 |
市场调查报告书
商品编码
1850085
石油和天然气安全:市场份额分析、行业趋势、统计数据和成长预测(2025-2030 年)Oil And Gas Security - Market Share Analysis, Industry Trends & Statistics, Growth Forecasts (2025 - 2030) |
||||||
※ 本网页内容可能与最新版本有所差异。详细情况请与我们联繫。
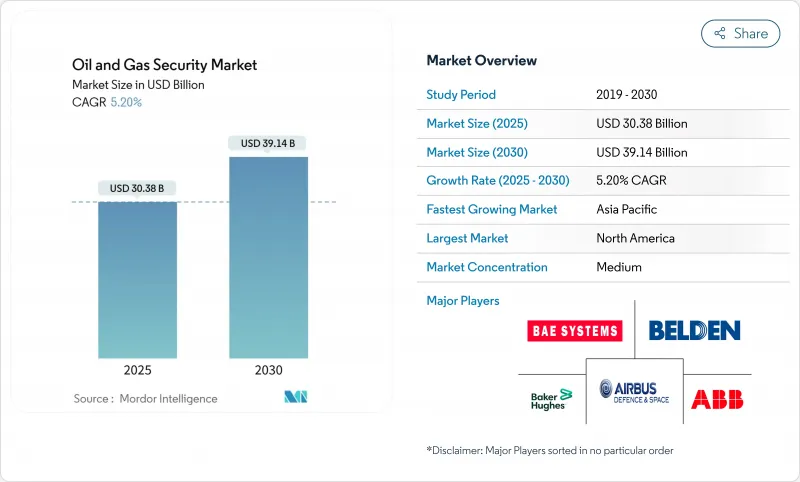
预计 2025 年石油和天然气安全市场规模为 303.8 亿美元,到 2030 年将达到 391.4 亿美元,预测期内(2025-2030 年)的复合年增长率为 5.20%。
这一成长轨迹表明,即使在大宗商品价格波动的情况下,能源公司仍在持续加大安全项目的投入。随着网路事件不仅影响资讯技术 (IT) 资产,也影响操作技术(OT) 资产,主导公司正在加速从预防性安全措施转向主动安全措施的转变。日益加剧的地缘政治紧张局势、日益严格的管道监管以及日益增长的保险需求,使得公司在网路和实体控制方面都投入了巨额预算。能够提供整合 OT-IT 堆迭(包括硬体、软体和託管服务)的供应商很可能在未来五年内获得巨大的价值。
全球石油和天然气安全市场趋势和洞察
OT-IT融合的扩大增加了网路风险
曾经与企业网路隔离的营运资产如今已连接到云端和企业系统,扩大了其攻击面。这种连结引发的事件使攻击者能够将重点从IT转移到对安全至关重要的OT,从而增加了物理中断的可能性。美国机构报告称,即使是低技能的团体也能成功攻击工业控制系统,暴露出其薄弱的隔离措施和最低限度的多因素身份验证。因此,网路分区、零信任策略和即时异常检测正在从最佳实践转变为基本期望。随着企业在不中断生产的情况下进行现代化改造,日益增加的复杂性迫使企业分阶段推出平行架构。改善管治以连接IT安全、工程和製造团队是未来支出的关键组成部分。
强制性的TSA和IEC管道网路法规
运输安全管理局(TSA) 修订后的指令要求管道运营商在规定的期限内检验控制措施、弥补差距并报告违规行为。 IEC 62443 也正在成为全球控制系统的基准,而日本的 CERT 等区域组织则提供实施指导。欧洲的 NIS2 指示进一步增加了义务,要求在 24 小时内揭露事件。不合规行为将面临经济处罚和潜在的停工令,这已将安全保障从一项可自由支配的开支提升为一项营运必需品。随着营运商寻求承包违规方案,对同时具备管治和技术部署专业知识的供应商的需求也日益增加。
旧式 SCADA 升级成本超支
许多平台依赖已有20年历史的监控系统,而这些系统的设计初衷并非针对网路暴露。企业经常低估分段、多因素身份验证和加密遥测所需的工程和停机成本。当相容性问题在部署中期浮现时,升级成本往往是原始预算的两到三倍。更长的资产生命週期使得资本配置变得困难,迫使营运商在短期生产力损失和长期弹性之间做出权衡。学术研究表明,低效率的跨职能沟通会进一步拖延执行并推高成本。
細項分析
到2024年,监控平台将占据30.4%的收入份额,证实了市场长期以来对周界监控和情境察觉的关注。与视讯分析、无人机和门禁控制相关的石油和天然气安全市场规模仍然庞大,但随着预算转向数位防御,其年增长率将有所放缓。网路和网路安全解决方案的复合年增长率为8.1%,这反映了强制性的管道法规和针对现场资产的勒索软体的兴起。像「殖民管道」攻击这样的事件凸显出,营运中断可能是由于笔记型电脑而非围栏突破造成的,这促使资本流向入侵侦测和安全的远端存取网关。
展望未来,融合摄影机讯号与网路遥测的整合指挥中心预计将超越单一用途的部署。这种整合可以透过将实体徽章与网路登入关联来减少误报。能够将摄影机、防火墙和控制器的事件交叉标记到统一萤幕上的供应商可能会在石油和天然气安全市场中占据越来越大的份额。因此,虽然监控系统仍然很重要,但它们正越来越多地被嵌入到更广泛的网实整合平台中,导致独立设备销售下降,而软体分析收入增加。
