 |
市场调查报告书
商品编码
1889164
全球联网汽车安全市场按应用、电动车类型、配置、安全类型、解决方案类型和地区划分-预测至2032年Connected Car Security Market by Type (Endpoint, Application, Network, Security), Solution (Software & Hardware), Application (TCU, Infotainment, ADAS, Communication Modules), Form (In-vehicle, External Cloud), EV Type & Region - Global Forecast to 2032 |
||||||
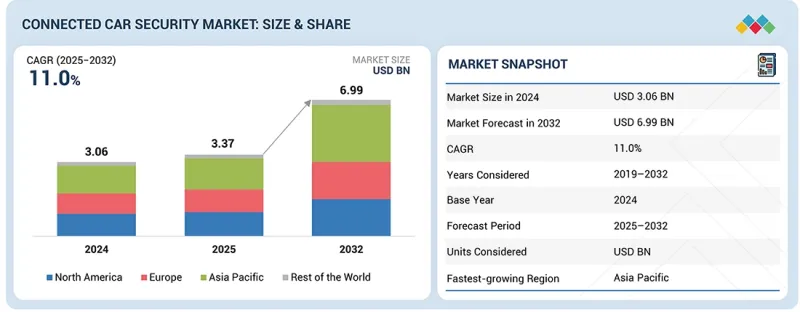
预计到 2025 年,联网汽车安全市场规模将达到 33.7 亿美元,到 2032 年将达到 69.9 亿美元,2025 年至 2032 年的复合年增长率为 11.0%。
市场成长的驱动因素包括软体定义车辆 (SDV)、空中 (OTA) 更新功能、V2X通讯的快速普及,以及针对车辆 ECU、远端资讯处理单元和云端平台的日益增长的网路安全威胁。
| 调查范围 | |
|---|---|
| 调查期 | 2019-2032 |
| 基准年 | 2024 |
| 预测期 | 2025-2032 |
| 目标单元 | 10亿美元 |
| 部分 | 按应用、电动车类型、形式、安全类型、解决方案类型和地区划分 |
| 目标区域 | 亚太地区、欧洲、北美和世界其他地区 |
此外,诸如联合国欧洲经济委员会WP.29 CSMS、ISO/SAE 21434、美国国家公路交通安全管理局网路安全指南以及中国汽车资料安全法规等法规,正迫使汽车製造商采用安全网关、入侵侦测/入侵防御系统(IDS/IPS)、硬体安全模组和加密通讯框架。此外,向电动车的转型以及连网高级驾驶辅助系统(ADAS)功能的普及,也增加了网路安全的复杂性,因此需要对资讯娱乐系统、远端资讯处理系统和自动驾驶系统进行多层保护。亚太地区(尤其是中国)的重大贡献,以及欧洲和北美不断增长的投资,正在加速全球先进联网汽车安全架构的普及。
车载安全解决方案的主导地位源自于电控系统(ECU)、网域控制器和远端资讯处理系统日益复杂的特性,这些系统需要嵌入式保护机制来防止未授权存取和系统篡改。联合国欧洲经济委员会 (UNECE) WP.29、ISO/SAE 21434 以及中国汽车资料安全法规的合规要求,正促使汽车製造商加快在车辆架构中采用安全网关、硬体安全模组 (HSM) 和入侵侦测系统。随着连网高级驾驶辅助系统 (ADAS)、数位驾驶座和车联网 (V2X)通讯在中豪华车型中逐渐成为标配,车载安全已成为保护内部网路、空中下载 (OTA) 软体和资料流的核心防线。这种持续的监管和技术推动,使车载解决方案成为市场中最大的收入来源。
随着产业向防篡改架构转型,硬体解决方案的采用率正在迅速成长。这些架构能够在ECU层面实现安全的资料处理、加密金钥储存和即时威胁防御。诸如TPM、HSM、安全微控制器和加密加速器等组件对于保护安全关键型ADAS系统、高效能运算单元和自动驾驶平台至关重要。针对车辆韧体和通讯汇流排的网路安全威胁日益增多,促使OEM厂商加快采用基于硬体的信任模型,以实现更强大的身份验证和加密。软体定义车辆(SDV)的日益普及以及对安全分区架构的需求进一步推动了这一需求,使得硬体解决方案儘管整合成本高昂,但仍成为成长最快的细分市场。
亚太地区预计将迎来强劲且加速的成长,主要得益于中国、日本、韩国和印度互联自动驾驶出行生态系统的快速发展。中国透过严格执行汽车资料安全法规,强制比亚迪、蔚来、小鹏、捷信和上汽等汽车製造商采用加密车载通讯、安全OTA平台以及嵌入式入侵侦测/防御系统(IDS/IPS)解决方案,从而推动了这一成长势头。日本和韩国正根据联合国欧洲经济委员会(UNECE)WP.29网路安全管理系统(CSMS)框架推进相关实施,并拥有强大的车载资讯服务网路和覆盖高端及大众市场的高联网汽车渗透率。电动车的快速普及、5G的大力部署以及政府主导的网路安全合规措施,持续创造着巨大的新商机,使亚太地区成为联网汽车安全市场成长最快的地区。
- By Company Type::OEMs-10% and Tier 1 Companies-90%
- By Designation::C-Level Executive-60%;Director-Level-30%;Others-10%
- By Region::North America-40%;Europe-50%;and Asia Pacific-10%
註:其他职位包括销售经理和产品经理。
联网汽车安全市场由NXP Semiconductors(荷兰)、AUMOVIO SE(德国)、Harman International(美国)、Vector Informatik GmbH(德国)、BlackBerry Limited(加拿大)、Thales(法国)、ARM Limited(英国)、WirelessCar(瑞典)、Astemo Ltd.(日本)和Keysight Technologies(美国)公司等主要製造商的安全厂商正在巩固汽车组合商(日本)和Keysight Technologies公司正在巩固其安全厂商(联网汽车正在巩固其安全厂商。
调查对象
本报告按安全类型(端点安全、应用安全、网路安全、云端安全)、应用(车载资讯控制单元 (TCU)、资讯娱乐系统、高级驾驶辅助系统 (ADAS) 和自动驾驶系统、通讯模组)、电动车类型(纯电动车 (BEV)、插电式混合动力汽车 (PHEV)、燃料电池电动车(FCEV))、解决方案类型(软体解决方案、硬体解决方案)、形式(车载解决方案、外部云端服务)和地区(北美、亚太、欧洲、世界其他地区)分析了连网汽车安全市场。报告涵盖了主要联网汽车安全市场中的竞争格局和主要企业的公司概况。
该研究还涵盖了对主要市场参与者的详细竞争分析、公司简介、对产品和业务供应的关键观察、近期发展和关键市场策略。
购买本报告的主要优势:
- 本报告提供了有关联网汽车安全市场及其细分市场收入数据的最佳近似信息,有助于市场领导和新参与企业。
- 本报告将帮助相关利益者了解竞争格局,并获得更深入的见解,从而更好地定位其业务并制定适当的打入市场策略。
- 它还有助于相关人员了解市场趋势,并提供有关关键市场驱动因素、限制、挑战和机会的资讯。
- 该报告还将帮助相关人员更好地了解联网汽车安全市场当前和未来的定价趋势。
该报告还深入分析了以下内容:
- 对关键驱动因素(透过远端资讯处理和V2X技术提高车辆互联性、强制遵守全球汽车网路安全法规、联网汽车和自动驾驶车辆遭受的网路攻击日益增多)、阻碍因素(传统ECU和车辆架构增加了安全升级的复杂性、实施和整合成本高昂)、机会(资安管理服务和车辆SOC的成长、对安全OTA和生命週期管理的需求不断增长、V2X和5G网路需要强大的基于PKI的安全保障)以及挑战(不断演变的网路威胁、在不损害安全关键功能的前提下最大限度地减少误报)的分析
- 产品开发/创新:深入分析联网汽车安全市场即将出现的技术趋势、研发活动以及产品和服务发布。
- 市场开发:提供不同地区盈利市场的全面讯息
- 市场多元化:提供联网汽车安全市场的新产品和服务、前沿地区、最新趋势和投资的全面资讯。
- 竞争评估:对连网汽车安全市场的主要企业(如 NXP Semiconductors(荷兰)、AUMOVIO SE(德国)、Harman International(美国)、Vector Informatik GmbH(美国)、BlackBerry Limited(加拿大)、Thales(法国)、ARM 主要企业 (英国)、WirelessCar(瑞典)、Astemos Ltd Technologies(瑞典市场)和美国市场成长率的联网汽车市场份额(瑞典)和美国市场份额(瑞典市场)。
目录
第一章 引言
第二章调查方法
第三章执行摘要
第四章重要考察
第五章 市场概览
- 市场动态
- 未满足的需求和差距
- 相互关联的市场与跨产业机会
- 一级/二级/三级公司的策略性倡议
第六章 产业趋势
- 波特五力分析
- 宏观经济展望
- 供应链分析
- 生态系分析
- 定价分析
- 贸易分析
- 2025-2026 年主要会议和活动
- 影响客户业务的趋势/干扰因素
- 投资和资金筹措方案
- 案例研究分析
- 美国2025年关税
第七章:顾客状况与购买行为
- 决策流程
- 买方相关人员和采购评估标准
- 招募障碍和内部挑战
- 各个终端用户产业尚未满足的需求
- 市场盈利
- 获利潜力
- 成本动态
- 关键应用领域的利润机会
第八章:科技、专利、数位化和人工智慧应用带来的策略颠覆
- 专利分析
- 生成式人工智慧将如何影响联网汽车安全市场
- 关键新兴技术
- 互补技术
- 技术/产品蓝图
- 联网汽车市场中OEM厂商的技术开发
第九章:监理环境
- 监管状态
- 地方法规
第十章联网汽车安全市场(按应用领域划分)
- 车载资讯控制单元(TCUS)
- 资讯娱乐系统
- 进阶驾驶辅助系统与自动驾驶系统
- 通讯模组
第十一章联网汽车安全市场(以电动车类型划分)
- 电动车
- PHEV
- 混合动力汽车
- 燃料电池汽车
第十二章联网汽车安全市场(按类型划分)
- 车载解决方案
- 外部云端服务
第十三章联网汽车安全市场(依安全类型划分)
- 端点安全
- 应用程式安全
- 网路安全
- 云端安全
第十四章联网汽车安全市场(依解决方案类型划分)
- 基于软体的解决方案
- 基于硬体的解决方案
第十五章联网汽车安全市场(按地区划分)
- 亚太地区
- 亚太地区:宏观经济展望
- 中国
- 日本
- 印度
- 韩国
- 其他的
- 欧洲
- 欧洲:宏观经济展望
- 英国
- 德国
- 法国
- 西班牙
- 义大利
- 其他的
- 北美洲
- 北美:宏观经济展望
- 美国
- 加拿大
- 墨西哥
- 其他地区
- 世界其他地区:宏观经济展望
- 伊朗
- 南非
第十六章 竞争格局
- 主要参与企业的策略/优势,2022-2024 年
- 2024年市占率分析
- 2020-2024年收入分析
- 品牌对比
- 估值和财务指标
- 公司估值矩阵:主要参与企业,2024 年
- 公司估值矩阵:Start-Ups/中小企业,2024 年
- 竞争场景
第十七章:公司简介
- 主要参与企业
- AUMOVIO SE
- BLACKBERRY LIMITED
- VECTOR INFORMATIK GMBH
- NXP SEMICONDUCTORS
- HARMAN INTERNATIONAL
- UPSTREAM SECURITY LTD.
