 |
市场调查报告书
商品编码
1637913
亚太网路安全:市场占有率分析、产业趋势与统计、成长预测(2025-2030 年)APAC Cybersecurity - Market Share Analysis, Industry Trends & Statistics, Growth Forecasts (2025 - 2030) |
||||||
※ 本网页内容可能与最新版本有所差异。详细情况请与我们联繫。
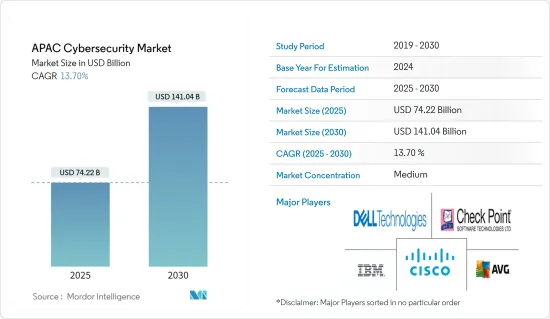
2025年亚太地区网路安全市场规模预估为742.2亿美元,预估至2030年将达1,410.4亿美元,预测期间(2025-2030年)复合年增长率为13.7%。
随着物联网的出现以及该地区数位转型的速度和范围的不断扩大,目前的网路基础设施更容易受到网路攻击。近年来,网路、社群媒体和行动装置的使用均大幅成长,推动该地区网路安全水准的强劲提升。由于这些攻击的严重性日益增加以及政府立法的严格,亚太地区的网路安全产业预计将进一步扩大。
主要亮点
- 已开发国家和新兴国家互联网使用量的不断增加正在推动网路安全解决方案的采用。此外,行动装置无线网路的扩展带来了资料脆弱性的增加,这使得网路安全成为任何组织的关键因素。
- 包括印度、中国、新加坡和日本在内的许多新兴国家正面临日益严峻的网路安全相关挑战。印度的 DNS 劫持案件数量位居第三,这显示登记的网路犯罪急剧增加。此外,根据IBM X-Force威胁情报指数2022,亚洲将在2021年遭受全球26%的攻击,成为全球受攻击最严重的地区。印度是亚洲遭受攻击最频繁的国家。澳洲网路安全成长网路最近进行的一项研究显示,未来十年网路安全产业的规模可能会扩大两倍。
- 近年来,网路安全事件屡屡发生,但大部分仍处于隐蔽状态。最近一些备受瞩目的案件对众多公众产生了重大影响,使其成为公众讨论的焦点以及政府和监管机构的关注。例如,印度官方网路安全组织CERT-In已就资讯安全实务、程序、网路事件的预防、回应和报告发布了指示,以确保网路的安全可靠,并引入了严格的网路安全报告要求。据该机构称,截至 2022 年 2 月,印度已发生 212 多起网路安全事件。
- 行业内部网路设备的数量正在增加,例如家用电器、连网汽车和工厂,这不仅透过降低设备成本,而且还透过创建新的商业模式和应用程序,推动了物联网的采用并加强了企业的网路安全。因此,M2M/IoT 连接的采用正在推动网路安全市场的发展。
- 挑战在于准备程度低和对传统身分验证技术的高度依赖。在安全专家建议采用脸部认证和生物识别等身分管理解决方案的市场环境中,超过 80% 的组织仍然仅依靠使用者名称和密码登录,这可能会对成长构成挑战。
亚太地区网路安全市场趋势
云端部署推动市场成长
- 随着企业越来越意识到将资料迁移到云端以节省成本和资源(而不是建置和维护新的资料储存)的重要性,对云端基础的解决方案的需求正在增长。正在增加。
- 这些优势正在推动该地区大大小小的企业采用云端基础的解决方案。未来几年,云端平台和生态系统有望成为爆发数位创新速度和规模的发射台。
- 根据思科网路安全报告,亚太地区国家更有可能将其基础架构的更高比例託管在云端而不是本地端。此外,2023 年 3 月举行的思科印度峰会上,将举办一个论坛,以促进网路安全能力,增强印度企业的安全韧性,并帮助他们利用数位化作为竞争优势。 ,思科宣布将在清奈建立一个新的资料中心,并资料位于孟买的现有资料中心进行现代化改造。
- 随着 Google Drive、Dropbox 和 Microsoft Azure 等云端服务越来越多地被采用,并且这些工具成为业务流程不可或缺的一部分,企业必须解决对敏感资料失去控制等安全性问题。这导致按需网路安全解决方案的采用率增加。
- 该地区的微软等公司正在提供云端基础的端点保护技术,使员工可以在他们想要的时间、地点和方式下工作,并帮助他们完成工作。对你有益。
中国占有最大市场占有率
- 国内网路攻击的增多促使中国加强防御能力。在世界其他地区,政府也是网路攻击的主要来源。根据Cloudflare提供的数据,2022年3月,中国占全球网路攻击事件的45%。
- 预计在预测期内,政府和相关监管机构将加大力度加强云端安全,从而推动基于网路安全的解决方案的采用。
- 2022年1月,国家网路资讯办公室宣布了对购买可能影响国家安全的网路产品和服务的关键资讯基础设施营运商(CIIO)进行网路安全审查的新措施。该措施包括对关键通讯产品、高效能电脑及伺服器、大容量储存设备、大型资料库及应用程式、云端运算服务以及其他对关键资讯基础设施安全有重大影响的网路产品和服务进行限制。向网路安全审查办公室(CRO)申请网路安全审查。
