 |
市场调查报告书
商品编码
1833452
资料中心逻辑安全市场机会、成长动力、产业趋势分析及 2025 - 2034 年预测Data Center Logical Security Market Opportunity, Growth Drivers, Industry Trend Analysis, and Forecast 2025 - 2034 |
||||||
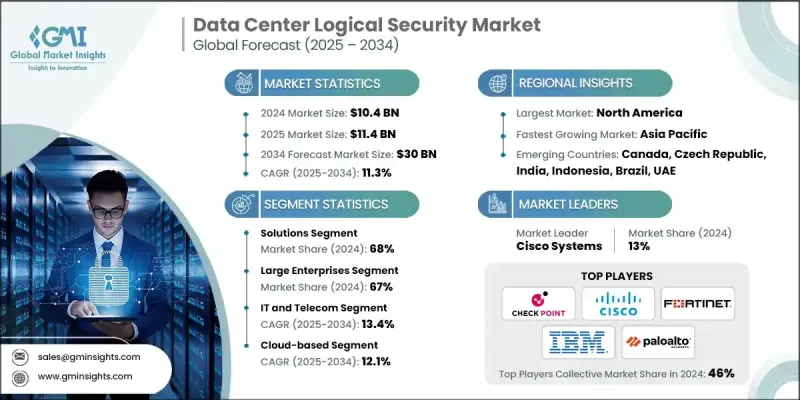
2024 年全球资料中心逻辑安全市场价值为 104 亿美元,预计到 2034 年将以 11.3% 的复合年增长率成长,达到 300 亿美元。
随着网路威胁的演变和数位转型的加速,资料中心内部的安全已成为营运信任和业务连续性的核心支柱,而不仅仅是基于边界的要求。企业正在转变其策略,采用整合平台,以实现跨混合云和多云环境的自动威胁侦测、主动合规性和全面保护。云端原生安全架构、人工智慧和零信任框架的采用,正在帮助企业应对更严格的全球资料保护法规并确保合规性。全球监管要求的收紧,导致对加密技术、身分驱动的安全模型和微分段的需求不断增加。这为网路安全供应商、合规专家和资料中心营运商之间的合作开闢了机会,以创建高度客製化的逻辑安全框架,以满足特定行业和区域的需求。此外,随着云端采用率的提高和软体定义网路 (SDN) 的兴起,企业正在寻求更敏捷、自动化的安全解决方案,以应对复杂的威胁,从而推动安全资讯和事件管理 (SIEM) 和入侵侦测/防御系统 (IDS/IPS) 的部署。
| 市场范围 | |
|---|---|
| 起始年份 | 2024 |
| 预测年份 | 2025-2034 |
| 起始值 | 104亿美元 |
| 预测值 | 300亿美元 |
| 复合年增长率 | 11.3% |
解决方案细分市场在2024年占据了68%的份额,预计到2034年将以10%的复合年增长率成长。这些解决方案越来越多地整合生成式人工智慧和机器学习技术,将安全方法从被动侦测转变为主动补救和自主威胁预防。这些人工智慧驱动的系统可以自动进行威胁搜寻,简化复杂的网路攻击场景,并在极少的人为干预下启动即时回应行动。这种演变对于保护大规模、快速变化的资料中心环境、缩小网路安全技能差距以及透过预测性和自我修復的安全基础设施防御高级威胁行为者至关重要。
大型企业在2024年占了67%的市场份额,预计在2025年至2034年期间的复合年增长率将达到10%。这些企业之所以占据主导地位,是因为它们有能力投资瞻博网路、趋势科技、飞塔和博通等领先供应商的高端整合安全平台。大型企业拥有庞大的数位足迹和复杂的合规性要求,因此需要高效能的安全解决方案和集中式管理系统。他们承担实施成本和管理复杂环境的能力促使供应商优先考虑他们的安全需求,从而有效地塑造了更广泛的市场格局。
2024年,北美资料中心逻辑安全市场占据37.7%的市场。该地区广泛实施的零信任安全模型正在重塑资料中心的安全保障方式。这些模型强制执行严格的存取控制、持续监控和细粒度的安全策略,显着降低了风险。随着医疗保健、保险和金融等行业对零信任的依赖日益加深,预计零信任将成为整个地区逻辑安全的基础模型,因为企业面临内部漏洞和外部威胁。
资料中心逻辑安全市场的关键参与者包括 Palo Alto Networks、思科系统、麦克菲、IBM、Fortinet、惠普企业、Check Point 软体技术、大陆集团、瞻博网路、趋势科技和博通。这些公司在提供针对现代资料中心环境的全面、基于人工智慧的安全解决方案方面处于领先地位。为了巩固其市场地位,资料中心逻辑安全产业的公司正在采取多项关键策略。他们高度重视研发,以开发能够自主侦测威胁并即时回应的人工智慧驱动、可自我修復的安全解决方案。
目录
第一章:方法论
- 市场范围和定义
- 研究设计
- 研究方法
- 资料收集方法
- 资料探勘来源
- 全球的
- 地区/国家
- 基础估算与计算
- 基准年计算
- 市场评估的主要趋势
- 初步研究和验证
- 主要来源
- 预测模型
- 研究假设和局限性
第二章:执行摘要
第三章:行业洞察
- 产业生态系统分析
- 供应商格局
- 利润率
- 成本结构
- 每个阶段的增值
- 影响价值链的因素
- 中断
- 产业衝击力
- 成长动力
- 不断升级的网路威胁
- 云端运算和混合环境
- 监理合规要求
- 零信任架构采用
- 产业陷阱与挑战
- 整合复杂性和成本
- 网路安全人才短缺
- 市场机会
- 人工智慧驱动的安全解决方案
- 託管安全服务(MSS)的成长
- 新兴市场的扩张
- 虚拟化和边缘运算安全
- 成长动力
- 成长潜力分析