2024年,硬体仍将占据石油和天然气安全市场的52.6%,涵盖危险区域强化防火墙、本质安全型摄影机和抗震伺服器。然而,随着营运商签订24/7全天候监控和事件回应合约以填补技能短缺,託管服务细分市场的复合年增长率将达到9.3%。随着新站点对高级分析、威胁情报回馈和定期红队评估的需求不断增加,与服务保留相关的石油和天然气安全市场规模正在扩大。
服务的成长也与需要独立检验和记录的监管审核息息相关。由于缺乏内部能力,企业正在转向专门从事 OT 资产管理的託管服务供应商 (MSSP)。这些供应商将资产发现、漏洞管理和合规性报告捆绑在多年期合约中。硬体供应商正透过基于结果的模式来应对这项挑战,将设备和服务打包在一起,从而拉平收益并深化客户保留率。
石油和天然气安全市场按安全产品类型(网路和网路安全、监视、筛检和检测等)、组件(硬体、软体平台、服务)、营运阶段(上游、中游、下游)、部署类型(内部部署、云端、混合/边缘云端)、应用程式(探勘和生产站点、海上平台和 FPSO 等)和地区进行细分。
区域分析
受美国运输安全管理局(TSA)强制指令以及Colonial Pipeline勒索软体事件后续影响的推动,北美将在2024年占据全球油气安全市场的36.22%。加拿大的威胁评估报告指出,国营企业正将生产基地和中游枢纽作为攻击目标,这促使政府在培训和津贴(OT)细分方面建立公私合作伙伴关係。在联邦审核指出防火墙过时且人机介面(HMI)未修补后,墨西哥湾和北坡的海上资产正在寻求紧急网路升级。
随着中国扩大边境地区的主干管道和储存容量,将营运技术安全与北京的主权云端运算授权相结合,亚太地区到2030年的复合年增长率将达到9.1%,成为全球最高。日本将颁布经济安全规则,将石油和天然气列为关键社会基础设施,要求业者向监管机构提交安全计画。印度将扩建炼油厂和LNG接收站,并从班加罗尔和海得拉巴的当地安全营运中心采购託管服务。为因应南海地区日益紧张的局势,澳洲和韩国将在新的液化天然气出口计划中纳入营运技术安全条款。
在欧洲,现代化以NIS2框架为中心,该框架要求对重要能源营业单位进行全天候事件报告和年度审核。德国、法国和荷兰的液化天然气进口扩张规模不断扩大,复杂性不断增加,需要对海上到终端的连结进行加密。在中东和非洲,记录在案的攻击事件增加了206%,导致资金筹措投入增加,并在区域网路论坛上进行了展示。拉丁美洲仍处于起步阶段,但随着巴西、阿根廷和圭亚那加大产量并寻求与IEC 62443接轨,投资正在增加。
其他福利:
- Excel 格式的市场预测 (ME) 表
- 3个月的分析师支持
目录
第一章 引言
- 研究假设和市场定义
- 调查范围
第二章调查方法
第三章执行摘要
第四章 市场状况
- 市场概况
- 市场驱动因素
- OT 和 IT 整合度的提高增加了网路风险
- 强制执行TSA和IEC管道网路规则
- 引入人工智慧预测安全分析
- 能源价格波动推动保险需求
- 需要从边缘到核心的安全保障的海上自主资产
- 市场限制
- 传统 SCADA 升级成本超支
- 偏远盆地OT安全人才短缺
- 云端基础的资料主权纠纷
- ESG相关投资撤资抑制长期资本投资
- 产业价值链分析
- 监管格局
- 技术展望
- 产业吸引力-波特五力分析
- 新进入者的威胁
- 买方的议价能力
- 供应商的议价能力
- 替代品的威胁
- 竞争对手之间的竞争
- 影响市场的宏观经济因素
第五章市场规模与成长预测(价值)
- 按安全类型
- 网路和网路安全
- 监控
- 筛检和检测
- 指挥与控制
- 实体存取控制
- 其他类型
- 按组件
- 硬体
- 软体平台
- 服务(託管和专业)
- 按营运阶段
- 上游(探勘和生产)
- 中游(管道和储存)
- 下游(炼油和分销)
- 依部署方式
- 本地部署
- 云
- 混合/边缘云端
- 按用途
- 探勘和生产基地
- 海上平台和FPSO
- 管道监控
- 炼油厂和石化厂
- 液化天然气和天然气处理
- 零售和配送终端
- 按地区
- 北美洲
- 美国
- 加拿大
- 墨西哥