- ASTEMO, LTD.
- TRUSTONIC
- KPIT
- THALES
- T-SYSTEMS INTERNATIONAL GMBH
- AUTOCRYPT CO., LTD.
- 其他公司
- ARM LIMITED
- TREND MICRO INCORPORATED
- ETAS
- KEYSIGHT TECHNOLOGIES
- INTERTEK GROUP PLC
- DEVICE AUTHORITY
- SECUNET SECURITY NETWORKS AG
- TRILLIUM SECURE, INC.
- WIRELESSCAR
- KARAMBA SECURITY
- INTERTRUST TECHNOLOGIES CORPORATION
- GUARDKNOX
- TATA ELXSI
第十八章附录
The connected car security market is projected to grow from USD 3.37 billion in 2025 to reach USD 6.99 billion by 2032, at a CAGR of 11.0% from 2025 to 2032. Market growth is driven by the rapid expansion of software-defined vehicles (SDVs), over-the-air (OTA) update capabilities, V2X communication, and the rising cybersecurity threats targeting vehicle ECUs, telematics units, and cloud platforms.
| Scope of the Report | |
|---|---|
| Years Considered for the Study | 2019-2032 |
| Base Year | 2024 |
| Forecast Period | 2025-2032 |
| Units Considered | USD Billion |
| Segments | Type, Solution, Application, Form, EV Type & Region |
| Regions covered | Asia Pacific, Europe, North America, Rest of the World |
Additionally, regulations such as UNECE WP.29 CSMS, ISO/SAE 21434, the US NHTSA cybersecurity guidelines, and China's Automotive Data Security Regulations are pushing automakers to adopt secure gateways, IDS/IPS, hardware-secured modules, and encrypted communication frameworks. Moreover, the shift toward electric vehicles and connected ADAS features increases cybersecurity complexity, requiring multi-layer protection for infotainment, telematics, and autonomous driving stacks. Substantial contributions from the Asia Pacific region, especially China, combined with increasing investments from Europe and North America, are accelerating the global adoption of advanced connected car security architectures.

"By form, the in-vehicle solutions segment is projected to account for a larger share than the external cloud services segment during the forecast period."
The dominance of in-vehicle security solutions is driven by the rising complexity of electronic control units (ECUs), domain controllers, and telematics systems, which require embedded protection to prevent unauthorized access and system manipulation. Compliance mandates under UNECE WP.29, ISO/SAE 21434, and China's Automotive Data Security Regulations have accelerated OEM adoption of secure gateways, hardware security modules (HSMs), and intrusion detection systems inside the vehicle architecture. As connected ADAS, digital cockpits, and V2X communication become standard across mid-range and premium models, in-vehicle security becomes the core protection layer for safeguarding internal networks, OTA software, and data flows. This sustained regulatory and technological push positions in-vehicle solutions as the largest revenue-generating segment in the market.
"By solution type, the hardware-based solutions segment is projected to be a faster-growing segment than the software-based segment during the forecast period."
The use of hardware-based solutions is expanding rapidly due to the industry's shift toward tamper-resistant architectures that ensure secure data processing, cryptographic key storage, and real-time threat mitigation at the ECU level. Components such as TPMs, HSMs, secure microcontrollers, and cryptographic accelerators are becoming essential for protecting safety-critical ADAS systems, high-performance computing units, and autonomous driving platforms. With rising cybersecurity threats targeting vehicle firmware and communication buses, OEMs are increasingly adopting hardware-rooted trust models for stronger authentication and encryption. Growing SDV adoption and the need for secured zonal architectures further accelerate demand, making hardware-based solutions the fastest-growing segment despite higher integration costs.
"Asia Pacific is projected to be the fastest-growing segment in the global connected car security market during the forecast period."
Asia Pacific is projected to witness strong and accelerating growth driven by the rapid expansion of connected and autonomous mobility ecosystems in China, Japan, South Korea, and India. China is leading this momentum through the strict enforcement of the automotive data security regulations, compelling OEMs such as BYD, NIO, XPeng, Zeekr, and SAIC to adopt encrypted in-vehicle communication, secure OTA platforms, and embedded IDS/IPS solutions. Japan and South Korea are advancing deployments in line with UNECE WP.29 CSMS frameworks, supported by robust telematics networks and high connected car penetration across both luxury and mass-market segments. With rapid EV adoption, strong 5G rollout, and government-led cybersecurity compliance, Asia Pacific continues to generate significant new revenue opportunities, making it the fastest-growing region in the connected car security market.
In-depth interviews were conducted with CEOs, marketing directors, other innovation and technology directors, and executives from various key organizations operating in this market.
- By Company Type: OEMs - 10% and Tier 1 Companies - 90%
- By Designation: C-Level Executive - 60%; Director-Level - 30%; Others - 10%
- By Region: North America - 40%; Europe - 50%; and Asia Pacific - 10%
Note: Others include Sales Managers and Product Managers.
The connected car security market is dominated by major players, such as NXP Semiconductors (Netherlands), AUMOVIO SE (Germany), Harman International (US), Vector Informatik GmbH (Germany), BlackBerry Limited (Canada), Thales (France), ARM Limited (UK), WirelessCar (Sweden), Astemo Ltd. (Japan), and Keysight Technologies (US.) These companies are expanding their portfolios to strengthen their connected car security market position.
Research Coverage
The report covers the connected car security market in terms of security type (Endpoint Security, Application Security, Network Security, and Cloud Security), application [Telematics Control Units (TCUs), Infotainment Systems, ADAS & Autonomous Driving Systems, and Communication Modules], electric vehicle type (BEV, PHEV, HEV, and FCEV), solution type (Software-based Solutions and Hardware-based Solutions), form (In-Vehicle Solutions and External Cloud Services), and Region (North America, Asia Pacific, Europe, and Rest of the World). It covers the competitive landscape and company profiles of the key players in the significant connected car security market.
The study also includes an in-depth competitive analysis of the key market players, their company profiles, key observations related to product and business offerings, recent developments, and key market strategies.
Key Benefits of Buying the Report:
- The report will help market leaders/new entrants with information on the closest approximations of revenue numbers for the connected car security market and its subsegments.
- This report will help stakeholders understand the competitive landscape and gain more insights, enabling them to position their businesses better and plan suitable go-to-market strategies.
- The report will also help stakeholders understand the market pulse and provide information on key market drivers, restraints, challenges, and opportunities.
- The report will also help stakeholders understand the current and future pricing trends of the connected car security market.
The report also provides insights into the following pointers:
- Analysis of key drivers (Increasing vehicle connectivity through telematics and V2X, mandatory compliance with global automotive cybersecurity regulations, and rising cyberattacks on connected and autonomous vehicles), restraints (Legacy ECU and vehicle architectures complicate security upgrades and high implementation and integration costs), opportunities (Growth of managed security services and vehicle SOCs, rising demand for secure OTA and lifecycle management, and V2X and 5G networks requiring strong PKI-based security), and challenges (Evolving cyber threats and minimizing false positives without compromising safety-critical functions)
- Product Developments/Innovation: Detailed insights into upcoming technologies, research & development activities, and product & service launches in the connected car security market.
