 |
市场调查报告书
商品编码
1627127
云端识别及存取管理软体:市场占有率分析、产业趋势、成长预测(2025-2030)Cloud Identity and Access Management Software - Market Share Analysis, Industry Trends & Statistics, Growth Forecasts (2025 - 2030) |
||||||
※ 本网页内容可能与最新版本有所差异。详细情况请与我们联繫。
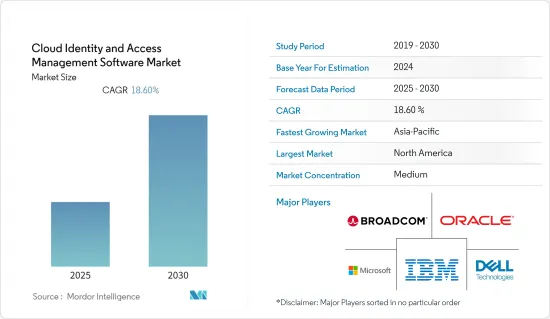
云端识别及存取管理软体市场预计在预测期内复合年增长率为 18.6%
主要亮点
- 随着成本的降低和规模经济的发展,云端技术正在彻底改变企业的营运方式。然而,缺乏适当的安全措施可能会削弱云端运算的优势。这需要对安全解决方案的基本需求,其中包括针对身分相关犯罪的安全性,这正在推动云端识别及存取管理市场的发展。
- 公共云端是市场上最受欢迎的云端部署类型。这是由于它在各个行业中的使用越来越多。然而,由于混合云端的采用将保持最高的复合年增长率。
- 随着行动电话和平板电脑变得越来越流行,员工现在可以将行动电话和笔记型电脑连接到业务网路。员工不再使用旧的办公桌面,而是更喜欢在企业中使用自己的设备,这增加了对云端身分和存取管理软体的需求,从而推动了市场研究。
云端识别及存取管理 (IAM) 软体在 COVID-19 影响期间对市场产生了积极影响,预计将在预测期间为市场成长做出重大贡献。 IAM厂商纷纷出面为企业提供协助。例如,IBM 在疫情期间宣布将向新客户免费提供 IBM Security MAss360 with Watson 和 IBM Cloud Identity 等关键技术 90 天。
云端识别及存取管理软体市场趋势
单一登入 (SSO) 和统一配置将实现最高成长
- 单一登入 (SSO) 是身分存取管理的最新创新。该解决方案的紧凑性和灵活性使其对从 IT 公司到製造业的广泛最终用户具有吸引力。
- 在联合配置的情况下,解决方案是称为联合身份和配置的两个独立系统的混合。联合身分是指允许不同计画/域共用身分管理责任的标准。另一方面,配置是管理使用者或系统存取权限所需的生命週期中所有步骤的自动化。
- 在利用云端中的应用程式和资料的同时管理内部用户帐户的能力是联合配置解决方案提供的主要优势,并且正在推动这些解决方案在市场上的显着增长。
- 此外,社会工程攻击和身分盗窃的增加正在推动单一登入和统一配置的成长,特别是在北美和欧洲的已开发国家。
- 身分盗窃资源中心估计,2022 年美国资料将被窃盗 1,802 次。同年,资料外洩、资料外洩、资料外洩等资料入侵也影响了超过4.22亿人。虽然这是三个不同的事件,但它们都有相似的特征。所有这三个案例都是未经授权的威胁行为者存取敏感资料的结果。
北美占最大市场占有率
- 大多数全球领先的云端公司都位于北美,也有许多新兴企业将云端作为解决方案部署的首选形式。
- 国际电联报告称,除了云端基础的软体服务采用率最高之外,北美地区非常积极主动并专注于网路安全。
- 此外,较低的资本支出和更快的更新部署等优势是北美采用云端基础的身份管理解决方案的关键原因。
- 该地区 BFSI 行业主要采用云端基础的IAM,并且未来可能会增加。因为,根据美国消费者哨兵网路报道,卡片诈骗和违规行为在身分窃盗总数中占很大比例。
- 该地区深受网路攻击影响,是世界上网路安全事件数量最多的地区之一。因此,该地区也采取了措施,是网路安全、技术和实施方面最先进的地区之一。因此,对网路安全日益增长的需求预计也将成为该地区云端识别及存取管理软体市场的驱动力。
云端识别及存取管理软体产业概述
全球和地区已有多家公司进入云端识别及存取管理市场,市场竞争温和。然而,市场正走向各种较小参与企业的整合。一些市场参与企业正在透过创新在市场上获得可持续的竞争优势。该市场的主要企业包括IBM公司、微软公司和甲骨文公司。
CloudIBN 于 2022 年 12 月宣布采用识别及存取管理服务。透过这套 IAM 解决方案,企业可以有效管理整个组织的使用者存取控制并确保资料安全。
其他好处
- Excel 格式的市场预测 (ME) 表
- 3 个月分析师支持
目录
第一章简介
- 研究假设和市场定义
- 调查范围
第二章调查方法
第三章执行摘要
第四章市场动态
- 市场概况
- 市场驱动因素
- 安全漏洞数量和相关成本增加
- 企业 BYOD 使用率呈上升趋势
- 市场限制因素
- 云端基础的应用程式面临网路风险的脆弱性
- 产业吸引力-波特五力分析
- 供应商的议价能力
- 买方议价能力
- 新进入者的威胁
- 替代品的威胁
- 竞争公司之间的敌对关係
- 技术简介
- COVID-19 市场影响评估
第五章市场区隔
- 按组织规模
- 小型企业
- 大型组织
- 按解决方案类型
- 审核、合规和管治
- 单一登入 (SSO) 和整合配置
- 特权存取管理
- 目录服务
- 其他的
- 依部署类型
- 民众
- 私人的
- 杂交种
- 按行业分类
- 资讯科技/通讯
- BFSI
- 医疗保健
- 娱乐媒体
- 零售
- 教育
- 其他行业
- 按地区
- 北美洲
- 欧洲
- 亚太地区
- 拉丁美洲
- 中东/非洲
第六章 竞争状况
- 公司简介
- Cyberark Software Ltd.
- Broadcom Inc.(CA Technologies)
- IBM Corporation
- Microsoft Corporation
- Oracle Corporation
- Okta Inc.
- Centrify Corporation
- Sailpoint Technologies Holdings Inc.
- Auth0 Inc.
- Dell Technologies Inc.
第七章 投资分析
第八章 市场机会及未来趋势
The Cloud Identity and Access Management Software Market is expected to register a CAGR of 18.6% during the forecast period.

Key Highlights
- Due to cost savings and economies of scale, cloud technology is revolutionizing how businesses operate. However, the lack of proper security measures can undermine the benefits of cloud computing. This calls for a fundamental need for security solutions, including security for identity-related crimes, and hence drives the market for cloud identity and access management.