- 监管格局
- 北美洲
- 欧洲
- 亚太地区
- 拉丁美洲
- 中东和非洲
- 波特的分析
- PESTEL分析
- 技术和创新格局
- 当前的技术趋势
- 无密码身份验证的演变
- 扩展检测和响应 (XDR) 演变
- 隐私保护分析技术
- 容器安全和运行时保护
- 新兴技术
- 去中心化身份和自主主权身份
- 同态加密与机密计算
- 云端安全网格架构
- 安全服务网格实现
- 当前的技术趋势
- 成本分解分析
- 专利分析
- 用例
- 金融服务
- 医疗保健与生命科学
- 政府与国防
- 製造业和工业
- 最佳情况
- 投资与融资趋势分析
- 供应链动态和依赖性
- 多云安全复杂性分析
- 合规负担评估框架
- 技能差距对安全态势的影响
- 安全债务管理危机
- 网路保险对安全投资的影响
- 市场扰动分析
- 量子计算影响时间表
- 人工智慧驱动的安全革命
- 零信任架构要求
- 云端原生安全转型
- 隐私监管爆炸性成长
- 供应商选择和实施策略
- 先进的供应商评估框架
- 实施最佳实践
- 风险缓解与管理
- 市场表现与投资报酬率分析
- 安全投资ROI框架
- 成本优化策略
- 绩效影响评估
- 永续性和环境方面
- 永续实践
- 减少废弃物的策略
- 生产中的能源效率
- 环保倡议
- 碳足迹考虑
第四章:竞争格局
- 介绍
- 公司市占率分析
- 北美洲
- 欧洲
- 亚太地区
- 拉丁美洲
- 多边环境协定
- 主要市场参与者的竞争分析
- 竞争定位矩阵
- 战略展望矩阵
- 关键进展
- 併购
- 伙伴关係与合作
- 新产品发布
- 扩张计划和资金
- 产品组合和技术基准测试
- 研发投资分析
- 市场集中度与供应商生态系统
- 配销通路与合作伙伴网路分析
- 供应商路线图一致性评估
- 技术整合复杂性矩阵
- 供应商财务稳定性评估
第五章:市场估计与预测:依组件划分,2021 - 2034 年
- 主要趋势
- 解决方案
- 身分和存取管理 (IAM)
- 防火墙及网路安全
- 资料保护和加密
- 安全资讯和事件管理 (SIEM)
- 端点安全
- 云端安全解决方案
- 服务
- 专业服务
- 系统整合
- 培训与咨询
- 支援与维护
- 託管服务
- 专业服务
第六章:市场估计与预测:依组织规模,2021 - 2034 年
- 主要趋势
- 中小企业
- 大型企业
第七章:市场估计与预测:依最终用途,2021 - 2034
- 主要趋势
- 金融服务业协会
- 资讯科技和电信
- 卫生保健
- 政府和国防
- 零售与电子商务
- 其他的
第 8 章:市场估计与预测:按部署,2021 年至 2034 年
- 主要趋势
- 本地
- 基于云端
第九章:市场估计与预测:按地区,2021 - 2034
- 主要趋势
- 北美洲
- 我们
- 加拿大
- 欧洲
- 德国
- 英国
- 法国
- 义大利
- 西班牙
- 北欧人
- 俄罗斯
- 亚太地区
- 中国
- 印度
- 日本
- 韩国
- 澳新银行
- 东南亚
- 拉丁美洲
- 巴西
- 墨西哥
- 阿根廷
- 多边环境协定
- 南非
- 沙乌地阿拉伯
- 阿联酋
第十章:公司简介
- Global companies
- Amazon Web Services (AWS)
- Broadcom
- Check Point Software Technologies
- Cisco Systems
- CrowdStrike
- Fortinet
- Hewlett Packard Enterprise
- IBM
- Juniper
- Microsoft
- McAfee
- Palo Alto Networks
- Trend Micro
- Continental
- Regional companies
- Okta
- Ping Identity
- Qualys
- Rapid7
- SentinelOne
- Splunk
- Tenable
- Varonis Systems
- 新兴企业
- Axonius
- Dynatrace
- Jit Security
- Lacework
- Orca Security
- Snyk
- Wiz
The Global Data Center Logical Security Market was valued at USD 10.4 billion in 2024 and is estimated to grow at a CAGR of 11.3% to reach USD 30 billion by 2034.