- 南美洲
- 巴西
- 阿根廷
- 智利
- 南美洲其他地区
- 欧洲
- 德国
- 英国
- 法国
- 义大利
- 西班牙
- 俄罗斯
- 其他欧洲地区
- 亚太地区
- 中国
- 印度
- 日本
- 韩国
- 马来西亚
- 新加坡
- 澳洲
- 其他亚太地区
- 中东和非洲
- 中东
- 阿拉伯聯合大公国
- 沙乌地阿拉伯
- 土耳其
- 其他中东地区
- 非洲
- 南非
- 奈及利亚
- 埃及
- 其他非洲国家
- 北美洲
第六章 竞争态势
- 市场集中度
- 策略趋势
- 市占率分析
- 公司简介
- ABB Ltd.
- Airbus Defence and Space
- BAE Systems plc
- Baker Hughes Cyber-Security Services
- Belden Inc.
- Check Point Software Technologies Ltd.
- Cisco Systems Inc.
- Claroty Ltd.
- Dragos Inc.
- Fortinet Inc.
- Honeywell International Inc.
- Huawei Technologies Co. Ltd.
- Johnson Controls International plc
- Kaspersky Lab JSC
- Microsoft Corp.
- Nozomi Networks Inc.
- Palo Alto Networks Inc.
- Parsons Corp.
- Rockwell Automation Inc.
- Schneider Electric SE
- Siemens AG
- Tenable OT Security
- Thales Group
- Trend Micro Inc.
- Waterfall Security Solutions Ltd.
第七章 市场机会与未来趋势
- 閒置频段和未满足需求评估
The Oil And Gas Security Market size is estimated at USD 30.38 billion in 2025, and is expected to reach USD 39.14 billion by 2030, at a CAGR of 5.20% during the forecast period (2025-2030).

This growth trajectory shows that energy companies are putting sustained capital into security programs even as commodity prices swing. The shift from reactive safeguards to proactive, intelligence-driven models is accelerating because cyber incidents now expose operational technology (OT) as well as information technology (IT) assets. Heightened geopolitical tension, stricter pipeline rules, and rising insurance prerequisites keep budgets anchored on both cyber and physical controls. Vendors that can blend hardware, software, and managed services into a unified OT-IT stack are positioned to capture disproportionate value in the next five years.