- Market Development: Comprehensive information about lucrative markets across varied regions
- Market Diversification: Exhaustive information about new products & services, untapped geographies, recent developments, and investments in the connected car security market
- Competitive Assessment: In-depth assessment of market share, growth strategies, and service offerings of leading players like as NXP Semiconductors (Netherlands), AUMOVIO SE (Germany), Harman International (US), Vector Informatik GmbH (Germany), BlackBerry Limited (Canada), Thales (France), ARM Limited (UK), WirelessCar (Sweden), Astemo Ltd. (Japan), and Keysight Technologies (US), among others, in connected car security market
TABLE OF CONTENTS
1 INTRODUCTION
- 1.1 STUDY OBJECTIVES
- 1.2 MARKET DEFINITION
- 1.3 STUDY SCOPE
- 1.3.1 MARKET SEGMENTATION & REGIONAL SCOPE
- 1.3.2 INCLUSIONS & EXCLUSIONS
- 1.4 YEARS CONSIDERED
- 1.5 CURRENCY CONSIDERED
- 1.6 STAKEHOLDERS
2 RESEARCH METHODOLOGY
- 2.1 RESEARCH DATA
- 2.1.1 SECONDARY DATA
- 2.1.1.1 Key secondary sources
- 2.1.1.2 Key data from secondary sources
- 2.1.2 PRIMARY DATA
- 2.1.2.1 Primary participants
- 2.1.2.2 Key industry insights
- 2.1.1 SECONDARY DATA
- 2.2 MARKET BREAKDOWN & DATA TRIANGULATION
- 2.3 MARKET SIZE ESTIMATION
- 2.3.1 TOP-DOWN APPROACH
- 2.4 MARKET FORECAST
- 2.5 RESEARCH ASSUMPTIONS
- 2.6 RESEARCH LIMITATIONS
3 EXECUTIVE SUMMARY
- 3.1 KEY INSIGHTS AND MARKET HIGHLIGHTS
- 3.2 KEY MARKET PARTICIPANTS: SHARED INSIGHTS AND STRATEGIC DEVELOPMENTS
- 3.3 DISRUPTIVE TRENDS SHAPING MARKET
- 3.4 HIGH-GROWTH SEGMENTS AND EMERGING FRONTIERS
- 3.5 SNAPSHOT: GLOBAL MARKET SIZE, GROWTH RATE, AND FORECAST
4 PREMIUM INSIGHTS
- 4.1 ATTRACTIVE OPPORTUNITIES FOR PLAYERS IN CONNECTED CAR SECURITY MARKET
- 4.2 CONNECTED CAR SECURITY MARKET, BY SECURITY TYPE
- 4.3 CONNECTED CAR SECURITY MARKET, BY ELECTRIC VEHICLE TYPE
- 4.4 CONNECTED CAR SECURITY MARKET, BY FORM
- 4.5 CONNECTED CAR SECURITY MARKET, BY APPLICATION
- 4.6 CONNECTED CAR SECURITY MARKET, BY SOLUTION TYPE
- 4.7 CONNECTED CAR SECURITY MARKET, BY REGION
5 MARKET OVERVIEW
- 5.1 INTRODUCTION
- 5.2 MARKET DYNAMICS
- 5.2.1 DRIVERS
- 5.2.1.1 Increasing vehicle connectivity through telematic and V2X
- 5.2.1.2 Mandatory compliance with global automotive cybersecurity regulations
- 5.2.1.3 Rising cyberattacks on connected and autonomous vehicles
- 5.2.2 RESTRAINTS
- 5.2.2.1 Legacy ECU and vehicle architectures complicating security upgrades
- 5.2.2.2 High implementation and integration costs
- 5.2.3 OPPORTUNITIES
- 5.2.3.1 Growth of managed security services and vehicle SOCs
- 5.2.3.2 Rising demand for secure OTA and lifecycle management
- 5.2.3.3 V2X and 5G networks require strong PKI-based security
- 5.2.4 CHALLENGES
- 5.2.4.1 Evolving cyber threats hindering long-term protection
- 5.2.4.2 Minimizing false positives without compromising safety-critical functions
- 5.2.1 DRIVERS
- 5.3 UNMET NEEDS AND WHITE SPACES
- 5.3.1 UNMET NEEDS IN CONNECTED CAR SECURITY MARKET
- 5.3.2 WHITE SPACE OPPORTUNITIES
- 5.4 INTERCONNECTED MARKETS AND CROSS-SECTOR OPPORTUNITIES
- 5.4.1 INTERCONNECTED MARKETS
- 5.4.2 CROSS-SECTOR OPPORTUNITIES
- 5.5 STRATEGIC MOVES BY TIER 1/2/3 PLAYERS
- 5.5.1 KEY MOVES AND STRATEGIC FOCUS
6 INDUSTRY TRENDS
- 6.1 PORTER'S FIVE FORCES ANALYSIS
- 6.1.1 THREAT FROM NEW ENTRANTS
- 6.1.2 THREAT FROM SUBSTITUTES
- 6.1.3 BARGAINING POWER OF SUPPLIERS
- 6.1.4 BARGAINING POWER OF BUYERS
- 6.1.5 INTENSITY OF COMPETITIVE RIVALRY
- 6.2 MACROECONOMIC OUTLOOK
- 6.2.1 INTRODUCTION
- 6.2.2 GDP TRENDS AND FORECAST
- 6.2.3 TRENDS IN GLOBAL CONNECTED CAR INDUSTRY
- 6.2.3.1 Transition toward software-defined vehicle era
- 6.2.3.2 Connectivity as enabler of autonomous mobility
- 6.2.3.3 Vehicle-to-everything (V2X) to build foundation for smart mobility
- 6.2.3.4 Evolution of vehicle architecture in software-driven era
- 6.2.3.5 Personalization and connected experiences in modern mobility
- 6.2.4 TRENDS IN GLOBAL AUTOMOTIVE & TRANSPORTATION INDUSTRY
- 6.2.4.1 Rapid but uneven EV adoption and market share gains
- 6.2.4.2 Battery pack cost decline and cell supply overcapacity reshaping economics
- 6.2.4.3 Heavy-duty and commercial electrification (plus selective hydrogen use) accelerating heterogeneously
- 6.2.4.4 ADAS proliferation and measured progress toward high autonomy and rise of pilot robotaxi deployment
- 6.2.4.5 Semiconductor cycles, supply resilience, and industrial policy reshaping auto supply chains
- 6.3 SUPPLY CHAIN ANALYSIS
- 6.4 ECOSYSTEM ANALYSIS
- 6.5 PRICING ANALYSIS
- 6.5.1 INDICATIVE PRICING, BY APPLICATION
- 6.5.2 INDICATIVE PRICING, BY SECURITY TYPE
- 6.5.3 INDICATIVE PRICING, BY REGION
- 6.6 TRADE ANALYSIS
- 6.6.1 IMPORT SCENARIO
- 6.6.2 EXPORT SCENARIO
- 6.7 KEY CONFERENCES & EVENTS, 2025-2026
- 6.8 TRENDS/DISRUPTIONS IMPACTING CUSTOMER BUSINESS
- 6.9 INVESTMENT & FUNDING SCENARIO
- 6.10 CASE STUDY ANALYSIS
- 6.10.1 CONTINENTAL DEVELOPED IN-VEHICLE CYBERSECURITY FRAMEWORK TO PROTECT CONNECTED ECUS AND SECURE DATA EXCHANGE
- 6.10.2 BOSCH IMPLEMENTED SECURE GATEWAY MODULE TO CONTROL EXTERNAL ACCESS AND STRENGTHEN VEHICLE COMMUNICATION SECURITY
- 6.10.3 HARMAN ENABLED CLOUD-BASED THREAT DETECTION TO MONITOR AND MITIGATE CYBER RISKS IN CONNECTED VEHICLE FLEETS
- 6.10.4 APTIV DEPLOYED END-TO-END CYBERSECURITY ARCHITECTURE TO SAFEGUARD OVER-THE-AIR UPDATES AND DATA TRANSFER
- 6.10.5 NXP INTRODUCED AUTOMOTIVE HARDWARE SECURITY MODULES TO ENCRYPT DATA AND ENSURE SECURE ECU COMMUNICATION
- 6.10.6 UPSTREAM SECURED VEHICLE FLEET OPERATIONS USING CLOUD ANALYTICS FOR THREAT DETECTION AND INCIDENT RESPONSE
- 6.10.7 ARGUS DEVELOPED NETWORK INTRUSION DETECTION AND PREVENTION SYSTEMS TO IDENTIFY AND BLOCK MALICIOUS TRAFFIC
- 6.10.8 BLACKBERRY QNX PROVIDED SECURE OPERATING SYSTEM FOUNDATION TO SUPPORT SAFETY-CRITICAL AUTOMOTIVE SOFTWARE
- 6.11 US 2025 TARIFF
- 6.11.1 INTRODUCTION
- 6.11.2 KEY TARIFF RATES
- 6.11.2.1 Key product-related tariffs
- 6.11.3 PRICE IMPACT ANALYSIS
- 6.11.4 IMPACT ON COUNTRY/REGION
- 6.11.4.1 US
- 6.11.4.2 Europe
- 6.11.4.3 Asia Pacific
- 6.11.5 IMPACT ON END-USE INDUSTRIES
7 CUSTOMER LANDSCAPE AND BUYER BEHAVIOR
- 7.1 DECISION-MAKING PROCESS
- 7.2 BUYER STAKEHOLDERS AND BUYING EVALUATION CRITERIA
- 7.2.1 KEY STAKEHOLDERS IN BUYING PROCESS
- 7.2.2 BUYING CRITERIA
- 7.3 ADOPTION BARRIERS AND INTERNAL CHALLENGES
- 7.4 UNMET NEEDS IN VARIOUS END-USER INDUSTRIES
- 7.5 MARKET PROFITABILITY
- 7.6 REVENUE POTENTIAL
- 7.7 COST DYNAMICS
- 7.8 MARGIN OPPORTUNITIES IN KEY APPLICATIONS
8 STRATEGIC DISRUPTION THROUGH TECHNOLOGY, PATENTS, DIGITAL, AND AI ADOPTION
- 8.1 PATENT ANALYSIS
- 8.1.1 INTRODUCTION
- 8.1.2 LIST OF PATENTS GRANTED TO LG ELECTRONICS
- 8.1.3 LIST OF PATENTS GRANTED TO INTEL CORPORATION
- 8.1.4 LIST OF PATENTS GRANTED TO SAMSUNG ELECTRONICS
- 8.2 IMPACT OF GENERATIVE AI ON CONNECTED CAR SECURITY MARKET
- 8.3 KEY EMERGING TECHNOLOGIES
- 8.3.1 VEHICLE SECURITY OPERATIONS CENTERS (VSOCS)
- 8.3.2 INTRUSION DETECTION & PREVENTION SYSTEMS
- 8.3.3 SECURE COMMUNICATION PROTOCOLS
- 8.3.4 ENCRYPTION & CRYPTOGRAPHY
- 8.3.5 HARDWARE SECURITY MODULES (HSMS)
- 8.3.6 TRUSTED PLATFORM MODULES (TPMS)
- 8.3.7 IDENTITY & ACCESS MANAGEMENT (IAM)
- 8.4 COMPLEMENTARY TECHNOLOGIES
- 8.4.1 CLOUD & EDGE-BASED VEHICLE SECURITY
- 8.4.2 AI-/ML-DRIVEN INTRUSION DETECTION & RESPONSE
- 8.4.3 BLOCKCHAIN FOR V2X AND DATA INTEGRITY