- 此外,加密在中国面临更大的阻力。该国政府的加密法规和执行是世界上最严格的之一,政府可以完全存取其境内的所有加密内容。 《中华人民共和国密码法》第三十一条规定,国家密码管理局有权对密码系统进行检查、存取。该规则适用于所有行业,包括微信等社交媒体平台,因为对话不是端对端加密的。
- 技术进步正在增加中国联网设备的数量。它是全球最大的物联网(IoT)市场。此外,5G和支援5G的设备将大大提高设备互联互通性。由此带来的连网设备的增加直接增加了安全产品的市场需求。
亚太网路安全产业概况
亚太网路安全市场处于半分散状态。企业对行动安全意识的不断提高,促使市场参与者采取併购、合作和新产品等策略性倡议。
- 2022 年 2 月:上述日期投资的印度 IBM 安全指挥中心标誌着对亚太地区组织安全事件回应和培训的一项重大投资。该中心旨在透过高度逼真的网路攻击模拟,为从高管到技术人员的每个人提供网路安全回应技术培训。这项投资还包括一个全新的安全营运中心 (SOC),这将扩大 IBM 广泛的全球 SOC 网络,为全球客户提供全天候的安全回应服务。
其他福利
- Excel 格式的市场预测 (ME) 表
- 3 个月的分析师支持
目录
第 1 章 简介
- 研究假设和市场定义
- 研究范围
第二章调查方法
第三章执行摘要
第四章 市场洞察
- 市场概况
- 产业价值链分析
- 产业吸引力-波特五力分析
- 供应商的议价能力
- 消费者议价能力
- 新进入者的威胁
- 替代品的威胁
- 竞争对手之间的竞争
- 产业指引及政策
- COVID-19 市场影响评估
第五章 市场动态
- 市场驱动因素
- 网路安全事件和报告法规迅速增加
- 日益增加的 M2M/IoT 连线要求企业加强网路安全措施
- 市场限制
- 网路安全专家短缺
- 高度依赖传统身分验证方法且缺乏准备
- 市场机会
- 物联网、BYOD、人工智慧和机器学习在网路安全领域的发展趋势
第六章 市场细分
- 依产品类型
- 解决方案
- 身分和存取管理
- 威胁侦测和预防(统一威胁管理和威胁缓解)
- 安全和漏洞管理
- DDoS 缓解
- 新一代防火墙
- IDS/IPS
- 安全资讯和事件管理
- 其他解决方案
- 按服务
- 解决方案
- 按部署
- 在云端
- 本地
- 按最终用户产业
- 航太和国防
- 银行、金融服务和保险
- 卫生保健
- 製造业
- 零售
- 资讯科技/通讯
- 其他最终用户产业
- 按国家
- 中国
- 印度
- 日本
- 韩国
第七章 竞争格局
- 公司简介
- AVG Technologies(Avast Software sro)
- IBM Corporation
- Check Point Software Technologies Ltd
- Cisco Systems Inc.
- Cyber Ark Software Ltd
- Dell Technologies Inc.
- Fireeye Inc.
- Fortinet Inc.
- Imperva Inc.
- Intel Security(Intel Corporation)
- Palo Alto Networks Inc.
- Proofpoint Inc.
- Rapid7 Inc.
- Broadcom Inc.
- Trend Micro Inc.
第八章投资分析
第九章:市场的未来
The APAC Cybersecurity Market size is estimated at USD 74.22 billion in 2025, and is expected to reach USD 141.04 billion by 2030, at a CAGR of 13.7% during the forecast period (2025-2030).

Due to the advent of IoT and the growing speed and scope of digital transformation in this region, the current network infrastructure is becoming more exposed to cyberattacks. Internet, social media, and mobile users have all seen significant increases in recent years, contributing to the region's strong rise in cybersecurity. The Asia-Pacific cybersecurity industry is expected to expand even more due to the increasing severity of these attacks and strict government laws.