Global Oil And Gas Security Market Trends and Insights
Growing OT-IT Convergence Elevating Cyber-Risk
Operational assets, once isolated from corporate networks, now connect to cloud and enterprise systems, broadening attack surfaces. Incidents prompted by this linkage allow adversaries to pivot from IT into safety-critical OT, increasing the likelihood of physical disruption. United States agencies report that even low-skill groups successfully target industrial control systems, exposing weak segmentation and minimal multifactor authentication. Network zoning, zero-trust policies, and real-time anomaly detection are therefore moving from best practice to baseline expectation. Complexity grows as firms modernize without halting production, forcing staged rollouts and parallel architectures. Improved governance that aligns IT security, engineering, and production teams forms a critical piece of spend over the forecast horizon.
Mandatory TSA and IEC Cyber Rules for Pipelines
Revised Transportation Security Administration directives compel pipeline operators to verify controls, close gaps, and report breaches in set time windows. IEC 62443 is simultaneously emerging as the global control-system benchmark, with regional groups such as Japan's CERT delivering implementation guidance. Europe's NIS2 directive layers additional duties by mandating incident disclosure within 24 hours. Monetary penalties and potential shutdown orders for non-compliance raise security from discretionary spending to operational necessity. Vendors versed in both governance and technical deployment are in demand as operators seek turnkey compliance programs.
Legacy SCADA Upgrades Cost Overruns
Many platforms still rely on 20-year-old supervisory control systems never architected for network exposure. Firms routinely underestimate the engineering and downtime expense needed for segmentation, multifactor authentication, and encrypted telemetry. Upgrades often cost two to three times the original budget when compatibility hurdles surface mid-deployment. Extended asset lifecycles make capital allocation difficult, forcing operators to weigh short-term productivity loss against long-term resilience. Academic studies find that ineffective cross-department communication further delays execution and inflates cost.
Other drivers and restraints analyzed in the detailed report include:
- AI-Driven Predictive Security Analytics Adoption
- Energy-Price Volatility Boosting Insurance Requirements
- Shortage of OT-Security Talent in Remote Basins
For complete list of drivers and restraints, kindly check the Table Of Contents.
Segment Analysis
Surveillance platforms commanded 30.4% revenue share in 2024, confirming the market's long-standing focus on perimeter and situational awareness. The oil and gas security market size tied to video analytics, drones, and access control remains significant, but annual growth moderates as budgets reallocate toward digital defenses. Network and cybersecurity solutions, advancing at an 8.1% CAGR, reflect mandatory pipeline rules and the rise in ransomware aimed at field assets. Incidents such as the Colonial Pipeline attack emphasized that an operational halt can stem from a laptop rather than a fence breach, nudging capital toward intrusion detection and secure remote-access gateways.
In the forecast window, integrated command centers that fuse camera feeds with cyber telemetry are expected to outpace single-purpose deployments. This convergence reduces false positives by correlating physical badges with network logins. Vendors able to cross-tag events from cameras, firewalls, and controllers into a unified screen are likely to capture an expanding slice of the oil and gas security market. Consequently, surveillance remains vital but increasingly embedded within broader cyber-physical platforms, moderating standalone unit sales while lifting software analytics revenue.
Hardware still comprised 52.6% of the oil and gas security market share in 2024, spanning firewalls ruggedized for hazardous zones, intrinsically safe cameras, and vibration-resistant servers. However, the managed-services segment posts a 9.3% CAGR as operators contract 24 X 7 monitoring and incident response to offset skill gaps. The oil and gas security market size attached to service retainers is increasing because each new site demands advanced analytics, threat intelligence feeds, and periodic red-team assessments.
Service growth is also tied to regulatory audits, which require independent validation and documentation. Firms lacking internal capacity rely on MSSPs that specialise in OT assets; these providers bundle asset discovery, vulnerability management, and compliance reporting into multi-year agreements. Hardware vendors are reacting through outcome-based models that package equipment and services, thereby smoothing revenue and deepening customer lock-in.
Oil and Gas Security Market is Segmented by Security Type (Network and Cyber Security, Surveillance, Screening and Detection, and More), Component (Hardware, Software Platforms, and Services), Operation Stage (Upstream, Midstream, and Downstream), Deployment Mode (On-Premise, Cloud, and Hybrid/Edge-Cloud), Application (Exploration and Production Sites, Offshore Platforms and FPSOs, and More), and Geography.
