 |
市场调查报告书
商品编码
1851479
物联网安全:市场占有率分析、产业趋势、统计数据和成长预测(2025-2030 年)IoT Security - Market Share Analysis, Industry Trends & Statistics, Growth Forecasts (2025 - 2030) |
||||||
※ 本网页内容可能与最新版本有所差异。详细情况请与我们联繫。
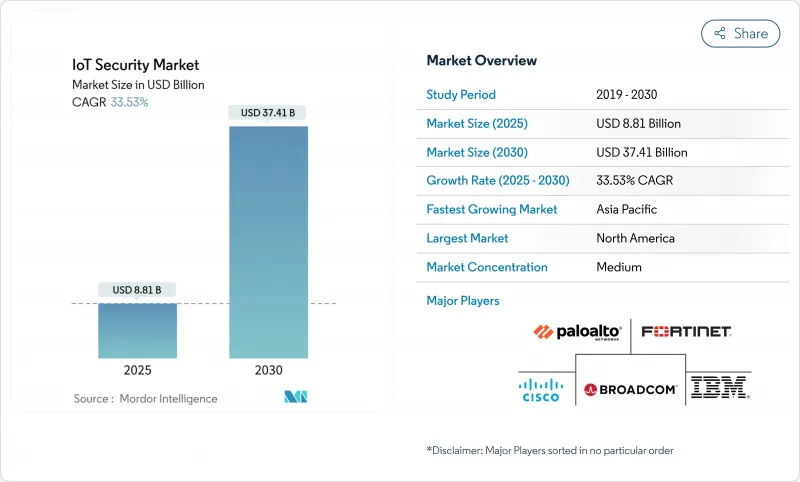
预计到 2025 年,物联网安全市场规模将达到 88.1 亿美元,到 2030 年将达到 374.1 亿美元,预测期(2025-2030 年)的复合年增长率为 33.53%。
随着监管机构强制要求所有连网产品都必须采用安全设计,操作技术正与IT网路融合,人工智慧分析技术能够对庞大的设备群进行即时侦测,企业正加速加大安全投入。英国的《产品安全和通讯基础设施法案》以及欧盟的《网路弹性法案》已将安全性从最佳实践转变为法律要求,预算也从可自由支配的计划转向了强制性合规。儘管随着数百万个未託管终端的出现,攻击面不断扩大,以边界为中心的防御仍然是重中之重,但向云端交付控制的转变正在重塑采购标准。供应商的差异化越来越依赖展示基于标准的自动化防御方案,这些方案能够从工厂车间扩展到远端边缘节点。
全球物联网安全市场趋势与洞察
资料外洩主导监管审查
监管机构已从自愿性指南转向惩罚性执法,欧盟《网路安全韧性法案》便是例证,该法案规定,对进入欧盟的不合规设备处以高达1500万欧元的罚款。英国法案禁止使用预设密码,强制规定更新窗口,并要求製造商重新设计其韧体流程。美国联邦通讯委员会(FCC)将于2024年推出的消费者标籤制度将允许买家比较产品的安全成熟度,从而使合规供应商获得竞争优势。诸如2025年3月耶鲁纽黑文医疗中心遭受的网路攻击导致550万份病患记录外洩等重大事件,凸显了监管的紧迫性,并加强了审查力度。顶级组装现在要求组件供应商持有第三方认证,这提高了没有安全开发流程记录的公司的进入门槛。
OT + IT 安全堆迭的集成
曾经孤立的操作技术网路如今正连接到企业云,并支援预测性维护和分析。 2025年第一季,针对北美工厂IT-OT介面的勒索软体攻击激增84%,促使采购文件中强制要求整合可见度。 Modbus和DNP3等传统工业通讯协定需要能够理解确定性流量和严格延迟阈值的安全工具,这促使供应商将深度封包检测整合到工厂环境中。思科2025财年第二季财报显示,随着客户将网路和安全性整合到统一平台上,安全收入增加了一倍以上。部署的复杂性推动了对专业服务的需求,这些服务能够帮助棕地工厂在不造成长时间停机的情况下完成迁移。随着整合配置的成熟,首席资讯安全们正在寻求能够从单一主机关联过程控制器、企业笔记型电脑和远端维护链路中异常情况的解决方案。
韧体更新生态系统碎片化
对 53,000 个常用微控制器的韧体镜像进行分析发现,99.43% 的镜像以明文形式存储,这使得攻击者可以直接存取引导程式和金钥。仅有三分之一的供应商维护自动化的空中升级流程,导致过时的组件平均长达 1.34 年未修补。欧盟法规强制要求自动化更新,并迫使远端刷写流程重新设计。更新造成的停机时间每小时可能损失数十万美元,这促使工业营运商犹豫不决,导致未打补丁的资产长期存在于关键基础设施中。这造成了日益增长的安全隐患,并减缓了高级身份验证框架的普及速度。
细分市场分析