- The public cloud is the most popular type of cloud deployment on the market. This is because it is being used more and more in many different industries. However, hybrid cloud deployment is expected to register the highest CAGR over the forecast period because of growing adoption among small and medium-sized enterprises.
- As mobile phones and tablets become more popular, employees can connect their phones and laptops to the business network. Instead of using their old office desktops, employees like to use their own devices in enterprises, which increases the need for cloud identity and access management software and hence drives the market studied.
During the COVID-19 impact period, cloud identity and access management (IAM) software was expected to have a positive impact on the market and contribute significantly to its growth over the forecast period. IAM vendors came forward to assist the enterprises. For instance, during the pandemic, IBM announced that it would make critical technologies such as IBM Security MAss360 with Watson and IBM Cloud Identity available at no charge for new clients for 90 days.
Cloud Identity and Access Management Software Market Trends
Single Sign-on (SSO) and Federated Provisioning is Expected to Witness the Highest Growth
- Single sign-on (SSO) is the most recent innovation in identity access management. The compact and highly flexible nature of this solution is attracting a wide range of end-users, ranging from IT companies to the manufacturing sector.
- In the case of federated provisioning, the solution is a mix of two separate systems called federated identity and provisioning. Federated identity refers to the standards that allow different policy domains to share identity management responsibilities. Provisioning, on the other hand, is the automation of all the steps in the lifecycle that are needed to manage user or system access entitlements.
- The capability of retaining in-house control of user accounts while leveraging cloud applications and data is the significant advantage that federated provisioning solutions offer and is driving the immense growth of these solutions in the market.
- Furthermore, the increasing number of social engineering attacks and identity thefts is driving the growth of both single sign-on and federated provisioning, especially in the developed countries of North America and Europe.
- The Identity Theft Resource Center thinks that in the United States in 2022, there were 1802 times when data was stolen. In the same year, data intrusions such as data breaches, data leaks, and data exposure also had an impact on over 422 million people. Even though these are three distinct events, they all share a similar trait. All three instances result in an unauthorized threat actor accessing the sensitive data.