Key Highlights
- The growing internet usage in both developed and developing countries increases the adoption of cybersecurity solutions. Additionally, due to increased data susceptibility brought on by the expansion of the wireless network for mobile devices, cybersecurity has become a crucial component of every organization.
- Many emerging countries, such as India, China, Singapore, and Japan, face increasing cybersecurity-related issues. India ranks third in the number of DNS hijacks, indicating a sharp rise in cybercrime registration. Additionally, Asia received 26% of all worldwide attacks in 2021, according to IBM X-Force Threat Intelligence Index 2022, making it the most attacked area globally. India tops the list of the most frequently attacked country in Asia. Recent research by the Australian Cyber Security Growth Network entitled the cybersecurity sector might triple in size over the next ten years.
- Although there have been several cybersecurity events in recent years, most of them have remained hidden. Recent high-profile incidents that significantly impacted many common persons have brought public conversation and government and regulatory body attention to the forefront. For Instance, CERT-In, India's official cybersecurity organization, issued a direction relating to Information security practices, procedures, prevention, response, and reporting of cyber incidents for safe and trusted internet to impose stringent cybersecurity reporting requirements. It stated that India had recorded over 2.12 lakh cybersecurity incidents as of February 2022.
- The industry is being driven by new business models and applications as well as reducing device costs, such as an increasing number of connected devices, including consumer electronics, connected cars, factories, etc., which is driving the adoption of IoT and strengthening cybersecurity in enterprises. So, The adoption of M2M/IoT connections drives the cybersecurity market.
- Low preparedness and a high reliance on conventional authentication techniques are challenging. In a market environment where security professionals advise identity-management solutions like facial recognition and biometric identification, more than 80% of organizations still rely solely on usernames and passwords for login, which could challenge growth.
Asia Pacific Cyber Security Market Trends
Cloud Deployment Drives Market Growth
- The increasing realization among companies about the importance of saving money and resources by moving their data to the cloud rather than building and maintaining new data storage drives the demand for cloud-based solutions, hence increasing the adoption of on-demand security services.
- Owing to these benefits, large enterprises and SMEs in the region are increasingly adopting cloud-based solutions. Over the next few years, cloud platforms and ecosystems are expected to serve as the launch pad for an explosion in the pace and scale of digital innovation.
- Countries in the Asia-Pacific tend to have higher percentages of their infrastructures hosted in the cloud rather than on-premise, according to the CISCO Cybersecurity report. Additionally, in March 2023, during the Cisco India Summit 2023, the company announced that it has been growing its cyber security capabilities to support Indian businesses in strengthening their security resilience and utilizing digitalization as a competitive advantage and to provide its clients with better security options, Cisco has been establishing a new data center in Chennai and modernizing the one that already exists in Mumbai.
- With the rising adoption of cloud services, like Google Drive, Dropbox, and Microsoft Azure, and with these tools emerging as an integral part of business processes, enterprises must deal with security issues, such as losing control over sensitive data. This gives rise to the increased incorporation of on-demand cyber-security solutions.
- The company, such as Microsoft in the region, offers Cloud-based endpoint protection technology that enables employees to work when, where, and how they need to function and can allow them to use the devices and apps they find most beneficial to get their work done.
China to Occupy the Largest Market Share
- Growing cyber-attacks in the country have propelled China to strengthen its defensive capabilities. The government is also a major source of cyberattacks in other parts of the world. According to the statistics provided by Cloudflare, in March 2022, China accounted for 45% of the world's cyberattack incidents.
- The increasing initiatives by the government and the related regulatory bodies to strengthen cloud security are expected to fuel the adoption of cyber security-based solutions over the forecast period.
- The Cyberspace Administration of China issued new measures for cybersecurity review in January 2022 for critical information infrastructure operators (CIIO) purchasing network products and services, which may influence national security. Under this measure, Important communications products, high-performance computers or servers, mass storage equipment, large database or application, cloud computing service, or any other network product or service that has an important influence on the security of any critical information infrastructure, CIIO should apply to Cybersecurity Review Office (CRO) for cybersecurity review.
- Moreover, encryption has met greater resistance in China. The government's encryption regulations and implementation are among the most restrictive in the world, giving the government full access to all encrypted content within its domestic territory. Article 31 of China's Cryptography Law allows the State Cryptography Administration to inspect and access encrypted systems. Since conversations are not end-to-end encrypted, this rule applies to all industries, including social media platforms like WeChat, which are required (and able) to turn over all user data.