到2024年,网路安全将占物联网安全市场收入的42%,这主要得益于企业将网路边缘视为单一统一的执法点。防火墙、微隔离和安全SD-WAN策略限制了不同端点之间的东西向流量,但通常缺乏晶片级的安全防护。随着生产线将传统可程式逻辑控制器连接到分析云,检验引擎现在除了解析标准IP协定外,还能解析工业通讯协定,这就需要专门的威胁情报来源。此外,FCC要求供应商描述云端更新路径的规定也促使买家转向那些整合防火墙和代理远端检测以验证修补程式状态的供应商。
随着平台向安全即服务 (Security as a Service) 模式转型,预计到 2030 年,云端/虚拟安全将以 35.45% 的复合年增长率成长。灵活的容量能够满足大规模韧体更新推送和视讯感测器回程传输突发的需求。企业透过在设备附近实施安全策略,同时将日誌传输到集中託管的分析平台进行关联异常检测,从而平衡延迟。像 LEA 这样的轻量级加密套件比 AES-128 功耗低 30%,即使在连结电池供电的标籤上也能实现即时加密。随着 5G RedCap 扩展工厂频宽,将云端策略引擎与本地执行代理结合的供应商有望获得更多的物联网安全市场份额。
到2024年,诸如加密库、身分平台和运行时异常检测代理等解决方案(这些方案通常打包在设备SDK中)将占据物联网安全市场58%的份额。由于预先认证的软体堆迭能够缩短ETSI EN 303 645和ISO 27400合规性审核,买家仍在为符合监管要求的软体许可分配预算。然而,随着人才短缺迫使营运商将全天候监控外包,服务(尤其是託管检测和回应服务)的复合年增长率将达到36.08%。
随着欧盟于2025年1月开始分阶段实施网路弹性法,强制製造商在产品发布前记录供应链风险评估,对专家咨询的需求日益增长。託管安全服务提供者正在集中工具并在客户之间共用威胁讯息,使中型公用事业公司也能获得以往只有全球品牌才能使用的功能。安全营运中心 (SOC) 团队正在整合人工智慧辅助系统来处理警报,在保持人员规模不变的情况下扩大服务利润,从而强化了从产品销售转向经常性收入模式的结构性转变。
物联网 (IoT) 安全市场报告按安全类型(网路安全、端点/设备安全、应用程式安全、云端/虚拟安全)、元件(解决方案和服务)、最终用户产业(智慧製造、连线健诊医疗、汽车和行动行程、能源和公共产业、其他)、部署模式(本地部署、云端/SECaaS、混合边缘)和行动旅游区进行细分。
区域分析
预计到2024年,北美仍将占全球收入的35%,这主要得益于联邦机构的倡议,例如FCC的标籤计划,该计划鼓励那些能够提供安全更新机製文件的供应商。各公司都在积极采用人工智慧驱动的分析技术,并充分利用其广泛的云端基础设施和成熟的安全营运中心(SOC)团队。美国国防安全保障部已将外国入侵关键基础设施列为首要风险,并支持联邦政府津贴监测和测试供水设施和管道。加拿大正在效仿美国的做法,而墨西哥的近岸外包热潮则要求在跨国物流枢纽中实现安全整合。硅谷和奥斯汀聚集了一批新兴企业,它们为财富500强企业的供应链提供取得专利的韧体完整性和后量子密码学解决方案。
亚太地区预计将以35.49%的复合年增长率快速成长,这主要得益于智慧城市的蓬勃发展和消费物联网的大规模普及。预计到2024年8月,中国的连网设备数量将达到25.7亿台,将增强本地通讯业者验证流量和阻止殭尸网路活动的能力。日本内务部将于2024年发布智慧城市安全指南,以推动地方政府从一开始就采用零信任原则进行采购。韩国的6G研究涵盖了物联网终端的抗量子密钥交换技术,一旦该标准稳定下来,韩国国内供应商预计将赢得出口合约。印尼和越南政府目前已将网路安全审核纳入製造业奖励,并鼓励外国投资者购买经过认证的安全平台。