North America Occupies the Largest Market Share
- Most of the cloud-advanced organizations in the world are from the North American region, along with a high number of startups whose most preferred mode of solution deployment is in the cloud.
- Along with the highest adoption of cloud-based software services, it is also reported by the ITU that the North American region is very proactive and committed to cybersecurity.
- Moreover, benefits like reduced CAPEX and faster rollouts of updates are some of the major reasons for the adoption of cloud-based identity management solutions in the North American region.
- Major adoption of cloud-based IAM in the region is seen in the BFSI sector, and it may continue to rise, as credit card frauds and breaches accounted for a major share of the total number of identity thefts, as reported by the US consumer sentinel network.
- The region is highly affected by cyberattacks and has one of the highest cybersecurity incidents in the world. Therefore, the region has also implemented its countermeasures and has become one of the most advanced regions with respect to cybersecurity, technology, and its adoption. Therefore, rising cybersecurity needs will also drive the cloud identity and access management software market in the region.
Cloud Identity and Access Management Software Industry Overview
The cloud identity and access management market comprises several global and regional players and is a moderately contested market space. However, the market is shifting toward the consolidation of various smaller players. Several market players are gaining a sustainable competitive advantage in the market through innovations. Some of the major players in the market are IBM Corporation, Microsoft Corporation, and Oracle Corporation, among others.
CloudIBN announced the introduction of Identity and Access Management services in December 2022. With the help of this IAM solution suite, businesses can effectively manage user access control across their whole organization and keep their data safe.
Additional Benefits:
- The market estimate (ME) sheet in Excel format
- 3 months of analyst support
TABLE OF CONTENTS
1 INTRODUCTION
- 1.1 Study Assumptions & Market Definition
- 1.2 Scope of the Study
2 RESEARCH METHODOLOGY
3 EXECUTIVE SUMMARY
4 MARKET DYNAMICS
- 4.1 Market Overview
- 4.2 Market Drivers
- 4.2.1 Increasing Number of Security Breaches and Related Costs
- 4.2.2 Increasing Trend of Using BYODs in Enterprises
- 4.3 Market Restraints
- 4.3.1 Vulnerability of Cloud-based Applications to Cyber Risks
- 4.4 Industry Attractiveness - Porter's Five Forces Analysis
- 4.4.1 Bargaining Power of Suppliers
- 4.4.2 Bargaining Power of Buyers
- 4.4.3 Threat of New Entrants
- 4.4.4 Threat of Substitute Products
- 4.4.5 Intensity of Competitive Rivalry
- 4.5 Technology Snapshot
- 4.6 Assessment of Impact of COVID-19 on the Market
5 MARKET SEGMENTATION
- 5.1 By Size of Organization
- 5.1.1 SMEs
- 5.1.2 Large Organization
- 5.2 By Type of Solution
- 5.2.1 Audit, Compliance, and Governance
- 5.2.2 Single Sign-on (SSO) and Federated Provisioning
- 5.2.3 Privileged Access Management
- 5.2.4 Directory Service
- 5.2.5 Other Types of Solutions
- 5.3 By Deployment Type
- 5.3.1 Public
- 5.3.2 Private
- 5.3.3 Hybrid
- 5.4 By End-User Vertical
- 5.4.1 IT and Telecommunication
- 5.4.2 BFSI
- 5.4.3 Healthcare
- 5.4.4 Entertainment and Media
- 5.4.5 Retail
- 5.4.6 Education
- 5.4.7 Other End-User Verticals
- 5.5 Geography
- 5.5.1 North America
- 5.5.2 Europe
- 5.5.3 Asia-Pacific
- 5.5.4 Latin America
- 5.5.5 Middle East and Africa
6 COMPETITIVE LANDSCAPE
- 6.1 Company Profiles
- 6.1.1 Cyberark Software Ltd.
- 6.1.2 Broadcom Inc. (CA Technologies)
- 6.1.3 IBM Corporation
- 6.1.4 Microsoft Corporation
- 6.1.5 Oracle Corporation
- 6.1.6 Okta Inc.
- 6.1.7 Centrify Corporation
- 6.1.8 Sailpoint Technologies Holdings Inc.
- 6.1.9 Auth0 Inc.
- 6.1.10 Dell Technologies Inc.