As cyber threats evolve and digital transformation accelerates, security within data centers has become a core pillar of operational trust and business continuity rather than just a perimeter-based requirement. Organizations are shifting their strategies to embrace integrated platforms that enable automated threat detection, proactive compliance, and comprehensive protection across hybrid and multi-cloud environments. The adoption of cloud-native security architectures, artificial intelligence, and zero-trust frameworks is helping businesses address stricter global data protection laws and ensure compliance. The tightening of regulatory mandates worldwide has created increased demand for encryption technologies, identity-driven security models, and micro-segmentation. This has opened up collaboration opportunities among cybersecurity providers, compliance specialists, and data center operators to create highly customized logical security frameworks tailored to sector-specific and regional requirements. Additionally, increased cloud adoption and the rise of software-defined networking (SDN) are driving the deployment of security information and event management (SIEM) and intrusion detection/prevention systems (IDS/IPS), as enterprises seek more agile, automated security solutions to stay ahead of sophisticated threats.
| Market Scope | |
|---|---|
| Start Year | 2024 |
| Forecast Year | 2025-2034 |
| Start Value | $10.4 Billion |
| Forecast Value | $30 Billion |
| CAGR | 11.3% |
The solutions segment held a 68% share in 2024 and is projected to grow at a CAGR of 10% through 2034. These solutions are increasingly integrating generative AI and machine learning technologies, shifting the security approach from reactive detection to initiative-taking remediation and autonomous threat prevention. These AI-powered systems can conduct automated threat hunting, simplifying complex cyberattack scenarios, and initiating real-time response actions with minimal human intervention. This evolution is crucial for protecting large-scale, fast-changing data center environments, closing the cybersecurity skills gap, and defending against advanced threat actors through predictive, self-healing security infrastructures.
The large enterprises segment held 67% share in 2024 and is forecasted to grow at a CAGR of 10% between 2025 and 2034. These organizations dominate due to their ability to invest in premium, integrated security platforms from leading vendors like Juniper, Trend Micro, Fortinet, and Broadcom. With vast digital footprints and complex compliance requirements, large enterprises require high-performance security solutions and centralized management systems. Their capacity to absorb implementation costs and manage sophisticated environments pushes vendors to prioritize their security demands, effectively shaping the broader market landscape.
North America Data Center Logical Security Market held 37.7% share in 2024. The widespread implementation of Zero Trust security models in the region is reshaping how data centers are secured. These models enforce strict access controls, constant monitoring, and granular security policies, significantly reducing risk. With sectors such as healthcare, insurance, and finance increasingly relying on Zero Trust, it is expected to become the foundational model for logical security across the region, as organizations face both internal vulnerabilities and external threats.
Key players shaping the Data Center Logical Security Market include Palo Alto Networks, Cisco Systems, McAfee, IBM, Fortinet, Hewlett Packard Enterprise, Check Point Software Technologies, Continental, Juniper, Trend Micro, and Broadcom. These companies are leading the charge in offering comprehensive, AI-enabled security solutions tailored for modern data center environments. To reinforce their position in the market, companies in the data center logical security industry are adopting several critical strategies. They are focusing heavily on R&D to develop AI-driven, self-healing security solutions capable of autonomous threat detection and real-time response.