欧洲正利用监管的力量而非单纯追求销售。欧盟《网路安全韧性法案》要求所有在欧盟销售的连网产品必须提供威胁建模、漏洞揭露和生命週期更新策略的文件。非欧洲製造商为了避免被排除在市场之外,也纷纷遵守该法案,从而将监管影响力扩展到全球。英国的《PSTI法案》取消了设备货架上的预设密码,并加强了基本的安全韧性。德国的工业4.0计划强调采用IEC 62443控制措施保障的确定性网络,而法国的都市资料平台则要求边缘网关和集中式分析之间进行端对端加密。欧盟的「数位欧洲计画」为中小企业采用经认证的安全协议堆迭津贴,从而扩大了託管服务提供者的潜在市场。
其他福利:
- Excel格式的市场预测(ME)表
- 3个月的分析师支持
目录
第一章 引言
- 研究假设和市场定义
- 调查范围
第二章调查方法
第三章执行摘要
第四章 市场情势
- 市场概览
- 市场驱动因素
- 资料外洩导致监管审查
- OT + IT 安全堆迭的集成
- 左移产品设计准则
- 人工智慧驱动的自适应威胁分析
- 基于卫星的NB-IoT在远端资产的部署
- 关键产业对安全物联网的需求日益增长
- 市场限制
- 韧体更新生态系统碎片化
- 旧式棕地的更新换代延迟
- 物联网领域网路安全人才短缺
- 边缘运算能力在加密方面的局限性
- 价值/供应链分析
- 监管环境
- 技术展望
- 波特五力分析
- 新进入者的威胁
- 买方的议价能力
- 供应商的议价能力
- 替代品的威胁
- 竞争对手之间的竞争
第五章 市场规模与成长预测
- 按证券类型
- 网路安全
- 端点/设备安全
- 应用程式安全
- 云端/虚拟安全
- 按组件
- 解决方案
- 身分和存取管理 (IAM) 和公钥基础设施 (PKI)
- DDoS防护
- IDS/IPS
- 加密和令牌化
- 服务
- 专业服务
- 託管安全服务
- 解决方案
- 按最终用户行业划分
- 智慧製造
- 互联医疗
- 汽车与出行
- 能源与公共产业
- BFSI
- 政府与智慧城市
- 零售和物流
- 透过部署模式
- 本地部署
- 云端/安全即服务
- 混合边缘
- 按地区
- 北美洲
- 美国
- 加拿大
- 墨西哥
- 南美洲
- 巴西
- 阿根廷
- 其他南美洲
- 欧洲
- 德国
- 英国
- 法国
- 义大利
- 其他欧洲地区
- 亚太地区
- 中国
- 日本
- 印度
- 韩国
- 亚太其他地区
- 中东和非洲
- 阿拉伯聯合大公国
- 沙乌地阿拉伯
- 南非
- 其他中东和非洲地区
- 北美洲
第六章 竞争情势
- 市场集中度
- 策略趋势
- 市占率分析
- 公司简介
- Cisco Systems
- IBM
- Broadcom(Symantec)
- Palo Alto Networks
- Check Point
- Fortinet
- Microsoft
- Trend Micro
- Armis
- Infineon Technologies
- ATandT Cybersecurity
- Darktrace
- SecureWorks
- Rapid7
- Trustwave
- Thales
- RSA Security
- Qualys
- Kaspersky
- Zscaler
第七章 市场机会与未来展望
The IoT Security Market size is estimated at USD 8.81 billion in 2025, and is expected to reach USD 37.41 billion by 2030, at a CAGR of 33.53% during the forecast period (2025-2030).