- 8.4.4 BIOMETRIC AUTHENTICATION FOR DRIVER & VEHICLE ACCESS
- 8.5 TECHNOLOGY/PRODUCT ROADMAP
- 8.5.1 SHORT-TERM (2025-2027): FOUNDATION & EARLY COMMERCIALIZATION
- 8.5.2 MID-TERM (2027-2030): EXPANSION & STANDARDIZATION
- 8.5.3 LONG-TERM (2030 ONWARDS): MASS COMMERCIALIZATION & DISRUPTION
- 8.6 TECHNOLOGICAL DEVELOPMENTS IN CONNECTED CAR MARKET, BY OEM
9 REGULATORY LANDSCAPE
- 9.1 REGULATORY LANDSCAPE
- 9.1.1 REGULATORY BODIES, GOVERNMENT AGENCIES, AND OTHER ORGANIZATIONS
- 9.2 REGULATIONS, BY REGION
- 9.2.1 NORTH AMERICA
- 9.2.2 EUROPE
- 9.2.3 ASIA PACIFIC
10 CONNECTED CAR SECURITY MARKET, BY APPLICATION
- 10.1 INTRODUCTION
- 10.2 TELEMATICS CONTROL UNITS (TCUS)
- 10.2.1 GROWING INTEGRATION OF CONNECTED SERVICES AND REAL-TIME VEHICLE MONITORING TO DRIVE MARKET
- 10.3 INFOTAINMENT SYSTEMS
- 10.3.1 GROWING COMPLEXITY OF INFOTAINMENT ARCHITECTURES TO DRIVE MARKET
- 10.4 ADAS & AUTONOMOUS DRIVING SYSTEMS
- 10.4.1 NEED FOR STRENGTHENING CYBERSECURITY FOR ADAS AND AUTONOMOUS DRIVING SYSTEMS TO BOOST MARKET
- 10.5 COMMUNICATION MODULES
- 10.5.1 GROWING ADOPTION OF OVER-THE-AIR UPDATES, REMOTE DIAGNOSTICS, PREDICTIVE MAINTENANCE, AND CONNECTED-SERVICE PLATFORMS TO DRIVE MARKET
11 CONNECTED CAR SECURITY MARKET, BY ELECTRIC VEHICLE TYPE
- 11.1 INTRODUCTION
- 11.2 BEV
- 11.2.1 STRONG ENDPOINT PROTECTION AND SECURE COMMUNICATION FRAMEWORKS IN BEVS TO DRIVE MARKET
- 11.3 PHEV
- 11.3.1 EXPANDING SOFTWARE DEPENDENCIES INCREASING CYBERSECURITY EXPOSURE TO DRIVE MARKET
- 11.4 HEV
- 11.4.1 FOCUS ON SAFEGUARDING VEHICLE-TO-VEHICLE AND VEHICLE-TO-INFRASTRUCTURE CHANNELS TO BOOST MARKET
- 11.5 FCEV
- 11.5.1 RELIANCE OF FCEVS ON CLOUD-BASED INFRASTRUCTURE TO BOOST MARKET
12 CONNECTED CAR SECURITY MARKET, BY FORM
- 12.1 INTRODUCTION
- 12.2 IN-VEHICLE SOLUTIONS
- 12.2.1 RAPIDLY ADOPTING ADVANCED ENDPOINT PROTECTION, INTRUSION DETECTION, SECURE UPDATES, AND RESILIENT COMMUNICATION FRAMEWORKS TO DRIVE MARKET
- 12.3 EXTERNAL CLOUD SERVICES
- 12.3.1 INCREASING RELIANCE OF VEHICLES ON ELECTRONIC CONTROL UNITS AND TELEMATICS TO DRIVE MARKET
13 CONNECTED CAR SECURITY MARKET, BY SECURITY TYPE
- 13.1 INTRODUCTION
- 13.2 ENDPOINT SECURITY
- 13.2.1 FOCUS ON DEVICE AUTHENTICATION, INTRUSION DETECTION, ENCRYPTION, AND DATA INTEGRITY TO BOOST MARKET
- 13.3 APPLICATION SECURITY
- 13.3.1 NEED FOR SECURING APPLICATIONS AGAINST DATA BREACHES TO DRIVE MARKET
- 13.4 NETWORK SECURITY
- 13.4.1 NEED FOR INTEGRATION OF ADVANCED ENCRYPTION, INTRUSION DETECTION SYSTEMS, AND SECURE GATEWAYS TO BOOST MARKET
- 13.5 CLOUD SECURITY
- 13.5.1 INCREASED RELIANCE OF CONNECTED VEHICLES ON CLOUD FOR OTA UPDATES AND REAL-TIME NAVIGATION TO DRIVE MARKET
14 CONNECTED CAR SECURITY MARKET, BY SOLUTION TYPE
- 14.1 INTRODUCTION
- 14.2 SOFTWARE-BASED SOLUTIONS
- 14.2.1 POPULARITY OF TELEMATICS, CLOUD CONNECTIVITY, ADAS, AND V2X COMMUNICATION TO BOOST GROWTH
- 14.3 HARDWARE-BASED SOLUTIONS
- 14.3.1 NEED FOR PREVENTING UNAUTHORIZED ACCESS, TAMPERING, AND SYSTEM MANIPULATION TO BOOST MARKET
15 CONNECTED CAR SECURITY MARKET, BY REGION
- 15.1 INTRODUCTION
- 15.2 ASIA PACIFIC
- 15.2.1 ASIA PACIFIC: MACROECONOMIC OUTLOOK
- 15.2.2 CHINA
- 15.2.2.1 Enforcement of stringent data rules for connected vehicles to drive market
- 15.2.3 JAPAN
- 15.2.3.1 Focus on strengthening connected car security amid digital shift to boost market
- 15.2.4 INDIA
- 15.2.4.1 Need for fast-track cybersecurity compliance for connected mobility to boost demand
- 15.2.5 SOUTH KOREA
- 15.2.5.1 Emphasis on enforcing stringent data rules for connected vehicles to boost market
- 15.2.6 REST OF ASIA PACIFIC
- 15.3 EUROPE
- 15.3.1 EUROPE: MACROECONOMIC OUTLOOK
- 15.3.2 UK
- 15.3.2.1 Need for new cybersecurity standards for connected vehicles to boost market
- 15.3.3 GERMANY
- 15.3.3.1 Focus on enforcing CSMS & SUMS compliance for new vehicles to drive market
- 15.3.4 FRANCE
- 15.3.4.1 Stringent enforcement of UNECE cybersecurity requirements to boost market
- 15.3.5 SPAIN
- 15.3.5.1 Innovation and rapid technological advancements to drive market
- 15.3.6 ITALY
- 15.3.6.1 Need for accelerating cybersecurity integration in smart mobility to drive market
- 15.3.7 REST OF EUROPE
- 15.4 NORTH AMERICA
- 15.4.1 NORTH AMERICA: MACROECONOMIC OUTLOOK
- 15.4.2 US
- 15.4.2.1 Focus on strengthening national security rules to drive market
- 15.4.3 CANADA
- 15.4.3.1 Need for advancing security of connected vehicles through comprehensive guidance to boost market
- 15.4.4 MEXICO
- 15.4.4.1 Awareness regarding critical importance of cybersecurity in automotive industry to drive market
- 15.5 REST OF THE WORLD
- 15.5.1 REST OF THE WORLD: MACROECONOMIC OUTLOOK
- 15.5.2 IRAN
- 15.5.2.1 Focus on secure connectivity to drive demand
- 15.5.3 SOUTH AFRICA
- 15.5.3.1 Rising adoption of connected mobility to drive market
16 COMPETITIVE LANDSCAPE
- 16.1 KEY PLAYER STRATEGIES/RIGHT TO WIN, 2022-2024
- 16.2 MARKET SHARE ANALYSIS, 2024
- 16.3 REVENUE ANALYSIS, 2020-2024
- 16.4 BRAND COMPARISON
- 16.5 COMPANY VALUATION AND FINANCIAL METRICS
- 16.6 COMPANY EVALUATION MATRIX: KEY PLAYERS, 2024
- 16.6.1 STARS
- 16.6.2 EMERGING LEADERS
- 16.6.3 PERVASIVE PLAYERS
- 16.6.4 PARTICIPANTS
- 16.6.5 COMPANY FOOTPRINT: KEY PLAYERS, 2024
- 16.6.5.1 Company footprint
- 16.6.5.2 Region footprint
- 16.6.5.3 Solution type footprint
- 16.6.5.4 Security type footprint
- 16.7 COMPANY EVALUATION MATRIX: STARTUPS/SMES, 2024
- 16.7.1 PROGRESSIVE COMPANIES
- 16.7.2 RESPONSIVE COMPANIES
- 16.7.3 DYNAMIC COMPANIES
- 16.7.4 STARTING BLOCKS
- 16.7.5 COMPETITIVE BENCHMARKING: STARTUPS/SMES, 2024
- 16.7.5.1 Detailed list of key startups/SMEs
- 16.7.5.2 Competitive benchmarking of key startups/SMEs
- 16.8 COMPETITIVE SCENARIO
- 16.8.1 PRODUCT LAUNCHES/ENHANCEMENTS
- 16.8.2 DEALS
17 COMPANY PROFILES
- 17.1 KEY PLAYERS
- 17.1.1 AUMOVIO SE
- 17.1.1.1 Business overview
- 17.1.1.2 Products/Solutions/Services offered
- 17.1.1.3 Recent developments
- 17.1.1.3.1 Product launches/enhancements
- 17.1.1.3.2 Deals
- 17.1.1.3.3 Expansion
- 17.1.1.4 MnM view
- 17.1.1.4.1 Key strengths
- 17.1.1.4.2 Strategic choices
- 17.1.1.4.3 Weaknesses and competitive threats
- 17.1.2 BLACKBERRY LIMITED
- 17.1.2.1 Business overview
- 17.1.2.2 Products/Solutions/Services offered
- 17.1.2.3 Recent developments
- 17.1.2.3.1 Product launches/enhancements
- 17.1.2.3.2 Deals
- 17.1.2.4 MnM view
- 17.1.2.4.1 Key strengths
- 17.1.2.4.2 Strategic choices
- 17.1.2.4.3 Weaknesses & competitive threats
- 17.1.3 VECTOR INFORMATIK GMBH
- 17.1.3.1 Business overview
- 17.1.3.2 Products/Solutions/Services offered
- 17.1.3.3 Recent developments
- 17.1.3.3.1 Product launches/enhancements
- 17.1.3.3.2 Deals
- 17.1.3.4 MnM view
- 17.1.3.4.1 Key strengths
- 17.1.3.4.2 Strategic choices
- 17.1.3.4.3 Weaknesses and competitive threats
- 17.1.4 NXP SEMICONDUCTORS
- 17.1.4.1 Business overview
- 17.1.4.2 Products/Solutions/Services offered
- 17.1.4.3 Recent developments
- 17.1.4.3.1 Deals
- 17.1.4.4 MnM view
- 17.1.4.4.1 Key strengths
- 17.1.4.4.2 Strategic choices
- 17.1.4.4.3 Weaknesses and competitive threats
- 17.1.5 HARMAN INTERNATIONAL
- 17.1.5.1 Business overview
- 17.1.5.2 Products/Solutions/Services offered
- 17.1.5.3 Recent developments
- 17.1.5.3.1 Deals
- 17.1.5.4 MnM view
- 17.1.5.4.1 Key strengths
- 17.1.5.4.2 Strategic choices
- 17.1.5.4.3 Weaknesses and competitive threats
- 17.1.6 UPSTREAM SECURITY LTD.
