutions continuously reshaping the cybersecurity landscape.
- Adopting zero-trust security requires a longer transition period for organizations with legacy systems. The deployment of thorough security measures may be delayed as a result. It takes time, money, and labor to upgrade or replace historical systems so they align with the zero-trust approach. As a result, some businesses may be discouraged from adopting zero-trust efforts. Legacy components may develop security flaws as organizations progressively use zero-trust security for their contemporary systems and applications, thereby offsetting the advantages of zero trust elsewhere in the network.
- Zero Trust Security has become much more crucial in the post-COVID-19 environment. Remote work, the cloud, emerging threats, and compliance obligations highlight the necessity for a flexible, proactive security approach. Organizations that adopt zero trust are better equipped to deal with the challenges of the post-pandemic scenario and protect their most essential assets in a constantly evolving digital environment.
Zero Trust Security Market Trends
Small and Medium Enterprises to Witness Major Growth
- SMEs play a central role in the economic landscape, helping to strengthen financial inclusion and supplying goods and services to poor and underserved markets. These enterprises are critical drivers of innovation and offer high growth potential. For instance, according to the European Commission, approximately 24.4 million small and medium-sized enterprises (SMEs) were estimated to be in the European Union in 2023, as SMEs form the backbone of the European economy.
- Even following a hybrid model, most small businesses have yet to prepare for flexibility within future work environments and employee policies. Growth in working from home, hybrid modalities, and family-focused employee structures aid quick transition to more secure strategies. To ensure sustainability, MSMEs should identify market opportunities and consumer demands.
- The cloud-based environment ensures long-term sustainability and resilience, driving the demand for various cybersecurity strategies for SMEs. A robust and secure work environment is guaranteed with zero-trust security, and an attempt to access an organization's network architecture can only succeed once trust is validated. When a user accesses an application, the user and device are confirmed, and trust is continuously monitored. This helps secure the organization's applications and environments from any user, device, and location, which is vital for SME's future growth.
- Many established and emerging cybersecurity players offer zero-trust network access (ZTNA) services for small and medium enterprises to cater to the rising demands. The cloud-delivered service extends the company's zero-trust solutions to cloud-native businesses and enterprises, embracing cloud adoption and giving SMEs improved productivity, better security, greater visibility, and a significantly reduced attack surface.
Asia Pacific Expected to Register Significant Growth
- Asia's technological abilities have increased over the past decade, with many businesses concentrating on the digital shift as one of their key goals throughout the pandemic. While the revolutions of digital transformation were set in motion much earlier, the pandemic accelerated their speed. It particularly impacted how organizations approach their IT ecosystem and security.
- Asia-Pacific is anticipated to dominate the global manufacturing industry, recording the highest inter-annual growth rate, especially in China. This country has achieved significant growth in its production rates compared to its pre-pandemic pace.
- China keeps prioritizing digitalization and improving its cybersecurity posture. ZAT solutions safeguard its digital operations and help comply with regulatory standards. Chinese businesses are increasingly realizing the value of ZAT solutions, making the Chinese market a key driver of adoption in the Asia-Pacific region.
- In August 2023, Singtel, Asia's leading telecommunications technology group, announced a strategic partnership to offer Zscaler's security solutions in Asia, a first for the region. Through this partnership, Singtel's MSSE offers businesses impacted by insufficient in-house resources or skill sets an all-in-one digital security solution that helps to protect their digital assets against cyber threats.
- Enterprises in the APAC region will now have seamless access to Zscaler's Zero Trust Exchange, a cloud-based platform, through Singtel's Managed Security Service Edge (MSSE) suite of services, which includes pre-sales to post-sales support from dedicated cybersecurity experts as well as resources such as build implementation, platform consultation, maintenance, and round-the-clock threat mitigation. As the rate of enterprise digitalization continues to accelerate at an unprecedented pace, so does the risk of cyber threats.
Zero Trust Security Industry Overview
The zero trust security market is fragmented with the presence of global and regional players such as Cisco Systems Inc., Palo Alto Networks Inc., IBM Corporation Inc., Broadcom Inc. (Symantec Corporation), and Microsoft Corporation. Moderate to high product differentiation, growing levels of product penetration, and high levels of competition characterize the market. Generally, the solutions are offered as a package solution, making the consolidated offering look like a part of the product's service.