Enterprises are accelerating spending because regulators now mandate security-by-design for every connected product, operational technology is converging with IT networks, and AI analytics deliver real-time detection across massive device fleets. The United Kingdom's Product Security and Telecommunications Infrastructure Act and the European Union's Cyber Resilience Act have transformed security from a best practice into a legal requirement, diverting budgets from discretionary projects to mandatory compliance. Perimeter-centric defenses retain priority as millions of unmanaged endpoints widen attack surfaces, yet the move toward cloud-delivered controls is reshaping procurement criteria. Vendor differentiation increasingly depends on evidence of automated, standards-aligned protection that scales from factory floors to remote edge nodes.
Global IoT Security Market Trends and Insights
Data-breach-led Regulatory Scrutiny
Regulators moved from voluntary guidelines to punitive enforcement, exemplified by the EU Cyber Resilience Act that can impose EUR 15 million penalties for non-compliant devices entering the bloc. The United Kingdom's PSTI Act, effective April 2024, bans default passwords and mandates defined update windows, forcing manufacturers to redesign firmware pipelines. Consumer-facing labels introduced by the US Federal Communications Commission in 2024 allow buyers to compare security maturity, shifting competitive advantage toward compliant vendors. High-profile incidents, such as the March 2025 cyberattack that exposed 5.5 million Yale New Haven Health patient records, illustrate regulatory urgency and intensify oversight. Tier-one assemblers now obligate component suppliers to hold third-party certifications, raising entry barriers for firms lacking documented secure-development processes.
Convergence of OT + IT Security Stacks
Operational technology networks that once ran in isolation now connect to corporate clouds to support predictive maintenance and analytics. Ransomware targeting the IT-OT interface surged 84% during Q1 2025 in North American plants, prompting unified visibility mandates in procurement documents. Legacy industrial protocols such as Modbus and DNP3 require security tools that understand deterministic traffic and strict latency thresholds, pushing vendors to integrate deep packet inspection tailored for factory environments. Cisco's security revenue more than doubled in its Q2 FY2025 results as customers consolidated on converged networking and security platforms. Implementation complexity has triggered demand for professional services that can migrate brown-field plants without prolonged downtime. As converged deployments mature, chief information security officers seek solutions that correlate anomalies across process controllers, corporate laptops, and remote maintenance links from a single console.
Fragmented Firmware-Update Ecosystem
Analysis of 53,000 firmware images across common microcontrollers showed 99.43% stored in plaintext, offering attackers direct access to boot loaders and secrets. Only one-third of vendors maintain an automated over-the-air update pipeline, leaving outdated components unpatched for an average of 1.34 years. EU rules now force automatic updates, compelling redesigns of remote-flash processes. Industrial operators hesitate because downtime for updates can cost hundreds of thousands of USD per hour, so unpatched assets persist inside critical infrastructure. The result is a widening security debt that slows the adoption of advanced authentication frameworks.
Other drivers and restraints analyzed in the detailed report include:
- Shift-left Product-design Mandates
- AI-powered Adaptive Threat Analytics
- Legacy Brownfield Device Refresh Lag
For complete list of drivers and restraints, kindly check the Table Of Contents.
Segment Analysis
Network Security generated 42% of IoT security market revenue in 2024, driven by enterprises that still treat the network edge as the only uniformly controllable enforcement point. Firewall, micro-segmentation, and secure SD-WAN policies restrict east-west traffic among heterogeneous endpoints that often lack chip-level safeguards. As production lines connect legacy programmable logic controllers to analytics clouds, inspection engines now parse industrial protocols alongside standard IP, demanding specialized threat-intel feeds. Adoption also benefits from the FCC rule requiring vendors to illustrate cloud-enabled update paths, nudging buyers toward providers that integrate firewall and proxy telemetry to verify patch status.
Cloud/Virtual Security is projected for a 35.45% CAGR through 2030 as platforms shift to security-as-a-service. Elastic capacity aligns with bursts from massive firmware-update pushes or backhaul from video sensors. Enterprises balance latency by keeping enforcement near the device while forwarding logs to centrally hosted analytics for correlated anomaly detection. Lightweight cipher suites such as LEA consume 30% less energy than AES-128, allowing real-time encryption even in coin-cell-powered tags. Vendors that fuse cloud policy engines with local enforcement agents are poised to capture additional IoT security market share once 5G RedCap widens bandwidth on factory floors.