- 17.1.6.1 Business overview
- 17.1.6.2 Products/Solutions/Services offered
- 17.1.6.3 Recent developments
- 17.1.6.3.1 Product launches/enhancements
- 17.1.6.3.2 Deals
- 17.1.7 ASTEMO, LTD.
- 17.1.7.1 Business overview
- 17.1.7.2 Products/Solutions/Services offered
- 17.1.7.3 Recent developments
- 17.1.7.3.1 Deals
- 17.1.7.3.2 Expansion
- 17.1.8 TRUSTONIC
- 17.1.8.1 Business overview
- 17.1.8.2 Products/Solutions/Services offered
- 17.1.8.3 Recent developments
- 17.1.8.3.1 Product launches/enhancements
- 17.1.8.3.2 Deals
- 17.1.9 KPIT
- 17.1.9.1 Business overview
- 17.1.9.2 Products/Solutions/Services offered
- 17.1.9.3 Recent developments
- 17.1.9.3.1 Deals
- 17.1.10 THALES
- 17.1.10.1 Business overview
- 17.1.10.2 Products/Solutions/Services offered
- 17.1.10.3 Recent developments
- 17.1.10.3.1 Product launches/enhancements
- 17.1.10.3.2 Deals
- 17.1.11 T-SYSTEMS INTERNATIONAL GMBH
- 17.1.11.1 Business overview
- 17.1.11.2 Products/Solutions/Services offered
- 17.1.11.3 Recent developments
- 17.1.11.3.1 Product launches/enhancements
- 17.1.11.3.2 Deals
- 17.1.12 AUTOCRYPT CO., LTD.
- 17.1.12.1 Business overview
- 17.1.12.2 Products/Solutions/Services offered
- 17.1.12.3 Recent developments
- 17.1.12.3.1 Product launches/enhancements
- 17.1.12.3.2 Deals
- 17.1.1 AUMOVIO SE
- 17.2 OTHER PLAYERS
- 17.2.1 ARM LIMITED
- 17.2.2 TREND MICRO INCORPORATED
- 17.2.3 ETAS
- 17.2.4 KEYSIGHT TECHNOLOGIES
- 17.2.5 INTERTEK GROUP PLC
- 17.2.6 DEVICE AUTHORITY
- 17.2.7 SECUNET SECURITY NETWORKS AG
- 17.2.8 TRILLIUM SECURE, INC.
- 17.2.9 WIRELESSCAR
- 17.2.10 KARAMBA SECURITY
- 17.2.11 INTERTRUST TECHNOLOGIES CORPORATION
- 17.2.12 GUARDKNOX
- 17.2.13 TATA ELXSI
18 APPENDIX
- 18.1 DISCUSSION GUIDE
- 18.2 KNOWLEDGESTORE: MARKETSANDMARKETS' SUBSCRIPTION PORTAL
- 18.3 CUSTOMIZATION OPTIONS
- 18.4 RELATED REPORTS
- 18.5 AUTHOR DETAILS
List of Tables
- TABLE 1 USD EXCHANGE RATES, 2020-2024
- TABLE 2 FACTOR ANALYSIS
- TABLE 3 IMPACT OF PORTER'S FIVE FORCES ON CONNECTED CAR SECURITY MARKET
- TABLE 4 ROLE OF PLAYERS IN MARKET ECOSYSTEM
- TABLE 5 INDICATIVE PRICING OF CONNECTED CAR SECURITY SYSTEMS, BY APPLICATION, 2024 (USD)
- TABLE 6 INDICATIVE PRICING OF CONNECTED CAR SECURITY SYSTEMS, BY SECURITY TYPE, 2024 (USD)
- TABLE 7 INDICATIVE PRICING OF CONNECTED CAR SECURITY SYSTEMS, BY REGION, 2024 (USD)
- TABLE 8 IMPORT DATA FOR HS CODE 8537-COMPLIANT PRODUCTS, BY COUNTRY, 2020-2024 (USD MILLION)
- TABLE 9 EXPORT DATA FOR HS CODE 8537-COMPLIANT PRODUCTS, BY COUNTRY, 2020-2024 (USD MILLION)
- TABLE 10 KEY CONFERENCES & EVENTS, 2025-2026
- TABLE 11 RECIPROCAL TARIFF RATES ADJUSTED BY US
- TABLE 12 TARIFF IMPACT ON CONNECTED CAR SECURITY
- TABLE 13 PRICE CHANGE (BY END-USE CATEGORY) AND PLAYERS IMPACTED
- TABLE 14 TARIFF IMPACT, BY END-USE INDUSTRY
- TABLE 15 INFLUENCE OF STAKEHOLDERS ON BUYING PROCESS, BY KEY APPLICATION (%)
- TABLE 16 KEY BUYING CRITERIA FOR KEY APPLICATIONS
- TABLE 17 CONNECTED CAR SECURITY MARKET: UNMET NEEDS FOR END USERS
- TABLE 18 KEY PATENTS, 2020-2025
- TABLE 19 LIST OF PATENTS GRANTED TO LG ELECTRONICS, 2020-2025
- TABLE 20 LIST OF PATENTS GRANTED TO INTEL CORPORATION, 2020-2025
- TABLE 21 LIST OF PATENTS GRANTED TO SAMSUNG ELECTRONICS, 2020-2025
- TABLE 22 ADOPTION OF AI IN CONNECTED CAR SECURITY MARKET: KEY DEVELOPMENTS, BY OEM
- TABLE 23 TECHNOLOGICAL DEVELOPMENTS IN CONNECTED CAR MARKET, BY OEM
- TABLE 24 NORTH AMERICA: REGULATORY BODIES, GOVERNMENT AGENCIES, AND OTHER ORGANIZATIONS
- TABLE 25 EUROPE: REGULATORY BODIES, GOVERNMENT AGENCIES, AND OTHER ORGANIZATIONS
- TABLE 26 ASIA PACIFIC: REGULATORY BODIES, GOVERNMENT AGENCIES, AND OTHER ORGANIZATIONS
- TABLE 27 NORTH AMERICA: POLICIES AND INITIATIVES SUPPORTING CONNECTED CAR CYBERSECURITY AND SECURE VEHICLE INFRASTRUCTURE
- TABLE 28 EUROPE: POLICIES AND INITIATIVES SUPPORTING CONNECTED CAR CYBERSECURITY & SECURE VEHICLE INFRASTRUCTURE
- TABLE 29 ASIA PACIFIC: POLICIES AND INITIATIVES SUPPORTING CONNECTED CAR CYBERSECURITY AND SECURE VEHICLE INFRASTRUCTURE
- TABLE 30 CONNECTED CAR SECURITY MARKET, BY APPLICATION, 2019-2024 (USD MILLION)
- TABLE 31 CONNECTED CAR SECURITY MARKET, BY APPLICATION, 2025-2032 (USD MILLION)
- TABLE 32 TELEMATICS CONTROL UNITS (TCUS): CONNECTED CAR SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 33 TELEMATICS CONTROL UNITS (TCUS): CONNECTED CAR SECURITY MARKET, BY REGION, 2025-2032 (USD MILLION)
- TABLE 34 INFOTAINMENT SYSTEMS: CONNECTED CAR SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 35 INFOTAINMENT SYSTEMS: CONNECTED CAR SECURITY MARKET, BY REGION, 2025-2032 (USD MILLION)
- TABLE 36 ADAS & AUTONOMOUS DRIVING SYSTEMS: CONNECTED CAR SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 37 ADAS & AUTONOMOUS DRIVING SYSTEMS: CONNECTED CAR SECURITY MARKET, BY REGION, 2025-2032 (USD MILLION)
- TABLE 38 COMMUNICATION MODULES: CONNECTED CAR SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 39 COMMUNICATION MODULES: CONNECTED CAR SECURITY MARKET, BY REGION, 2025-2032 (USD MILLION)
- TABLE 40 CONNECTED CAR SECURITY MARKET, BY ELECTRIC VEHICLE TYPE, 2019-2024 (USD MILLION)
- TABLE 41 CONNECTED CAR SECURITY MARKET, BY ELECTRIC VEHICLE TYPE, 2025-2032 (USD MILLION)
- TABLE 42 BEV: CONNECTED CAR SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 43 BEV: CONNECTED CAR SECURITY MARKET, BY REGION, 2025-2032 (USD MILLION)
- TABLE 44 PHEV: CONNECTED CAR SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 45 PHEV: CONNECTED CAR SECURITY MARKET, BY REGION, 2025-2032 (USD MILLION)
- TABLE 46 HEV: CONNECTED CAR SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 47 HEV: CONNECTED CAR SECURITY MARKET, BY REGION, 2025-2032 (USD MILLION)
- TABLE 48 FCEV: CONNECTED CAR SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 49 FCEV: CONNECTED CAR SECURITY MARKET, BY REGION, 2025-2032 (USD MILLION)
- TABLE 50 CONNECTED CAR SECURITY MARKET, BY FORM, 2019-2024 (USD MILLION)
- TABLE 51 CONNECTED CAR SECURITY MARKET, BY FORM, 2025-2032 (USD MILLION)