- Owing to technological advancements, there is an increase in the number of connected devices in China. It is the world's largest Internet of Things (IoT) market. Furthermore, 5G and 5G enabled devices will exponentially increase the devices' interconnectivity. As a result, it increases connected devices, directly augmenting the market's need for security products.
Asia Pacific Cyber Security Industry Overview
The Asia-Pacific cybersecurity market is semi fragmented. Players in the market adopt strategic initiatives such as mergers and acquisitions, partnerships, and new product offerings due to increasing awareness regarding mobility security among enterprises.
- February 2022: The IBM Security Command Center in India, for which investments were made on the aforementioned date, represents a sizeable investment in security incident response and training for organizations throughout the Asia-Pacific. It is designed to prepare everyone from the C-Suite to technical staff by training cybersecurity response techniques through highly realistic, simulated cyberattacks. The investment also includes a brand-new Security Operation Center (SOC), which would be added to IBM's extensive worldwide network of SOCs and would offer clients all over the world round-the-clock security response services.
Additional Benefits:
- The market estimate (ME) sheet in Excel format
- 3 months of analyst support
TABLE OF CONTENTS
1 INTRODUCTION
- 1.1 Study Assumptions and Market Definition
- 1.2 Scope of the Study
2 RESEARCH METHODOLOGY
3 EXECUTIVE SUMMARY
4 MARKET INSIGHTS
- 4.1 Market Overview
- 4.2 Industry Value Chain Analysis
- 4.3 Industry Attractiveness - Porter's Five Forces Analysis
- 4.3.1 Bargaining Power of Suppliers
- 4.3.2 Bargaining Power of Consumers
- 4.3.3 Threat of New Entrants
- 4.3.4 Threat of Substitute Products
- 4.3.5 Competitive Rivalry within the Industry
- 4.4 Industry Guidelines and Policies
- 4.5 Assessment of the Impact of the COVID-19 on the Market
5 MARKET DYNAMICS
- 5.1 Market Drivers
- 5.1.1 Rapidly Increasing Cybersecurity Incidents and Regulations Requiring Their Reporting
- 5.1.2 Growing M2M/IoT Connections Demanding Strengthened Cybersecurity in Enterprises
- 5.2 Market Restraints
- 5.2.1 Lack of Cybersecurity Professionals
- 5.2.2 High Reliance on Traditional Authentication Methods and Low Preparedness
- 5.3 Market Opportunities
- 5.3.1 Rise in the Trends of IoT, BYOD, Artificial Intelligence, and Machine Learning in Cybersecurity
6 MARKET SEGMENTATION
- 6.1 By Product Type
- 6.1.1 Solutions
- 6.1.1.1 Identity and Access Management
- 6.1.1.2 Threat Detection and Prevention (Unified Threat Management and Threat Mitigation)
- 6.1.1.3 Security and Vulnerability Management
- 6.1.1.4 DDoS Mitigation
- 6.1.1.5 Next Generation Firewall
- 6.1.1.6 IDS/IPS
- 6.1.1.7 Security Information and Event Management
- 6.1.1.8 Other Solutions
- 6.1.2 Services
- 6.1.1 Solutions
- 6.2 By Deployment
- 6.2.1 On-cloud
- 6.2.2 On-premises
- 6.3 By End-user Industry
- 6.3.1 Aerospace and Defense
- 6.3.2 Banking, Financial Services, and Insurance
- 6.3.3 Healthcare
- 6.3.4 Manufacturing
- 6.3.5 Retail
- 6.3.6 IT and Telecommunication
- 6.3.7 Other End-user Industries
- 6.4 By Country
- 6.4.1 China
- 6.4.2 India
- 6.4.3 Japan
- 6.4.4 South Korea
7 COMPETITIVE LANDSCAPE
- 7.1 Company Profiles
- 7.1.1 AVG Technologies (Avast Software s.r.o.)
- 7.1.2 IBM Corporation
- 7.1.3 Check Point Software Technologies Ltd
- 7.1.4 Cisco Systems Inc.
- 7.1.5 Cyber Ark Software Ltd
- 7.1.6 Dell Technologies Inc.
- 7.1.7 Fireeye Inc.
- 7.1.8 Fortinet Inc.
- 7.1.9 Imperva Inc.
- 7.1.10 Intel Security (Intel Corporation)
- 7.1.11 Palo Alto Networks Inc.
- 7.1.12 Proofpoint Inc.
- 7.1.13 Rapid7 Inc.
- 7.1.14 Broadcom Inc.
- 7.1.15 Trend Micro Inc.