Solutions retained a 58% share of the IoT security market size in 2024, spanning encryption libraries, identity platforms, and runtime anomaly detection agents packaged into device SDKs. Pre-certified stacks shorten compliance audits under ETSI EN 303 645 or ISO 27400, so buyers still allocate budget to software licenses that tick regulatory checklists. However, Services, especially managed detection and response, will rise at a 36.08% CAGR because talent shortages push operators to outsource 24X7 monitoring.
Professional consulting demand climbed after the EU began a phased enforcement of the Cyber Resilience Act in January 2025, forcing manufacturers to document supply-chain risk assessments before product launch. Managed Security Services Providers centralize tooling and share threat intel across customers, giving midsize utilities access to capabilities once reserved for global brands. As SOC teams integrate AI co-pilots that triage alerts, service margins expand even while headcount stays flat, reinforcing the structural shift from product sales to recurring revenue models.
The Internet of Things (IoT) Security Market Report is Segmented by Security Type (Network Security, Endpoint/Devices Security, Application Security, and Cloud/Virtual Security), Component (Solutions and Services), End-User Industry (Smart Manufacturing, Connected Healthcare, Automotive and Mobility, Energy and Utilities, and More), Deployment Mode (On-Premise, Cloud/SECaaS, and Hybrid Edge), and Geography.
Geography Analysis
North America retained 35% of global revenue in 2024, anchored by federal initiatives such as the FCC labeling scheme that favor vendors prepared to document secure-update mechanisms. Enterprises adopted AI-enabled analytics early, leveraging extensive cloud infrastructure and mature SOC staffing. The Department of Homeland Security specifically names foreign intrusions into critical infrastructure as a top risk, driving federal grants toward water-utility and pipeline monitoring pilots. Canada mirrors the US approach, while Mexico's near-shoring boom requires integrated security across cross-border logistics hubs. Startups cluster around Silicon Valley and Austin, funneling patented firmware-integrity and post-quantum crypto solutions into Fortune 500 supply chains.
Asia Pacific is the fastest-growing territory, forecast for 35.49% CAGR, propelled by aggressive smart-city rollouts and massive consumer IoT adoption. China reported 2.57 billion connected terminals by August 2024, stretching local operators' capacity to authenticate traffic and block botnet activity. Japan's Ministry of Internal Affairs and Communications issued secure smart-city guidelines in 2024, catalysing municipal procurements that embed zero-trust from the outset. South Korea's 6G research includes quantum-resistant key exchange for IoT endpoints, positioning domestic vendors to capture export contracts once standards stabilize. Governments in Indonesia and Vietnam now bundle cyber-hygiene audits into manufacturing incentives, compelling foreign investors to purchase certified security platforms.
Europe leverages regulatory pull rather than raw volume. The Cyber Resilience Act obliges every connected product sold in the bloc to document threat modeling, vulnerability disclosure, and lifelong update policies. Manufacturers outside Europe comply to avoid market exclusion, exporting the regulation's influence worldwide. The United Kingdom's PSTI Act removes default passwords from consumer electronics shelves, enhancing baseline resilience. Germany's Industrie 4.0 projects emphasize deterministic networking secured by IEC 62443 controls, while France's metropolitan data platforms require end-to-end encryption between edge gateways and centralized analytics. Funding from the EU's Digital Europe Programme subsidizes SME adoption of certified security stacks, broadening the addressable market for managed service providers.