Geography Analysis
North America maintained a 36.22% stake in the oil and gas security market in 2024, supported by mandatory TSA directives and the lingering lessons of the Colonial Pipeline ransomware event. Canada's threat assessments cite state-sponsored actors targeting production and midstream hubs, prompting coordinated public-private drills and grants for OT segmentation. Offshore assets in the Gulf of Mexico and the North Slope face calls for urgent cyber upgrades following federal audits that flagged outdated firewalls and unpatched HMIs.
Asia-Pacific records the fastest CAGR at 9.1% through 2030 as China extends trunk pipelines and storage capacity into border regions, blending OT security with sovereign cloud mandates from Beijing. Japan legislated economic-security rules that classify oil and gas as critical social infrastructure, compelling operators to file security plans with regulators. India expands refinery capacity and LNG terminals, sourcing managed services from local security operations centers in Bengaluru and Hyderabad. Australia and South Korea embed OT security clauses into new LNG export projects after noting rising regional tension in the South China Sea.
Europe's modernization drive centers on the NIS2 framework that mandates 24-hour incident reporting and annual audits for essential energy entities. LNG import build-outs across Germany, France, and the Netherlands add scale and complexity, necessitating encrypted maritime-to-terminal links. The Middle East and Africa experience stepped-up funding after a 206% rise in documented attacks, showcased at regional cyber forums. Latin America remains nascent but sees incremental investment as Brazil, Argentina, and Guyana grow production and seek alignment with IEC 62443.
- ABB Ltd.
- Airbus Defence and Space
- BAE Systems plc
- Baker Hughes Cyber-Security Services
- Belden Inc.
- Check Point Software Technologies Ltd.
- Cisco Systems Inc.
- Claroty Ltd.
- Dragos Inc.
- Fortinet Inc.
- Honeywell International Inc.
- Huawei Technologies Co. Ltd.
- Johnson Controls International plc
- Kaspersky Lab JSC
- Microsoft Corp.
- Nozomi Networks Inc.
- Palo Alto Networks Inc.
- Parsons Corp.
- Rockwell Automation Inc.
- Schneider Electric SE
- Siemens AG
- Tenable OT Security
- Thales Group
- Trend Micro Inc.
- Waterfall Security Solutions Ltd.
Additional Benefits:
- The market estimate (ME) sheet in Excel format
- 3 months of analyst support
TABLE OF CONTENTS
1 INTRODUCTION
- 1.1 Study Assumptions and Market Definition
- 1.2 Scope of the Study
2 RESEARCH METHODOLOGY
3 EXECUTIVE SUMMARY
4 MARKET LANDSCAPE
- 4.1 Market Overview
- 4.2 Market Drivers
- 4.2.1 Growing OT and IT convergence elevating cyber-risk
- 4.2.2 Mandatory TSA and IEC cyber rules for pipelines
- 4.2.3 AI-driven predictive security analytics adoption
- 4.2.4 Energy-price volatility boosting insurance requirements
- 4.2.5 Autonomous offshore assets needing edge-to-core security
- 4.3 Market Restraints
- 4.3.1 Legacy SCADA upgrades cost overruns
- 4.3.2 Shortage of OT-security talent in remote basins
- 4.3.3 Cloud-based data-sovereignty conflicts
- 4.3.4 ESG divestments curbing long-term capex