- TABLE 52 IN-VEHICLE SOLUTIONS: CONNECTED CAR SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 53 IN-VEHICLE SOLUTIONS: CONNECTED CAR SECURITY MARKET, BY REGION, 2025-2032 (USD MILLION)
- TABLE 54 EXTERNAL CLOUD SERVICES: CONNECTED CAR SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 55 EXTERNAL CLOUD SERVICES: CONNECTED CAR SECURITY MARKET, BY REGION, 2025-2032 (USD MILLION)
- TABLE 56 CONNECTED CAR SECURITY MARKET, BY SECURITY TYPE, 2019-2024 (USD MILLION)
- TABLE 57 CONNECTED CAR SECURITY MARKET, BY SECURITY TYPE, 2025-2032 (USD MILLION)
- TABLE 58 ENDPOINT SECURITY: CONNECTED CAR SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 59 ENDPOINT SECURITY: CONNECTED CAR SECURITY MARKET, BY REGION, 2025-2032 (USD MILLION)
- TABLE 60 APPLICATION SECURITY: CONNECTED CAR SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 61 APPLICATION SECURITY: CONNECTED CAR SECURITY MARKET, BY REGION, 2025-2032 (USD MILLION)
- TABLE 62 NETWORK SECURITY: CONNECTED CAR SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 63 NETWORK SECURITY: CONNECTED CAR SECURITY MARKET, BY REGION, 2025-2032 (USD MILLION)
- TABLE 64 CLOUD SECURITY: CONNECTED CAR SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 65 CLOUD SECURITY: CONNECTED CAR SECURITY MARKET, BY REGION, 2025-2032 (USD MILLION )
- TABLE 66 CONNECTED CAR SECURITY MARKET, BY SOLUTION TYPE, 2019-2024 (USD MILLION)
- TABLE 67 CONNECTED CAR SECURITY MARKET, BY SOLUTION TYPE, 2025-2032 (USD MILLION)
- TABLE 68 SOFTWARE-BASED SOLUTIONS: CONNECTED CAR SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 69 SOFTWARE-BASED SOLUTIONS: CONNECTED CAR SECURITY MARKET, BY REGION, 2025-2032 (USD MILLION)
- TABLE 70 HARDWARE-BASED SOLUTIONS: CONNECTED CAR SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 71 HARDWARE-BASED SOLUTIONS: CONNECTED CAR SECURITY MARKET, BY REGION, 2025-2032 (USD MILLION)
- TABLE 72 CONNECTED CAR SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 73 CONNECTED CAR SECURITY MARKET, BY REGION, 2025-2032 (USD MILLION)
- TABLE 74 ASIA PACIFIC: CONNECTED CAR SECURITY MARKET, BY SECURITY TYPE, 2019-2024 (USD MILLION)
- TABLE 75 ASIA PACIFIC: CONNECTED CAR SECURITY MARKET, BY SECURITY TYPE, 2025-2032 (USD MILLION)
- TABLE 76 ASIA PACIFIC: CONNECTED CAR SECURITY MARKET, BY APPLICATION, 2019-2024 (USD MILLION)
- TABLE 77 ASIA PACIFIC: CONNECTED CAR SECURITY MARKET, BY APPLICATION, 2025-2032 (USD MILLION)
- TABLE 78 ASIA PACIFIC: CONNECTED CAR SECURITY MARKET, BY COUNTRY/REGION, 2019-2024 (USD MILLION)
- TABLE 79 ASIA PACIFIC: CONNECTED CAR SECURITY MARKET, BY COUNTRY/REGION, 2025-2032 (USD MILLION)
- TABLE 80 CHINA: CONNECTED CAR SECURITY MARKET, BY SECURITY TYPE, 2019-2024 (USD MILLION)
- TABLE 81 CHINA: CONNECTED CAR SECURITY MARKET, BY SECURITY TYPE, 2025-2032 (USD MILLION)
- TABLE 82 CHINA: CONNECTED CAR SECURITY MARKET, BY APPLICATION, 2019-2024 (USD MILLION)
- TABLE 83 CHINA: CONNECTED CAR SECURITY MARKET, BY APPLICATION, 2025-2032 (USD MILLION)
- TABLE 84 JAPAN: CONNECTED CAR SECURITY MARKET, BY SECURITY TYPE, 2019-2024 (USD MILLION)
- TABLE 85 JAPAN: CONNECTED CAR SECURITY MARKET, BY SECURITY TYPE, 2025-2032 (USD MILLION)
- TABLE 86 JAPAN: CONNECTED CAR SECURITY MARKET, BY APPLICATION, 2019-2024 (USD MILLION)
- TABLE 87 JAPAN: CONNECTED CAR SECURITY MARKET, BY APPLICATION, 2025-2032 (USD MILLION)
- TABLE 88 INDIA: CONNECTED CAR SECURITY MARKET, BY SECURITY TYPE, 2019-2024 (USD MILLION)
- TABLE 89 INDIA: CONNECTED CAR SECURITY MARKET, BY SECURITY TYPE, 2025-2032 (USD MILLION)
- TABLE 90 INDIA: CONNECTED CAR SECURITY MARKET, BY APPLICATION, 2019-2024 (USD MILLION)
- TABLE 91 INDIA: CONNECTED CAR SECURITY MARKET, BY APPLICATION, 2025-2032 (USD MILLION)
- TABLE 92 SOUTH KOREA: CONNECTED CAR SECURITY MARKET, BY SECURITY TYPE, 2019-2024 (USD MILLION)
- TABLE 93 SOUTH KOREA: CONNECTED CAR SECURITY MARKET, BY SECURITY TYPE, 2025-2032 (USD MILLION)
- TABLE 94 SOUTH KOREA: CONNECTED CAR SECURITY MARKET, BY APPLICATION, 2019-2024 (USD MILLION)
- TABLE 95 SOUTH KOREA: CONNECTED CAR SECURITY MARKET, BY APPLICATION, 2025-2032 (USD MILLION)
- TABLE 96 REST OF ASIA PACIFIC: CONNECTED CAR SECURITY MARKET, BY SECURITY TYPE, 2019-2024 (USD MILLION)
- TABLE 97 REST OF ASIA PACIFIC: CONNECTED CAR SECURITY MARKET, BY SECURITY TYPE, 2025-2032 (USD MILLION)
- TABLE 98 REST OF ASIA PACIFIC: CONNECTED CAR SECURITY MARKET, BY APPLICATION, 2019-2024 (USD MILLION)
- TABLE 99 REST OF ASIA PACIFIC: CONNECTED CAR SECURITY MARKET, BY APPLICATION, 2025-2032 (USD MILLION)
- TABLE 100 EUROPE: CONNECTED CAR SECURITY MARKET, BY SECURITY TYPE, 2019-2024 (USD MILLION)
- TABLE 101 EUROPE: CONNECTED CAR SECURITY MARKET, BY SECURITY TYPE, 2025-2032 (USD MILLION)
- TABLE 102 EUROPE: CONNECTED CAR SECURITY MARKET, BY APPLICATION, 2019-2024 (USD MILLION)
- TABLE 103 EUROPE: CONNECTED CAR SECURITY MARKET, BY APPLICATION, 2025-2032 (USD MILLION)
- TABLE 104 EUROPE: CONNECTED CAR SECURITY MARKET, BY COUNTRY/REGION, 2019-2024 (USD MILLION)
- TABLE 105 EUROPE: CONNECTED CAR SECURITY MARKET, BY COUNTRY/REGION, 2025-2032 (USD MILLION)
- TABLE 106 UK: CONNECTED CAR SECURITY MARKET, BY SECURITY TYPE, 2019-2024 (USD MILLION)
- TABLE 107 UK: CONNECTED CAR SECURITY MARKET, BY SECURITY TYPE, 2025-2032 (USD MILLION)
- TABLE 108 UK: CONNECTED CAR SECURITY MARKET, BY APPLICATION, 2019-2024 (USD MILLION)
- TABLE 109 UK: CONNECTED CAR SECURITY MARKET, BY APPLICATION, 2025-2032 (USD MILLION)
- TABLE 110 GERMANY: CONNECTED CAR SECURITY MARKET, BY SECURITY TYPE, 2019-2024 (USD MILLION)
- TABLE 111 GERMANY: CONNECTED CAR SECURITY MARKET, BY SECURITY TYPE, 2025-2032 (USD MILLION)
- TABLE 112 GERMANY: CONNECTED CAR SECURITY MARKET, BY APPLICATION, 2019-2024 (USD MILLION)
- TABLE 113 GERMANY: CONNECTED CAR SECURITY MARKET, BY APPLICATION, 2025-2032 (USD MILLION)
- TABLE 114 FRANCE: CONNECTED CAR SECURITY MARKET, BY SECURITY TYPE, 2019-2024 (USD MILLION)
- TABLE 115 FRANCE: CONNECTED CAR SECURITY MARKET, BY SECURITY TYPE, 2025-2032 (USD MILLION)
- TABLE 116 FRANCE: CONNECTED CAR SECURITY MARKET, BY APPLICATION, 2019-2024 (USD MILLION)
- TABLE 117 FRANCE: CONNECTED CAR SECURITY MARKET, BY APPLICATION, 2025-2032 (USD MILLION)