- Cisco Systems
- IBM
- Broadcom (Symantec)
- Palo Alto Networks
- Check Point
- Fortinet
- Microsoft
- Trend Micro
- Armis
- Infineon Technologies
- ATandT Cybersecurity
- Darktrace
- SecureWorks
- Rapid7
- Trustwave
- Thales
- RSA Security
- Qualys
- Kaspersky
- Zscaler
Additional Benefits:
- The market estimate (ME) sheet in Excel format
- 3 months of analyst support
TABLE OF CONTENTS
1 INTRODUCTION
- 1.1 Study Assumptions and Market Definition
- 1.2 Scope of the Study
2 RESEARCH METHODOLOGY
3 EXECUTIVE SUMMARY
4 MARKET LANDSCAPE
- 4.1 Market Overview
- 4.2 Market Drivers
- 4.2.1 Data-breach?led regulatory scrutiny
- 4.2.2 Convergence of OT + IT security stacks
- 4.2.3 Shift-left product-design mandates
- 4.2.4 AI-powered adaptive threat analytics
- 4.2.5 Satellite-based NB-IoT roll-out in remote assets
- 4.2.6 Increasing Demand for Secure IoT in Critical Industries
- 4.3 Market Restraints
- 4.3.1 Fragmented firmware-update ecosystem
- 4.3.2 Legacy brown-field device refresh lag
- 4.3.3 Shortage of IoT-specific cyber-talent
- 4.3.4 Edge-compute power limits for encryption
- 4.4 Value/Supply-Chain Analysis
- 4.5 Regulatory Landscape
- 4.6 Technological Outlook
- 4.7 Porter's Five Forces Analysis
- 4.7.1 Threat of New Entrants
- 4.7.2 Bargaining Power of Buyers
- 4.7.3 Bargaining Power of Suppliers
- 4.7.4 Threat of Substitutes
- 4.7.5 Competitive Rivalry
5 MARKET SIZE AND GROWTH FORECASTS (VALUE)
- 5.1 By Security Type
- 5.1.1 Network Security
- 5.1.2 Endpoint/Device Security
- 5.1.3 Application Security
- 5.1.4 Cloud/Virtual Security
- 5.2 By Component
- 5.2.1 Solutions
- 5.2.1.1 IAM and PKI
- 5.2.1.2 DDoS Protection
- 5.2.1.3 IDS/IPS
- 5.2.1.4 Encryption and Tokenisation
- 5.2.2 Services
- 5.2.2.1 Professional Services
- 5.2.2.2 Managed Security Services
- 5.2.1 Solutions
- 5.3 By End-user Industry
- 5.3.1 Smart Manufacturing
- 5.3.2 Connected Healthcare
- 5.3.3 Automotive and Mobility
- 5.3.4 Energy and Utilities
- 5.3.5 BFSI
- 5.3.6 Government and Smart Cities
- 5.3.7 Retail and Logistics
- 5.4 By Deployment Mode
- 5.4.1 On-premise
- 5.4.2 Cloud/SECaaS
- 5.4.3 Hybrid Edge
- 5.5 By Geography
- 5.5.1 North America
- 5.5.1.1 United States
- 5.5.1.2 Canada
- 5.5.1.3 Mexico
- 5.5.2 South America
- 5.5.2.1 Brazil
- 5.5.2.2 Argentina
- 5.5.2.3 Rest of South America
- 5.5.3 Europe
- 5.5.3.1 Germany
- 5.5.3.2 United Kingdom
- 5.5.3.3 France
- 5.5.3.4 Italy
- 5.5.3.5 Rest of Europe
- 5.5.4 Asia-Pacific
- 5.5.4.1 China
- 5.5.4.2 Japan
- 5.5.4.3 India
- 5.5.4.4 South Korea
- 5.5.4.5 Rest of Asia Pacific
- 5.5.5 Middle East and Africa
- 5.5.5.1 United Arab Emirates
- 5.5.5.2 Saudi Arabia
- 5.5.5.3 South Africa
- 5.5.5.4 Rest of Middle East and Africa
- 5.5.1 North America
6 COMPETITIVE LANDSCAPE
- 6.1 Market Concentration
- 6.2 Strategic Moves
- 6.3 Market Share Analysis
- 6.4 Company Profiles (includes Global level Overview, Market level overview, Core Segments, Financials as available, Strategic Information, Market Rank/Share for key companies, Products and Services, Recent Developments)
- 6.4.1 Cisco Systems
- 6.4.2 IBM
- 6.4.3 Broadcom (Symantec)
- 6.4.4 Palo Alto Networks
- 6.4.5 Check Point
- 6.4.6 Fortinet
- 6.4.7 Microsoft
- 6.4.8 Trend Micro
- 6.4.9 Armis
- 6.4.10 Infineon Technologies
- 6.4.11 ATandT Cybersecurity
- 6.4.12 Darktrace
- 6.4.13 SecureWorks
- 6.4.14 Rapid7
- 6.4.15 Trustwave
- 6.4.16 Thales
- 6.4.17 RSA Security
- 6.4.18 Qualys
- 6.4.19 Kaspersky
- 6.4.20 Zscaler
7 MARKET OPPORTUNITIES AND FUTURE OUTLOOK
- 7.1 White-space and Unmet-need Assessment