- 4.4 Industry Value Chain Analysis
- 4.5 Regulatory Landscape
- 4.6 Technological Outlook
- 4.7 Industry Attractiveness - Porter's Five Forces Analysis
- 4.7.1 Threat of New Entrants
- 4.7.2 Bargaining Power of Buyers
- 4.7.3 Bargaining Power of Suppliers
- 4.7.4 Threat of Substitutes
- 4.7.5 Intensity of Competitive Rivalry
- 4.8 Impact of Macroeconomic Factors on the Market
5 MARKET SIZE AND GROWTH FORECASTS (VALUES)
- 5.1 By Security Type
- 5.1.1 Network and Cyber Security
- 5.1.2 Surveillance
- 5.1.3 Screening and Detection
- 5.1.4 Command and Control
- 5.1.5 Physical Access Control
- 5.1.6 Other Types
- 5.2 By Component
- 5.2.1 Hardware
- 5.2.2 Software Platforms
- 5.2.3 Services (Managed and Professional)
- 5.3 By Operation Stage
- 5.3.1 Upstream (Exploration and Production)
- 5.3.2 Midstream (Pipelines and Storage)
- 5.3.3 Downstream (Refining and Distribution)
- 5.4 By Deployment Mode
- 5.4.1 On-premise
- 5.4.2 Cloud
- 5.4.3 Hybrid/Edge-Cloud
- 5.5 By Application
- 5.5.1 Exploration and Production Sites
- 5.5.2 Offshore Platforms and FPSOs
- 5.5.3 Pipeline Monitoring
- 5.5.4 Refineries and Petrochem Plants
- 5.5.5 LNG and Gas Processing
- 5.5.6 Retail and Distribution Terminals
- 5.6 By Geography
- 5.6.1 North America
- 5.6.1.1 United States
- 5.6.1.2 Canada
- 5.6.1.3 Mexico
- 5.6.2 South America
- 5.6.2.1 Brazil
- 5.6.2.2 Argentina
- 5.6.2.3 Chile
- 5.6.2.4 Rest of South America
- 5.6.3 Europe
- 5.6.3.1 Germany
- 5.6.3.2 United Kingdom
- 5.6.3.3 France
- 5.6.3.4 Italy
- 5.6.3.5 Spain
- 5.6.3.6 Russia
- 5.6.3.7 Rest of Europe
- 5.6.4 Asia-Pacific
- 5.6.4.1 China
- 5.6.4.2 India
- 5.6.4.3 Japan
- 5.6.4.4 South Korea
- 5.6.4.5 Malaysia
- 5.6.4.6 Singapore
- 5.6.4.7 Australia
- 5.6.4.8 Rest of Asia-Pacific
- 5.6.5 Middle East and Africa
- 5.6.5.1 Middle East
- 5.6.5.1.1 United Arab Emirates
- 5.6.5.1.2 Saudi Arabia
- 5.6.5.1.3 Turkey
- 5.6.5.1.4 Rest of Middle East
- 5.6.5.2 Africa
- 5.6.5.2.1 South Africa
- 5.6.5.2.2 Nigeria
- 5.6.5.2.3 Egypt
- 5.6.5.2.4 Rest of Africa
- 5.6.1 North America
6 COMPETITIVE LANDSCAPE
- 6.1 Market Concentration
- 6.2 Strategic Moves
- 6.3 Market Share Analysis
- 6.4 Company Profiles (includes Global level Overview, Market level overview, Core Segments, Financials as available, Strategic Information, Market Rank/Share for key companies, Products and Services, and Recent Developments)
- 6.4.1 ABB Ltd.
- 6.4.2 Airbus Defence and Space
- 6.4.3 BAE Systems plc
- 6.4.4 Baker Hughes Cyber-Security Services
- 6.4.5 Belden Inc.
- 6.4.6 Check Point Software Technologies Ltd.
- 6.4.7 Cisco Systems Inc.
- 6.4.8 Claroty Ltd.
- 6.4.9 Dragos Inc.
- 6.4.10 Fortinet Inc.
- 6.4.11 Honeywell International Inc.
- 6.4.12 Huawei Technologies Co. Ltd.
- 6.4.13 Johnson Controls International plc
- 6.4.14 Kaspersky Lab JSC
- 6.4.15 Microsoft Corp.
- 6.4.16 Nozomi Networks Inc.
- 6.4.17 Palo Alto Networks Inc.
- 6.4.18 Parsons Corp.
- 6.4.19 Rockwell Automation Inc.
- 6.4.20 Schneider Electric SE
- 6.4.21 Siemens AG
- 6.4.22 Tenable OT Security
- 6.4.23 Thales Group
- 6.4.24 Trend Micro Inc.
- 6.4.25 Waterfall Security Solutions Ltd.
7 MARKET OPPORTUNITIES AND FUTURE TRENDS
- 7.1 White-Space and Unmet-Need Assessment