Table of Contents
Chapter 1 Methodology
- 1.1 Market scope and definition
- 1.2 Research design
- 1.2.1 Research approach
- 1.2.2 Data collection methods
- 1.3 Data mining sources
- 1.3.1 Global
- 1.3.2 Regional/Country
- 1.4 Base estimates and calculations
- 1.4.1 Base year calculation
- 1.4.2 Key trends for market estimation
- 1.5 Primary research and validation
- 1.5.1 Primary sources
- 1.6 Forecast model
- 1.7 Research assumptions and limitations
Chapter 2 Executive Summary
- 2.1 Industry 360° synopsis
- 2.2 Key market trends
- 2.2.1 Regional
- 2.2.2 Solution
- 2.2.3 Organization size
- 2.2.4 End Use
- 2.2.5 Deployment
- 2.3 TAM Analysis, 2025-2034
- 2.4 CXO perspectives: strategic imperatives
- 2.4.1 Executive decision points
- 2.4.2 Critical success factors
- 2.5 Future outlook and strategic recommendations
- 2.5.1 Technology roadmap & innovation trends
- 2.5.2 Emerging use cases & applications
- 2.5.3 Next-generation data center architecture security
- 2.5.4 Artificial intelligence & machine learning integration
- 2.5.5 Autonomous security operations evolution
- 2.5.6 Post-quantum cryptography transition
Chapter 3 Industry Insights
- 3.1 Industry ecosystem analysis
- 3.1.1 Supplier landscape
- 3.1.2 Profit margin
- 3.1.3 Cost structure
- 3.1.4 Value addition at each stage
- 3.1.5 Factor affecting the value chain
- 3.1.6 Disruptions
- 3.2 Industry impact forces
- 3.2.1 Growth drivers
- 3.2.1.1 Escalating cyber threats
- 3.2.1.2 Cloud computing & hybrid environments
- 3.2.1.3 Regulatory compliance requirements
- 3.2.1.4 Zero-trust architecture adoption
- 3.2.2 Industry pitfalls and challenges
- 3.2.2.1 Integration complexity & cost
- 3.2.2.2 Cybersecurity talent shortage
- 3.2.3 Market opportunities
- 3.2.3.1 AI-driven security solutions
- 3.2.3.2 Growth in managed security services (MSS)
- 3.2.3.3 Expansion in emerging markets
- 3.2.3.4 Virtualization & edge computing security
- 3.2.1 Growth drivers
- 3.3 Growth potential analysis
- 3.4 Regulatory landscape
- 3.4.1 North America
- 3.4.2 Europe
- 3.4.3 Asia Pacific
- 3.4.4 Latin America
- 3.4.5 Middle East & Africa
- 3.5 Porter’s analysis
- 3.6 PESTEL analysis
- 3.7 Technology and innovation landscape
- 3.7.1 Current technological trends
- 3.7.1.1 Password less authentication evolution
- 3.7.1.2 Extended detection & response (XDR) evolution
- 3.7.1.3 Privacy-preserving analytics technologies
- 3.7.1.4 Container security & runtime protection
- 3.7.2 Emerging technologies
- 3.7.2.1 Decentralized identity & self-sovereign identity
- 3.7.2.2 Homomorphic encryption & confidential computing
- 3.7.2.3 Cloud security mesh architecture
- 3.7.2.4 Security service mesh implementation
- 3.7.1 Current technological trends
- 3.8 Cost breakdown analysis
- 3.9 Patent analysis
- 3.10 Use cases
- 3.10.1 Financial Services
- 3.10.2 Healthcare & Life Sciences
- 3.10.3 Government & Defense
- 3.10.4 Manufacturing & Industrial
- 3.11 Best-case scenario
- 3.12 Investment & funding trends analysis
- 3.13 Supply chain dynamics & dependencies
- 3.14 Multi-cloud security complexity analysis
- 3.15 Compliance burden assessment framework
- 3.16 Skills gap impact on security posture
- 3.17 Security debt management crisis
- 3.18 Cyber insurance impact on security investments
- 3.19 Market disruption analysis
- 3.19.1 Quantum computing impact timeline
- 3.19.2 AI-powered security revolution
- 3.19.3 Zero trust architecture mandates
- 3.19.4 Cloud-native security transformation
- 3.19.5 Privacy regulation explosion
- 3.20 Vendor selection & implementation strategy