- TABLE 118 SPAIN: CONNECTED CAR SECURITY MARKET, BY SECURITY TYPE, 2019-2024 (USD MILLION)
- TABLE 119 SPAIN: CONNECTED CAR SECURITY MARKET, BY SECURITY TYPE, 2025-2032 (USD MILLION)
- TABLE 120 SPAIN: CONNECTED CAR SECURITY MARKET, BY APPLICATION, 2019-2024 (USD MILLION)
- TABLE 121 SPAIN: CONNECTED CAR SECURITY MARKET, BY APPLICATION, 2025-2032 (USD MILLION)
- TABLE 122 ITALY: CONNECTED CAR SECURITY MARKET, BY SECURITY TYPE, 2019-2024 (USD MILLION)
- TABLE 123 ITALY: CONNECTED CAR SECURITY MARKET, BY SECURITY TYPE, 2025-2032 (USD MILLION)
- TABLE 124 ITALY: CONNECTED CAR SECURITY MARKET, BY APPLICATION, 2019-2024 (USD MILLION)
- TABLE 125 ITALY: CONNECTED CAR SECURITY MARKET, BY APPLICATION, 2025-2032 (USD MILLION)
- TABLE 126 REST OF EUROPE: CONNECTED CAR SECURITY MARKET, BY SECURITY TYPE, 2019-2024 (USD MILLION)
- TABLE 127 REST OF EUROPE: CONNECTED CAR SECURITY MARKET, BY SECURITY TYPE, 2025-2032 (USD MILLION)
- TABLE 128 REST OF EUROPE: CONNECTED CAR SECURITY MARKET, BY APPLICATION, 2019-2024 (USD MILLION)
- TABLE 129 REST OF EUROPE: CONNECTED CAR SECURITY MARKET, BY APPLICATION, 2025-2032 (USD MILLION)
- TABLE 130 NORTH AMERICA: CONNECTED CAR SECURITY MARKET, BY SECURITY TYPE, 2019-2024 (USD MILLION)
- TABLE 131 NORTH AMERICA: CONNECTED CAR SECURITY MARKET, BY SECURITY TYPE, 2025-2032 (USD MILLION)
- TABLE 132 NORTH AMERICA: CONNECTED CAR SECURITY MARKET, BY APPLICATION, 2019-2024 (USD MILLION)
- TABLE 133 NORTH AMERICA: CONNECTED CAR SECURITY MARKET, BY APPLICATION, 2025-2032 (USD MILLION)
- TABLE 134 NORTH AMERICA: CONNECTED CAR SECURITY MARKET, BY COUNTRY, 2019-2024 (USD MILLION)
- TABLE 135 NORTH AMERICA: CONNECTED CAR SECURITY MARKET, BY COUNTRY, 2025-2032 (USD MILLION)
- TABLE 136 US: CONNECTED CAR SECURITY MARKET, BY SECURITY TYPE, 2019-2024 (USD MILLION)
- TABLE 137 US: CONNECTED CAR SECURITY MARKET, BY SECURITY TYPE, 2025-2032 (USD MILLION)
- TABLE 138 US: CONNECTED CAR SECURITY MARKET, BY APPLICATION, 2019-2024 (USD MILLION)
- TABLE 139 US: CONNECTED CAR SECURITY MARKET, BY APPLICATION, 2025-2032 (USD MILLION)
- TABLE 140 CANADA: CONNECTED CAR SECURITY MARKET, BY SECURITY TYPE, 2019-2024 (USD MILLION)
- TABLE 141 CANADA: CONNECTED CAR SECURITY MARKET, BY SECURITY TYPE, 2025-2032 (USD MILLION)
- TABLE 142 CANADA: CONNECTED CAR SECURITY MARKET, BY APPLICATION, 2019-2024 (USD MILLION)
- TABLE 143 CANADA: CONNECTED CAR SECURITY MARKET, BY APPLICATION, 2025-2032 (USD MILLION)
- TABLE 144 MEXICO: CONNECTED CAR SECURITY MARKET, BY SECURITY TYPE, 2019-2024 (USD MILLION)
- TABLE 145 MEXICO: CONNECTED CAR SECURITY MARKET, BY SECURITY TYPE, 2025-2032 (USD MILLION)
- TABLE 146 MEXICO: CONNECTED CAR SECURITY MARKET, BY APPLICATION, 2019-2024 (USD MILLION)
- TABLE 147 MEXICO: CONNECTED CAR SECURITY MARKET, BY APPLICATION, 2025-2032 (USD MILLION)
- TABLE 148 REST OF THE WORLD: CONNECTED CAR SECURITY MARKET, BY SECURITY TYPE, 2019-2024 (USD MILLION)
- TABLE 149 REST OF THE WORLD: CONNECTED CAR SECURITY MARKET, BY SECURITY TYPE, 2025-2032 (USD MILLION)
- TABLE 150 REST OF THE WORLD: CONNECTED CAR SECURITY MARKET, BY APPLICATION, 2019-2024 (USD MILLION)
- TABLE 151 REST OF THE WORLD: CONNECTED CAR SECURITY MARKET, BY APPLICATION, 2025-2032 (USD MILLION)
- TABLE 152 REST OF THE WORLD: CONNECTED CAR SECURITY MARKET, BY COUNTRY, 2019-2024 (USD MILLION)
- TABLE 153 REST OF THE WORLD: CONNECTED CAR SECURITY MARKET, BY COUNTRY, 2025-2032 (USD MILLION)
- TABLE 154 IRAN: CONNECTED CAR SECURITY MARKET, BY SECURITY TYPE, 2019-2024 (USD MILLION)
- TABLE 155 IRAN: CONNECTED CAR SECURITY MARKET, BY SECURITY TYPE, 2025-2032 (USD MILLION)
- TABLE 156 IRAN: CONNECTED CAR SECURITY MARKET, BY APPLICATION, 2019-2024 (USD MILLION)
- TABLE 157 IRAN: CONNECTED CAR SECURITY MARKET, BY APPLICATION, 2025-2032 (USD MILLION)
- TABLE 158 SOUTH AFRICA: CONNECTED CAR SECURITY MARKET, BY SECURITY TYPE, 2019-2024 (USD MILLION)
- TABLE 159 SOUTH AFRICA: CONNECTED CAR SECURITY MARKET, BY SECURITY TYPE, 2025-2032 (USD MILLION)
- TABLE 160 SOUTH AFRICA: CONNECTED CAR SECURITY MARKET, BY APPLICATION, 2019-2024 (USD MILLION)
- TABLE 161 SOUTH AFRICA: CONNECTED CAR SECURITY MARKET, BY APPLICATION, 2025-2032 (USD MILLION)
- TABLE 162 OVERVIEW OF STRATEGIES ADOPTED BY KEY MARKET VENDORS, 2022-2024
- TABLE 163 CONNECTED CAR SECURITY MARKET: DEGREE OF COMPETITION
- TABLE 164 CONNECTED CAR SECURITY MARKET: REGION FOOTPRINT
- TABLE 165 CONNECTED CAR SECURITY MARKET: SOLUTION TYPE FOOTPRINT
- TABLE 166 CONNECTED CAR SECURITY MARKET: APPLICATION FOOTPRINT
- TABLE 167 CONNECTED CAR SECURITY MARKET: SECURITY TYPE FOOTPRINT
- TABLE 168 CONNECTED CAR SECURITY MARKET: KEY STARTUPS/SMES
- TABLE 169 CONNECTED CAR SECURITY MARKET: COMPETITIVE BENCHMARKING OF KEY STARTUPS/SMES
- TABLE 170 CONNECTED CAR SECURITY MARKET: PRODUCT LAUNCHES/ENHANCEMENTS, MAY 2023-SEPTEMBER 2025
- TABLE 171 CONNECTED CAR SECURITY MARKET: DEALS, MAY 2023-SEPTEMBER 2025
- TABLE 172 AUMOVIO SE: COMPANY OVERVIEW
- TABLE 173 AUMOVIO SE: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 174 AUMOVIO SE: PRODUCT LAUNCHES/ENHANCEMENTS
- TABLE 175 AUMOVIO SE: DEALS
- TABLE 176 AUMOVIO SE: EXPANSION
- TABLE 177 BLACKBERRY LIMITED: COMPANY OVERVIEW
- TABLE 178 BLACKBERRY LIMITED: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 179 BLACKBERRY LIMITED: PRODUCT LAUNCHES/ENHANCEMENTS
- TABLE 180 BLACKBERRY LIMITED: DEALS
- TABLE 181 VECTOR INFORMATIK GMBH: COMPANY OVERVIEW
- TABLE 182 VECTOR INFORMATIK GMBH: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 183 VECTOR INFORMATIK GMBH: PRODUCT LAUNCHES/ENHANCEMENTS
- TABLE 184 VECTOR INFORMATIK GMBH: DEALS
- TABLE 185 NXP SEMICONDUCTORS: COMPANY OVERVIEW
- TABLE 186 NXP SEMICONDUCTORS: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 187 NXP SEMICONDUCTORS: DEALS
- TABLE 188 HARMAN INTERNATIONAL: COMPANY OVERVIEW
- TABLE 189 HARMAN INTERNATIONAL: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 190 HARMAN INTERNATIONAL: DEALS
- TABLE 191 UPSTREAM SECURITY LTD.: COMPANY OVERVIEW