- In September 2023, Broadcom acquired Vmware. With its potential VMware acquisition, Broadcom can meld Symantec's security portfolio with VMware's SD-WAN capabilities. By integrating Symantec, VMware SD-WAN, and some of Carbon Black's security capabilities, Broadcom could enter the single-vendor secure access service edge (SASE) industry and boost its overall SASE industry share and revenue if executed well. Broadcom's current Symantec SASE and security service edge (SSE) portfolio includes components such as secure web gateway (SWG), data loss prevention (DLP), cloud access security brokers (CASB), zero-trust network access (ZTNA), SSL inspection, and web isolation.
- In July 2023, Accenture teamed with Palo Alto Networks to bolster Zero Trust Security. In order to enable enterprises to improve their cybersecurity posture and speed up the implementation of business transformation initiatives, they have joined forces to deliver jointly secure access service edge solutions using a SASE solution. Palo Alto Networks and Accenture provide a comprehensive managed SASE solution that tackles organizations' challenges. Enterprises worldwide can accelerate their business transformation by combining the strength of the largest global systems integrator with the SASE solution, benefiting from improved network performance and a consistent security policy and implementation.
Additional Benefits:
- The market estimate (ME) sheet in Excel format
- 3 months of analyst support
TABLE OF CONTENTS
1 INTRODUCTION
- 1.1 Study Assumptions and Market Definition
- 1.2 Scope of the Study
2 RESEARCH METHODOLOGY
3 EXECUTIVE SUMMARY
4 MARKET INSIGHTS
- 4.1 Market Overview
- 4.2 Industry Attractiveness - Porter's Five Forces Analysis
- 4.2.1 Bargaining Power of Suppliers
- 4.2.2 Bargaining Power of Buyers
- 4.2.3 Threat of New Entrants
- 4.2.4 Threat of Substitutes
- 4.2.5 Intensity of Competitive Rivalry
- 4.3 Impact of COVID-19
- 4.4 Industry Value Chain Analysis
- 4.5 Technology Snapshot
- 4.5.1 Zero Trust Networks
- 4.5.2 Zero Trust Devices
- 4.5.3 Zero Trust Data
- 4.5.4 Zero Trust Identities
- 4.5.5 Zero Trust Applications (Visibility and Analytics)
5 MARKET DYNAMICS
- 5.1 Market Drivers
- 5.1.1 Increasing Number of Data Breaches
- 5.1.2 Security Perimeter of an Organization not Being Limited to Workplace
- 5.2 Market Restraints
- 5.2.1 Legacy Applications, Infrastructure, and Operating Systems Not Likely to Adopt Zero Trust Model
6 MARKET SEGMENTATION
- 6.1 By Deployment
- 6.1.1 On-premise
- 6.1.2 Cloud
- 6.2 By Organization Size
- 6.2.1 Small and Medium Enterprises
- 6.2.2 Large Enterprises
- 6.3 By End-user Industry
- 6.3.1 IT and Telecom
- 6.3.2 BFSI
- 6.3.3 Manufacturing
- 6.3.4 Healthcare
- 6.3.5 Energy and Power
- 6.3.6 Retail
- 6.3.7 Government
- 6.3.8 Other End-user Industries
- 6.4 By Geography***
- 6.4.1 North America
- 6.4.2 Europe
- 6.4.3 Asia
- 6.4.4 Australia and New Zealand
- 6.4.5 Latin America
- 6.4.6 Middle East and Africa
7 COMPETITIVE LANDSCAPE
- 7.1 Company Profiles*
- 7.1.1 Cisco Systems Inc.
- 7.1.2 Palo Alto Networks Inc.
- 7.1.3 Broadcom Inc. (Symantec Corporation)
- 7.1.4 Microsoft Corporation
- 7.1.5 IBM Corporation
- 7.1.6 Google Inc.
- 7.1.7 Check Point Software Technologies Ltd
- 7.1.8 Blackberry Limited
- 7.1.9 Akamai Technologies Inc.
- 7.1.10 Delinea (Centrify Corporation)
- 7.1.11 Okta Inc.
- 7.1.12 Fortinet Inc.
- 7.1.13 Sophos Group PLC
- 7.1.14 Cyxtera Technologies Inc.