- 3.20.1 Advanced vendor evaluation framework
- 3.20.2 Implementation best practices
- 3.20.3 Risk mitigation & management
- 3.21 Market performance & ROI analysis
- 3.21.1 Security investment ROI framework
- 3.21.2 Cost optimization strategies
- 3.21.3 Performance impact assessment
- 3.22 Sustainability and environmental aspects
- 3.22.1 Sustainable practices
- 3.22.2 Waste reduction strategies
- 3.22.3 Energy efficiency in production
- 3.22.4 Eco-friendly initiatives
- 3.22.5 Carbon footprint considerations
Chapter 4 Competitive Landscape, 2024
- 4.1 Introduction
- 4.2 Company market share analysis
- 4.2.1 North America
- 4.2.2 Europe
- 4.2.3 Asia Pacific
- 4.2.4 LATAM
- 4.2.5 MEA
- 4.3 Competitive analysis of major market players
- 4.4 Competitive positioning matrix
- 4.5 Strategic outlook matrix
- 4.6 Key developments
- 4.6.1 Mergers & acquisitions
- 4.6.2 Partnerships & collaborations
- 4.6.3 New product launches
- 4.6.4 Expansion plans and funding
- 4.7 Product portfolio & technology benchmarking
- 4.8 Research & development investment analysis
- 4.9 Market concentration & vendor ecosystem
- 4.10 Distribution channel & partner network analysis
- 4.11 Vendor roadmap alignment assessment
- 4.12 Technology integration complexity matrix
- 4.13 Vendor financial stability assessment
Chapter 5 Market Estimates & Forecast, By Component, 2021 - 2034 ($Mn)
- 5.1 Key trends
- 5.2 Solution
- 5.2.1 Identity and access management (IAM)
- 5.2.2 Firewall & network security
- 5.2.3 Data protection & encryption
- 5.2.4 Security information & event management (SIEM)
- 5.2.5 Endpoint security
- 5.2.6 Cloud security solutions
- 5.3 Services
- 5.3.1 Professional services
- 5.3.1.1 System integration
- 5.3.1.2 Training & consulting
- 5.3.1.3 Support & maintenance
- 5.3.2 Managed services
- 5.3.1 Professional services
Chapter 6 Market Estimates & Forecast, By Organization Size, 2021 - 2034 ($Mn)
- 6.1 Key trends
- 6.2 SME
- 6.3 Large enterprises
Chapter 7 Market Estimates & Forecast, By End Use, 2021 - 2034 ($Mn)
- 7.1 Key trends
- 7.2 BFSI
- 7.3 IT & Telecom
- 7.4 Healthcare
- 7.5 Government & defense
- 7.6 Retail & e-commerce
- 7.7 Others
Chapter 8 Market Estimates & Forecast, By Deployment, 2021 - 2034 ($Mn)
- 8.1 Key trends
- 8.2 On-premises
- 8.3 Cloud-based
Chapter 9 Market Estimates & Forecast, By Region, 2021 - 2034 ($Mn)
- 9.1 Key trends
- 9.2 North America
- 9.2.1 US
- 9.2.2 Canada
- 9.3 Europe
- 9.3.1 Germany
- 9.3.2 UK
- 9.3.3 France
- 9.3.4 Italy
- 9.3.5 Spain
- 9.3.6 Nordics
- 9.3.7 Russia
- 9.4 Asia Pacific
- 9.4.1 China
- 9.4.2 India
- 9.4.3 Japan
- 9.4.4 South Korea
- 9.4.5 ANZ
- 9.4.6 Southeast Asia
- 9.5 Latin America
- 9.5.1 Brazil
- 9.5.2 Mexico
- 9.5.3 Argentina
- 9.6 MEA
- 9.6.1 South Africa
- 9.6.2 Saudi Arabia
- 9.6.3 UAE
Chapter 10 Company Profiles
- 10.1 Global companies
- 10.1.1 Amazon Web Services (AWS)
- 10.1.2 Broadcom
- 10.1.3 Check Point Software Technologies
- 10.1.4 Cisco Systems
- 10.1.5 CrowdStrike
- 10.1.6 Fortinet
- 10.1.7 Google
- 10.1.8 Hewlett Packard Enterprise
- 10.1.9 IBM
- 10.1.10 Juniper
- 10.1.11 Microsoft
- 10.1.12 McAfee
- 10.1.13 Palo Alto Networks
- 10.1.14 Trend Micro
- 10.1.15 Continental
- 10.2 Regional companies
- 10.2.1 Okta
- 10.2.2 Ping Identity
- 10.2.3 Qualys
- 10.2.4 Rapid7
- 10.2.5 SentinelOne
- 10.2.6 Splunk
- 10.2.7 Tenable
- 10.2.8 Varonis Systems
- 10.3 Emerging players
- 10.3.1 Axonius
- 10.3.2 Dynatrace
- 10.3.3 Jit Security
- 10.3.4 Lacework
- 10.3.5 Orca Security
- 10.3.6 Snyk
- 10.3.7 Wiz