- TABLE 192 UPSTREAM SECURITY LTD.: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 193 UPSTREAM SECURITY LTD.: PRODUCT LAUNCHES/ENHANCEMENTS
- TABLE 194 UPSTREAM SECURITY LTD.: DEALS
- TABLE 195 ASTEMO, LTD.: COMPANY OVERVIEW
- TABLE 196 ASTEMO, LTD.: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 197 ASTEMO, LTD.: DEALS
- TABLE 198 ASTEMO, LTD: EXPANSION
- TABLE 199 TRUSTONIC: COMPANY OVERVIEW
- TABLE 200 TRUSTONIC: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 201 TRUSTONIC: PRODUCT LAUNCHES/ENHANCEMENTS
- TABLE 202 TRUSTONIC: DEALS
- TABLE 203 KPIT: COMPANY OVERVIEW
- TABLE 204 KPIT: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 205 KPIT: DEALS
- TABLE 206 THALES: COMPANY OVERVIEW
- TABLE 207 THALES: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 208 THALES: PRODUCT LAUNCHES/ENHANCEMENTS
- TABLE 209 THALES: DEALS
- TABLE 210 T-SYSTEMS INTERNATIONAL GMBH: COMPANY OVERVIEW
- TABLE 211 T-SYSTEMS INTERNATIONAL GMBH: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 212 T-SYSTEMS INTERNATIONAL GMBH: PRODUCT LAUNCHES/ENHANCEMENTS
- TABLE 213 T-SYSTEMS INTERNATIONAL GMBH: DEALS
- TABLE 214 AUTOCRYPT CO., LTD.: COMPANY OVERVIEW
- TABLE 215 AUTOCRYPT CO., LTD.: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 216 AUTOCRYPT CO., LTD.: PRODUCT LAUNCHES/ENHANCEMENTS
- TABLE 217 AUTOCRYPT CO., LTD.: DEALS
- TABLE 218 ARM LIMITED: COMPANY OVERVIEW
- TABLE 219 TREND MICRO INCORPORATED: COMPANY OVERVIEW
- TABLE 220 ETAS: COMPANY OVERVIEW
- TABLE 221 KEYSIGHT TECHNOLOGIES: COMPANY OVERVIEW
- TABLE 222 INTERTEK GROUP PLC: COMPANY OVERVIEW
- TABLE 223 DEVICE AUTHORITY: COMPANY OVERVIEW
- TABLE 224 SECUNET SECURITY NETWORKS AG: COMPANY OVERVIEW
- TABLE 225 TRILLIUM SECURE: COMPANY OVERVIEW
- TABLE 226 WIRELESSCAR: COMPANY OVERVIEW
- TABLE 227 KARAMBA SECURITY: COMPANY OVERVIEW
- TABLE 228 INTERTRUST TECHNOLOGIES CORPORATION: COMPANY OVERVIEW
- TABLE 229 GUARDKNOX: COMPANY OVERVIEW
- TABLE 230 TATA ELXSI: COMPANY OVERVIEW
List of Figures
- FIGURE 1 CONNECTED CAR SECURITY MARKET: RESEARCH DESIGN
- FIGURE 2 RESEARCH DESIGN MODEL
- FIGURE 3 BREAKDOWN OF PRIMARY INTERVIEWS
- FIGURE 4 DATA TRIANGULATION
- FIGURE 5 CONNECTED CAR SECURITY MARKET ESTIMATION: RESEARCH FLOW
- FIGURE 6 TOP-DOWN APPROACH
- FIGURE 7 KEY INSIGHTS AND MARKET HIGHLIGHTS
- FIGURE 8 CONNECTED CAR SECURITY MARKET, 2025-2032
- FIGURE 9 MAJOR STRATEGIES ADOPTED BY KEY PLAYERS IN CONNECTED CAR SECURITY MARKET, 2022-2025
- FIGURE 10 DISRUPTIVE TRENDS IMPACTING GROWTH OF CONNECTED CAR SECURITY MARKET
- FIGURE 11 HIGH-GROWTH SEGMENTS AND EMERGING FRONTIERS IN CONNECTED CAR SECURITY MARKET, 2025
- FIGURE 12 ASIA PACIFIC TO REGISTER HIGHEST GROWTH RATE DURING FORECAST PERIOD
- FIGURE 13 RISING VEHICLE CONNECTIVITY AND STRINGENT GOVERNMENT REGULATIONS TO DRIVE MARKET
- FIGURE 14 NETWORK SECURITY SEGMENT TO LEAD MARKET BY 2032
- FIGURE 15 BEV SEGMENT TO LEAD MARKET BY 2032
- FIGURE 16 IN-VEHICLE SOLUTIONS SEGMENT TO LEAD MARKET BY 2032
- FIGURE 17 TELEMATICS CONTROL UNITS (TCUS) SEGMENT TO ACCOUNT FOR LARGEST MARKET BY 2032
- FIGURE 18 SOFTWARE-BASED SOLUTIONS SEGMENT TO LEAD MARKET BY 2032
- FIGURE 19 ASIA PACIFIC TO ACCOUNT FOR LARGEST SHARE DURING FORECAST PERIOD
- FIGURE 20 CONNECTED CAR SECURITY MARKET: DRIVERS, RESTRAINTS, OPPORTUNITIES, AND CHALLENGES
- FIGURE 21 TELEMATICS AND V2X
- FIGURE 22 ISO/SAE 21434 CYBERSECURITY PROCESS ACTIVITIES
- FIGURE 23 DISTRIBUTION OF AUTOMOTIVE CYBERATTACKS, 2024
- FIGURE 24 GLOBAL OTA VEHICLES IN OPERATION, 2024 VS. 2028
- FIGURE 25 SECURITY RISKS FOR CONNECTED CARS
- FIGURE 26 CONNECTED CAR SECURITY MARKET: PORTER'S FIVE FORCES ANALYSIS
- FIGURE 27 CONNECTED CAR SECURITY MARKET: GDP TRENDS AND FORECAST, 2024-2032
- FIGURE 28 SDV MARKET PENETRATION, 2019-2030
- FIGURE 29 SUPPLY CHAIN ANALYSIS
- FIGURE 30 CONNECTED CAR SECURITY MARKET ECOSYSTEM
- FIGURE 31 IMPORT DATA FOR HS CODE 8537-COMPLIANT PRODUCTS, BY COUNTRY, 2020-2024 (USD MILLION)
- FIGURE 32 EXPORT DATA FOR HS CODE 8537-COMPLIANT PRODUCTS, BY COUNTRY, 2020-2024 (USD MILLION)
- FIGURE 33 TRENDS/DISRUPTIONS IMPACTING CUSTOMER BUSINESS
- FIGURE 34 INVESTMENT & FUNDING SCENARIO, 2025
- FIGURE 35 FACTORS IMPACTING DECISION-MAKING
- FIGURE 36 INFLUENCE OF STAKEHOLDERS ON BUYING PROCESS, BY KEY APPLICATION
- FIGURE 37 KEY BUYING CRITERIA FOR KEY APPLICATIONS
- FIGURE 38 ADOPTION BARRIERS AND INTERNAL CHALLENGES
- FIGURE 39 PATENTS APPLIED AND GRANTED, 2015-2025
- FIGURE 40 REGIONAL ANALYSIS OF PATENTS, 2025
- FIGURE 41 AUTOMOTIVE CYBER SECURITY WITH VEHICLE SECURITY OPERATIONS SYSTEM (VCOS)
- FIGURE 42 AUTOMOTIVE INTRUSION DETECTION SYSTEMS
- FIGURE 43 AUTOMOTIVE INTRUSION DETECTION SYSTEMS
- FIGURE 44 REASONS TO UPGRADE TO TPM 2.0
- FIGURE 45 CONNECTED VEHICLE AND MOBILE EDGE COMPUTING
- FIGURE 46 INTEGRATED ML-BASED IDS FOR AUTONOMOUS VEHICLES
- FIGURE 47 CONNECTED CAR SECURITY MARKET, BY APPLICATION, 2025 VS. 2032 (USD MILLION)
- FIGURE 48 CONNECTED CAR SECURITY MARKET, BY ELECTRIC VEHICLE TYPE, 2025 VS. 2032 (USD MILLION)
- FIGURE 49 CONNECTED CAR SECURITY MARKET, BY FORM, 2025 VS. 2032 (USD MILLION)
- FIGURE 50 CONNECTED CAR SECURITY MARKET, BY SECURITY TYPE, 2025 VS. 2032 (USD MILLION)
- FIGURE 51 CONNECTED CAR SECURITY MARKET, BY SOLUTION TYPE, 2025 VS. 2032 (USD MILLION)
- FIGURE 52 ASIA PACIFIC TO GROW AT HIGHEST RATE DURING FORECAST PERIOD
- FIGURE 53 ASIA PACIFIC: CONNECTED CAR SECURITY MARKET SNAPSHOT
- FIGURE 54 NORTH AMERICA: CONNECTED CAR SECURITY MARKET SNAPSHOT
- FIGURE 55 MARKET SHARE ANALYSIS, 2024
- FIGURE 56 REVENUE ANALYSIS OF TOP FIVE PLAYERS, 2020-2024 (USD MILLION)
- FIGURE 57 BRAND COMPARISON
- FIGURE 58 COMPANY VALUATION, 2024 (USD BILLION)
- FIGURE 59 FINANCIAL METRICS, 2025
- FIGURE 60 CONNECTED CAR SECURITY MARKET: COMPANY EVALUATION MATRIX (KEY PLAYERS), 2024
- FIGURE 61 CONNECTED CAR SECURITY MARKET: COMPANY FOOTPRINT
- FIGURE 62 CONNECTED CAR SECURITY MARKET: COMPANY EVALUATION MATRIX (STARTUPS/SMES), 2024
- FIGURE 63 BLACKBERRY LIMITED: COMPANY SNAPSHOT
- FIGURE 64 NXP SEMICONDUCTORS: COMPANY SNAPSHOT
- FIGURE 65 KPIT: COMPANY SNAPSHOT
- FIGURE 66 THALES: COMPANY SNAPSHOT











